信息网络安全 ›› 2025, Vol. 25 ›› Issue (6): 872-888.doi: 10.3969/j.issn.1671-1122.2025.06.003
基于联邦学习的智能汽车CAN总线入侵检测系统
荀毅杰1,2, 崔嘉容1,2, 毛伯敏1,2( ), 秦俊蔓1,2
), 秦俊蔓1,2
- 1.西北工业大学网络空间安全学院,西安 710072
2.西北工业大学深圳研究院,深圳 518057
-
收稿日期:2025-02-25出版日期:2025-06-10发布日期:2025-07-11 -
通讯作者:毛伯敏 maobomin@nwpu.edu.cn -
作者简介:荀毅杰(1994—),男,山西,副教授,博士,主要研究方向为智能车联网安全、人工智能和信息安全|崔嘉容(2002—),女,河北,硕士研究生,主要研究方向为智能车联网安全|毛伯敏(1989—),男,湖北,教授,博士,主要研究方向为空天地一体化网络、卫星物联网、车联网、边缘计算|秦俊蔓(1996—),女,安徽,博士研究生,主要研究方向为智能车联网安全、人工智能和信息安全。 -
基金资助:国家自然科学基金(62202386);国家自然科学基金(62402389);广东省基础与应用基础研究基金(2024A1515011198);广东省基础与应用基础研究基金(2024A1515010209);广东省基础与应用基础研究基金(2023A1515110079)
Intrusion Detection System for the Controller Area Network Bus of Intelligent Vehicles Based on Federated Learning
XUN Yijie1,2, CUI Jiarong1,2, MAO Bomin1,2( ), QIN Junman1,2
), QIN Junman1,2
- 1. School of Cybersecurity, Northwestern Polytechnical University, Xi’an 710072, China
2. Research & Development Institute of Northwestern Polytechnical University in Shenzhen, Shenzhen 518057, China
-
Received:2025-02-25Online:2025-06-10Published:2025-07-11
摘要:
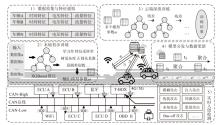
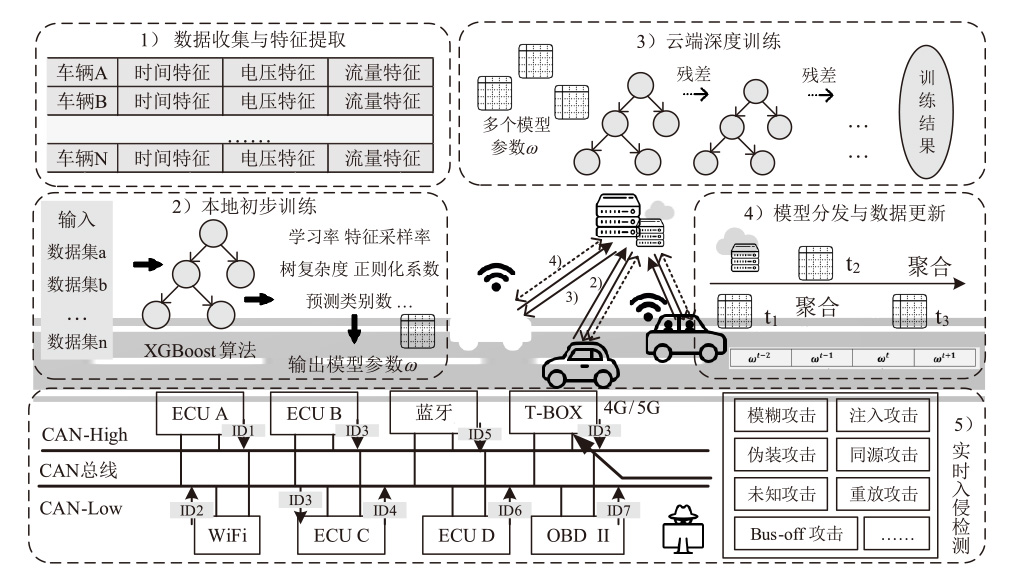
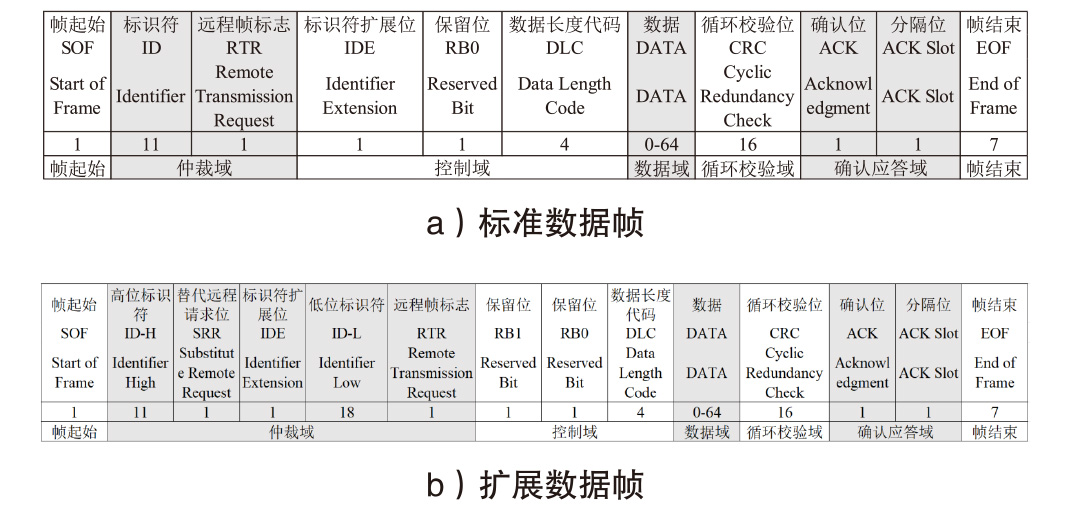
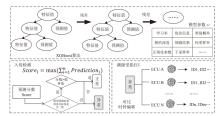
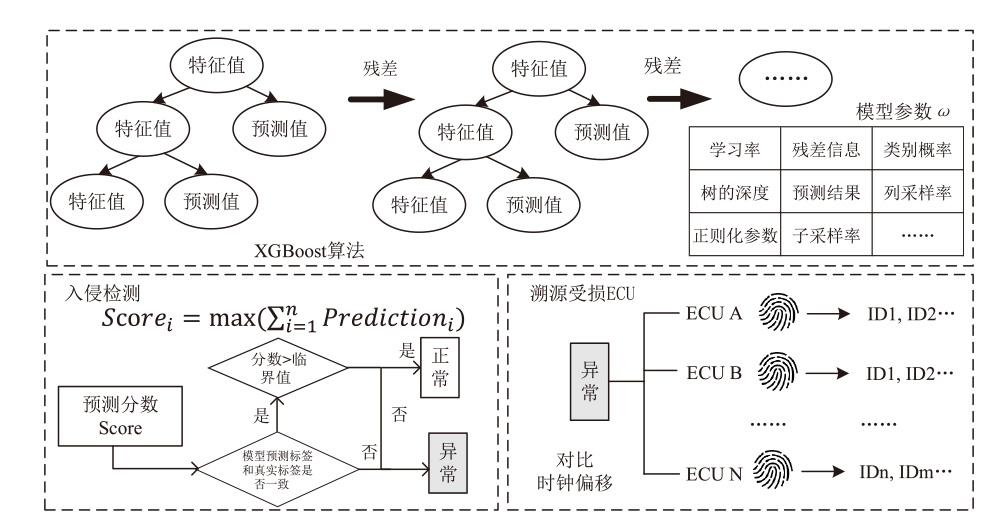
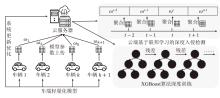
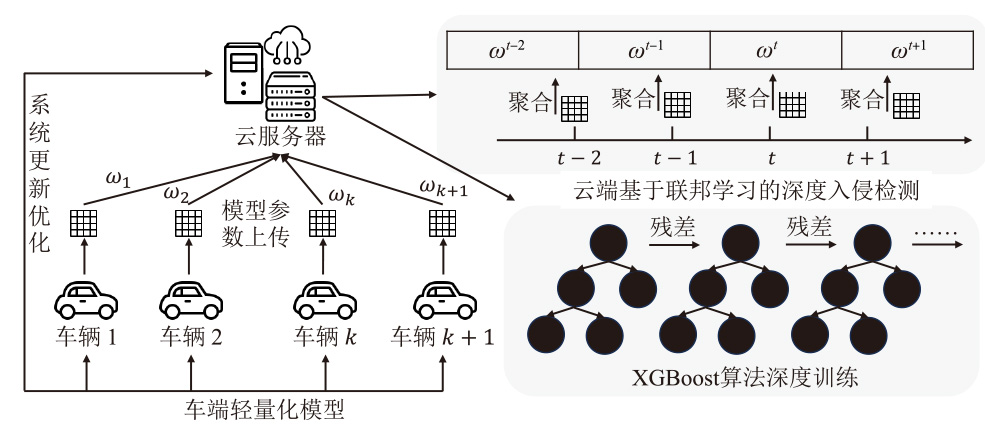
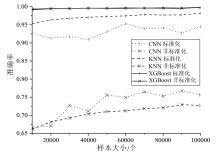
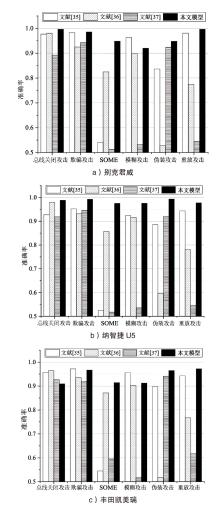
智能汽车已经成为人们日常出行必不可少的交通工具。控制器局域网总线(CAN)作为智能汽车内部的核心通信协议总线,其安全问题备受关注。CAN总线因通信接口访问控制薄弱、数据交互缺乏认证、报文无源/目的地址等因素使车辆易受到恶意攻击。车内网关、防火墙等安全方案受车内带宽和计算资源的限制,难以搭载强大的加密认证算法,防护能力受限。而现有的基于单类旁路特征(电压、时钟或数据流等)的入侵检测系统(IDS),检测攻击能力受限,如基于时钟偏斜的IDS无法检测非周期性攻击。为此,文章提出一种基于联邦学习的智能汽车CAN总线入侵检测系统。车端收集多维度特征数据进行轻量化训练后将参数传到云端,云端通过异步横向联邦学习结构收集不同车辆传过来的参数,用极端梯度提升算法开展深度训练,并将训练好的模型参数传给车端,车端进行检测并溯源。在3款不同品牌真实车辆上的实验结果表明,该系统能够高精度检测6种典型的攻击类型,包括总线关闭、欺骗、同源、模糊、伪装和重放攻击,平均检测时延为0.0987ms。
中图分类号:
引用本文
荀毅杰, 崔嘉容, 毛伯敏, 秦俊蔓. 基于联邦学习的智能汽车CAN总线入侵检测系统[J]. 信息网络安全, 2025, 25(6): 872-888.
XUN Yijie, CUI Jiarong, MAO Bomin, QIN Junman. Intrusion Detection System for the Controller Area Network Bus of Intelligent Vehicles Based on Federated Learning[J]. Netinfo Security, 2025, 25(6): 872-888.
表1
多车型6种攻击入侵检测评估结果
| 车辆 | 指标 | 攻击类型 | |||||
|---|---|---|---|---|---|---|---|
| 总线 关闭 | 欺骗 | SOME | 模糊(Fuzzy) | 伪装(Masquerade) | 重放(Replay) | ||
| 别克 君威 | 准确率 | 0.9966 | 0.9856 | 0.9482 | 0.9199 | 0.9479 | 0.9966 |
| 精确率 | 1 | 0.9756 | 0.9090 | 0.8651 | 0.9090 | 1 | |
| 召回率 | 0.9932 | 0.9960 | 0.9960 | 0.9949 | 0.9955 | 0.9960 | |
| FPR | 0 | 0.0249 | 0.0997 | 0.1551 | 0.0997 | 0 | |
| FNR | 0.0068 | 0.0040 | 0.0040 | 0.0051 | 0.0045 | 0.0040 | |
| 纳智捷U5 | 准确率 | 0.9882 | 0.9923 | 0.9748 | 0.9752 | 0.9931 | 0.9773 |
| 精确率 | 0.9839 | 0.9903 | 0.9584 | 0.9541 | 0.9887 | 0.9593 | |
| 召回率 | 0.9927 | 0.9943 | 0.9927 | 0.9984 | 0.9916 | 0.9968 | |
| FPR | 0.0162 | 0.0097 | 0.0431 | 0.0479 | 0.0114 | 0.0422 | |
| FNR | 0.0073 | 0.0057 | 0.0073 | 0.0016 | 0.0024 | 0.0032 | |
| 丰田 凯美瑞 | 准确率 | 0.9091 | 0.9666 | 0.9140 | 0.9123 | 0.9649 | 0.9718 |
| 精确率 | 0.8449 | 0.9320 | 0.8541 | 0.8517 | 0.9350 | 0.9496 | |
| 召回率 | 1 | 0.9979 | 0.9986 | 0.9993 | 0.9993 | 0.9972 | |
| FPR | 0.0918 | 0.0646 | 0.1706 | 0.0695 | 0.0695 | 0.0530 | |
| FNR | 0 | 0.0021 | 0.0014 | 0.0007 | 0 | 0.0028 | |
| [1] | Editorial Department of China Journal of Highway and Transport. Review on China’s Automotive Engineering Research Progress: 2023[J]. China Journal of Highway and Transport, 2023, 36(11): 1-192. |
|
《中国公路学报》编辑部. 中国汽车工程学术研究综述·2023[J]. 中国公路学报, 2023, 36(11): 1-192.
doi: 10.19721/j.cnki.1001-7372.2023.11.001 |
|
| [2] | MILLER C, VALASEK C. Remote Exploitation of an Unaltered Passenger Vehicle[J]. Black Hat USA, 2015, (S91): 1-91. |
| [3] | BARAN G. Vulnerabilities in Skoda & Volkswagen Cars Let Hackers Remotely Track Users[EB/OL]. (2024-12-12)[2025-02-23]. https://cybersecuritynews.com/vulnerabilities-skoda-volkswagen-cars. |
| [4] | YAN Minrui, LI Jiahao. Security Research on Mercedes-Benz: From Hardware to Car Control[J]. Black Hat USA, 2020, 2020: 1-81. |
| [5] | GB/T 38628-2020 Information Security Technology Cybersecurity Guide for Automotive Electronics Systems[S]. Beijing: Standards Press of China, 2020. |
| GB/T 38628-2020 信息安全技术汽车电子系统网络安全指南[S]. 北京: 中国标准出版社, 2020. | |
| [6] | GB/T 45181-2024 Security-Related Misbehavior Detection Mechanism for Connected Vehicles[S]. Beijing: Standards Press of China, 2024. |
| GB/T 45181-2024 车联网网络安全异常行为检测机制[S]. 北京: 中国标准出版社, 2024. | |
| [7] | JOHANSSON K H, TÖRNGREN M, NIELSEN L. Vehicle Applications of Controller Area Network[M]. Boston: Birkhäuser Boston, 2005. |
| [8] | DU Xinying, HE Mingshu, WANG Xiaojuan. A Feature Fusion-Based Controller Area Network Intrusion Detection Method[J]. Journal of Beijing University of Posts and Telecommunications, 2025, 48(2): 1-7. |
| 杜欣颖, 何明枢, 王小娟. 基于特征融合的控制器局域网入侵检测方法[J]. 北京邮电大学学报, 2025, 48(2): 1-7. | |
| [9] | CAI Zhiqiang, WANG Aohui, ZHANG Wenkai. 0-Days & Mitigations: Roadways to Exploit and Secure Connected BMW Cars[J]. Black Hat USA, 2019, 2019(39): 6-37. |
| [10] | KIM J H, SEO S H, HAI N T, et al. Gateway Framework for In-Vehicle Networks Based on CAN, FlexRay, and Ethernet[J]. IEEE transactions on vehicular technology, 2014, 64(10): 4472-4486. |
| [11] | WANG Wenwei, GUO Kaidi, CAO Wanke, et al. Review of Electrical and Electronic Architectures for Autonomous Vehicles: Topologies, Networking and Simulators[J]. Automotive Innovation, 2024, 7(1): 82-101. |
| [12] | LENARD T, BOLBOACA R. A Statefull Firewall and Intrusion Detection System Enforced with Secure Logging for Controller Area Network[C]// ACM. Proceedings of the 2021 European Interdisciplinary Cybersecurity Conference. New York: ACM, 2021: 39-45. |
| [13] | LUO Feng, HOU Shuo. Security Mechanisms Design of Automotive Gateway Firewall[R]. Detroit: SAE International, No. 2019-01-0481, 2019. |
| [14] | RATHORE M S, POONGODI M, SAURABH P, et al. A Novel Trust-Based Security and Privacy Model for Internet of Vehicles Using Encryption and Steganography[J]. Computers and Electrical Engineering, 2022, 102: 1-18. |
| [15] | AKIB A, ANIKA A, MOUKAHAL L, et al. Security Assessment of In-Vehicle Communication Protocols[J]. Vehicular Communications, 2023, 44: 1-20. |
| [16] | CHO K T, SHIN K G. Fingerprinting Electronic Control Units for Vehicle Intrusion Detection[C]// USENIX. 25th USENIX Security Symposium (USENIX Security 16). Berkeley: USENIX, 2016: 911-927. |
| [17] | YOUNG C, OLUFOWOBI H, BLOOM G, et al. Automotive Intrusion Detection Based on Constant can Message Frequencies across Vehicle Driving Modes[C]// ACM. Proceedings of the ACM Workshop on Automotive Cybersecurity. New York: ACM, 2019: 9-14. |
| [18] | TAYLOR A, JAPKOWICZ N, LEBLANC S. Frequency-Based anomaly Detection for the Automotive CAN Bus[C]// IEEE. 2015 World Congress on Industrial Control Systems Security (WCICSS). New York: IEEE, 2015: 45-49. |
| [19] | CHOI W, JOO K, JO H J, et al. VoltageIDS: Low-Level Communication Characteristics for Automotive Intrusion Detection System[J]. IEEE Transactions on Information Forensics and Security, 2018, 13(8): 2114-2129. |
| [20] | KNEIB M, HUTH C. Scission: Signal Characteristic-Based Sender Identification and Intrusion Detection in Automotive Networks[C]// ACM. 2018 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2018: 787-800. |
| [21] | WU Wufei, HUANG Yizhi, KURACHI R, et al. Sliding Window Optimized Information Entropy Analysis Method for Intrusion Detection on In-Vehicle Networks[J]. IEEE Access, 2018, 6: 45233-45245. |
| [22] | LI Yang, MOUBAYED A, HAMIEH I, et al. Tree-Based Intelligent Intrusion Detection System in Internet of Vehicles[C]// IEEE. 2019 IEEE Global Communications Conference (GLOBECOM). New York: IEEE, 2019: 1-6. |
| [23] | SONG H M, WOO J, KIM H K. In-Vehicle Network Intrusion Detection Using Deep Convolutional Neural Network[J]. Vehicular Communications, 2020, 21: 1-13. |
| [24] | DAVIS R I, BURNS A, BRIL R J, et al. Controller Area Network (CAN) Schedulability Analysis: Refuted, Revisited and Revised[J]. Real-Time Systems, 2007, 35: 239-272. |
| [25] | KUANG Boyu, LI Yuze, GU Fangming, et al. Review of Internet of Vehicle Security Research: Threats, Countermeasures, and Future Prospects[J]. Journal of Computer Research and Development, 2023, 60(10): 2304-2321. |
| 况博裕, 李雨泽, 顾芳铭, 等. 车联网安全研究综述:威胁、对策与未来展望[J]. 计算机研究与发展, 2023, 60(10): 2304-2321. | |
| [26] | ZHOU Chuanxin, SUN Yi, WANG Degang, et al. Survey of Federated Learning Research[J]. Chinese Journal of Network and Information Security, 2021, 7(5): 77-92. |
| 周传鑫, 孙奕, 汪德刚, 等. 联邦学习研究综述[J]. 网络与信息安全学报, 2021, 7(5): 77-92. | |
| [27] | IEHIRA K, INOUE H, ISHIDA K. Spoofing Attack Using Bus-Off Attacks against a Specific ECU of the CAN Bus[C]// IEEE. 2018 15th IEEE Annual Consumer Communications & Networking Conference (CCNC). New York: IEEE, 2018: 1-4. |
| [28] | YANG Yun, DUAN Zongtao, TEHRANIPOOR M. Identify a Spoofing Attack on an In-Vehicle CAN Bus Based on the Deep Features of an ECU Fingerprint Signal[J]. Smart Cities, 2020, 3(1): 17-30. |
| [29] | MCMAHAN B, MOORE E, RAMAGE D, et al. Communication-Efficient Learning of Deep Networks from Decentralized Data[C]// PMLR. Proceedings of the 20th International Conference on Artificial Intelligence and Statistics. New York: PMLR, 2017: 1273-1282. |
| [30] | LI Tian, SAHU A K, ZAHEER M, et al. Federated Optimization in Heterogeneous Networks[J]. Proceedings of Machine Learning and Systems, 2020, 2: 429-450. |
| [31] | XIE Cong, KOYEJO S, GUPTA I. Asynchronous Federated Optimization[EB/OL]. (2019-04-10)[2025-02-23]. https://arxiv.org/abs/1903.03934. |
| [32] | MIRZAEE P H, SHOJAFAR M, CRUICKSHANK H, et al. CHFL: A Collaborative Hierarchical Federated Intrusion Detection System for Vehicular Networks[C]// IEEE. 2022 IEEE Symposium on Computers and Communications (ISCC). New York: IEEE, 2022: 1-7. |
| [33] | DRISS M, ALMOMANI I, HUMA Z E, et al. A Federated Learning Framework for Cyberattack Detection in Vehicular Sensor Networks[J]. Complex & Intelligent Systems, 2022, 8(5): 4221-4235. |
| [34] | MUZUN A, JAVED A, RANA O. A Robust Multi-Stage Intrusion Detection System for In-Vehicle Network Security Using Hierarchical Federated Learning[J]. Vehicular Communications, 2024, 49: 1-15. |
| [35] | LEE S, CHOI W, JO H J, et al. ErrIDS: An Enhanced Cumulative Timing Error-Based Automotive Intrusion Detection System[J]. IEEE Transactions on Intelligent Transportation Systems, 2023, 24(11): 12406-12421. |
| [36] | HOSSAIN M D, INOUE H, OCHIAI H, et al. LSTM-Based Intrusion Detection System for In-Vehicle Can Bus Communications[J]. IEEE Access, 2020, 8: 185489-185502. |
| [37] | SCHELL O, KNEIB M. VALID: Voltage-Based Lightweight Intrusion Detection for the Controller Area Network[C]// IEEE. 2020 IEEE 19th International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom). New York: IEEE, 2021: 225-232. |
| [1] | 邓东上, 王伟业, 张卫东, 吴宣够. 基于模型特征方向的分层个性化联邦学习框架[J]. 信息网络安全, 2025, 25(6): 889-897. |
| [2] | 朱率率, 刘科乾. 基于掩码的选择性联邦蒸馏方案[J]. 信息网络安全, 2025, 25(6): 920-932. |
| [3] | 金增旺, 江令洋, 丁俊怡, 张慧翔, 赵波, 方鹏飞. 工业控制系统安全研究综述[J]. 信息网络安全, 2025, 25(3): 341-363. |
| [4] | 刘晨飞, 万良. 基于时空图神经网络的CAN总线入侵检测方法[J]. 信息网络安全, 2025, 25(3): 478-493. |
| [5] | 李佳东, 曾海涛, 彭莉, 汪晓丁. 一种保护数据隐私的匿名路由联邦学习框架[J]. 信息网络安全, 2025, 25(3): 494-503. |
| [6] | 徐茹枝, 仝雨蒙, 戴理朋. 基于异构数据的联邦学习自适应差分隐私方法研究[J]. 信息网络安全, 2025, 25(1): 63-77. |
| [7] | 刘联海, 黎汇业, 毛冬晖. 基于图像凸包特征的CBAM-CNN网络入侵检测方法[J]. 信息网络安全, 2024, 24(9): 1422-1431. |
| [8] | 郭倩, 赵津, 过弋. 基于分层聚类的个性化联邦学习隐私保护框架[J]. 信息网络安全, 2024, 24(8): 1196-1209. |
| [9] | 张浩, 谢大智, 胡云晟, 叶骏威. 基于半监督学习的网络异常检测研究综述[J]. 信息网络安全, 2024, 24(4): 491-508. |
| [10] | 江荣, 刘海天, 刘聪. 基于集成学习的无监督网络入侵检测方法[J]. 信息网络安全, 2024, 24(3): 411-426. |
| [11] | 薛茗竹, 胡亮, 王明, 王峰. 基于联邦学习和区块链技术的TAP规则处理系统[J]. 信息网络安全, 2024, 24(3): 473-485. |
| [12] | 冯光升, 蒋舜鹏, 胡先浪, 马明宇. 面向物联网的入侵检测技术研究新进展[J]. 信息网络安全, 2024, 24(2): 167-178. |
| [13] | 林怡航, 周鹏远, 吴治谦, 廖勇. 基于触发器逆向的联邦学习后门防御方法[J]. 信息网络安全, 2024, 24(2): 262-271. |
| [14] | 金志刚, 丁禹, 武晓栋. 融合梯度差分的双边校正联邦入侵检测算法[J]. 信息网络安全, 2024, 24(2): 293-302. |
| [15] | 孙红哲, 王坚, 王鹏, 安雨龙. 基于Attention-BiTCN的网络入侵检测方法[J]. 信息网络安全, 2024, 24(2): 309-318. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||