信息网络安全 ›› 2024, Vol. 24 ›› Issue (8): 1173-1183.doi: 10.3969/j.issn.1671-1122.2024.08.004
基于多尺度特征融合重建学习的深度伪造人脸检测算法
- 1.南京理工大学计算机科学与工程学院,南京 210094
2.鹿邑县公安局视频侦查大队,周口 477299
3.中国科学院自动化研究所,北京 100190
-
收稿日期:2024-05-11出版日期:2024-08-10发布日期:2024-08-22 -
通讯作者:胡晰远huxy@njust.edu.cn -
作者简介:许楷文(1996—),男,江苏,博士研究生,主要研究方向为深度伪造检测|周翊超(1983—),男,山东,副研究员,博士,主要研究方向为多模态信息融合与处理|谷文权(1982—),男,河南,主要研究方向为视频侦查与影像物证检验|陈晨(1982—),女,河南,副研究员,博士,主要研究方向为机器学习理论、流形学习|胡晰远(1984—),男,浙江,教授,博士,主要研究方向为人工智能理论及其应用、图像与视频处理 -
基金资助:国家自然科学基金(62172227)
A Multi-Scale Feature Fusion Deepfake Detection Algorithm Based on Reconstruction Learning
XU Kaiwen1, ZHOU Yichao1, GU Wenquan2, CHEN Chen3, HU Xiyuan1( )
)
- 1. School of Computer Science and Engineering, Nanjing University of Science and Technology, Nanjing 210094, China
2. Luyi County Public Security Bureau Video Investigation Brigade, Zhoukou 477299, China
3. Institute of Automation, Chinese Academy of Sciences, Beijing 100190, China
-
Received:2024-05-11Online:2024-08-10Published:2024-08-22
摘要:
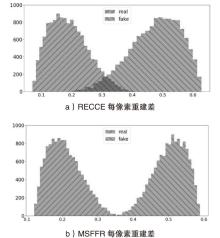
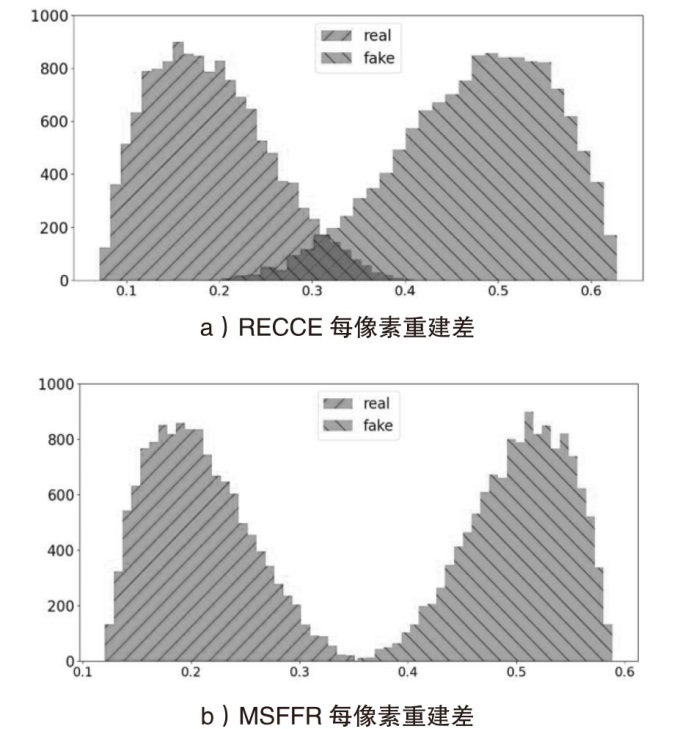
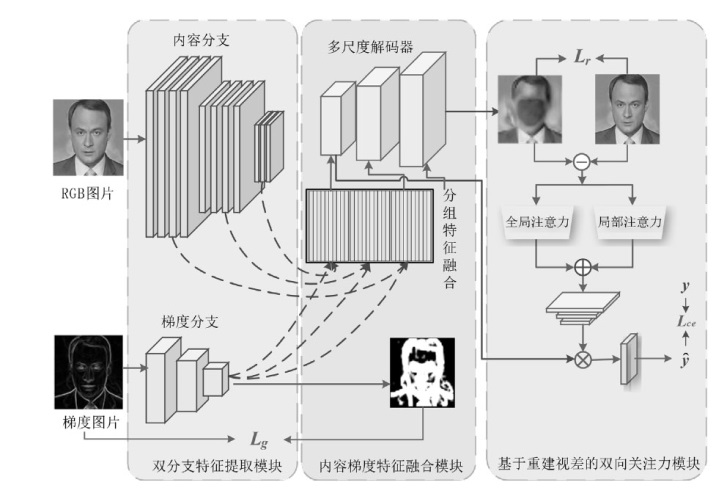
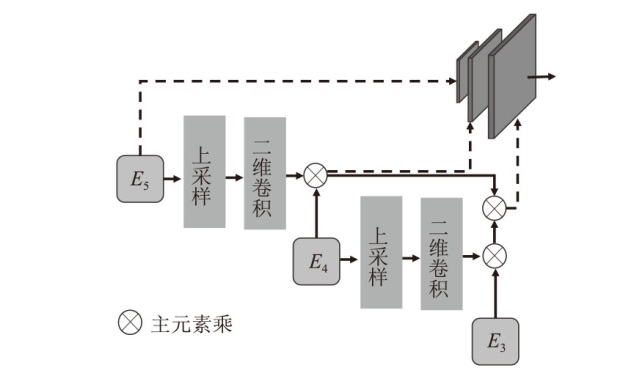
随着深度伪造技术的快速发展,针对深度伪造人脸的检测已经成为计算机视觉领域的研究热点。虽然现有的基于噪声、局部纹理或频率特征的检测方法能够在特定场景中表现出良好的检测效果,但这些方法缺乏对人脸细粒度表征特征的深入挖掘,限制了其泛化能力。为了解决上述问题,文章提出了一种新型的基于多尺度特征融合重建的分类网络模型MSFFR,该网络模型从重建学习的角度学习挖掘人脸细粒度内容和梯度表征特征信息,并采用多尺度特征融合的方式实现伪造人脸的检测,通过融合这两种信息来识别伪造面孔。文章提出的模型包含3个创新模块,设计了双分支特征提取模块,用于揭示真实人脸与伪造人脸之间的分布差异;提出了细粒度内容和梯度特征融合模块,用于探索挖掘人脸细粒度内容特征与梯度特征之间的相关性;引入了基于重建视差的双向注意力模块,有效地指导模型对融合后的特征进行分类。在大规模基准数据集上进行的广泛实验表明,与现有技术相比,文章提出的方法在检测性能方面具有显著提高,尤其是在泛化能力方面表现出色。
中图分类号:
引用本文
许楷文, 周翊超, 谷文权, 陈晨, 胡晰远. 基于多尺度特征融合重建学习的深度伪造人脸检测算法[J]. 信息网络安全, 2024, 24(8): 1173-1183.
XU Kaiwen, ZHOU Yichao, GU Wenquan, CHEN Chen, HU Xiyuan. A Multi-Scale Feature Fusion Deepfake Detection Algorithm Based on Reconstruction Learning[J]. Netinfo Security, 2024, 24(8): 1173-1183.
表1
域内对比实验
| 模型 | FF++(LQ) | FF++(HQ) | WildDeepfake | Celeb-DF | ||||
|---|---|---|---|---|---|---|---|---|
| Acc | AUC | Acc | AUC | Acc | AUC | Acc | AUC | |
| ADD-Net[ | 87.50% | 91.01% | 96.78% | 97.74% | 76.25% | 86.17% | 96.93% | 99.55% |
| SCL[ | 89.00% | 92.40% | 96.69% | 99.30% | — | — | — | — |
| MADD[ | 88.69% | 90.40% | 97.60% | 99.29% | 82.62% | 90.71% | 97.92% | 99.94% |
| F3Net[ | 90.43% | 93.30% | 97.52% | 98.10% | 80.66% | 87.53% | 95.95% | 98.93% |
| PEL[ | 90.52% | 94.28% | 97.63% | 99.32% | 84.14% | 91.62% | — | — |
| RECCE[ | 91.03% | 95.02% | 97.06% | 99.32% | 83.25% | 92.02% | 98.59% | 99.94% |
| ITA-SIA[ | 90.23% | 93.45% | 97.64% | 99.35% | 83.95% | 91.34% | 98.48% | 99.96% |
| SFDG[ | 92.28% | 95.98% | 98.19% | 99.53% | 84.41% | 92.57% | 99.22% | 99.96% |
| MRL[ | 91.81% | 96.18% | 93.82% | 98.27% | — | — | — | 99.96% |
| SI-Net[ | 87.90% | 90.53% | 96.85% | 99.08% | 84.08% | 91.33% | — | — |
| MRE-Net[ | 91.60% | 96.55% | 97.76% | 99.57% | 85.61% | 91.23% | — | — |
| DisGRL[ | 91.27% | 95.19% | 97.69% | 99.48% | 84.53% | 93.27% | 98.71% | 99.91% |
| MSFFR | 93.73% | 97.12% | 98.43% | 99.99% | 86.76% | 95.27% | 99.99% | 99.99% |
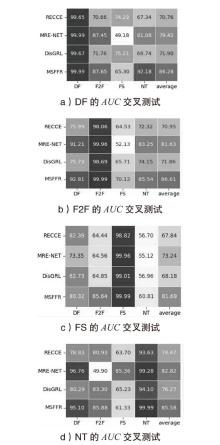
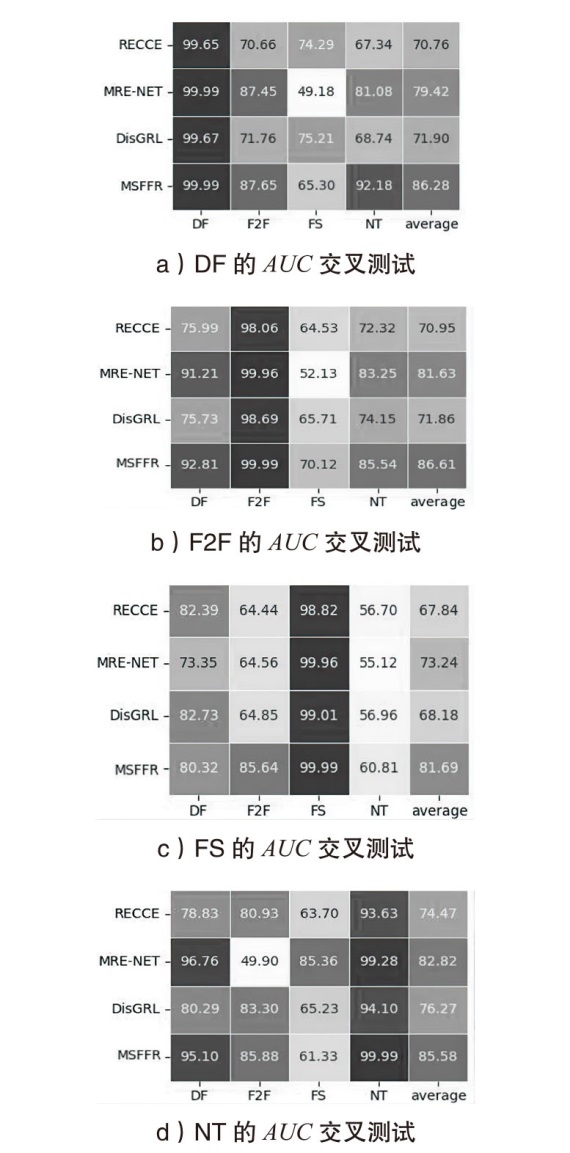
表2
跨数据集泛化性实验
| 训练集 | 模型 | 测试集 | |||||||
|---|---|---|---|---|---|---|---|---|---|
| Celeb-DF | DFD | WildDeepfake | DFDC | ||||||
| AUC | EER↓ | AUC | EER↓ | AUC | EER↓ | AUC | EER↓ | ||
| FF++ | ADD-Net | 57.83% | 0.444 | 57.16% | 0.453 | 54.21% | 0.462 | 51.60% | 0.548 |
| MADD | 68.64% | 0.371 | 74.19% | 0.327 | 65.65% | 0.397 | 63.02% | 0.410 | |
| F3Net | 67.95% | 0.368 | 69.50% | 0.354 | 60.49% | 0.434 | 57.87% | 0.442 | |
| PEL | 69.18% | 0.357 | 75.86% | 0.308 | 67.39% | 0.383 | 63.31% | 0.404 | |
| RECCE | 68.71% | 0.357 | — | — | 64.31% | 0.405 | 69.06% | 0.360 | |
| SFDG | 75.83% | 0.303 | 88.00% | 0.197 | 69.27% | 0.377 | 73.64% | 0.337 | |
| IID[ | 83.80% | 0.248 | 93.92% | 0.140 | — | — | 81.23% | 0.268 | |
| DisGRL | 70.03% | 0.342 | — | — | 66.73% | 0.392 | 70.89% | 0.342 | |
| MSFFR | 91.20% | 0.127 | 94.25% | 0.098 | 87.09% | 0.195 | 86.53% | 0.162 | |
| [1] | GOODFELLOW I, POUGET-ABADIE J, MIRZA M, et al. Generative Adversarial Networks[J]. Communications of the ACM, 2020, 63(11): 139-144. |
| [2] | KINGMA D P, WELLING M. An Introduction to Variational Autoencoders[J]. Foundations and Trends® in Machine Learning, 2019, 12(4): 307-392. |
| [3] | PENG Shufan, CAI Manchun, LIU Xiaowen, et al. Deepfake Detection Algorithm Based on Image Fine-Grained Features[J]. Netinfo Security, 2022, 22(11): 77-84. |
| 彭舒凡, 蔡满春, 刘晓文, 等. 基于图像细粒度特征的深度伪造检测算法[J]. 信息网络安全, 2022, 22(11): 77-84. | |
| [4] | ZI Bojia, CHANG Minghao, CHEN Jingjing, et al. WildDeepfake: A Challenging Real-World Dataset for Deepfake Detection[C]// ACM. Proceedings of the 28th ACM International Conference on Multimedia. New York: ACM, 2020: 2382-2390. |
| [5] | GU Qiqi, CHEN Shen, YAO Taiping, et al. Exploiting Fine-Grained Face Forgery Clues via Progressive Enhancement Learning[C]// AAAI. Proceedings of the AAAI Conference on Artificial Intelligence. Menlo Park: AAAI, 2022, 36(1): 735-743. |
| [6] | GU Zhihao, CHEN Yang, YAO Taiping, et al. Delving into the Local: Dynamic Inconsistency Learning for DeepFake Video Detection[C]// AAAI. Proceedings of the AAAI Conference on Artificial Intelligence. Menlo Park: AAAI, 2022, 36(1): 744-752. |
| [7] | LI Jiaming, XIE Hongtao, LI Jiahong, et al. Frequency-Aware Discriminative Feature Learning Supervised by Single-Center Loss for Face Forgery Detection[C]// IEEE. 2021 IEEE/CVF Conference on Computer Vision and Pattern Recognition (CVPR). New York: IEEE, 2021: 6458-6467. |
| [8] | CAO Junyi, MA Chao, YAO Taiping, et al. End-to-End Reconstruction-Classification Learning for Face Forgery Detection[C]// IEEE. 2022 IEEE/CVF Conference on Computer Vision and Pattern Recognition (CVPR). New York: IEEE, 2022: 4113-4122. |
| [9] | CHOI Y, CHOI M, KIM M, et al. StarGAN: Unified Generative Adversarial Networks for Multi-Domain Image-to-Image Translation[C]// IEEE. 2018 IEEE/CVF Conference on Computer Vision and Pattern Recognition. New York: IEEE, 2018: 8789-8797. |
| [10] | ABDAL R, QIN Yipeng, WONKA P. Image2StyleGAN: How to Embed Images into the StyleGAN Latent Space?[C]// IEEE. 2019 IEEE/CVF International Conference on Computer Vision (ICCV). New York: IEEE, 2019: 4432-4441. |
| [11] | ZHAO Hanqing, WEI Tianyi, ZHOU Wenbo, et al. Multi-Attentional Deepfake Detection[C]// IEEE. 2021 IEEE/CVF Conference on Computer Vision and Pattern Recognition (CVPR). New York: IEEE, 2021: 2185-2194. |
| [12] | LI Jiaming, XIE Hongtao, LI Jiahong, et al. Frequency-Aware Discriminative Feature Learning Supervised by Single-Center Loss for Face Forgery Detection[C]// IEEE. 2021 IEEE/CVF Conference on Computer Vision and Pattern Recognition (CVPR). New York: IEEE, 2021: 6458-6467. |
| [13] | ZHAO Tianchen, XU Xiang, XU Mingze, et al. Learning Self-Consistency for Deepfake Detection[C]// IEEE. 2021 IEEE/CVF International Conference on Computer Vision (ICCV). New York: IEEE, 2021: 15023-15033. |
| [14] | DONG Shichao, WANG Jin, LIANG Jianjun, et al. Explaining Deepfake Detection by Analysing Image Matching[C]// Springer. European Conference on Computer Vision. Heidelberg: Springer, 2022: 18-35. |
| [15] | KHALID H, WOO S S. OC-FakeDect: Classifying Deepfakes Using One-Class Variational Autoencoder[C]// IEEE. 2020 IEEE/CVF Conference on Computer Vision and Pattern Recognition Workshops (CVPRW). New York: IEEE, 2020: 656-657. |
| [16] | TAN Mingxing, LE Q V. EfficientNet: Rethinking Model Scaling for Convolutional Neural Networks[C]// PMLR. International Conference on Machine Learning. New York: PMLR, 2019: 6105-6114. |
| [17] | ROSSLER A, COZZOLINO D, VERDOLIVA L, et al. FaceForensics++: Learning to Detect Manipulated Facial Images[C]// IEEE. 2019 IEEE/CVF International Conference on Computer Vision (ICCV). New York: IEEE, 2019: 1-11. |
| [18] | DOLHANSKY B, BITTON J, PFLAUM B, et al. The DeepFake Detection Challenge (DFDC) Dataset[EB/OL]. (2020-06-12)[2024-04-30]. https://doi.org/10.48550/arXiv.2006.07397. |
| [19] | LI Yuezun, YANG Xin, SUN Pu, et al. Celeb-DF: A Large-Scale Challenging Dataset for DeepFake Forensics[C]// IEEE. 2020 IEEE/CVF Conference on Computer Vision and Pattern Recognition (CVPR). New York: IEEE, 2020: 3207-3216. |
| [20] | DUFOUR N, GULLY A. Contributing Data to Deepfake Detection Research[EB/OL]. [2024-04-30]. https://ai.googleblog.com/2019/09/contributing-data-to-deepfake-detection.html. |
| [21] | QIAN Yuyang, YIN Guojun, SHENG Lu, et al. Thinking in Frequency: Face Forgery Detection by Mining Frequency-Aware Clues[C]// Springer. European Conference on Computer Vision. Heidelberg: Springer, 2020: 86-103. |
| [22] | SUN Ke, LIU Hong, YAO Taiping, et al. An Information Theoretic Approach For Attention-Driven Face Forgery Detection[C]// Springer. European Conference on Computer Vision. Heidelberg: Springer, 2022: 111-127. |
| [23] | WANG Yuan, YU Kun, CHEN Chen, et al. Dynamic Graph Learning with Content-Guided Spatial-Frequency Relation Reasoning for Deepfake Detection[C]// IEEE. 2023 IEEE/CVF Conference on Computer Vision and Pattern Recognition (CVPR). New York: IEEE, 2023: 7278-7287. |
| [24] | YANG Ziming, LIANG Jian, XU Yuting, et al. Masked Relation Learning for DeepFake Detection[J]. IEEE Transactions on Information Forensics and Security, 2023, 18: 1696-1708. |
| [25] | WANG Jian, DU Xiaoyu, CHENG Yu, et al. SI-Net: Spatial Interaction Network for Deepfake Detection[J]. Multimedia Systems, 2023, 29(5): 3139-3150. |
| [26] | PANG Guilin, ZHANG Baopeng, TENG Zhu, et al. MRE-Net: Multi-Rate Excitation Network for Deepfake Video Detection[J]. IEEE Transactions on Circuits and Systems for Video Technology, 2023, 33(8): 3663-3676. |
| [27] | SHI Zenan, CHEN Haipeng, CHEN Long, et al. Discrepancy-Guided Reconstruction Learning for Image Forgery Detection[EB/OL]. (2023-04-26)[2024-04-30]. https://arxiv.org/abs/2304.13349v2. |
| [28] | HUANG Baojin, WANG Zhongyuan, YANG Jifan, et al. Implicit Identity Driven Deepfake Face Swapping Detection[C]// IEEE. Proceedings of the IEEE/CVF Conference on Computer Vision and Pattern Recognition. New York: IEEE, 2023: 4490-4499. |
| [1] | 秦元庆, 董泽阳, 韩汶君. 一种基于任务和可信等级的数控网络跨域互操作方法[J]. 信息网络安全, 2024, 24(8): 1143-1151. |
| [2] | 杜晔, 田晓清, 李昂, 黎妹红. 基于改进鲸鱼算法优化SVM的软件缺陷检测方法[J]. 信息网络安全, 2024, 24(8): 1152-1162. |
| [3] | 夏辉, 钱祥运. 基于特征空间相似的隐形后门攻击[J]. 信息网络安全, 2024, 24(8): 1163-1172. |
| [4] | 徐茹枝, 张凝, 李敏, 李梓轩. 针对恶意软件的高鲁棒性检测模型研究[J]. 信息网络安全, 2024, 24(8): 1184-1195. |
| [5] | 郭倩, 赵津, 过弋. 基于分层聚类的个性化联邦学习隐私保护框架[J]. 信息网络安全, 2024, 24(8): 1196-1209. |
| [6] | 张兴兰, 李登祥. 基于Grover量子搜索算法的MD5碰撞攻击模型[J]. 信息网络安全, 2024, 24(8): 1210-1219. |
| [7] | 孙中岫, 彭诚, 范伟. 基于无证书签名的5G系统广播消息身份认证协议[J]. 信息网络安全, 2024, 24(8): 1220-1230. |
| [8] | 陈昊然, 刘宇, 陈平. 基于大语言模型的内生安全异构体生成方法[J]. 信息网络安全, 2024, 24(8): 1231-1240. |
| [9] | 郭钰铮, 郭春, 崔允贺, 李显超. 基于随机博弈网的窃密木马诱导式博弈模型[J]. 信息网络安全, 2024, 24(8): 1241-1251. |
| [10] | 赵伟, 任潇宁, 薛吟兴. 基于集成学习的成员推理攻击方法[J]. 信息网络安全, 2024, 24(8): 1252-1264. |
| [11] | 王文涛, 刘彦飞, 毛博文, 余成波. 面向多维属性融合的加权网络结构洞节点发现算法[J]. 信息网络安全, 2024, 24(8): 1265-1276. |
| [12] | 邢长友, 王梓澎, 张国敏, 丁科. 基于预训练Transformers的物联网设备识别方法[J]. 信息网络安全, 2024, 24(8): 1277-1290. |
| [13] | 吕秋云, 周凌飞, 任一支, 周士飞, 盛春杰. 一种全生命周期可控的公共数据共享方案[J]. 信息网络安全, 2024, 24(8): 1291-1305. |
| [14] | 黄旺旺, 周骅, 王代强, 赵麒. 基于国密SM9的物联网可重构密钥安全认证协议设计[J]. 信息网络安全, 2024, 24(7): 1006-1014. |
| [15] | 张晓均, 张楠, 郝云溥, 王周阳, 薛婧婷. 工业物联网系统基于混沌映射三因素认证与密钥协商协议[J]. 信息网络安全, 2024, 24(7): 1015-1026. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||