信息网络安全 ›› 2024, Vol. 24 ›› Issue (5): 745-755.doi: 10.3969/j.issn.1671-1122.2024.05.008
一种带作弊识别的动态(t,n)门限量子秘密共享方案
- 陕西师范大学数学与统计学院,西安 710119
-
收稿日期:2023-10-17出版日期:2024-05-10发布日期:2024-06-24 -
通讯作者:关飞婷 E-mail:ftguan123@163.com -
作者简介:郭建胜(1979—),男,青海,副教授,博士,主要研究方向为密码学|关飞婷(1999—),女,山西,硕士研究生,主要研究方向为密码学|李志慧(1966—),女,陕西,教授,博士,主要研究方向为有限域和密码学 -
基金资助:国家自然科学基金(12071271)
A Dynamic (t,n) Threshold Quantum Secret Sharing Scheme with Cheating Identification
GUO Jiansheng, GUAN Feiting( ), LI Zhihui
), LI Zhihui
- School of Mathematics and Statistics, Shaanxi Normal University, Xi’an 710119, China
-
Received:2023-10-17Online:2024-05-10Published:2024-06-24 -
Contact:GUAN Feiting E-mail:ftguan123@163.com
摘要:
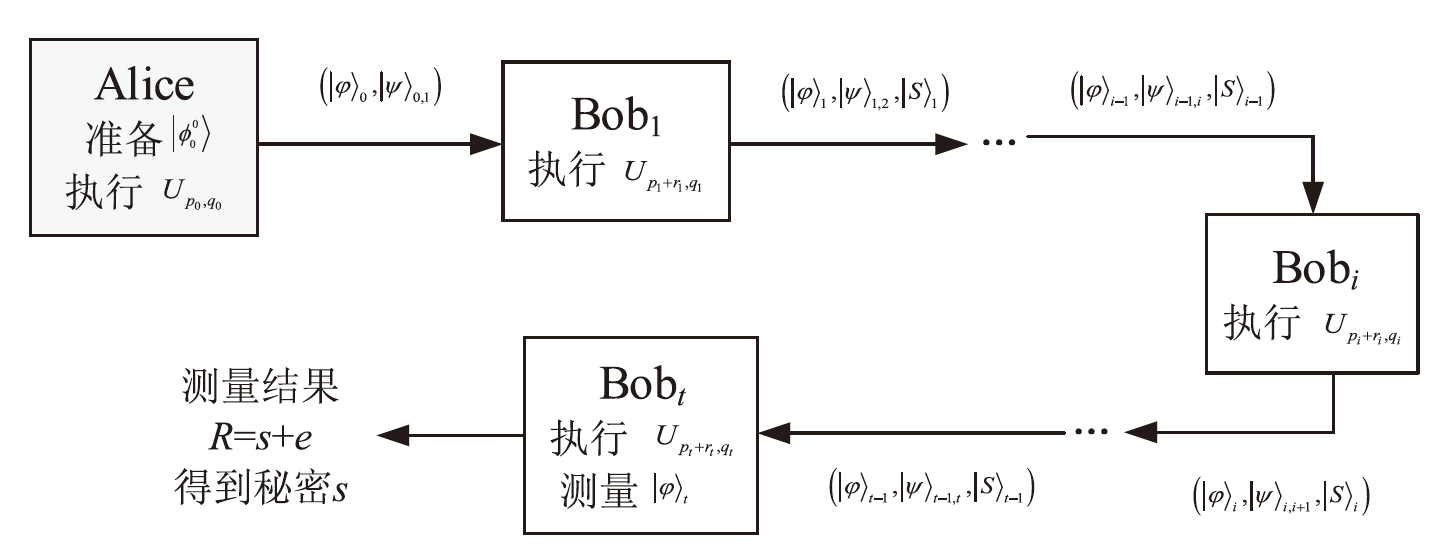
文章基于齐次线性反馈移位寄存器(Linear Feedback Shift Register,LFSR) 序列和d维单量子态提出了一种带作弊识别的动态(t,n)门限量子秘密共享方案。在该方案中,可信的分发者确定共享的秘密,并为参与者分配份额,参与者对传输中的粒子执行相应的酉操作来恢复秘密。在秘密重建阶段,通过执行量子态数字签名,不仅可以检测到作弊行为,还可以识别具体的作弊者并将其删除,最终参与者可以验证恢复秘密的正确性。该方案可以在不更改旧参与者份额的前提下,无需其他参与者的帮助便可实现参与者的动态更新。安全性分析表明,该方案能够抵抗常见的外部攻击和内部攻击。
中图分类号:
引用本文
郭建胜, 关飞婷, 李志慧. 一种带作弊识别的动态(t,n)门限量子秘密共享方案[J]. 信息网络安全, 2024, 24(5): 745-755.
GUO Jiansheng, GUAN Feiting, LI Zhihui. A Dynamic (t,n) Threshold Quantum Secret Sharing Scheme with Cheating Identification[J]. Netinfo Security, 2024, 24(5): 745-755.
表2
本文方案和现有方案的比较
| 文献[12]方案 | 文献[16]方案 | 文献[23]方案 | 文献[24]方案 | 本文 方案 | |
|---|---|---|---|---|---|
| 所用量子态 | d维 Bell态 | d维 Bell态 | d维 GHZ态 | d维 Bell态 | MUB |
| 动态 | 否 | 否 | 是 | 是 | 是 |
| 作弊识别 | 否 | 是 | 否 | 否 | 是 |
| 抵抗伪造 攻击 | 是 | 是 | 是 | 是 | 是 |
| 抵抗否认 攻击 | 否 | 否 | 否 | 否 | 是 |
| 诱饵粒子数 | $N(m+1)$ | $N(m+1)$ | $nN$ | $N(m+1)$ | 0 |
| 所用的 粒子总数 | $N(m+1)+2$ | $N(m+1)+n(m-1)+2$ | $n(N+1)$ | $N(m+1)+2$ | $4m-2$ |
| 酉操作次数 | $m+1$ | $\frac{n}{2}(m+1)(m-1)+1$ | 0 | $m+1$ | $9m-4$ |
| 测量操作 次数 | $N(m+1)+1$ | $N(m+1)+\frac{nm}{2}+1$ | $n(N+1)$ | $N(m+1)+1$ | $4m-1$ |
| [1] | HILLERY M, BUZEK V, BERTHIAUME A. Quantum Secret Sharing[J]. Physical Review A, 1999, 59(3): 1829-1834. |
| [2] | YAN Fengli, GAO Ting. Quantum Secret Sharing between Multiparty and Multiparty without Entanglement[EB/OL]. (2005-07-07)[2023-10-01]. https://doi.org/10.1103/PhysRevA.72.012304. |
| [3] | DEHKORDI M, FATTAHI E. Threshold Quantum Secret Sharing Between Multiparty and Multiparty Using Greenberger-Horne-Zeilinger State[J]. Quantum Information Processing, 2013, 12(2): 1299-1306. |
| [4] | CLEVE R, GOTTESMAN D, LO H. How to Share a Quantum Secret[J]. Physical Review Letters, 1999, 83(3): 648-651. |
| [5] | LIU Lu, LI Zhihui, LU Dianjun, et al. Quantum Secret Sharing Scheme Based on Linear Codes[J]. Netinfo Security, 2021, 21(8): 62-69. |
| 刘璐, 李志慧, 芦殿军, 等. 基于线性码的量子秘密共享方案[J]. 信息网络安全, 2021, 21(8): 62-69. | |
| [6] | YANG Yuguang, WANG Yuan, CHAI Haiping, et al. Member Expansion in Quantum (t, n) Threshold Secret Sharing Schemes[J]. Optics Communications, 2011, 284(13): 3479-3482. |
| [7] | JIA Hengyue, WEN Qiaoyan, GAO Fei, et al. Dynamic Quantum Secret Sharing[J]. Physics Letters A, 2012, 376(10-11): 1035-1041. |
| [8] | HSU J L, CHONG Songkong, HWANG T, et al. Dynamic Quantum Secret Sharing[J]. Quantum Information Processing, 2013, 12(1): 331-344. |
| [9] | YANG Yuguang, TENG Yiwei, CHAI Haiping, et al. Verifiable Quantum (k, n)- Threshold Secret Key Sharing[J]. International Journal of Theoretical Physics, 2011, 50(3): 792-798. |
| [10] | SONG Xiuli, LIU Yanbing. Cryptanalysis and Improvement of Verifiable Quantum (k, n) Secret Sharing[J]. Quantum Information Processing, 2016, 15(2): 851-868. |
| [11] | LI Zhihui, LUO Shuangshuang, WEI Xingjia. Quantum Secret Sharing Schemes Based on a Class of Restricted Access Structures[J]. Netinfo Security, 2023, 23(8): 32-40. |
| 李志慧, 罗双双, 韦性佳. 基于一类受限存取结构上的量子秘密共享方案[J]. 信息网络安全, 2023, 23(8): 32-40. | |
| [12] | QIN Huawang, DAI Yuewei. Verifiable (t, n) Threshold Quantum Secret Sharing Using d-Dimensional Bell State[J]. Information Processing Letters, 2016, 116(5): 351-355. |
| [13] | LU Changbin, MIAO Fuyou, HOU Junpeng, et al. A Verifiable Framework of Entanglement-Free Quantum Secret Sharing with Information-Theoretical Security[EB/OL]. (2019-11-29)[2023-10-01]. https://doi.org/10.1007/s11128-019-2509-x. |
| [14] | LIU Xiaofen, CHEN Xiaofeng, LIAN Guiren, et al. Authenticated Multiparty Quantum Secret Sharing Protocol with d-Level Single Particle[J]. Netinfo Security, 2020, 20(3): 51-55. |
| 刘晓芬, 陈晓峰, 连桂仁, 等. 基于d级单粒子的可认证多方量子秘密共享协议[J]. 信息网络安全, 2020, 20(3):51-55. | |
| [15] | YAN Chenhong, LI Zhihui, LIU Lu, et al. Cheating Identifiable (k, n) Threshold Quantum Secret Sharing Scheme[EB/OL]. (2021-12-23)[2023-10-01]. https://doi.org/10.1007/s11128-021-03343-2. |
| [16] | RATHI D, KUMAR S. A d-Level Quantum Secret Sharing Scheme with Cheat-Detection (t, m) Threshold[EB/OL]. (2023-04-28)[2023-10-01]. https://doi.org/10.1007/s11128-023-03928-z. |
| [17] | SHAMIR A. How to Share a Secret[J]. Communications of the ACM, 1979, 22: 612-613. |
| [18] | WANG Tianyin, LI Yanping. Cryptanalysis of Dynamic Quantum Secret Sharing[J]. Quantum Information Processing, 2013, 12(5): 1991-1997. |
| [19] | LIAO Cihong, YANG Chunwei, HWANG T. Comment on “Dynamic Quantum Secret Sharing”[J]. Quantum Information Processing, 2013, 12(10): 3143-3147. |
| [20] |
YUAN Jiangtao, LI Lixiang. A Fully Dynamic Secret Sharing Scheme[J]. Information Sciences, 2019, 496: 42-52.
doi: 10.1016/j.ins.2019.04.061 |
| [21] | DU Yutao, BAO Wansu. Dynamic Quantum Secret Sharing Protocol Based on Two-Particle Transform of Bell States[J]. Chinese Physics B, 2018, 27(8): 1-6. |
| [22] | HU Wenwen, ZHOU Rigui, LI Xin, et al. A Novel Dynamic Quantum Secret Sharing in High-Dimensional Quantum System[EB/OL]. (2021-05-03)[2023-10-01]. https://doi.org/10.1007/s11128-021-03103-2. |
| [23] | LI Fulin, HU Hang, ZHU Shixin, et al. A Verifiable (k, n)- Threshold Dynamic Quantum Secret Sharing Scheme[EB/OL]. (2022-07-26)[2023-10-01]. https://doi.org/10.1007/s11128-022-03617-3. |
| [24] | LI Fulin, CHEN Tingyan, ZHU Shixin. Dynamic (t, n) Threshold Quantum Secret Sharing Based on d-Dimensional Bell State[J]. Physica A, 2022, 606: 1-9. |
| [25] | YANG Yuguang, LU Jiayu. A Dynamic and Hierarchical Quantum Secret Sharing Protocol Based on Starlike Cluster States[J]. Netinfo Security, 2023, 23(6): 34-42. |
| 杨宇光, 卢嘉煜. 一种基于星型簇态的动态的分级的量子秘密共享协议[J]. 信息网络安全, 2023, 23(6): 34-42. | |
| [26] | WOOTTERS W, FIELDS B. Optimal State-Determination by Mutually Unbiased Measurements[J]. Annals of Physics, 1989, 191(2): 363-381. |
| [27] | GAO Fei, QIN Sujuan, GUO Fenzhuo, et al. Cryptanalysis of the Arbitrated Quantum Signature Protocols[EB/OL]. (2011-08-29)[2023-10-01]. https://doi.org/10.1103/PhysRevA.84.022344. |
| [28] |
SONG Xiuli, LIU Yanbing, XIAO Min, et al. A Verifiable (t, n) Threshold Quantum State Sharing against Denial Attack[J]. IEEE Access, 2019, 7: 98908-98920.
doi: 10.1109/ACCESS.2019.2928855 |
| [1] | 李志慧, 罗双双, 韦性佳. 基于一类受限存取结构上的量子秘密共享方案[J]. 信息网络安全, 2023, 23(8): 32-40. |
| [2] | 杨宇光, 卢嘉煜. 一种基于星型簇态的动态的分级的量子秘密共享协议[J]. 信息网络安全, 2023, 23(6): 34-42. |
| [3] | 易铮阁, 袁文勇, 李瑞峰, 杨晓元. 一种支持动态操作的身份基云存储方案[J]. 信息网络安全, 2022, 22(2): 86-95. |
| [4] | 刘璐, 李志慧, 芦殿军, 闫晨红. 基于线性码的量子秘密共享方案[J]. 信息网络安全, 2021, 21(8): 62-69. |
| [5] | 刘晓芬, 陈晓峰, 连桂仁, 林崧. 基于d级单粒子的可认证多方量子秘密共享协议[J]. 信息网络安全, 2020, 20(3): 51-55. |
| [6] | 刘成基, 李志慧, 司萌萌, 白晨明. 基于局域区分的六粒子正交纠缠态的量子秘密共享方案[J]. 信息网络安全, 2018, 18(4): 56-64. |
| [7] | 程资, 靳俐荣, 石金晶. 基于RS码生成机制的(k,n)门限量子秘密共享方案[J]. 信息网络安全, 2016, 16(4): 44-49. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||