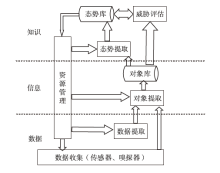
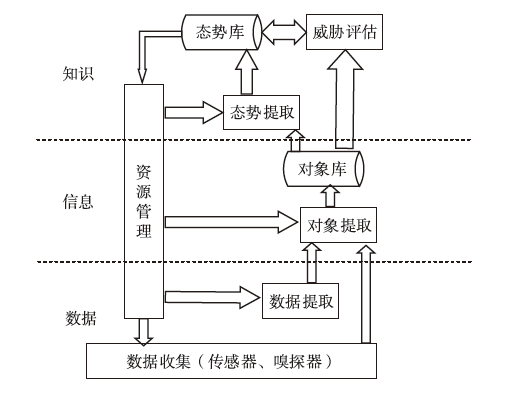
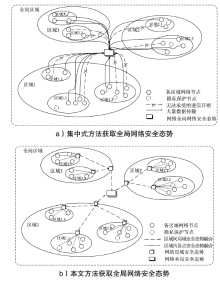
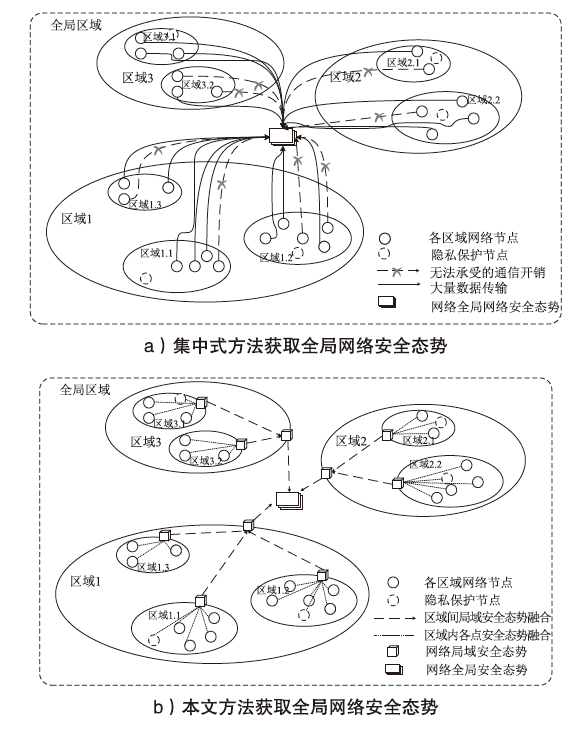
信息网络安全 ›› 2024, Vol. 24 ›› Issue (3): 398-410.doi: 10.3969/j.issn.1671-1122.2024.03.006
基于自注意力机制的网络局域安全态势融合方法研究
- 1.南京理工大学网络空间安全学院,南京 210094
2.南京理工大学计算机科学与工程学院,南京 210094
-
收稿日期:2024-01-29出版日期:2024-03-10发布日期:2024-04-03 -
通讯作者:魏松杰 E-mail:swei@njust.edu.cn -
作者简介:杨志鹏(1998—),男,新疆,硕士研究生,CCF学生会员,主要研究方向为网络安全态势感知与深度学习|刘代东(1999—),男,湖南,硕士研究生,CCF学生会员,主要研究方向为区块链技术应用与网络安全|袁军翼(1999—),男,江苏,硕士研究生,CCF学生会员,主要研究方向为恶意软件检测与网络安全|魏松杰(1977—),男,天津,副教授,博士,CCF高级会员,主要研究方向为网络与信息安全、移动恶意检测、软件定义网络和安全风险评估 -
基金资助:工信部2020年工业互联网创新发展工程(TC200H01V)
Research on Network Local Security Situation Fusion Method Based on Self-Attention Mechanism
YANG Zhipeng1, LIU Daidong1, YUAN Junyi2, WEI Songjie1( )
)
- 1. School of Cyber Science and Engineering, Nanjing University of Science and Technology, Nanjing 210094, China
2. School of Computer Science and Engineering, Nanjing University of Science and Technology, Nanjing 210094, China
-
Received:2024-01-29Online:2024-03-10Published:2024-04-03 -
Contact:WEI Songjie E-mail:swei@njust.edu.cn
摘要:
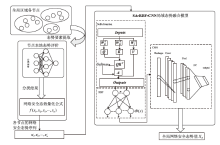
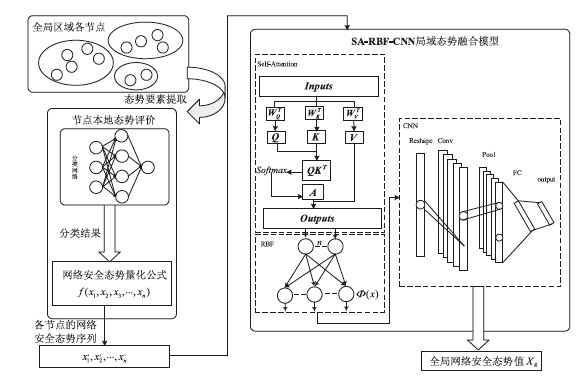
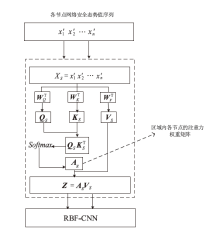
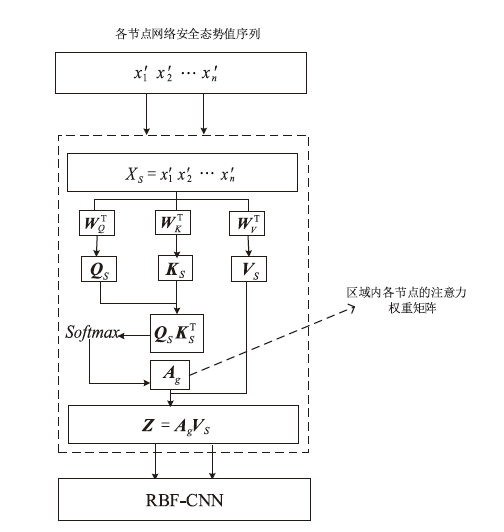
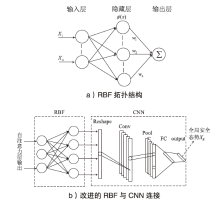
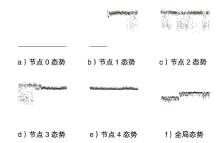
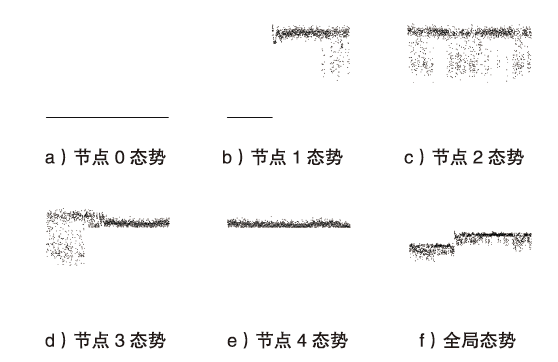
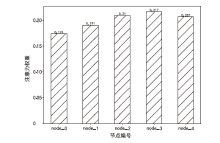
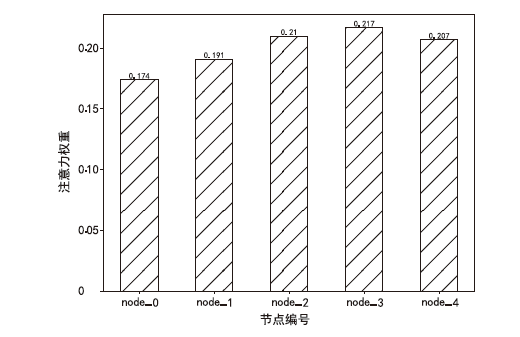
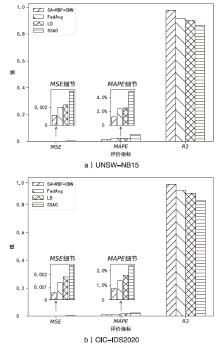
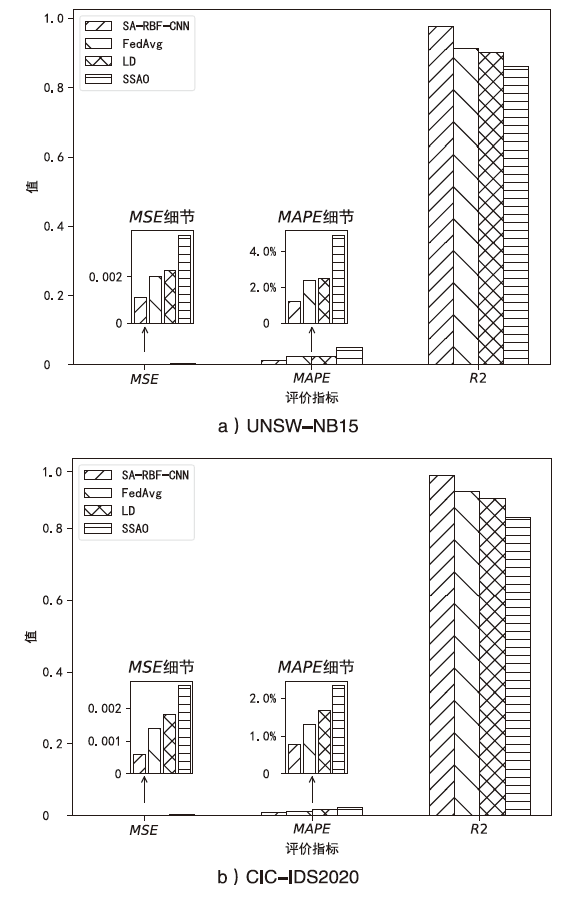
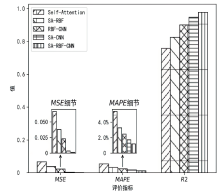
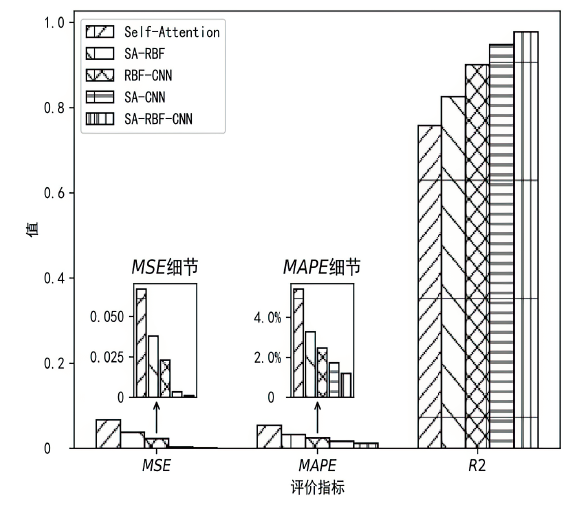
针对传统网络安全态势感知方法无法高效整合多节点数据、获取全局网络安全态势的问题,文章提出了一种基于自注意力机制(Self-Attention Mechanism)、径向基函数(Radial Basis Function,RBF)神经网络与卷积神经网络(Convolutional Neural Network,CNN)的网络局域安全态势融合方法SA-RBF-CNN(Self-Attention-RBF-CNN)。通过自注意力机制,模型能有效识别并强调关键节点,增强对全局安全态势的认识。同时,改进的RBF结构与CNN结合能进一步提炼特征,增强模型对复杂数据模式的捕捉能力。实验结果显示,SA-RBF-CNN在识别网络安全态势预测的关键指标上优于其他类似方法,与传统态势感知方法相比,其提升了计算速度,减少了通信开销,证明该模型具有一定的实际应用价值。
中图分类号:
引用本文
杨志鹏, 刘代东, 袁军翼, 魏松杰. 基于自注意力机制的网络局域安全态势融合方法研究[J]. 信息网络安全, 2024, 24(3): 398-410.
YANG Zhipeng, LIU Daidong, YUAN Junyi, WEI Songjie. Research on Network Local Security Situation Fusion Method Based on Self-Attention Mechanism[J]. Netinfo Security, 2024, 24(3): 398-410.
表1
各威胁危险度
| 威胁名称 | 威胁中文 名称 | 威胁 危险度 | 描述 |
|---|---|---|---|
| Normal | 正常 | 0.000 | 未受到攻击 |
| Fuzzers | 模糊攻击 | 0.925 | 通过提供随机生成的数据使 网络暂停 |
| Analysis | 分析攻击 | 0.961 | 包含端口扫描、垃圾邮件等不同的攻击 |
| Backdoors | 后门 | 1.190 | 绕过系统安全机制秘密访问数据 |
| DoS | 拒绝服务 攻击 | 0.914 | 恶意尝试使服务器或网络资源对 用户不可用 |
| Exploits | 渗透攻击 | 1.202 | 利用程序的漏洞获得控制权 |
| Generic | 通用攻击 | 0.913 | 一种适用于所有分组密码的攻击 |
| Reconnaissance | 侦察攻击 | 0.942 | 使攻击者获得更多有关受害者的 信息 |
| Shellcode | 漏洞代码 | 1.301 | 一段利用软件漏洞执行的代码 |
| Worms | 恶性计算机 病毒 | 1.144 | 复制自身以传播到其他计算机的 病毒 |
| [1] | D’AMBROSIO B, TAKIKAWA M, FITZGERALD J, et al. Security Situation Assessment and Response Evaluation (SSARE)[C]// IEEE. Proceedings DARPA Information Survivability Conference and Exposition II. DISCEX’01. New York:IEEE, 2001: 387-394. |
| [2] | GONG Jian, ZANG Xiaodong, SU Qi, et al. A Review of Network Security Situation Awareness[J]. Journal of Software, 2017, 28(4): 1010-1026. |
| 龚俭, 臧小东, 苏琪, 等. 网络安全态势感知综述[J]. 软件学报, 2017, 28(4):1010-1026. | |
| [3] |
ENDSLEY M R. Design and Evaluation for Situation Awareness Enhancement[J]. Proceedings of the Human Factors Society Annual Meeting, 1988, 32(2): 97-101.
doi: 10.1177/154193128803200221 URL |
| [4] | BASS T. Multisensor Data Fusion for Next Generation Distributed Intrusion Detection Systems[J]. Proceedings of the IRIS National Symposium on Sensor and Data Fusion, 1999, 24(28): 24-27. |
| [5] | BASS T. Intrusion Detection Systems and Multisensor Data Fusion[J]. Communications of the ACM, 2000, 43(4): 99-105. |
| [6] | TAO Yuan, HUANG Tao, ZHANG Mohan, et al. Research and Development Trend Analysis of Key Technologies for Cyberspace Security Situation Awareness[J]. Netinfo Security, 2018, 18(8): 79-85. |
| 陶源, 黄涛, 张墨涵, 等. 网络安全态势感知关键技术研究及发展趋势分析[J]. 信息网络安全, 2018, 18(8):79-85. | |
| [7] | HUSÁK M, KOMÁRKOVÁ J, BOU-HARB E, et al. Survey of Attack Projection, Prediction, and Forecasting in Cyber Security[J]. IEEE Communications Surveys & Tutorials, 2019, 21(1): 640-660. |
| [8] | HU Chuhang, LIU Guikai, LI Ming. A Network Security Situation Prediction Method Based on Attention-CNN-BiGRU[C]// IEEE. 2022 IEEE 25th International Conference on Computer Supported Cooperative Work in Design (CSCWD). New York: IEEE, 2022: 257-262. |
| [9] | XIE Lixia, WANG Yachao, YU Jinbo. Network Security Situation Awareness Based on Neural Networks[J]. Journal of Tsinghua University (Science and Technology), 2013, 53(12): 1750-1760. |
| 谢丽霞, 王亚超, 于巾博. 基于神经网络的网络安全态势感知[J]. 清华大学学报(自然科学版), 2013, 53(12):1750-1760. | |
| [10] | YU Qing, ZHENG Chonghui, DU Ye. Research on Key Technologies of Security Situation Assessment for the Virtual Layer of Cloud Platform[J]. Netinfo Security, 2020, 20(7): 53-59. |
| 余晴, 郑崇辉, 杜晔. 面向云平台虚拟层的安全态势评估关键技术研究[J]. 信息网络安全, 2020, 20(7):53-59. | |
| [11] |
CHEN Zhihua. Research on Internet Security Situation Awareness Prediction Technology Based on Improved RBF Neural Network Algorithm[J]. Journal of Computational and Cognitive Engineering, 2022, 1(3): 103-108.
doi: 10.47852/bonviewJCCE149145205514 URL |
| [12] | ELMAN J L. Distributed Representations, Simple Recurrent Networks, and Grammatical Structure[J]. Machine Learning, 1991, 7: 195-225. |
| [13] |
ZHANG Haofang, KANG Chunying, XIAO Yao. Research on Network Security Situation Awareness Based on the LSTM-DT Model[J]. Sensors, 2021, 21(14): 4788.
doi: 10.3390/s21144788 URL |
| [14] |
ZHANG Shengcai, FU Qiming, AN Dezhi. Network Security Situation Prediction Model Based on VMD Decomposition and DWOA Optimized BiGRU-ATTN Neural Network[J]. IEEE Access, 2023, 11: 129507-129535.
doi: 10.1109/ACCESS.2023.3333666 URL |
| [15] |
GUO Qipeng, QIU Xipeng, XUE Xiangyang, et al. Low-Rank and Locality Constrained Self-Attention for Sequence Modeling[J]. IEEE/ACM Transactions on Audio, Speech, and Language Processing, 2019, 27(12): 2213-2222.
doi: 10.1109/TASLP.6570655 URL |
| [16] |
MEI Xiaoguang, PAN E, MA Yong, et al. Spectral-Spatial Attention Networks for Hyperspectral Image Classification[J]. Remote Sensing, 2019, 11(8): 963.
doi: 10.3390/rs11080963 URL |
| [17] | LI Jiyu, FU Zhangjie, ZHANG Yubin. An Image Information Hiding Algorithm Based on Cross-Domain Adversarial Adaptation[J]. Netinfo Security, 2023, 23(1): 93-102. |
| 李季瑀, 付章杰, 张玉斌. 一种基于跨域对抗适应的图像信息隐藏算法[J]. 信息网络安全, 2023, 23(1):93-102. | |
| [18] | HU Chuhang, LIU Guikai, LI Ming. A Network Security Situation Prediction Method Based on Attention-CNN-BiGRU[C]// IEEE. 2022 IEEE 25th International Conference on Computer Supported Cooperative Work in Design (CSCWD). New York: IEEE, 2022: 257-262. |
| [19] |
ZHAO Dongmei, SHEN Pengcheng, ZENG Shuiguang. ALSNAP: Attention-Based Long and Short-Period Network Security Situation Prediction[J]. Ad Hoc Networks, 2023, 150: 103279.
doi: 10.1016/j.adhoc.2023.103279 URL |
| [20] | CHENG Jiagen, QI Zhenghua, CHEN Tianfu. Network Security Situation Awareness Based on RBF Neural Network[J]. Journal of Nanjing University of Posts and Telecommunications (Natural Science), 2019, 39(4):88-95. |
| 程家根, 祁正华, 陈天赋. 基于RBF神经网络的网络安全态势感知[J]. 南京邮电大学学报(自然科学版), 2019, 39(4):88-95. | |
| [21] | YAO Chengpeng, YANG Yu, YIN Kun. Research on Network Security Situation Prediction Method Based on AM and LSTM Hybrid Neural Network[C]// IEEE. 2021 8th International Forum on Electrical Engineering and Automation (IFEEA). New York: IEEE, 2021: 322-330. |
| [22] |
ZHAO Dongmei, SONG Huiqian, ZHANG Hongbin. Network Security Situation Assessment Based on Time Factor and Composite CNN Structure[J]. Computer Science, 2021, 48(12): 349-356.
doi: 10.11896/jsjkx.210400227 |
|
赵冬梅, 宋会倩, 张红斌. 基于时间因子和复合CNN结构的网络安全态势评估[J]. 计算机科学, 2021, 48(12):349-356.
doi: 10.11896/jsjkx.210400227 |
|
| [23] |
CHANG Liwei, LIU Xiujuan, QIAN Yuhua, et al. Network Security Situation Awareness Model Based on Multi-Source Fusion of Convolutional Neural Networks[J]. Computer Science, 2023, 50(5): 382-389.
doi: 10.11896/jsjkx.220400134 |
|
常利伟, 刘秀娟, 钱宇华, 等. 基于卷积神经网络多源融合的网络安全态势感知模型[J]. 计算机科学, 2023, 50(5):382-389.
doi: 10.11896/jsjkx.220400134 |
|
| [24] |
VAN P J M, PEDRYCZ W. A Fuzzy Extension of Saaty’s Priority Theory[J]. Fuzzy Sets and Systems, 1983, 11(1-3): 229-241.
doi: 10.1016/S0165-0114(83)80082-7 URL |
| [25] | MOUSTAFA N, SLAY J. UNSW-NB15:A Comprehensive Dataset for Network Intrusion Detection Systems (UNSW-NB15 Network Dataset)[C]// IEEE. 2015 Military Communications and Information Systems Conference (MilCIS). New York: IEEE, 2015: 1-6. |
| [26] | WANG Yixuan, ZHAO Bo, LI Weidong, et al. An Ontology-Centric Approach for Network Security Situation Awareness[C]// IEEE. 2023 IEEE 47th Annual Computers, Software, and Applications Conference (COMPSAC). New York: IEEE, 2023: 777-787. |
| [27] |
XIAO Lin, BOYD S. Fast Linear Iterations for Distributed Averaging[J]. Systems & Control Letters, 2004, 53(1): 65-78.
doi: 10.1016/j.sysconle.2004.02.022 URL |
| [28] | MCMAHAN B, MOORE E, RAMAGE D, et al. Communication-Efficient Learning of Deep Networks from Decentralized Data[C]// PMLR. Proceedings of the 20th International Conference on Artificial Intelligence and Statistics. New York: PMLR, 2017: 1273-1282. |
| [1] | 江荣, 刘海天, 刘聪. 基于集成学习的无监督网络入侵检测方法[J]. 信息网络安全, 2024, 24(3): 411-426. |
| [2] | 江魁, 卢橹帆, 苏耀阳, 聂伟. 基于Attention-GRU的SHDoS攻击检测研究[J]. 信息网络安全, 2024, 24(3): 427-437. |
| [3] | 冯光升, 蒋舜鹏, 胡先浪, 马明宇. 面向物联网的入侵检测技术研究新进展[J]. 信息网络安全, 2024, 24(2): 167-178. |
| [4] | 赵鹏程, 于俊清, 李冬. 一种基于深度学习的SRv6网络流量调度优化算法[J]. 信息网络安全, 2024, 24(2): 272-281. |
| [5] | 金志刚, 丁禹, 武晓栋. 融合梯度差分的双边校正联邦入侵检测算法[J]. 信息网络安全, 2024, 24(2): 293-302. |
| [6] | 薛羽, 张逸轩. 深层神经网络架构搜索综述[J]. 信息网络安全, 2023, 23(9): 58-74. |
| [7] | 刘宇啸, 陈伟, 张天月, 吴礼发. 基于稀疏自动编码器的可解释性异常流量检测[J]. 信息网络安全, 2023, 23(7): 74-85. |
| [8] | 蒋英肇, 陈雷, 闫巧. 基于双通道特征融合的分布式拒绝服务攻击检测算法[J]. 信息网络安全, 2023, 23(7): 86-97. |
| [9] | 赵彩丹, 陈璟乾, 吴志强. 基于多通道联合学习的自动调制识别网络[J]. 信息网络安全, 2023, 23(4): 20-29. |
| [10] | 谭柳燕, 阮树骅, 杨敏, 陈兴蜀. 基于深度学习的教育数据分类方法[J]. 信息网络安全, 2023, 23(3): 96-102. |
| [11] | 徐占洋, 程洛飞, 程建春, 许小龙. 一种使用Bi-ADMM优化深度学习模型的方案[J]. 信息网络安全, 2023, 23(2): 54-63. |
| [12] | 陈得鹏, 刘肖, 崔杰, 仲红. 一种基于双阈值函数的成员推理攻击方法[J]. 信息网络安全, 2023, 23(2): 64-75. |
| [13] | 文伟平, 朱一帆, 吕子晗, 刘成杰. 针对品牌的网络钓鱼扩线与检测方案[J]. 信息网络安全, 2023, 23(12): 1-9. |
| [14] | 刘军, 武志超, 吴建, 谭振华. 一种融合图像空间特征注意力机制的恶意代码识别模型[J]. 信息网络安全, 2023, 23(12): 29-37. |
| [15] | 廖丽云, 张伯雷, 吴礼发. 基于代价敏感学习的物联网异常检测模型[J]. 信息网络安全, 2023, 23(11): 94-103. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||