信息网络安全 ›› 2024, Vol. 24 ›› Issue (2): 217-228.doi: 10.3969/j.issn.1671-1122.2024.02.005
面向异构复合任务的无人集群动态重叠联盟任务分配方法
- 1.南京信息工程大学电子与信息工程学院,南京 210044
2.南京航空航天大学电子信息工程学院,南京211106
3.海南大学信息与通信工程学院,海口 570228
-
收稿日期:2023-06-21出版日期:2024-02-10发布日期:2024-03-06 -
通讯作者:程田圆 E-mail:3383774180@qq.com -
作者简介:姚昌华(1983—),男,重庆,教授,博士,主要研究方向为智能无人集群和电磁频谱对抗|程田圆(1999—),女,山东,硕士研究生,主要研究方向为智能无人集群|屈毓锛(1987—),男,湖北,副研究员,博士,CCF会员,主要研究方向为移动边缘计算、边缘人工智能、无人机协同智能及其应用|苏婷(1985—),女,安徽,副教授,博士,主要研究方向为信号处理、无线通信 -
基金资助:国家自然科学基金(61971439);国家自然科学基金(U22B2002);江苏省自然科学基金(BK20191329)
A Task Allocation Method for Unmanned Clusters Based on Dynamic Overlapping Coalition Toward Heterogeneous Composite Tasks
YAO Changhua1, CHENG Tianyuan1( ), QU Yuben2, SU Ting3
), QU Yuben2, SU Ting3
- 1. School of Electronics & Information Engineering, Nanjing University of Information Science & Technology, Nanjing 210044, China
2. College of Electronic and Information Engineering, Nanjing University of Aeronautics and Astronautics, Nanjing 211106, China
3. School of Information and Communication Engineering, Hainan University, Haikou 570228, China
-
Received:2023-06-21Online:2024-02-10Published:2024-03-06 -
Contact:CHENG Tianyuan E-mail:3383774180@qq.com
摘要:
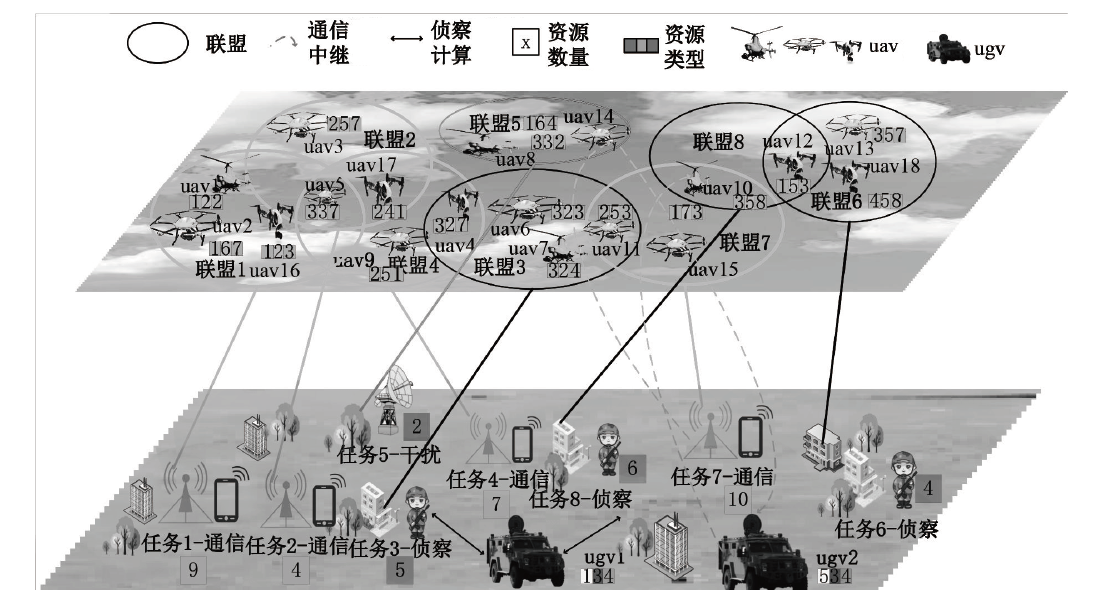
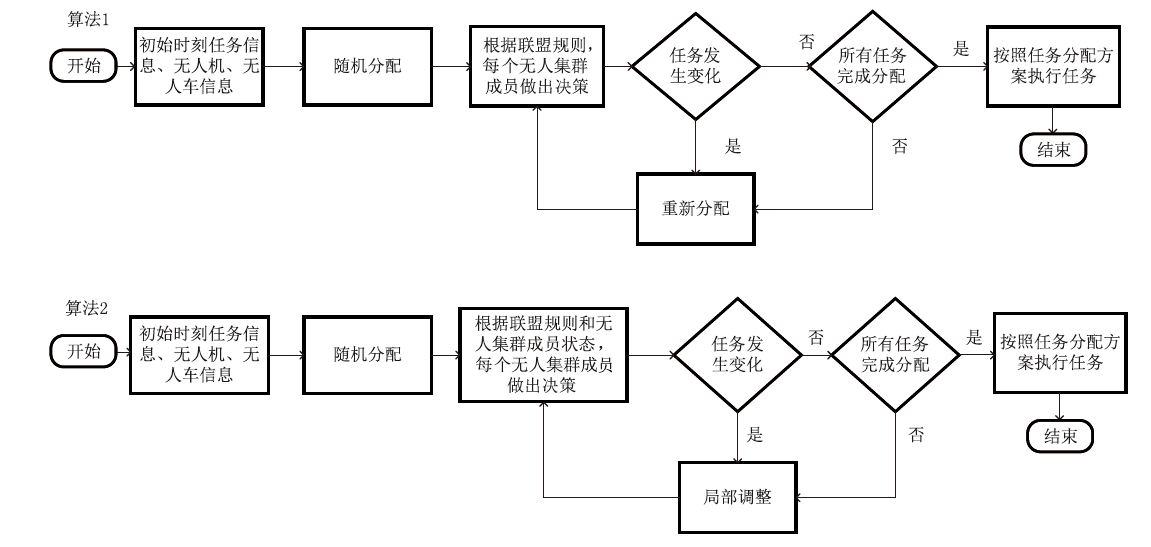
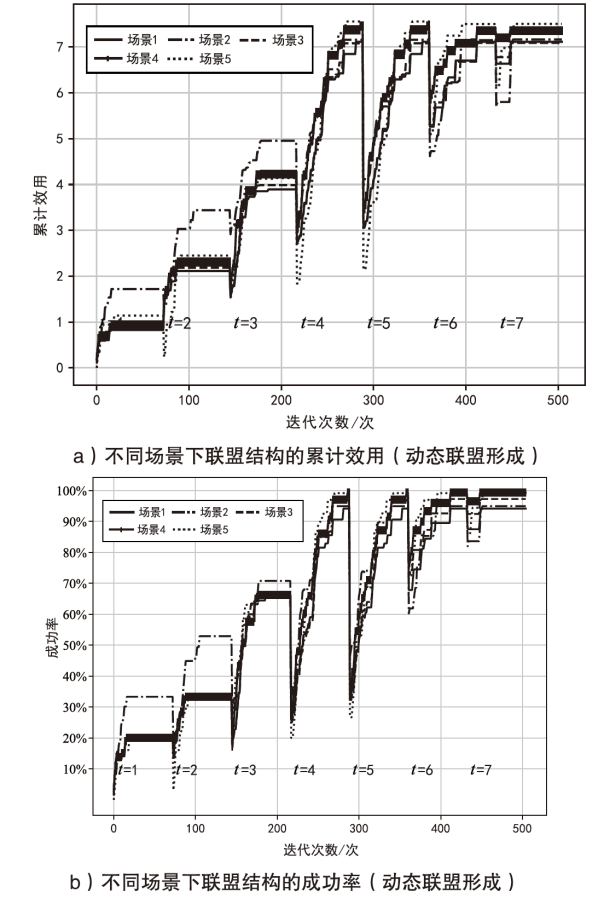
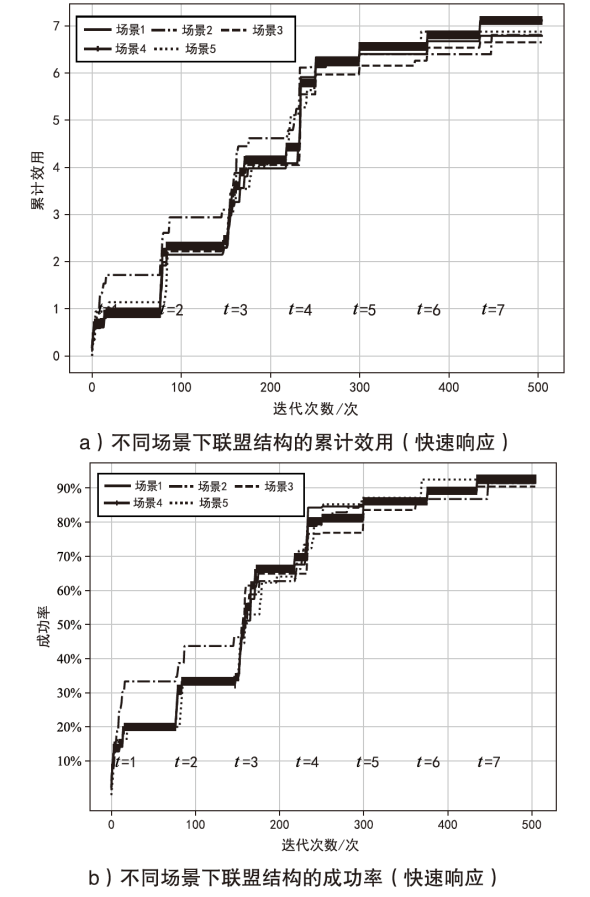
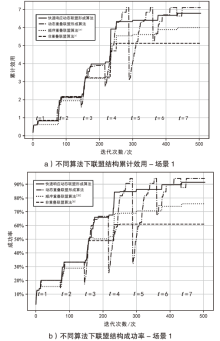
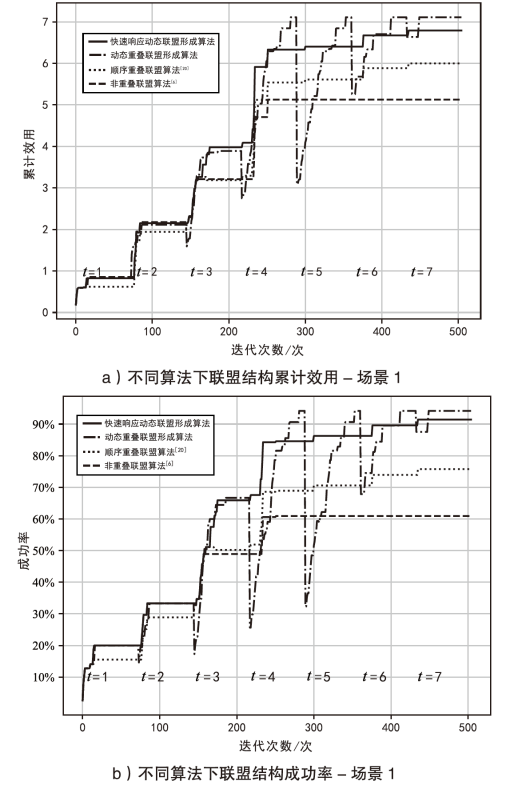
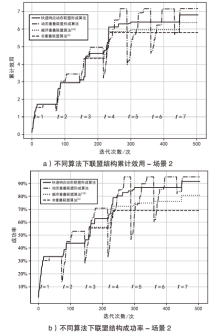
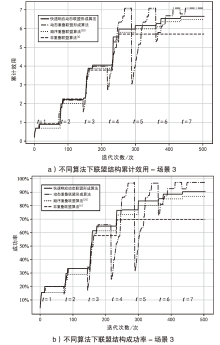
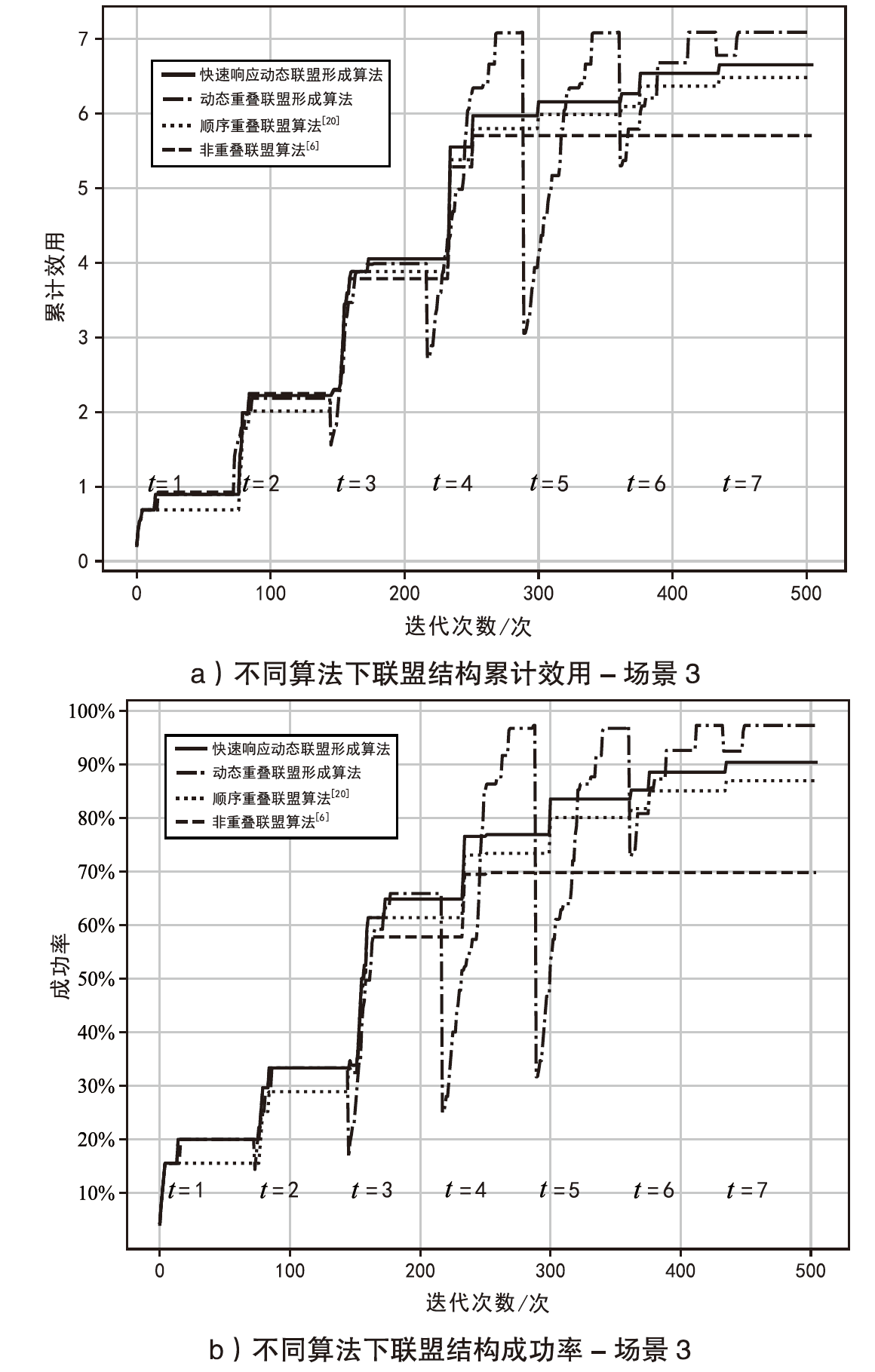
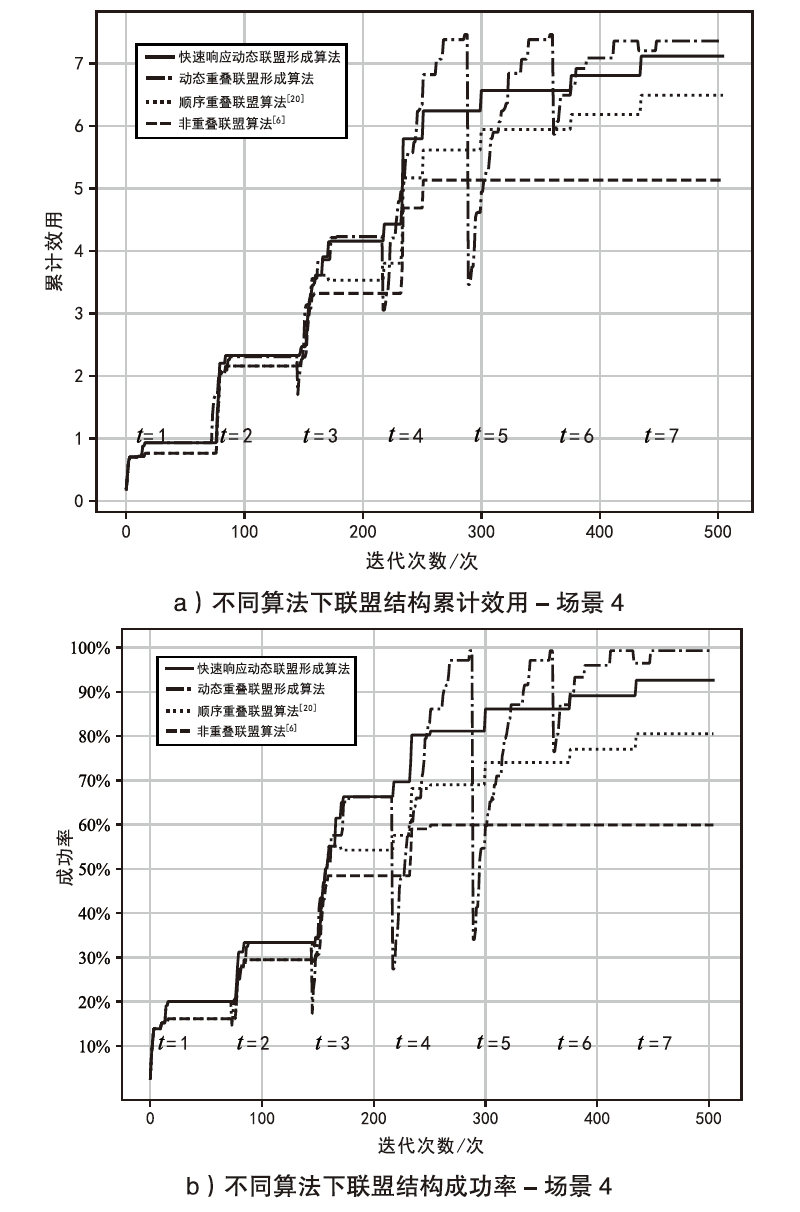
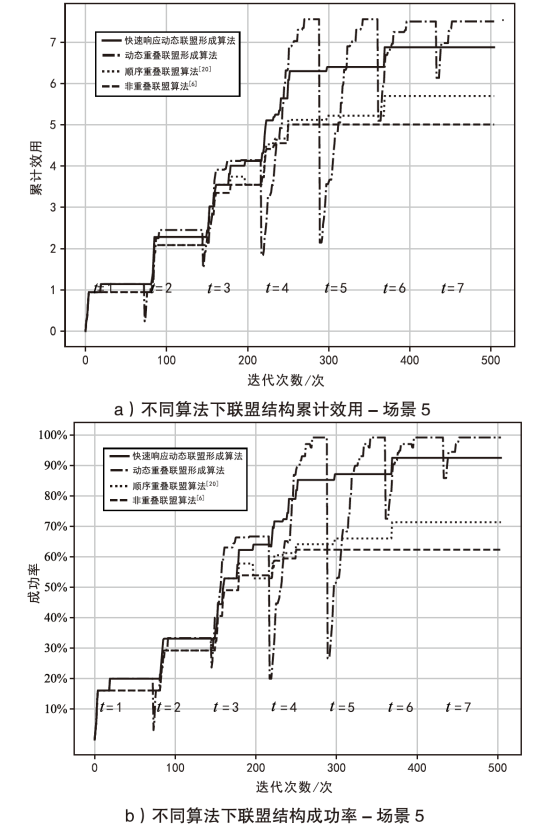
智能无人集群由于其平台特性的多样性,具备较好的资源调配空间和功能弹性,能够应对复杂多变的任务需求。现有研究大多未考虑任务的异构性和关联性等实际需求,其任务分配方法在需求和资源的适配性、集群协同的动态响应能力上存在不足。文章针对无人集群系统在遂行多目标任务过程中存在的任务分配不均、协同性差和动态适应性差等问题,提出了面向异构复合任务的动态响应重叠联盟任务分配架构。首先,综合考虑多个耦合异构任务的价值、优先级、需求和任务变化带来的影响来构建联盟博弈模型;然后设计算法,分布式协同调度不同无人集群(无人机和无人车)的资源,实现集群异构成员的资源与异构任务合理匹配,并能根据任务变化情况进行高效的动态调整。仿真结果表明,文章提出的算法能够适应动态任务场景,形成稳定高效的任务联盟和资源分配方案,提高了无人集群遂行多样化异构任务的系统收益和成功率,实现了无人集群系统在动态条件下的协同任务分配优化。
中图分类号:
引用本文
姚昌华, 程田圆, 屈毓锛, 苏婷. 面向异构复合任务的无人集群动态重叠联盟任务分配方法[J]. 信息网络安全, 2024, 24(2): 217-228.
YAO Changhua, CHENG Tianyuan, QU Yuben, SU Ting. A Task Allocation Method for Unmanned Clusters Based on Dynamic Overlapping Coalition Toward Heterogeneous Composite Tasks[J]. Netinfo Security, 2024, 24(2): 217-228.
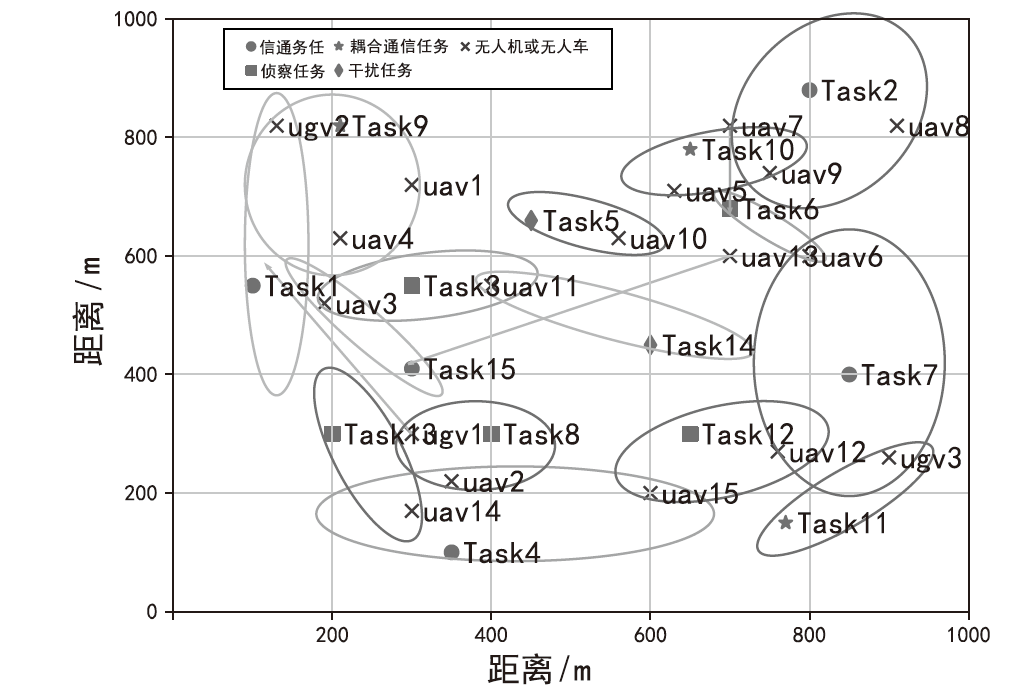
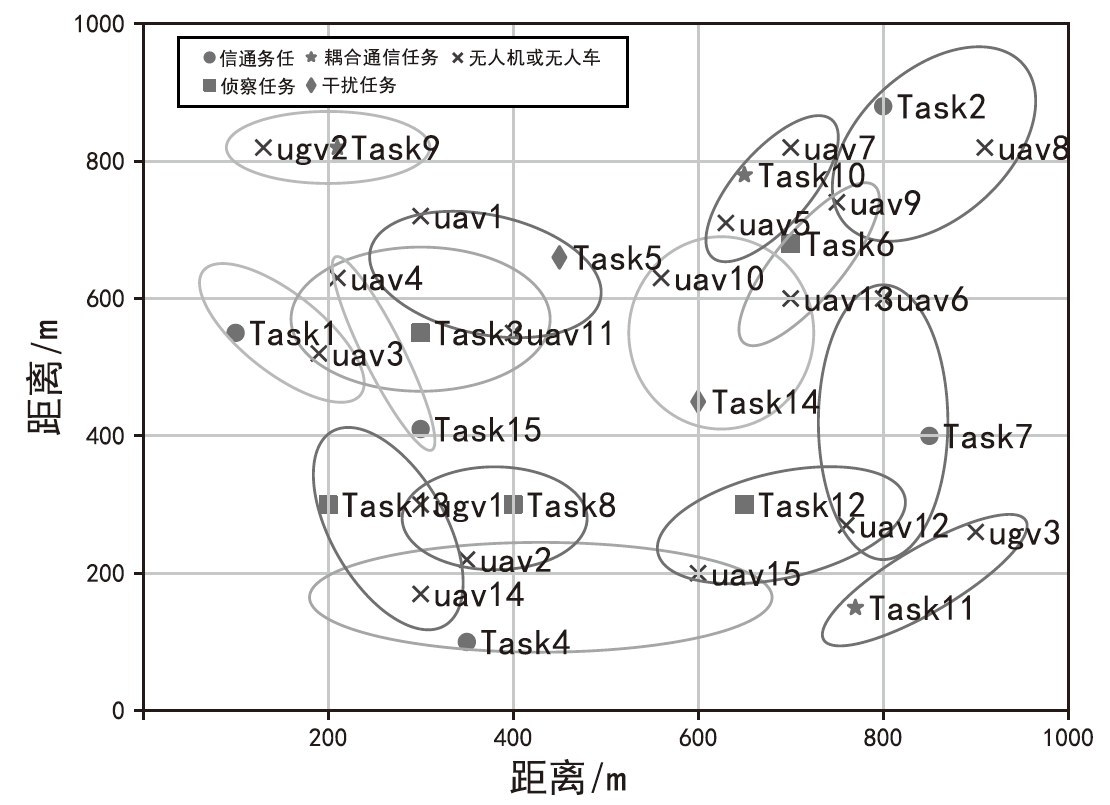
表1
场景1信息
| 任务和无人集群成员的属性 | 任务15个、无人机15架、无人车3辆 |
|---|---|
| 任务开始时间/s | [4,3,1,3,3,4,2,4,1,4,4,1,3,3,2] |
| 任务结束时间/s | [8,6,3,7,7,7,5,6,6,6,8,6,6,6,4] |
| 任务价值 | [0.40,0.70,0.50,0.20,0.90,0.40,0.30,0.20,0.90,0.40,0.30,0.90,0.90,0.40,0.98] |
| 任务优先级 | [0.80,0.30,0.90,0.80,0.60,0.50,0.20,0.40,0.70,0.50,0.60,0.70,0.10,0.20,0.99] |
| 任务通信需求/Hz | [0.9,0.75,0.80,0.00,0.00,0.00,0.70,0.00,0.00,0.90,0.90,0.00,0.00,0.50,0.70] |
| 任务侦察需求/pixel | [0.00,0.00,0.00,0.84,0.80,1.00,0.00,0.80,0.60,0.80,0.84,0.00,0.00,0.00,0.80] |
| 任务干扰需求/Hz | [0.00,0.00,0.00,0.00,0.00,0.00,0.00,0.00,0.00,0.00,0.00,0.50,0.75,0.00,0.00] |
| 任务位置/m | [(100,550),(800,880),(350,100),(300,550),(700,680),(400,300),(850,400),(650,300),(200,300),(210,820),(770,150),(450,660),(600,450),(300,410),(650,780)] |
| 无人机通信资源/Hz | [0.375,0.3125,0.250,0.475,0.500,0.3125,0.300,0.250,0.550,0.350,0.3125,0.400,0.550,0.3125,0.400] |
| 无人机侦察资源/pixel | [0.50,0.25,0.20,0.25,0.25,0.375,0.80,0.40,0.80,0.50,0.90,0.375,0.375,0.40,0.60] |
| 无人机干扰资源/Hz | [0.40,0.60,0.50,0.40,0.60,0.50,0.40,0.60, 0.50,0.15,0.70,0.50,0.40,0.60,0.50] |
| 无人机位置/m | [(300,720),(350,220),(190,520),(210,630),(630,710),(800,600),(700,820),(910,820),(750,740),(560,630),(400,550),(760,270),(700,600), (300,170),(600,200)] |
| 无人车通信资源/Hz | [0.500,0.700,0.975] |
| 无人车侦察资源/pixel | [0.7,0.7,0.8] |
| 无人车干扰资源/Hz | [0.4,0.6,0.5] |
| 无人车位置/m | [(300,300),(130,820),(900,260)] |
表5
场景3更改任务需求
| 任务的属性 | 任务15个 |
|---|---|
| 任务通信需求/Hz | [0.90, 0.75, 0.50, 0.00, 0.00, 0.00, 0.70, 0.00, 0.00, 0.90, 0.90, 0.00, 0.00, 0.60, 0.70] |
| 任务侦察需求/pixel | [0.000, 0.000, 0.000, 1.000, 0.800, 1.000, 0.000, 0.375, 0.600, 0.800, 0.840, 0.000, 0.000, 0.000, 0.800] |
| 任务干扰需求/Hz | [0.00, 0.00, 0.00, 0.00, 0.00, 0.00, 0.00, 0.00, 0.00, 0.00, 0.00, 0.75, 0.50, 0.00, 0.00] |
表6
场景4更改无人机、无人车资源
| 无人集群成员的属性 | 无人机15架、无人车3辆 |
|---|---|
| 无人机通信资源/Hz | [0.3750, 0.3750, 0.4750, 0.4750, 0.5000, 0.4750, 0.3000, 0.2500, 0.5500, 0.3500, 0.3125, 0.4000, 0.5500, 0.3125, 0.400] |
| 无人机侦察资源/pixel | [0.500, 0.500, 0.250, 0.250, 0.250, 0.375, 0.800, 0.400, 0.800, 0.500, 0.800, 0.600, 0.375, 0.400, 0.600] |
| 无人机干扰资源/Hz | [0.4, 0.6, 0.5, 0.4, 0.4, 0.5, 0.4, 0.6, 0.5, 0.5, 0.7, 0.5, 0.4, 0.6, 0.5] |
| 无人车通信资源/Hz | [0.500, 0.550, 0.975] |
| 无人车侦察资源/pixel | [0.7, 0.7, 0.8] |
| 无人车干扰资源/Hz | [0.4, 0.6, 0.5] |
表7
场景5更改拓扑结构
| 任务和无人集群成员的属性 | 无人机15架、无人车3辆 |
|---|---|
| 任务位置/m | [(100, 200),(800, 800),(180, 880),(520, 520),(390, 400),(870, 620),(650, 300),(110, 410),(310, 800),(610, 800),(300, 600),(200, 610),(600, 450),(800, 400),(700, 600)] |
| 无人机位置/m | [(250, 800),(360, 650),(180, 500),(260, 910),(130, 300),(260, 550),(60, 290),(300, 420),(900, 700),(440, 480),(520, 400),(700, 800),(800, 600),(770, 300),(700, 500)] |
| 无人车位置/m | [(500, 600),(630, 630),(300, 300)] |
| [1] |
PENG Qiang, WU Husheng, XUE Ruisong. Review of Dynamic Task Allocation Methods for UAV Swarms Oriented to Ground Targets[J]. Complex System Modeling and Simulation, 2021, 1(3): 163-175.
doi: 10.23919/CSMS.2021.0022 URL |
| [2] |
MOTLAGH N H, BAGAA M, TALEB T. Energy and Delay Aware Task Assignment Mechanism for UAV-Based IoT Platform[J]. IEEE Internet of Things Journal, 2019, 6(4): 6523-6536.
doi: 10.1109/JIoT.6488907 URL |
| [3] | MA Peibo, ZHONG Lin. Assignment of UAV Reconnaissance Task Based on Ant Colony Algorithm[J]. Radio Communications Technology, 2022, 48(2): 371-375. |
| 马培博, 钟麟. 基于蚁群算法的无人机侦察任务分配[J]. 无线电通信技术, 2022, 48(2): 371-375. | |
| [4] | GHAMRY K A, KAMEL M A,ZHANG Youmin. Multiple UAVs in Forest Fire Fighting Mission Using Particle Swarm Optimization[C]// IEEE. 2017 International Conference on Unmanned Aircraft Systems (ICUAS). New York:IEEE, 2017: 1404-1409. |
| [5] | BEKMEZCI I, ERMIS M, KAPLAN S. Connected Multi UAV Task Planning for Flying Ad Hoc Networks[C]// IEEE. 2014 IEEE International Black Sea Conference on Communications and Networking (BlackSeaCom). New York:IEEE, 2014: 28-32. |
| [6] |
CHEN Jiaxin, WU Qihui, XU Yuhua, et al. Joint Task Assignment and Spectrum Allocation in Heterogeneous UAV Communication Networks: A Coalition Formation Game-Theoretic Approach[J]. IEEE Transactions on Wireless Communications, 2021, 20(1): 440-452.
doi: 10.1109/TWC.7693 URL |
| [7] | SAAD W, ZHU Han, BASAR T, et al. A Selfish Approach to Coalition Formation Among Unmanned Air Vehicles in Wireless Networks[C]// Springer. 2009 International Conference on Game Theory for Networks. Heidelberg: Springer, 2009: 259-267. |
| [8] |
LUAN Heyu, XU Yitao, LIU Dianxiong, et al. Energy Efficient Task Cooperation for Multi-UAV Networks: A Coalition Formation Game Approach[J]. IEEE Access, 2020, 8: 149372-149384.
doi: 10.1109/Access.6287639 URL |
| [9] |
NGJS, LIM W YB, DAI H N, et al. Joint Auction-Coalition Formation Framework for Communication-Efficient Federated Learning in UAV-Enabled Internet of Vehicles[J]. IEEE Transactions on Intelligent Transportation Systems, 2021, 22(4): 2326-2344.
doi: 10.1109/TITS.2020.3041345 URL |
| [10] |
LIU Dianxiong, XU Yuhua, XU Yitao, et al. Opportunistic Data Collection in Cognitive Wireless Sensor Networks: Air-Ground Collaborative Online Planning[J]. IEEE Internet of Things Journal, 2020, 7(9): 8837-8851.
doi: 10.1109/JIoT.6488907 URL |
| [11] | BARDHAN R, GHOSE D. Resource Allocation and Coalition Formation for UAVs: A Cooperative Game Approach[C]// IEEE. 2013 IEEE International Conference on Control Applications (CCA). New York:IEEE, 2013: 1200-1205. |
| [12] | CHEN Jiaxin, CHEN Ping, WU Qihui, et al. A Game-Theoretic Perspective on Resource Management for Large-Scale UAV Communication Networks[J]. China Communications, 2021, 18(1): 70-87. |
| [13] |
ZHANG Zengfeng, SONG Lingyang, HAN Zhu, et al. Coalitional Games with Overlapping Coalitions for Interference Management in Small Cell Networks[J]. IEEE Transactions on Wireless Communications, 2014, 13(5): 2659-2669.
doi: 10.1109/TWC.2014.032514.130942 URL |
| [14] |
DUAN Xiaojun, LIU Huiying, TANG Hong, et al. A Novel Hybrid Auction Algorithm for Multi-UAVs Dynamic Task Assignment[J]. IEEE Access, 2020, 8: 86207-86222.
doi: 10.1109/Access.6287639 URL |
| [15] | FU Xiaowei, FENG Peng, GAO Xiaoguang. Swarm UAVs Task and Resource Dynamic Assignment Algorithm Based on Task Sequence Mechanism[J]. IEEE Access, 2019, 99: 1-11. |
| [16] | ZHENG Hongxing, GUO Jifeng, XIE Xudong, et al. A Distributed Coalition Formation Method of Heterogeneous UAV Swarm in Unknown Dynamic Environment[J]. Journal of Astronautics, 2022, 43(2): 189-197. |
| 郑红星, 郭继峰, 谢旭东, 等. 一种未知动态环境下异构无人机集群分布式联盟形成方法[J]. 宇航学报, 2022, 43(2): 189-197. | |
| [17] | AFGHAH F, ZAERI-AMIRANI M, RAZI A, et al. A Coalition Formation Approach to Coordinated Task Allocation in Heterogeneous UAV Networks[C]// IEEE. 2018 Annual American Control Conference (ACC). New York:IEEE, 2018: 5968-5975. |
| [18] |
SAAD W, ZHU Han, BASAR T, et al. Hedonic Coalition Formation for Distributed Task Allocation among Wireless Agents[J]. IEEE Transactions on Mobile Computing, 2011, 10(9): 1327-1344.
doi: 10.1109/TMC.2010.242 URL |
| [19] |
LIU Zhong, GAO Xiaoguang, FU Xiaowei, et al. Coalition Formation of Multiple Heterogeneous Unmanned Aerial Vehicles in Cooperative Search and Attack in Unknown Environment[J]. Acta Armamentarii, 2015, 36(12): 2284-2297.
doi: 10.3969/j.issn.1000-1093.2015.12.011 |
|
刘重, 高晓光, 符小卫, 等. 未知环境下异构多无人机协同搜索打击中的联盟组建[J]. 兵工学报, 2015, 36(12): 2284-2297.
doi: 10.3969/j.issn.1000-1093.2015.12.011 |
|
| [20] |
QI Nan, HUAGN Zanqi, ZHOU Fuhui, et al. A Task-Driven Sequential Overlapping Coalition Formation Game for Resource Allocation in Heterogeneous UAV Networks[J]. IEEE Transactions on Mobile Computing, 2022, 22(8): 4439-4455.
doi: 10.1109/TMC.2022.3165965 URL |
| [21] | WANG Hui, LIU Shuang. Task Allocation of Multi-UAV Coalition Based on Resource Constraints[J]. Journal of East China University of Science and Technology, 2021, 47(4): 504-509. |
| 王辉, 刘爽. 基于资源约束的多无人机联盟的任务分配[J]. 华东理工大学学报(自然科学版), 2021, 47(4): 504-509. | |
| [22] | YAO Changhua, AN Lei. Autonomous Collaborative Optimization of UAV Swarms for Multimode Heterogeneous Task[J]. Telecommunication Engineering, 2023, 63(8): 1151-1158. |
| 姚昌华, 安蕾. 面向多模异构任务的无人机群自主协同优化[J]. 电讯技术, 2023, 63(8): 1151-1158. |
| [1] | 冯光升, 蒋舜鹏, 胡先浪, 马明宇. 面向物联网的入侵检测技术研究新进展[J]. 信息网络安全, 2024, 24(2): 167-178. |
| [2] | 翟鹏, 何泾沙, 张昱. 物联网环境下基于SM9算法和区块链技术的身份认证方法[J]. 信息网络安全, 2024, 24(2): 179-187. |
| [3] | 顾妍妍, 沈丽敏, 高晨旭, 朱婷. 车载网中高效安全的无证书聚合签名方案[J]. 信息网络安全, 2024, 24(2): 188-202. |
| [4] | 赵耿, 马英杰, 董有恒. 混沌密码理论研究与应用新进展[J]. 信息网络安全, 2024, 24(2): 203-216. |
| [5] | 何业锋, 权家辉, 刘妍. 基于混合区块链的位置隐私保护方案[J]. 信息网络安全, 2024, 24(2): 229-238. |
| [6] | 钮可, 梁钰承, 孟逸飞, 汪晶晶. 基于双域标记的视频鲁棒可逆水印算法[J]. 信息网络安全, 2024, 24(2): 239-251. |
| [7] | 黄海燕, 艾宇昕, 梁琳琳, 李赞. 窃听者攻击下的RSMA无线通信系统中的物理层安全性能分析[J]. 信息网络安全, 2024, 24(2): 252-261. |
| [8] | 林怡航, 周鹏远, 吴治谦, 廖勇. 基于触发器逆向的联邦学习后门防御方法[J]. 信息网络安全, 2024, 24(2): 262-271. |
| [9] | 赵鹏程, 于俊清, 李冬. 一种基于深度学习的SRv6网络流量调度优化算法[J]. 信息网络安全, 2024, 24(2): 272-281. |
| [10] | 王鹃, 龚家新, 蔺子卿, 张晓娟. 多维深度导向的Java Web模糊测试方法[J]. 信息网络安全, 2024, 24(2): 282-292. |
| [11] | 金志刚, 丁禹, 武晓栋. 融合梯度差分的双边校正联邦入侵检测算法[J]. 信息网络安全, 2024, 24(2): 293-302. |
| [12] | 颜海龙, 王树兰. 基于国产密码技术的不动产登记集成办事平台设计与实现[J]. 信息网络安全, 2024, 24(2): 303-308. |
| [13] | 孙红哲, 王坚, 王鹏, 安雨龙. 基于Attention-BiTCN的网络入侵检测方法[J]. 信息网络安全, 2024, 24(2): 309-318. |
| [14] | 余尚戎, 肖景博, 殷琪林, 卢伟. 关注社交异配性的社交机器人检测框架[J]. 信息网络安全, 2024, 24(2): 319-327. |
| [15] | 赖成喆, 赵益宁, 郑东. 基于同态加密的隐私保护与可验证联邦学习方案[J]. 信息网络安全, 2024, 24(1): 93-105. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||