信息网络安全 ›› 2023, Vol. 23 ›› Issue (10): 64-69.doi: 10.3969/j.issn.1671-1122.2023.10.009
基于HPC的虚拟化平台异常检测技术研究与实现
- 1.南开大学网络空间安全学院,天津 300350
2.天津市网络与数据安全技术重点实验室,天津 300350
-
收稿日期:2023-06-26出版日期:2023-10-10发布日期:2023-10-11 -
通讯作者:张健 E-mail:zhang.jian@nankai.edu.cn -
作者简介:邢凌凯(2001—),男,江苏,硕士研究生,主要研究方向为云安全、网络安全|张健(1968—),男,天津,正高级工程师,博士,CCF会员,主要研究方向为云安全、网络安全和系统安全 -
基金资助:国家重点研发计划(2022YFB3103202);天津市重点研发计划(20YFZCGX00680);天津市新一代人工智能科技重大专项(19ZXZNGX00090)
Research and Implementation on Abnormal Behavior Detection Technology of Virtualization Platform Based on HPC
XING Lingkai1,2, ZHANG Jian1,2( )
)
- 1. College of Cyber Science, Nankai University, Tianjin 300350, China
2. Tianjin Key Laboratory of Network and Data Security Technology, Tianjin 300350, China
-
Received:2023-06-26Online:2023-10-10Published:2023-10-11
摘要:
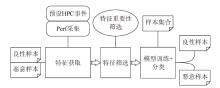
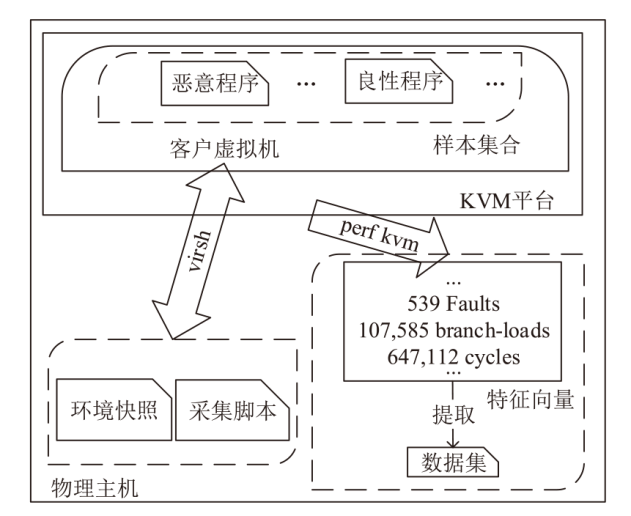
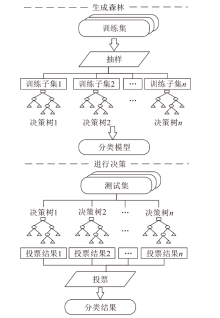
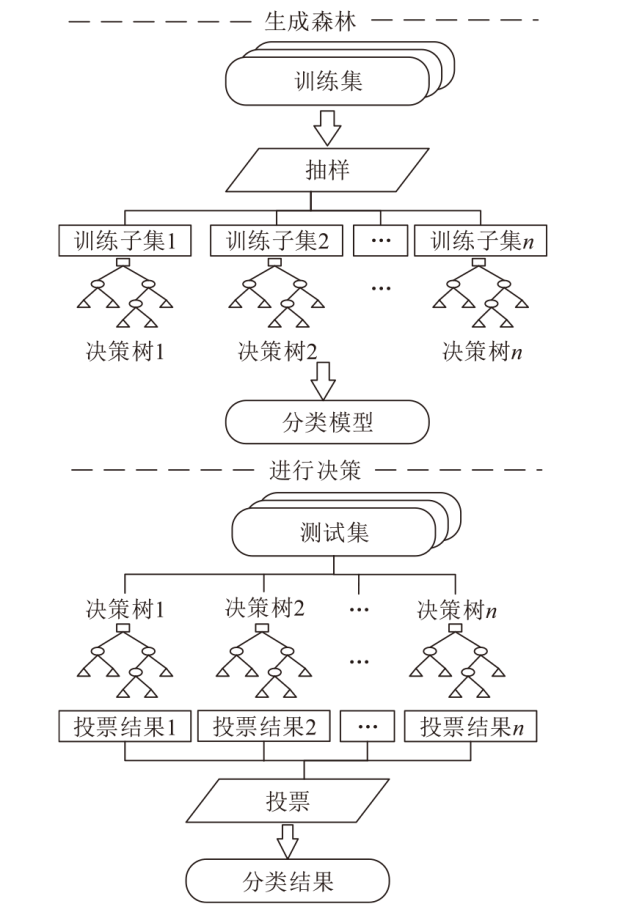
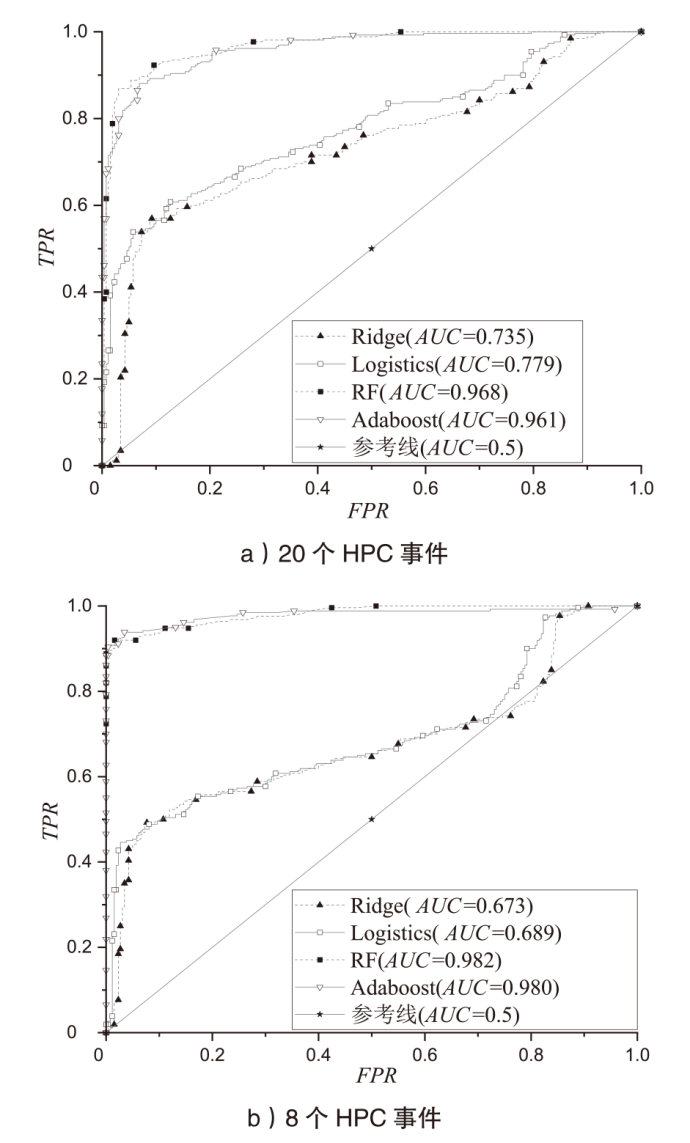
文章针对虚拟化平台异常行为检测问题提出一种基于硬件性能计数器 (Hardware Performance Counter,HPC)和集成学习的动态检测方法。该方法基于KVM虚拟化平台,采集平台运行样本时的HPC值,按照随机森林(Random Forest,RF)学习时产生的特征重要性分数进行特征筛选,提高RF分类模型的准确率,实现异常检测。文章在平台上采集了1040个良性程序样本和1040个恶意程序样本,在特征筛选阶段选取8个判断恶意样本的重要HPC事件。实验结果表明,特征筛选后的RF分类模型在测试集上可以达到95.38%的准确率,相较于特征筛选前的同类模型和其他传统机器学习模型具有更高的准确性和稳定性。
中图分类号:
引用本文
邢凌凯, 张健. 基于HPC的虚拟化平台异常检测技术研究与实现[J]. 信息网络安全, 2023, 23(10): 64-69.
XING Lingkai, ZHANG Jian. Research and Implementation on Abnormal Behavior Detection Technology of Virtualization Platform Based on HPC[J]. Netinfo Security, 2023, 23(10): 64-69.
表2
HPC事件特征重要性排序
| HPC事件名称 | 平均权重 | HPC事件名称 | 平均权重 |
|---|---|---|---|
| instructions | 0.203351 | iTLB-load-misses | 0.025661 |
| L1-icache-load-misses | 0.167181 | dTLB-stores | 0.024406 |
| cache-references | 0.092756 | dTLB-loads | 0.024112 |
| branch-load-misses | 0.065809 | branch-loads | 0.023056 |
| L1-dcache-load-misses | 0.064845 | L1-dcache-stores | 0.022282 |
| cycles | 0.062174 | L1-dcache-loads | 0.021630 |
| faults | 0.051012 | dTLB-load-misses | 0.021491 |
| iTLB-loads | 0.032164 | dTLB-store-misses | 0.016320 |
| LLC-store-misses | 0.030016 | LLC-loads | 0.014983 |
| LLC-load-misses | 0.022998 | LLC-stores | 0.013761 |
| [1] | VMware. VMware Security Response Center(vSRC) Response to ‘ESXiArgs’ Ransomware Attacks[EB/OL]. (2023-02-06) [2023-04-20]. https://blogs.vmware.com/security/2023/02/83330.html. |
| [2] | Shenzhen Yunzhan Information Technology Co., Ltd. Ransomware Virus Targeting VMware ESXi Server Attacks are Spreading, Ransomware Defense, Emergency Rescue, Hardening Guide[EB/OL]. (2023-03-28) [2023-04-20]. https://www.sohu.com/a/660016097_121679003. |
| 深圳云展信息技术有限公司. 勒索病毒针对VMware ESXi服务器攻击正在蔓延,勒索防御,紧急救援,加固指南[EB/OL]. (2023-03-28) [2023-04-20]. https://www.sohu.com/a/660016097_121679003. | |
| [3] | UEKI K, KOURAI K. Fine-Grained Autoscaling with In-VM Containers and VM Introspection[C]// IEEE. 2020 IEEE/ACM 13th International Conference on Utility and Cloud Computing(UCC). New York: IEEE, 2020: 155-164. |
| [4] | SHARIF M, LEE W, CUI Weidong. Secure In-VM Monitoring Using Hardware Virtualization[C]// ACM. ACM Conference on Computer and Communications Security. New York: ACM, 2009: 477-488. |
| [5] | BILL B. The Rootkit Arsenal Escape and Evasion in the Dark Corners of the System[M]. Sudbury: Wordware Publishing, 2012. |
| [6] | YAN Guanglu, LUO Senlin, LIU Wangtong, et al. Highly Reliable In-VM Hidden Process Adversarial Detection Method[J]. Transaction of Beijing Institute of Technology, 2018, 38(3): 305-312. |
| 闫广禄, 罗森林, 刘望桐, 等. 高可靠In-VM隐藏进程对抗检测方法[J]. 北京理工大学学报, 2018, 38(3):305-312. | |
| [7] | ENRICO B, PIETRO F, MARIUS M, et al. Branch History Injection: On the Effectiveness of Hardware Mitigations Against Cross-Privilege Spectre-v2 Attacks[C]// NDSS. 30th ISOC Network and Distributed System Security Symposium. San Diego: ISOC, 2023: 1-18. |
| [8] | ROBERT B, HANS N J, THILO K, et al. One Glitch to Rule Them All: Fault Injection Attacks Against AMD’s Secure Encrypted Virtualization[C]// ACM. The 2021 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2022: 971-988. |
| [9] | PATEL N, SASAN A, HOMAYOUN H. Analyzing Hardware Based Malware Detectors[C]// IEEE. The 54th Annual Design Automation Conference 2017. New York: IEEE, 2017: 1-6. |
| [10] | NIU Weina, ZHAO Chengyang, ZHANG Xiaosong, et al. ROPDetector: A Real-Time Detection Method for ROP Attacks Based on Hardware Performance Counters[J]. Chinese Journal of Computers, 2021, 44(4): 761-772. |
| 牛伟纳, 赵成洋, 张小松, 等. ROPDetector:一种基于硬件性能计数器的ROP攻击实时检测方法[J]. 计算机学报, 2021, 44(4):761-772. | |
| [11] | Shanghai Yucheng Information Technology Co., Ltd. Introduction and Use of System-Level Performance Analysis Tools PERF[EB/OL]. (2019-11-18) [2023-04-23]. https://www.cnblogs.com/xuanbjut/p/11884262.html. |
| 上海语程信息科技有限公司. 系统级性能分析工具PERF的介绍与使用[EB/OL]. (2019-11-18) [2023-04-23]. https://www.cnblogs.com/xuanbjut/p/11884262.html. | |
| [12] | REN Yongjie, CHENG Zhou. KVM in Action: Principles, Advanced and Performance Tuning[M]. Beijing: China Machine Press, 2019. |
| 任永杰, 程舟. KVM实战:原理、进阶与性能调优[M]. 北京: 机械工业出版社, 2019. | |
| [13] | RED Hat. Perf_events[EB/OL]. (2018-04-20) [2023-04-23]. https://www.linux-kvm.org/page/Perf_events. |
| [14] | XU Jiayun, LI Yingjiu, ROBERT H, et al. Differential Training: A Generic Framework to Reduce Label Noises for Android Malware Detection[C]// NDSS. The Network and Distributed System Security Symposium(NDSS) 2021. San Diego: ISOC, 2021: 1-14. |
| [15] | ZHOU Zhihua. Machine Learning[M]. Beijing: Tsinghua University Press, 2016. |
| 周志华. 机器学习[M]. 北京: 清华大学出版社, 2016. | |
| [16] | SINGH B, EVTYUSHKIN D, EWELL J, et al. On the Detection of Kernel-Level Rootkits Using Hardware Performance Counters[C]// ACM. Asia Conference on Computer and Communications Security(ASIACCS) 2017. New York: ACM, 2017: 483-493. |
| [17] | SAYADI H, SAI M, HOUMANSADR A, et al. Comprehensive Assessment of Run-Time Hardware-Supported Malware Detection Using General and Ensemble Learning[C]// ACM. International Conference on Computing Frontiers. New York: ACM, 2018: 212-215. |
| [18] | GAN Yuyou, MAO Yuhao, ZHANG Xuhong, et al. “Is Your Explanation Stable?”: A Robustness Evaluation Framework for Feature Attribution[C]// ACM. The 2022 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2022: 1157-1171. |
| [19] | SAYADI H, PATEL N, MANOJ P, et al. Ensemble Learning for Effective Run-Time Hardware-Based Malware Detection: A Comprehensive Analysis and Classification[C]// ACM. ACM/IEEE Design Automation Conference. New York: ACM, 2018: 1-6. |
| [1] | 曹越, 吕臣臣, 孙娅苹, 张宇昂. 面向车联网环境的异常行为检测机制研究综述[J]. 信息网络安全, 2023, 23(4): 10-19. |
| [2] | 王浩洋, 李伟, 彭思维, 秦元庆. 一种基于集成学习的列车控制系统入侵检测方法[J]. 信息网络安全, 2022, 22(5): 46-53. |
| [3] | 林发鑫, 张健. 虚拟化平台异常行为检测系统的设计与实现[J]. 信息网络安全, 2022, 22(11): 62-67. |
| [4] | 曾颖明, 王斌, 郭敏. 基于群体智能的网络安全协同防御技术研究[J]. 信息网络安全, 2020, 20(9): 52-56. |
| [5] | 王湘懿, 张健. 基于图像和机器学习的虚拟化平台异常检测[J]. 信息网络安全, 2020, 20(9): 92-96. |
| [6] | 冉金鹏, 王翔, 赵尚弘, 高航航. 基于果蝇优化的虚拟SDN网络映射算法[J]. 信息网络安全, 2020, 20(6): 65-74. |
| [7] | 荆涛, 万巍. 面向属性迁移状态的P2P网络行为分析方法研究[J]. 信息网络安全, 2020, 20(1): 16-25. |
| [8] | 白嘉萌, 寇英帅, 刘泽艺, 查达仁. 云计算平台基于角色的权限管理系统设计与实现[J]. 信息网络安全, 2020, 20(1): 75-82. |
| [9] | 马泽文, 刘洋, 徐洪平, 易航. 基于集成学习的DoS攻击流量检测技术[J]. 信息网络安全, 2019, 19(9): 115-119. |
| [10] | 时向泉, 陶静, 赵宝康. 面向虚拟化环境的网络访问控制系统[J]. 信息网络安全, 2019, 19(10): 1-9. |
| [11] | 李月, 姜玮, 季佳华, 段德忠. 一种基于虚拟化平台的安全外包技术研究[J]. 信息网络安全, 2018, 18(5): 82-88. |
| [12] | 李月, 姜玮, 季佳华, 段德忠. 一种基于虚拟化平台的安全外包技术研究[J]. 信息网络安全, 2018, 18(5): 82-88. |
| [13] | 朱维军, 樊永文, 班绍桓. 动态虚拟MSISDN的拟态自动机模型与安全性验证方法[J]. 信息网络安全, 2018, 18(4): 15-22. |
| [14] | 杜春来, 孔丹丹, 王景中, 谭兴邦. 一种基于指令虚拟化的代码保护模型[J]. 信息网络安全, 2017, 17(2): 22-28. |
| [15] | 张健, 蔡长亮, 宫良一, 顾兆军. 基于KVM虚拟化环境的异常行为检测技术研究[J]. 信息网络安全, 2017, 17(11): 1-6. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||