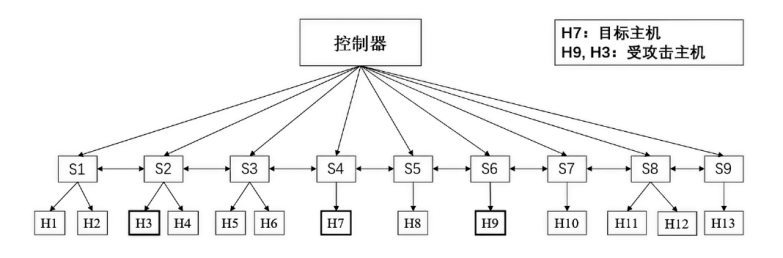
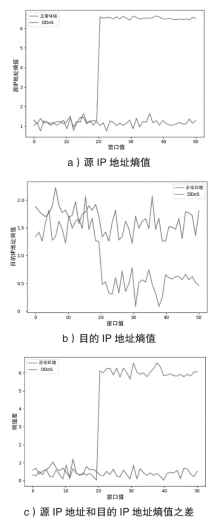
信息网络安全 ›› 2023, Vol. 23 ›› Issue (10): 1-7.doi: 10.3969/j.issn.1671-1122.2023.10.001
SDN网络中基于联合熵与多重聚类的DDoS攻击检测
- 1.福州大学计算机与大数据学院,福州 350116
2.福建省网络计算与智能信息处理重点实验室,福州 350116
3.达尔豪斯大学电气与计算机工程学院,哈利法克斯 B3J1Z1
-
收稿日期:2023-06-28出版日期:2023-10-10发布日期:2023-10-11 -
通讯作者:张浩 E-mail:zhanghao@fzu.edu.cn -
作者简介:王智(1998—),男,山西,硕士研究生,CCF会员,主要研究方向为网络安全、机器学习|张浩(1981—),男,安徽,副教授,博士,CCF会员,主要研究方向为信息安全、安全大数据分析和计算智能算法|顾建军(1972—),男,江苏,教授,博士,主要研究方向为机器学习、神经网络和控制、生物医学工程和康复工程 -
基金资助:国家自然科学基金(U1804263);国家自然科学基金(U21A20472);国家留学基金(202006655011);福建省自然科学基金(2020J01130167);福建省自然科学基金(2021J01616);福建省自然科学基金(2021J01625)
A Hybrid Method of Joint Entropy and Multiple Clustering Based DDoS Detection in SDN
WANG Zhi1,2, ZHANG Hao1,2( ), Jason GU3
), Jason GU3
- 1. Colleage of Computer and Date Science, Fuzhou University, Fuzhou 350116, China
2. Fujian Key Laboratory of Network Computing and Intelligent Information Processing, Fuzhou 350116, China
3. Department of Electrical and Computer Engineering, Dalhousie University, Halifax B3J1Z1, Canada
-
Received:2023-06-28Online:2023-10-10Published:2023-10-11
摘要:
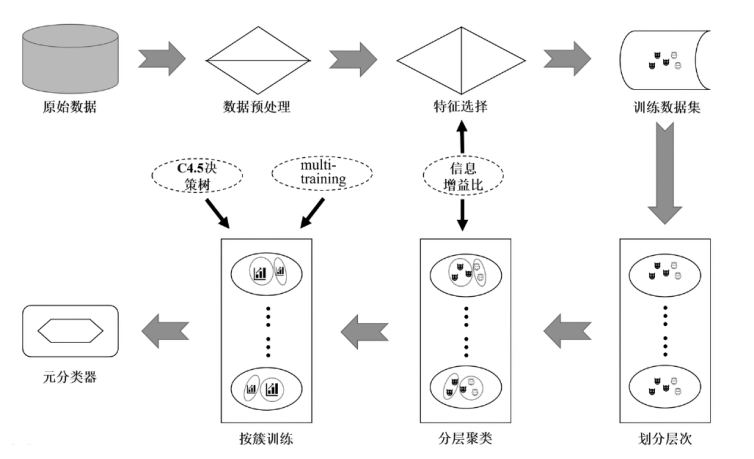
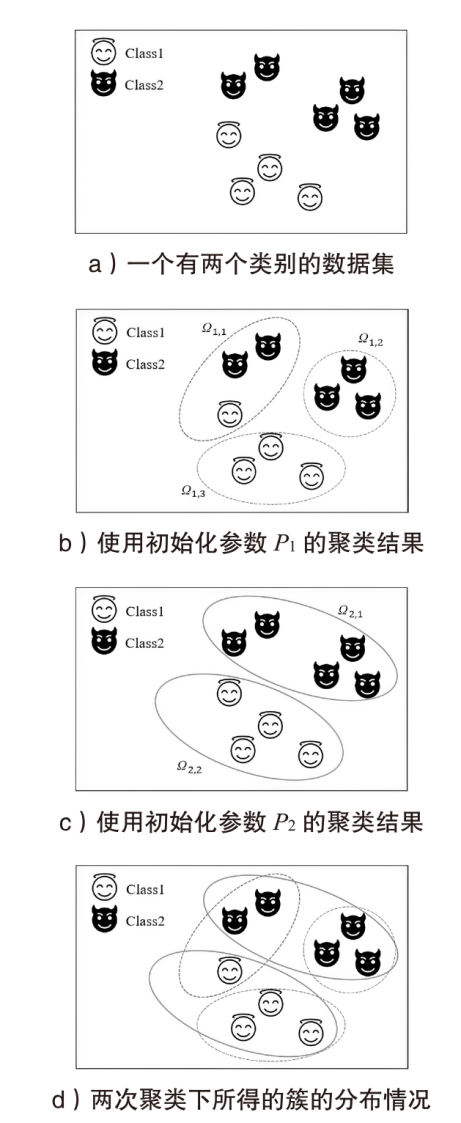
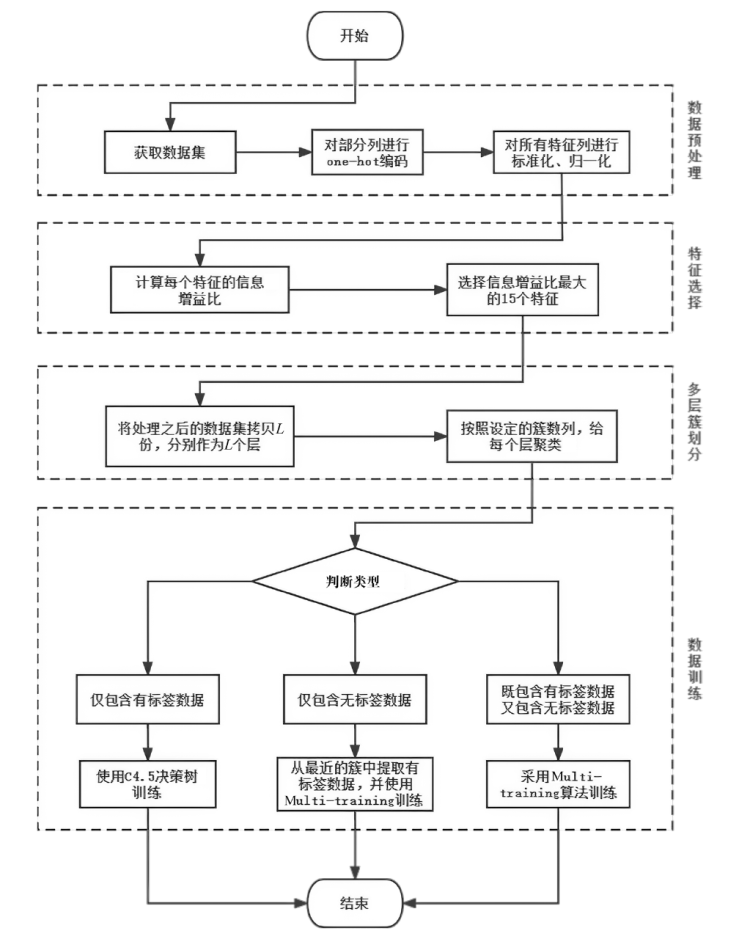
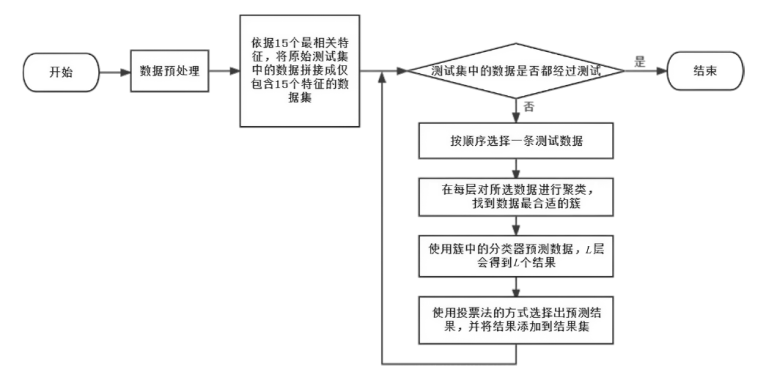
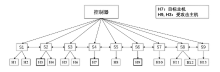
软件定义网络(Software Defined Networking,SDN)作为一种新兴的网络范式,在带来便利性的同时也引入了更为严峻的分布式拒绝服务攻击(Distributed Denial of Service Attacks,DDoS)风险。现有的模型通常是使用机器学习模型来检测DDoS攻击,忽略了模型给SDN控制器带来的额外开销。为了更加高效且精确地检测DDoS攻击,文章采取了多级检测模块的方式,即一级模块通过计算当前流量窗口的联合熵快速检测异常,二级模块采用半监督模型,并使用特征选择、multi-training算法、多重聚类等技术,通过训练多个局部模型提高检测性能。与现有的其他模型相比,该模型在多个数据集上均表现更好,拥有更好的检测精度和泛化能力。
中图分类号:
引用本文
王智, 张浩, 顾建军. SDN网络中基于联合熵与多重聚类的DDoS攻击检测[J]. 信息网络安全, 2023, 23(10): 1-7.
WANG Zhi, ZHANG Hao, Jason GU. A Hybrid Method of Joint Entropy and Multiple Clustering Based DDoS Detection in SDN[J]. Netinfo Security, 2023, 23(10): 1-7.
| [1] | KOPONEN T, CASADO M, GUDE N, et al. Distributed Control Platform for Large-Scale Production Networks: USA, 8. 830. 823[P]. 2014-09-09. |
| [2] |
KAUR S, KUMAR K, AGGARWAL N, et al. A Comprehensive Survey of DDoS Defense Solutions in SDN: Taxonomy, Research Challenges, and Future Directions[J]. Computers & Security, 2021, 110(1): 102423-102431.
doi: 10.1016/j.cose.2021.102423 URL |
| [3] |
SINGH J, BEHAL S. Detection and Mitigation of DDoS Attacks in SDN: A Comprehensive Review, Research Challenges and Future Directions[J]. Computer Science Review, 2020, 37: 100279-100294.
doi: 10.1016/j.cosrev.2020.100279 URL |
| [4] |
JASIM M N, GAATA M T. K-Means Clustering-Based Semi-Supervised for DDoS Attacks Classification[J]. Bulletin of Electrical Engineering and Informatics, 2022, 11(6): 3570-3576.
doi: 10.11591/eei.v11i6 URL |
| [5] |
KALKAN K, ALTAY L, GUR G, et al. JESS: Joint Entropy-Based DDoS Defense Scheme in SDN[J]. IEEE Journal on Selected Areas in Communications, 2018, 36(10): 2358-2372.
doi: 10.1109/JSAC.2018.2869997 URL |
| [6] |
MAHESHWARI A, MEHRAJ B, KHAN M S, et al. An Optimized Weighted Voting Based Ensemble Model for DDoS Attack Detection and Mitigation in SDN Environment[J]. Microprocessors and Microsystems, 2022, 89: 104412-104438.
doi: 10.1016/j.micpro.2021.104412 URL |
| [7] | YU Junqing, LI Zizun, WU Chi, et al. A Two-Stage DDoS Attack Detection and Defense Method in Software Defined Network[J]. Netinfo Security, 2022, 22(1): 1-8. |
| 于俊清, 李自尊, 吴驰, 等. 面向软件定义网络的两级DDoS攻击检测与防御[J]. 信息网络安全, 2022, 22(1): 1-8. | |
| [8] |
VILLA-PÉREZ M E, ALVAREZ-CARMONA M A, LOYOLA-GONZALEZ O, et al. Semi-Supervised Anomaly Detection Algorithms: A Comparative Summary and Future Research Directions[J]. Knowledge-Based Systems, 2021, 218: 106878-100686.
doi: 10.1016/j.knosys.2021.106878 URL |
| [9] |
TAN Liang, PAN Yue, WU Jing, et al. A New Framework for DDoS Attack Detection and Defense in SDN Environment[J]. IEEE Access, 2020, 8: 161908-161919.
doi: 10.1109/Access.6287639 URL |
| [10] | WANG Cong, CUI Yunhe, GAO Hongfeng. DDoS Attack Detection Based on Improved D-S Theory in SDN[J]. Computer System & Applications, 2022, 31(8): 354-360. |
| 王聪, 崔允贺, 高鸿峰. SDN环境下基于改进D-S理论的DDoS攻击检测[J]. 计算机系统应用, 2022, 31(8): 354-360. | |
| [11] |
SABIROV D S, SHEPELEVICH I S. Information Entropy in Chemistry: An Overview[J]. Entropy, 2021, 23(10): 1240-1249.
doi: 10.3390/e23101240 URL |
| [12] |
ZHANG Long, WANG Jinsong. A Hybrid Method of Entropy and SSAE-SVM Based DDoS Detection and Mitigation Mechanism in SDN[J]. Computers & Security, 2022, 115: 102604-102620.
doi: 10.1016/j.cose.2022.102604 URL |
| [13] |
SINAGA K P, YANG M S. Unsupervised K-Means Clustering Algorithm[J]. IEEE Access, 2020, 8: 80716-80727.
doi: 10.1109/Access.6287639 URL |
| [14] |
RAHMAN A, VERMA B. Novel Layered Clustering-Based Approach for Generating Ensemble of Classifiers[J]. IEEE Transactions on Neural Networks, 2011, 22(5): 781-792.
doi: 10.1109/TNN.2011.2118765 pmid: 21486714 |
| [15] | QUINLAN J R. Induction of Decision Trees[J]. Machine Learning, 1986, 1: 81-106. |
| [16] |
ZHOU Zhihua, LI Ming. Tri-Training: Exploiting Unlabeled Data Using Three Classifiers[J]. IEEE Transactions on Knowledge and Data Engineering, 2005, 17(11): 1529-1541.
doi: 10.1109/TKDE.2005.186 URL |
| [17] |
AHUJA N, SINGAL G, MUKHOPADHYAY D, et al. Automated DDOS Attack Detection in Software DefIned Networking[J]. Journal of Network and Computer Applications, 2021, 187: 103108-102122.
doi: 10.1016/j.jnca.2021.103108 URL |
| [18] | NING Xin, WANG Xinran, XU Shaohui, et al. A Review of Research on Co-Training[J]. Concurrency and Computation: Practice and Experience, 2021, 35(18): 1-16. |
| [19] |
Al-JARRAH O Y, Al-HAMMDI Y, YOO P D, et al. Semi-Supervised Multi-Layered Clustering Model for Intrusion Detection[J]. Digital Communications and Networks, 2018, 4(4): 277-286.
doi: 10.1016/j.dcan.2017.09.009 URL |
| [1] | 林义钧, 吴渝, 李红波. 基于Affinity Propagation算法的半监督微博水军识别[J]. 信息网络安全, 2022, 22(3): 85-96. |
| [2] | 于俊清, 李自尊, 吴驰, 赵贻竹. 面向软件定义网络的两级DDoS攻击检测与防御[J]. 信息网络安全, 2022, 22(1): 1-8. |
| [3] | 范广宇, 王兴伟, 贾杰, 黄敏. SDN应用平面与控制平面安全交互方法[J]. 信息网络安全, 2021, 21(6): 70-79. |
| [4] | 李朝阳, 谭晶磊, 胡瑞钦, 张红旗. 基于双重地址跳变的移动目标防御方法[J]. 信息网络安全, 2021, 21(2): 24-33. |
| [5] | 王鹃, 杨泓远, 樊成阳. 一种基于多阶段攻击响应的SDN动态蜜罐[J]. 信息网络安全, 2021, 21(1): 27-40. |
| [6] | 冉金鹏, 王翔, 赵尚弘, 高航航. 基于果蝇优化的虚拟SDN网络映射算法[J]. 信息网络安全, 2020, 20(6): 65-74. |
| [7] | 王健, 王语杰, 韩磊. 基于突变模型的SDN环境中DDoS攻击检测方法[J]. 信息网络安全, 2020, 20(5): 11-20. |
| [8] | 周亚球, 任勇毛, 李琢, 周旭. 基于SDN的科学DMZ研究与实现[J]. 信息网络安全, 2019, 19(9): 134-138. |
| [9] | 赖成喆, 王文娟. 面向车队的安全且具备隐私保护的移动性管理框架[J]. 信息网络安全, 2018, 18(7): 36-46. |
| [10] | 石悦, 李相龙, 戴方芳. 一种基于属性基加密的增强型软件定义网络安全框架[J]. 信息网络安全, 2018, 18(1): 15-22. |
| [11] | 李剑锋, 刘渊, 张浩, 王晓锋. 面向IaaS云平台的路由转发优化研究与实现[J]. 信息网络安全, 2017, 17(9): 10-15. |
| [12] | 徐洋, 陈燚, 何锐, 谢晓尧. SDN中DDoS检测及多层防御方法研究[J]. 信息网络安全, 2017, 17(12): 22-28. |
| [13] | 齐宇. SDN安全研究[J]. 信息网络安全, 2016, 16(9): 69-72. |
| [14] | 陈颖聪, 陈广清, 陈智明, 万能. 面向智能电网SDN的二进制代码分析漏洞扫描方法研究[J]. 信息网络安全, 2016, 16(7): 35-39. |
| [15] | 蒋宽, 杨鹏. 基于数据包回溯的软件定义网络中的故障排除[J]. 信息网络安全, 2016, 16(3): 71-76. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||