信息网络安全 ›› 2023, Vol. 23 ›› Issue (8): 76-85.doi: 10.3969/j.issn.1671-1122.2023.08.007
联盟链下基于联邦学习聚合算法的入侵检测机制优化研究
- 1.中国科学院信息工程研究所,北京 100085
2.中国科学院大学网络空间安全学院,北京 100049
3.中国电子技术标准化研究院,北京 100007
-
收稿日期:2023-04-18出版日期:2023-08-10发布日期:2023-08-08 -
通讯作者:张珠君 E-mail:zhangzhujun@iie.ac.cn -
作者简介:彭翰中(2000—),男,湖南,硕士研究生,主要研究方向为物联网安全、区块链安全|张珠君(1987—),女,河北,工程师,博士,主要研究方向为物联网安全、区块链技术与应用|闫理跃(1986—),男,北京,工程师,博士,主要研究方向为供应链应用与安全|胡成林(1987—),男,北京,工程师,硕士,主要研究方向为供应链应用与安全 -
基金资助:国家重点研发计划(2019YFB1005204)
Research on Intrusion Detection Mechanism Optimization Based on Federated Learning Aggregation Algorithm under Consortium Chain
PENG Hanzhong1,2, ZHANG Zhujun1,2( ), YAN Liyue3, HU Chenglin3
), YAN Liyue3, HU Chenglin3
- 1. Institute of Information Engineering, Chinese Academy of Sciences, Beijing 100085, China
2. School of Cyber Security, University of Chinese Academy of Sciences, Beijing 100049, China
3. Chinese Electronics Standardization Institute, Beijing 100007, China
-
Received:2023-04-18Online:2023-08-10Published:2023-08-08 -
Contact:ZHANG Zhujun E-mail:zhangzhujun@iie.ac.cn
摘要:
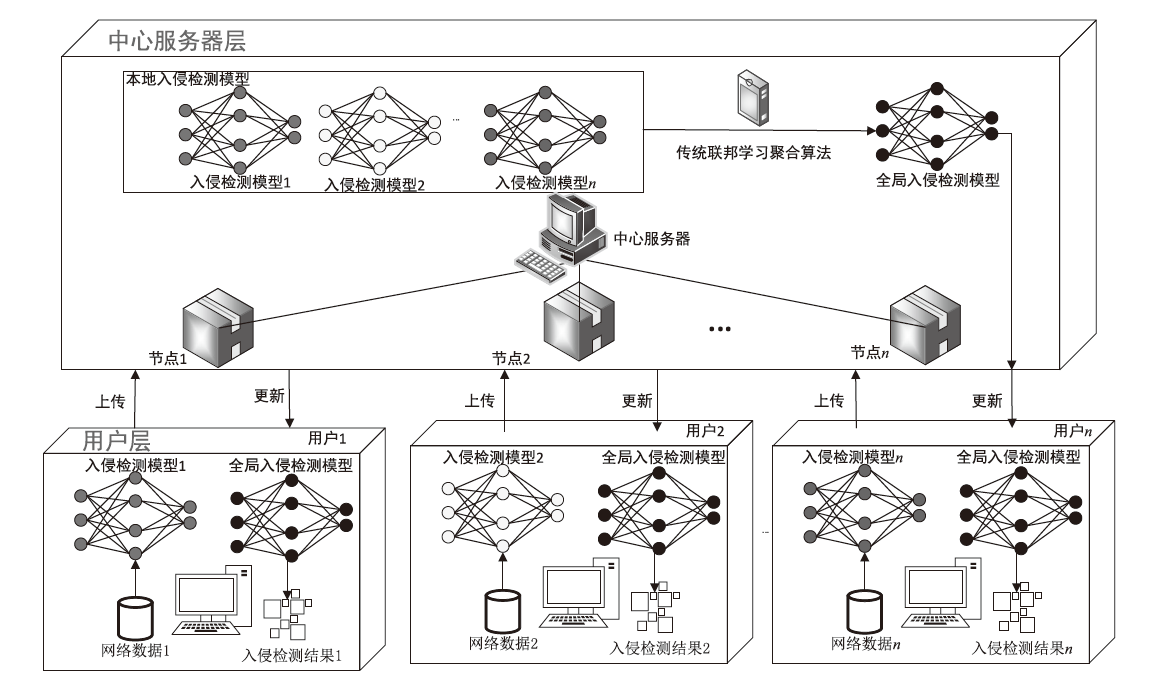
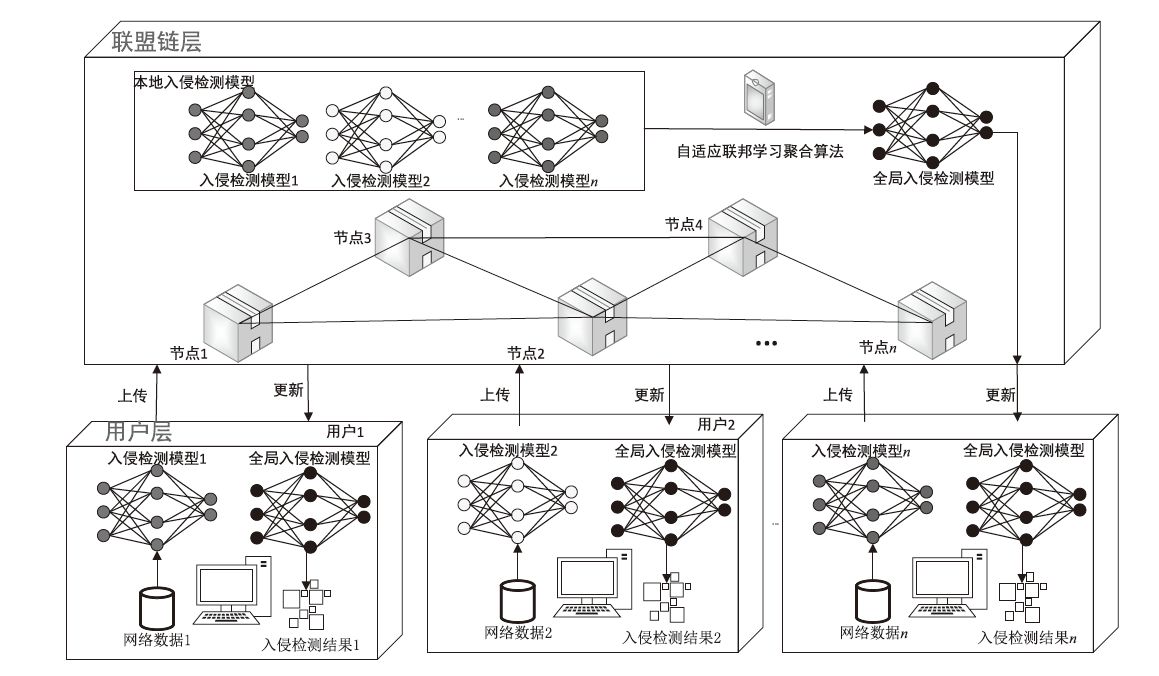
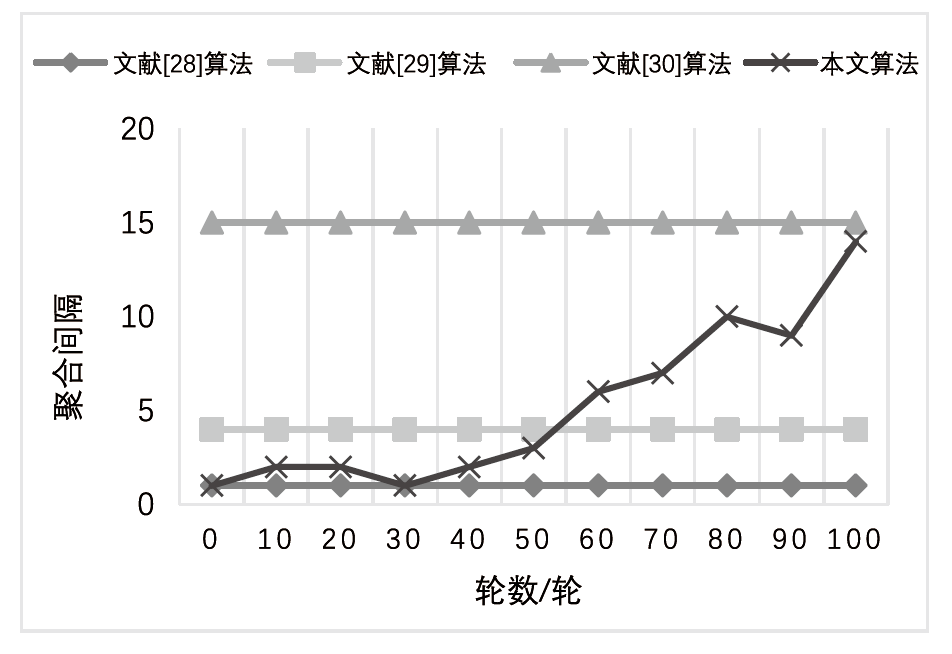
近年来,联邦学习备受关注,因为它能在保护用户隐私的前提下训练和聚合入侵检测模型。联盟链作为一种高效且可控的分布式账本技术,与联邦学习技术结合被应用于多节点入侵检测场景。然而,传统的联盟链下基于联邦学习聚合入侵检测模型的算法存在缺陷,无法根据网络环境动态调整聚合算法参数,导致通信成本过高。因此,文章根据联盟链网络环境设计自适应联邦学习聚合算法,动态调整入侵检测模型聚合间隔,以平衡模型准确度与通信成本。理论分析和实验结果表明,相较于传统联邦学习聚合算法,该入侵检测模型的聚合过程在保证了模型准确度的前提下降低了系统通信成本,提高了模型聚合效率,具有良好的应用前景。
中图分类号:
引用本文
彭翰中, 张珠君, 闫理跃, 胡成林. 联盟链下基于联邦学习聚合算法的入侵检测机制优化研究[J]. 信息网络安全, 2023, 23(8): 76-85.
PENG Hanzhong, ZHANG Zhujun, YAN Liyue, HU Chenglin. Research on Intrusion Detection Mechanism Optimization Based on Federated Learning Aggregation Algorithm under Consortium Chain[J]. Netinfo Security, 2023, 23(8): 76-85.
| [1] |
APRUZZESE G, PAJOLA L, CONTI M. The Cross-Evaluation of Machine Learning-Based Network Intrusion Detection Systems[J]. IEEE Transactions on Network and Service Management, 2022, 19(4): 5152-5169.
doi: 10.1109/TNSM.2022.3157344 URL |
| [2] | ZHANG Chunying, JIA Donghao, WANG Liya, et al. Comparative Research on Network Intrusion Detection Methods Based on Machine Learning[EB/OL]. (2022-10-15)[2023-04-05]. https://doi.org/10.1016/j.cose.2022.102861. |
| [3] |
TSAI C, HSU Y, LIN C, et al. Intrusion Detection by Machine Learning: A Review[J]. Expert Systems with Applications, 2009, 36(10): 11994-12000.
doi: 10.1016/j.eswa.2009.05.029 URL |
| [4] |
WANG Ziyue, PENG Yanjun, LI Dapeng, et al. Mmnet: A Multi-Scale Deep Learning Network for the Left Ventricular Segmentation of Cardiac Mri Images[J]. Applied Intelligence, 2022, 52(5): 5225-5240.
doi: 10.1007/s10489-021-02720-9 |
| [5] | VASILOMANOLAKIS E, KARUPPAYAH S, MÜHLHÄUSER M, et al. Taxonomy and Survey of Collaborative Intrusion Detection[J]. ACM Computing Surveys (CSUR), 2015, 47(4): 1-33. |
| [6] |
GONG Maoguo, XIE Yu, PAN Ke, et al. A Survey on Differentially Private Machine Learning[J]. IEEE Computational Intelligence Magazine, 2020, 15(2): 49-64.
doi: 10.1109/MCI.10207 URL |
| [7] | ZHANG Chen, XIE Yu, BAI Hang, et al. A Survey on Federated Learning[EB/OL]. (2022-10-15)[2023-04-05]. https://doi.org/10.1016/j.knosys.2021.106775. |
| [8] |
MOTHUKURI V, KHARE P, PARIZI R M, et al. Federated-Learning-Based Anomaly Detection for IoT Security Attacks[J]. IEEE Internet of Things Journal, 2021, 9(4): 2545-2554.
doi: 10.1109/JIOT.2021.3077803 URL |
| [9] | MA Chuan, LI Jun, DING Ming, et al. On Safeguarding Privacy and Security in the Framework of Federated Learning[J]. IEEE Network, 2020, 34(4): 242-248. |
| [10] |
MOTHUKURI V, PARIZI R M, POURIYEH S, et al. A Survey on Security and Privacy of Federated Learning[J]. Future Generation Computer Systems, 2021, 115: 619-640.
doi: 10.1016/j.future.2020.10.007 URL |
| [11] | LI Tian, SAHU A K, TALWALKAR A, et al. Federated Learning: Challenges, Methods, and Future Directions[J]. IEEE Signal Processing Magazine, 2020, 37(3): 50-60. |
| [12] |
ZHENG Zibin, XIE Shaoan, DAI Hongning, et al. Blockchain Challenges and Opportunities: A Survey[J]. International Journal of Web and Grid Services, 2018, 14(4): 352-375.
doi: 10.1504/IJWGS.2018.095647 URL |
| [13] | DIB O, BROUSMICHE K L, DURAND A, et al. Consortium Blockchains: Overview, Applications and Challenges[J]. International Journal on Advances in Telecommunications, 2018, 11: 51-64. |
| [14] |
ZHANG Weishan, LU Qinghua, YU Qiuyu, et al. Blockchain-Based Federated Learning for Device Failure Detection in Industrial IoT[J]. IEEE Internet of Things Journal, 2020, 8(7): 5926-5937.
doi: 10.1109/JIOT.2020.3032544 URL |
| [15] | ZAABAR B, CHEIKHROUHOU O, ABID M. Intrusion Detection System for IoMT through Blockchain-Based Federated Learning[C]//IEEE.2022 15th International Conference on Security of Information and Networks (SIN). New York: IEEE, 2022: 1-8. |
| [16] |
LIU Hong, ZHANG Shuaipeng, ZHANG Pengfei, et al. Blockchain and Federated Learning for Collaborative Intrusion Detection in Vehicular Edge Computing[J]. IEEE Transactions on Vehicular Technology, 2021, 70(6): 6073-6084.
doi: 10.1109/TVT.2021.3076780 URL |
| [17] | SARHAN M, LO W W, LAYEGHY S, et al. HBFL: A Hierarchical Blockchain-Based Federated Learning Framework for Collaborative IoT Intrusion Detection[EB/OL]. (2022-04-08)[2023-04-05]. https://doi.org/10.48550/arXiv.2204.04254. |
| [18] | ZHOU Wei, WANG Chao, XU Jian, et al. Decentralized Federated Learning Model for Privacy Protection Based on Blockchain[J]. Journal of Computer Research and Development, 2022, 59(11): 2423-2436. |
| 周炜, 王超, 徐剑, 等. 基于区块链的隐私保护去中心化联邦学习模型[J]. 计算机研究与发展, 2022, 59(11): 2423-2436. | |
| [19] |
TAN Rongjie, HONG Zhiyong, YU Wenhua, et al. Decentralized Federated Learning Strategy with Non-Independent Uniformly Distributed Data[J]. Computer Engineering and Applications, 2023, 59(1): 269-277.
doi: 10.3778/j.issn.1002-8331.2204-0165 |
|
谭荣杰, 洪智勇, 余文华, 等. 非独立同分布数据下的去中心化联邦学习策略[J]. 计算机工程与应用, 2023, 59(1): 269-277.
doi: 10.3778/j.issn.1002-8331.2204-0165 |
|
| [20] |
WANG Shiqiang, TUOR T, SALONIDIS T, et al. Adaptive Federated Learning in Resource Constrained Edge Computing Systems[J]. IEEE Journal on Selected Areas in Communications, 2019, 37(6): 1205-1221.
doi: 10.1109/JSAC.2019.2904348 |
| [21] | LUO Bing, LI Xiang, WANG Shiqiang, et al. Cost-Effective Federated Learning Design[C]//IEEE.IEEE INFOCOM 2021-IEEE Conference on Computer Communications. New York: IEEE, 2021: 1-10. |
| [22] |
LIN F P C, HOSSEINALIPOUR S, AZAM S S, et al. Semi-Decentralized Federated Learning with Cooperative D2D Local Model Aggregations[J]. IEEE Journal on Selected Areas in Communications, 2021, 39(12): 3851-3869.
doi: 10.1109/JSAC.2021.3118344 URL |
| [23] |
CHENG Jieren, LUO Ping, XIONG Naixue, et al. AAFL: Asynchronous-Adaptive Federated Learning in Edge-Based Wireless Communication Systems for Countering Communicable Infectious Diseasess[J]. IEEE Journal on Selected Areas in Communications, 2022, 40(11): 3172-3190.
doi: 10.1109/JSAC.2022.3211564 URL |
| [24] |
LIU Lumin, ZHANG Jun, SONG Shenghui, et al. Hierarchical Federated Learning with Quantization: Convergence Analysis and System Design[J]. IEEE Transactions on Wireless Communications, 2023, 22(1): 2-18.
doi: 10.1109/TWC.2022.3190512 URL |
| [25] | WU Jiagao, WANG Yu, SHEN Zhangchi, et al. Adaptive Client and Communication Optimizations in Federated Learning[EB/OL]. (2023-04-08)[2023-04-15]. https://doi.org/10.1016/j.is.2023.102226. |
| [26] | TANG Lun, WANG Zhiping, PU Hao, et al. Research on Efficient Federated Learning Communication Mechanism Based on Adaptive Gradient Compression[J]. Journal of Electronics and Information Technology, 2023, 45(1): 227-234. |
| 唐伦, 汪智平, 蒲昊, 等. 基于自适应梯度压缩的高效联邦学习通信机制研究[J]. 电子与信息学报, 2023, 45(1): 227-234. | |
| [27] | GONG Maoguo, GAO Yuan, WANG Jiongqian, et al. Adaptive Federated Learning Algorithm Based on Evolutionary Strategy[J]. Scientia Sinica (Informationis), 2023, 53(3): 437-453. |
| 公茂果, 高原, 王炯乾, 等. 基于进化策略的自适应联邦学习算法[J]. 中国科学:信息科学, 2023, 53(3): 437-453. | |
| [28] | WENG Jiasi, WENG Jian, ZHANG Jilian, et al. Deepchain: Auditable and Privacy-Preserving Deep Learning with Blockchain-Based Incentive[J]. IEEE Transactions on Dependable and Secure Computing, 2021, 18(5): 2438-2455. |
| [29] |
LIU Wei, CHEN Li, CHEN Yunfei, et al. Accelerating Federated Learning via Momentum Gradient Descent. IEEE Transactions on Parallel and Distributed Systems, 2020, 31(8): 1754-1766.
doi: 10.1109/TPDS.71 URL |
| [30] |
PHONG L T, AONO Y, HAYASHI T, et al. Privacy-Preserving Deep Learning via Additively Homomorphic Encryption. IEEE Transactions on Information Forensics and Security, 2018, 13(5): 1333-1345.
doi: 10.1109/TIFS.2017.2787987 URL |
| [1] | 俞惠芳, 乔一凡, 孟茹. 面向区块链金融的抗量子属性基门限环签密方案[J]. 信息网络安全, 2023, 23(7): 44-52. |
| [2] | 陈晶, 彭长根, 谭伟杰, 许德权. 基于差分隐私和秘密共享的多服务器联邦学习方案[J]. 信息网络安全, 2023, 23(7): 98-110. |
| [3] | 刘长杰, 石润华. 基于安全高效联邦学习的智能电网入侵检测模型[J]. 信息网络安全, 2023, 23(4): 90-101. |
| [4] | 张学旺, 张豪, 姚亚宁, 付佳丽. 基于群签名和同态加密的联盟链隐私保护方案[J]. 信息网络安全, 2023, 23(3): 56-61. |
| [5] | 金志刚, 刘凯, 武晓栋. 智能电网AMI领域IDS研究综述[J]. 信息网络安全, 2023, 23(1): 1-8. |
| [6] | 刘忻, 李韵宜, 王淼. 一种基于机密计算的联邦学习节点轻量级身份认证协议[J]. 信息网络安全, 2022, 22(7): 37-45. |
| [7] | 吕国华, 胡学先, 杨明, 徐敏. 基于联邦随机森林的船舶AIS轨迹分类算法[J]. 信息网络安全, 2022, 22(4): 67-76. |
| [8] | 陈彬杰, 魏福山, 顾纯祥. 基于KNN的具有隐私保护功能的区块链异常交易检测[J]. 信息网络安全, 2022, 22(3): 78-84. |
| [9] | 张学旺, 姚亚宁, 黎志鸿, 张豪. 基于联盟链和Asmuth-Bloom秘密共享算法的数据共享方案[J]. 信息网络安全, 2022, 22(11): 17-23. |
| [10] | 白宏鹏, 邓东旭, 许光全, 周德祥. 基于联邦学习的入侵检测机制研究[J]. 信息网络安全, 2022, 22(1): 46-54. |
| [11] | 徐硕, 张睿, 夏辉. 基于数据属性修改的联邦学习隐私保护策略[J]. 信息网络安全, 2022, 22(1): 55-63. |
| [12] | 路宏琳, 王利明, 杨婧. 一种新的参数掩盖联邦学习隐私保护方案[J]. 信息网络安全, 2021, 21(8): 26-34. |
| [13] | 任涛, 金若辰, 罗咏梅. 融合区块链与联邦学习的网络入侵检测算法[J]. 信息网络安全, 2021, 21(7): 27-34. |
| [14] | 路宏琳, 王利明. 面向用户的支持用户掉线的联邦学习数据隐私保护方法[J]. 信息网络安全, 2021, 21(3): 64-71. |
| [15] | 姜楠, 崔耀辉, 王健, 吴晋超. 基于上下文特征的IDS告警日志攻击场景重建方法[J]. 信息网络安全, 2020, 20(7): 1-10. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||