信息网络安全 ›› 2023, Vol. 23 ›› Issue (8): 52-65.doi: 10.3969/j.issn.1671-1122.2023.08.005
基于区块链的电力应用数据安全共享研究
覃思航1,2,3,4, 代炜琦1,2,3( ), 曾海燕4, 顾显俊4
), 曾海燕4, 顾显俊4
- 1.华中科技大学网络空间安全学院,武汉 430074
2.分布式系统安全湖北省重点实验室,武汉 430074
3.湖北省大数据安全工程技术研究中心,武汉 430074
4.国网湖北省电力有限公司武汉供电公司,武汉 430010
-
收稿日期:2023-05-20出版日期:2023-08-10发布日期:2023-08-08 -
通讯作者:代炜琦 E-mail:wqdai@hust.edu.cn -
作者简介:覃思航(1990—),男,湖北,工程师,博士研究生,主要研究方向为网络与信息安全|代炜琦(1984—),男,湖北,副教授,博士,CCF会员,主要研究方向为区块链、隐私计算、云安全、可信计算、虚拟化安全|曾海燕(1979—),女,湖北,高级工程师,硕士,主要研究方向为电力系统自动化|顾显俊(1981—),男,湖北,高级工程师,硕士,主要研究方向为信息通信 -
基金资助:国家重点研发计划(2019YFB2101700);国家自然科学基金(62072202)
Secure Sharing of Power Application Data Based on Blockchain
QIN Sihang1,2,3,4, DAI Weiqi1,2,3( ), ZENG Haiyan4, GU Xianjun4
), ZENG Haiyan4, GU Xianjun4
- 1. School of Cyber Science and Engineering, Huazhong University of Science and Technology, Wuhan 430074, China
2. Hubei Key Laboratory of Distributed System Security, Wuhan 430074, China
3. Hubei Engineering Research Center on Big Data Security, Wuhan 430074, China
4. Wuhan Power Supply Company of State Grid Hubei Electric Power Co., Ltd., Wuhan 430010, China
-
Received:2023-05-20Online:2023-08-10Published:2023-08-08 -
Contact:DAI Weiqi E-mail:wqdai@hust.edu.cn
摘要:
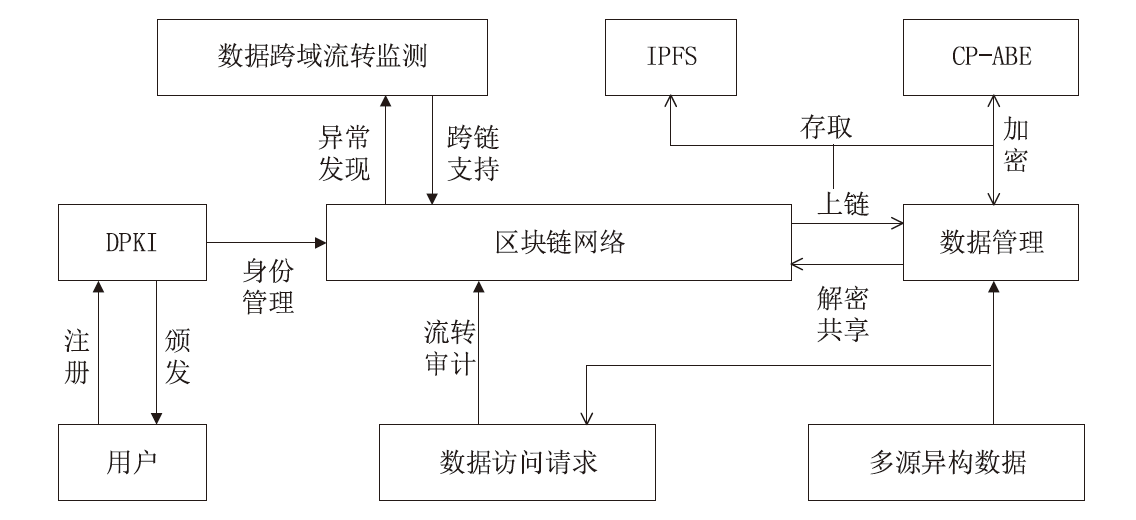
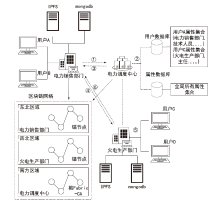
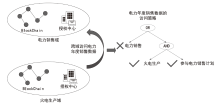
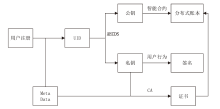
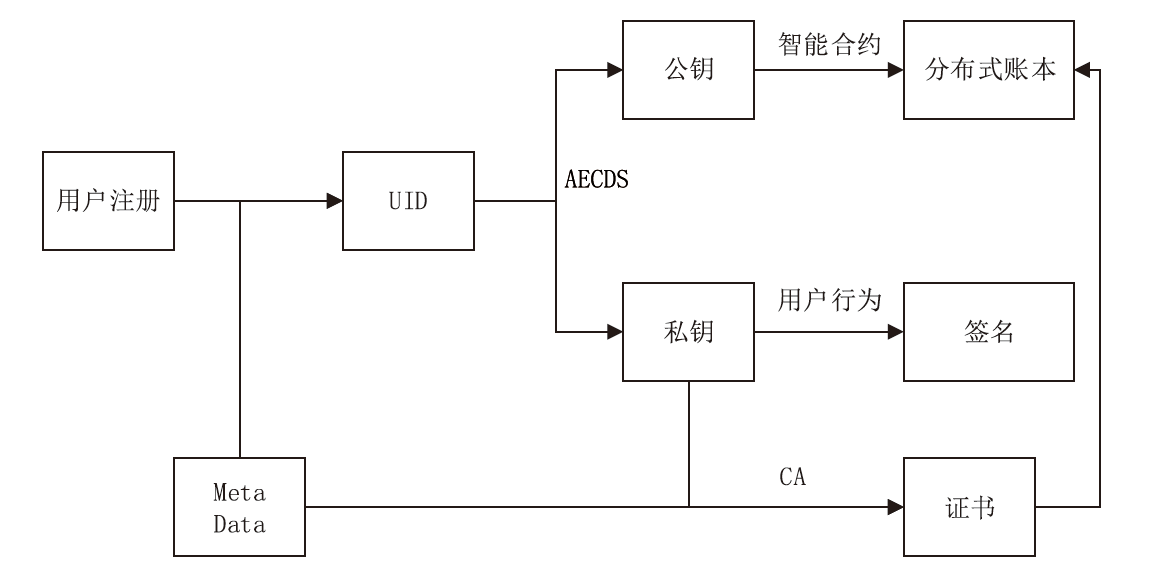
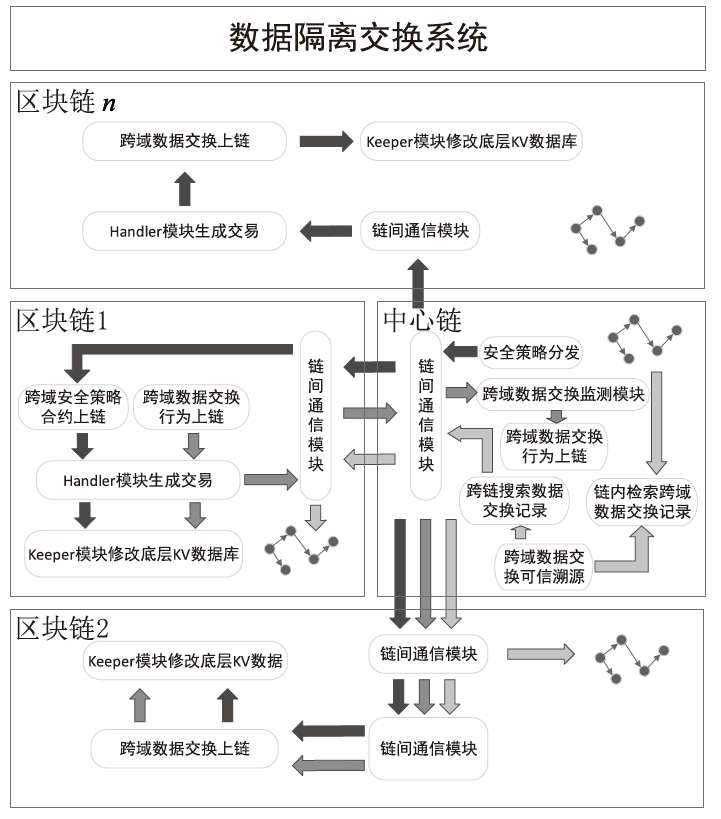
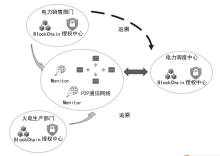
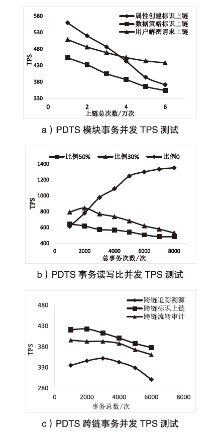
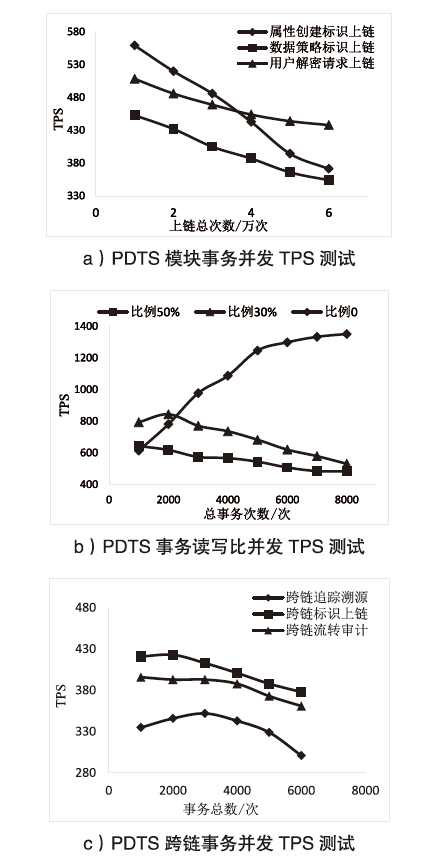
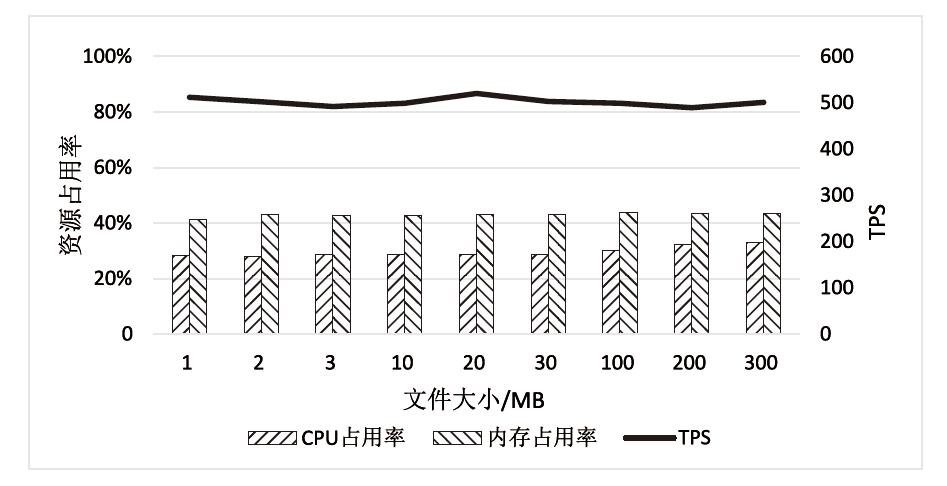
随着电力网络智能化的发展,海量的业务数据分散存储于不同的部门中,数据共享的安全性差、流转管控难,如何在保障数据安全隐私性的前提下进行数据安全可控的共享成为难题。针对以上问题,文章提出一种基于区块链的电力应用数据安全共享方法,通过基于属性加密的访问控制提高数据流转中的安全性,避免一对多数据共享时的多次加密,通过区块链分布式账本保证数据标识、加密策略、用户身份与属性密码等隐私数据的安全性,并根据智能合约审计防止用户通过篡改属性信息欺骗访问控制机制。实验结果表明,区块链智能合约能够实现机构间的数据流转管控,具备追踪溯源和异常发现能力。基于HyperLedger Fabric框架搭建的区块链网络上的数据标识上链时延在60~100 ms,TPS大于400。
中图分类号:
引用本文
覃思航, 代炜琦, 曾海燕, 顾显俊. 基于区块链的电力应用数据安全共享研究[J]. 信息网络安全, 2023, 23(8): 52-65.
QIN Sihang, DAI Weiqi, ZENG Haiyan, GU Xianjun. Secure Sharing of Power Application Data Based on Blockchain[J]. Netinfo Security, 2023, 23(8): 52-65.
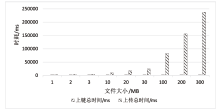
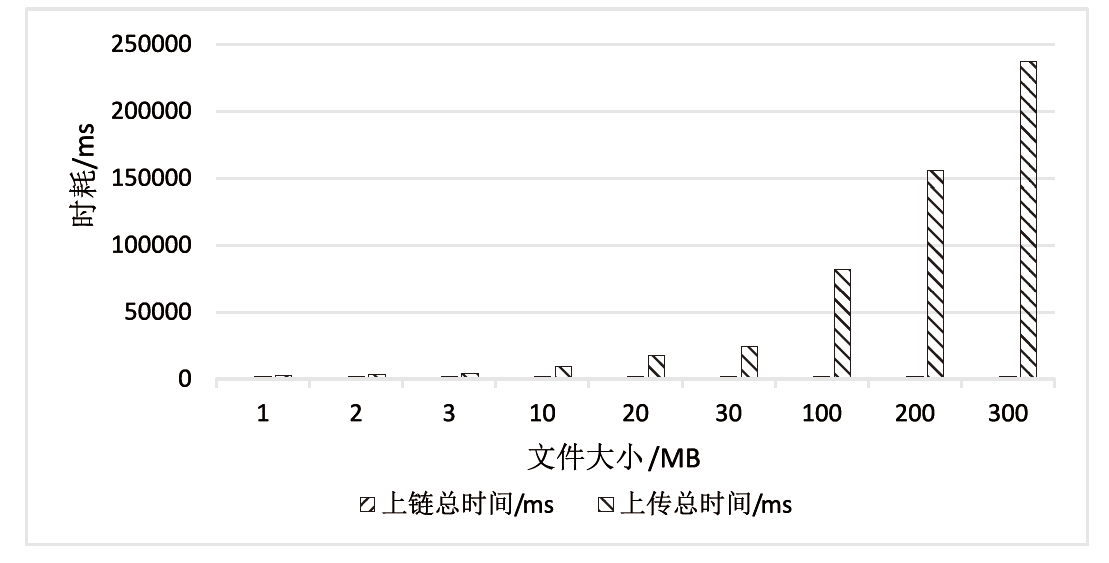
表4
数据上传平均时耗
| 数据大小 | 区块链 时耗/ms | IPFS 时耗/ms | ABE解密 时耗/ms | 总时耗/ms |
|---|---|---|---|---|
| 1 MB | 2161 | 287 | 402 | 2890 |
| 2 MB | 2080 | 421 | 723 | 3224 |
| 3 MB | 2089 | 623 | 1121 | 3833 |
| 10 MB | 2053 | 1343 | 6232 | 9628 |
| 20 MB | 2162 | 2321 | 12323 | 16806 |
| 30 MB | 2117 | 3424 | 16342 | 21883 |
| 100 MB | 2073 | 9231 | 72311 | 83615 |
| 200 MB | 2068 | 18732 | 132434 | 153234 |
| 300 MB | 2067 | 27771 | 201012 | 230850 |
| [1] | NAKAMOTO S. Bitcoin: A Peer-to-Peer Electronic Cash System[EB/OL]. (2008-10-31)[2023-05-16]. https://bitcoin.org/bitcoin.pdf. |
| [2] |
DAI Chuangchuang, LUAN Haijing, YANG Xueying, et al. Overview of Blockchain Technology[J]. Computer Science, 2021, 48(11A): 500-508.
doi: 10.11896/jsjkx.201200163 |
|
代闯闯, 栾海晶, 杨雪莹, 等. 区块链技术研究综述[J]. 计算机科学, 2021, 48(11A):500-508.
doi: 10.11896/jsjkx.201200163 |
|
| [3] | LIU Mingda, CHEN Zuoning, SHI Yijuan, et al. Research Progress of Blockchain in Data Security[J]. Chinese Journal of Computers, 2021, 44(1): 1-27. |
| 刘明达, 陈左宁, 拾以娟, 等. 区块链在数据安全领域的研究进展[J]. 计算机学报, 2021, 44(1):1-27. | |
| [4] | LIANG Hejun, HAN Jingti. Research on Decentralized Transaction Consensus Mechanism of Cloud Computing Resources Based on Block Chain[J]. Computer Science, 2019, 46(11A): 548-552. |
| 梁贺君, 韩景倜. 基于区块链的云计算资源去中心化交易共识机制研究[J]. 计算机科学, 2019, 46(11A): 548-552. | |
| [5] | ALI M, KARIMIPOUR H, TARIQ M. Integration of Blockchain and Federated Learning for Internet of Things: Recent Advances and Future Challenges[EB/OL]. (2021-06-18)[2023-05-16]. https://www.sciencedirect.com/science/article/abs/pii/S0167404821001796. |
| [6] | ZHU Linkai, PENG Sheng, CAI Zhiming, et al. Research on Privacy Data Protection Based on Trusted Computing and Blockchain[J]. Security and Communication Networks, 2021(1): 1-9. |
| [7] |
LI Ting, KHAN M, SHARMA A, et al. A Secure Framework for IoT-Based Smart Climate Agriculture System: Toward Blockchain and Edge Computing[J]. Journal of Intelligent Systems, 2022, 31(1): 221-236.
doi: 10.1515/jisys-2022-0012 URL |
| [8] |
XU Guangxia, ZHANG Jiajun, CLIFF U G O, et al. An Efficient Blockchain-Based Privacy-Preserving Scheme with Attribute and Homomorphic Encryption[J]. International Journal of Intelligent Systems, 2022, 37(12): 10715-10750.
doi: 10.1002/int.v37.12 URL |
| [9] |
QIU Jing, TIAN Zhihong, DU Chunlai, et al. A Survey on Access Control in the Age of Internet of Things[J]. IEEE Internet of Things Journal, 2020, 7(6): 4682-4696.
doi: 10.1109/JIoT.6488907 URL |
| [10] | DHARANI J, SUNDARAKANTHAM K, SINGH K, et al. A Privacy-Preserving Framework for Endorsement Process in Hyperledger Fabric[EB/OL]. (2022-03-11)[2023-05-16]. https://www.sciencedirect.com/science/article/abs/pii/S0167404822000360. |
| [11] | YU Kechen, GUO Li, YAO Mengmeng. Design of Blockchain-Based High-Value Data Sharing System[J]. Netinfo Security, 2021, 21(11): 75-84. |
| 于克辰, 郭莉, 姚萌萌. 基于区块链的高价值数据共享系统设计[J]. 信息网络安全, 2021, 21(11):75-84. | |
| [12] |
HASSIJA V, CHAMOLA V, GARG S, et al. A Blockchain-Based Framework for Lightweight Data Sharing and Energy Trading in V2G Network[J]. IEEE Transactions on Vehicular Technology, 2020, 69(6): 5799-5812.
doi: 10.1109/TVT.25 URL |
| [13] | ZHANG Lihua, CAO Yu, ZHANG Ganzhe, et al. A Blockchain-Based Microgrid Data Disaster Backup Scheme in Edge Computing[J]. Security and Communication Networks, 2021, 2021(1): 1-19. |
| [14] | ZHANG Meng, WANG Shen, ZHANG Pan, et al. Protecting Data Privacy for Permissioned Blockchains Using Identity-Based Encryption[C]// IEEE. Electronic and Automation Control Conference (ITNEC). New York: IEEE, 2019: 602-605. |
| [15] |
WANG Ze, LIN Jingqiang, CAI Quanwei, et al. Blockchain-Based Certificate Transparency and Revocation Transparency[J]. IEEE Transactions on Dependable and Secure Computing, 2022, 19(1): 681-697.
doi: 10.1109/TDSC.2020.2983022 URL |
| [16] | GUY Z, OZ N, ALEX S, et al. Decentralizing Privacy:Using Blockchain to Protect Personal Data[C]// IEEE. IEEE Security and Privacy Workshops. New York: IEEE, 2015: 180-184. |
| [17] |
SUN Hao, MAO Hanyu, ZHANG Yanfeng, et al. Development and Application of Blockchain Cross-Chain Technology[J]. Computer Science, 2022, 49(5): 287-295.
doi: 10.11896/jsjkx.210800132 |
|
孙浩, 毛瀚宇, 张岩峰, 等. 区块链跨链技术发展及应用[J]. 计算机科学, 2022, 49(5):287-295.
doi: 10.11896/jsjkx.210800132 |
|
| [18] |
YIN Zeyuan, ZHANG Bingsheng, XU Jingzhong, et al. Bool Network: An Open, Distributed, Secure Cross-Chain Notary Platform[J]. IEEE Transactions on Information Forensics and Security, 2022, 17(1): 3465-3478.
doi: 10.1109/TIFS.2022.3209546 URL |
| [19] | LIN Shaofeng, KONG Yihan, NIE Shaotao, et al. Research on Cross-Chain Technology of Blockchain[C]//IEEE. 6th International Conference on Smart Grid and Electrical Automation (ICSGEA). New York: IEEE, 2021: 405-408. |
| [20] |
ZHANG Chaodong, WANG Baosheng, DENG Wenping. Design of Supply Chain Traceability System Based on Side Chain Technology[J]. Computer Engineering, 2019, 45(11): 1-8.
doi: 10.19678/j.issn.1000-3428.0055286 |
|
张朝栋, 王宝生, 邓文平. 基于侧链技术的供应链溯源系统设计[J]. 计算机工程, 2019, 45(11): 1-8.
doi: 10.19678/j.issn.1000-3428.0055286 |
|
| [21] | LI Zujian, ZHANG Zhihong. Research and Implementation of Multi-Chain Digital Wallet Based on Hash TimeLock[C]//Springer. Blockchain and Trustworthy Systems-First International Conference, BlockSys. Berlin: Springer, 2020: 175-182. |
| [22] |
YE Shaojie, WANG Xiaoyi, XU Caichao, et al. BitXHub: Side-Relay Chain Based Heterogeneous Blockchain Interoperable Platform[J]. Computer Science, 2020, 47(6): 294-302.
doi: 10.11896/jsjkx.191100055 |
|
叶少杰, 汪小益, 徐才巢, 等. BitXHub:基于侧链中继的异构区块链互操作平台[J]. 计算机科学, 2020, 47(6):294-302.
doi: 10.11896/jsjkx.191100055 |
| [1] | 公鹏飞, 谢四江, 程安东. 基于HotStuff改进的多主节点共识算法[J]. 信息网络安全, 2023, 23(9): 108-117. |
| [2] | 周权, 陈民辉, 卫凯俊, 郑玉龙. 基于SM9的属性加密的区块链访问控制方案[J]. 信息网络安全, 2023, 23(9): 37-46. |
| [3] | 赵佳豪, 蒋佳佳, 张玉书. 基于动态默克尔哈希树的跨链数据一致性验证模型[J]. 信息网络安全, 2023, 23(9): 95-107. |
| [4] | 邵震哲, 蒋佳佳, 赵佳豪, 张玉书. 面向跨链的改进加权拜占庭容错算法[J]. 信息网络安全, 2023, 23(8): 109-120. |
| [5] | 郭瑞, 魏鑫, 陈丽. 工业物联网环境下可外包的策略隐藏属性基加密方案[J]. 信息网络安全, 2023, 23(3): 1-12. |
| [6] | 李春晓, 王耀飞, 徐恩亮, 赵钰. 基于双线性映射的区块链安全范围搜索技术研究[J]. 信息网络安全, 2023, 23(3): 22-34. |
| [7] | 王晶宇, 马兆丰, 徐单恒, 段鹏飞. 支持国密算法的区块链交易数据隐私保护方案[J]. 信息网络安全, 2023, 23(3): 84-95. |
| [8] | 冯怡婷, 马兆丰, 徐单恒, 段鹏飞. 跨链接入的区块链安全强度评估方法[J]. 信息网络安全, 2023, 23(1): 84-92. |
| [9] | 张光华, 刘永升, 王鹤, 于乃文. 基于BiLSTM和注意力机制的智能合约漏洞检测方案[J]. 信息网络安全, 2022, 22(9): 46-54. |
| [10] | 张玉健, 刘代富, 童飞. 基于局部图匹配的智能合约重入漏洞检测方法[J]. 信息网络安全, 2022, 22(8): 1-7. |
| [11] | 胡艺, 佘堃. 基于区块链和智能合约的双链车联网系统[J]. 信息网络安全, 2022, 22(8): 26-35. |
| [12] | 黄保华, 赵伟宏, 彭丽, 谢统义. 基于MPT索引的高效链上PKI模型[J]. 信息网络安全, 2022, 22(8): 72-80. |
| [13] | 王健, 黄俊. 基于智能合约的日志安全存储与公平访问方法[J]. 信息网络安全, 2022, 22(7): 27-36. |
| [14] | KELEKET GOMA Christy Junior Yannick, 易文哲, 王鹃. 一种基于SGX的轻量Fabric链码可信执行环境构建方法[J]. 信息网络安全, 2022, 22(7): 73-83. |
| [15] | 王姝爽, 马兆丰, 刘嘉微, 罗守山. 区块链跨链安全接入与身份认证方案研究与实现[J]. 信息网络安全, 2022, 22(6): 61-72. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||