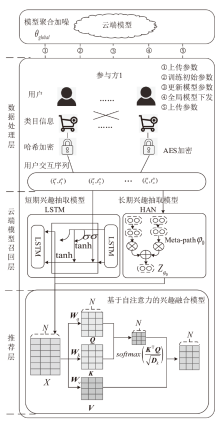
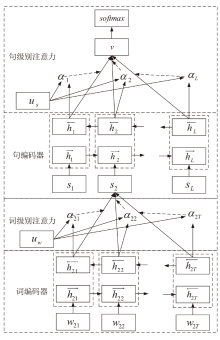
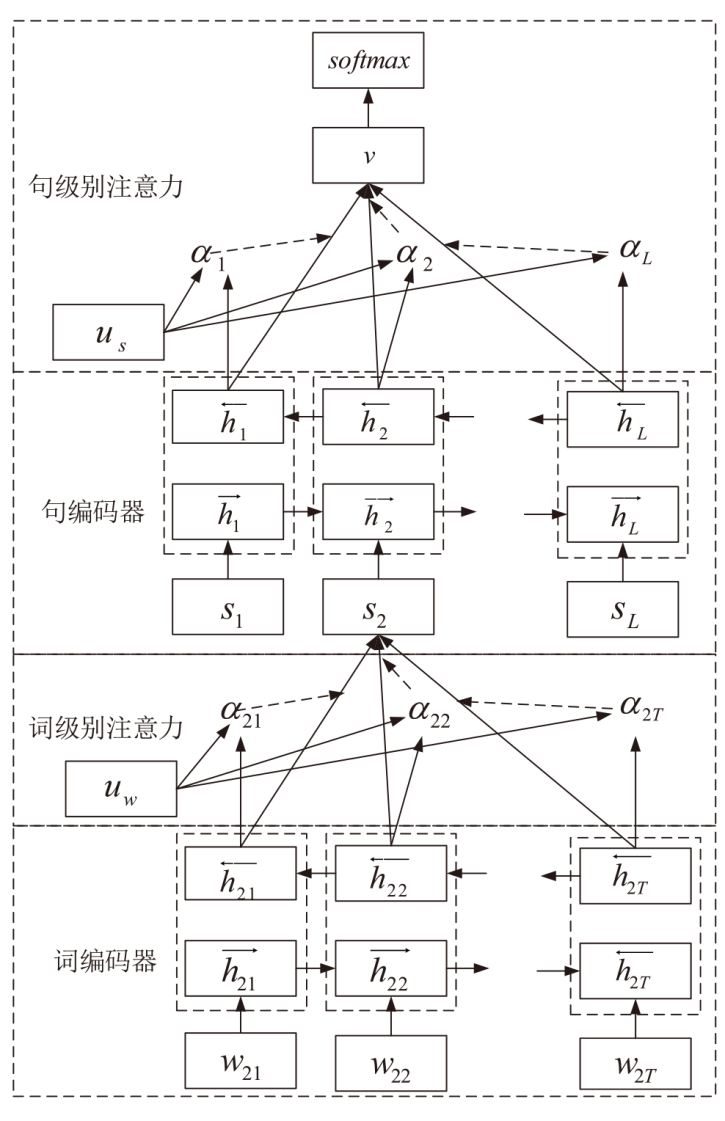
信息网络安全 ›› 2023, Vol. 23 ›› Issue (7): 31-43.doi: 10.3969/j.issn.1671-1122.2023.07.004
基于云联邦的差分隐私保护动态推荐模型
刘刚1,2, 杨雯莉1,2( ), 王同礼1,2, 李阳1,2
), 王同礼1,2, 李阳1,2
- 1.哈尔滨工程大学计算机科学与技术学院,哈尔滨 150001
2.哈尔滨工程大学电子政务建模仿真国家工程实验室,哈尔滨 150001
-
收稿日期:2023-03-23出版日期:2023-07-10发布日期:2023-07-14 -
通讯作者:杨雯莉 Yangwenli@hrbeu.edu.cn -
作者简介:刘刚(1976—),男,山东,副教授,博士,CCF会员,主要研究方向为机器学习、数据挖掘、自然语言处理|杨雯莉(1999—),女,辽宁,硕士研究生,主要研究方向为自然语言处理|王同礼(1998—),男,山东,硕士研究生,主要研究方向为自然语言处理|李阳(1996—),男,河北,硕士研究生,主要研究方向为自然语言处理 -
基金资助:黑龙江省高等教育教学改革研究项目(SJGZ20200044);黑龙江省自然科学基金(LH2021F015);高端外国专家引进计划(G2021180008L)
Differential Privacy-Preserving Dynamic Recommendation Model Based on Cloud Federation
LIU Gang1,2, YANG Wenli1,2( ), WANG Tongli1,2, LI Yang1,2
), WANG Tongli1,2, LI Yang1,2
- 1. College of Computer Science and Technology, Harbin Engineering University, Harbin 150001, China
2. Modeling and Emulation in E-Government National Engineering Laboratory, Harbin Engineering University, Harbin 150001, China
-
Received:2023-03-23Online:2023-07-10Published:2023-07-14
摘要:
为提高推荐系统的准确性和个性化水平,同时保护用户的隐私,文章提出一种基于云联邦的差分隐私保护动态推荐模型(P2RCF)。该模型采用注意力机制动态调整融合长短期用户兴趣,增强推荐系统的灵活性,同时引入差分隐私技术和云联邦技术保护用户的隐私信息。文章在公共数据集上进行了实验,实验结果表明,该模型可以在保护用户数据隐私的同时提高推荐的准确性和个性化水平。
中图分类号:
引用本文
刘刚, 杨雯莉, 王同礼, 李阳. 基于云联邦的差分隐私保护动态推荐模型[J]. 信息网络安全, 2023, 23(7): 31-43.
LIU Gang, YANG Wenli, WANG Tongli, LI Yang. Differential Privacy-Preserving Dynamic Recommendation Model Based on Cloud Federation[J]. Netinfo Security, 2023, 23(7): 31-43.
表1
符号及说明
| 符号 | 说明 |
|---|---|
| 用户集合 | |
| 物品集合 | |
| n | 用户集合总数 |
| m | 物品集合总数 |
| 用户的历史交互行为 | |
| 用户的历史交互行为序列总数 | |
| 时间间隔 | |
| p | 序列长度 |
| 用户长期兴趣备选集 | |
| 用户短期兴趣备选集 |
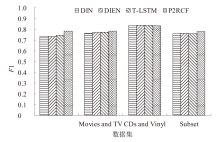
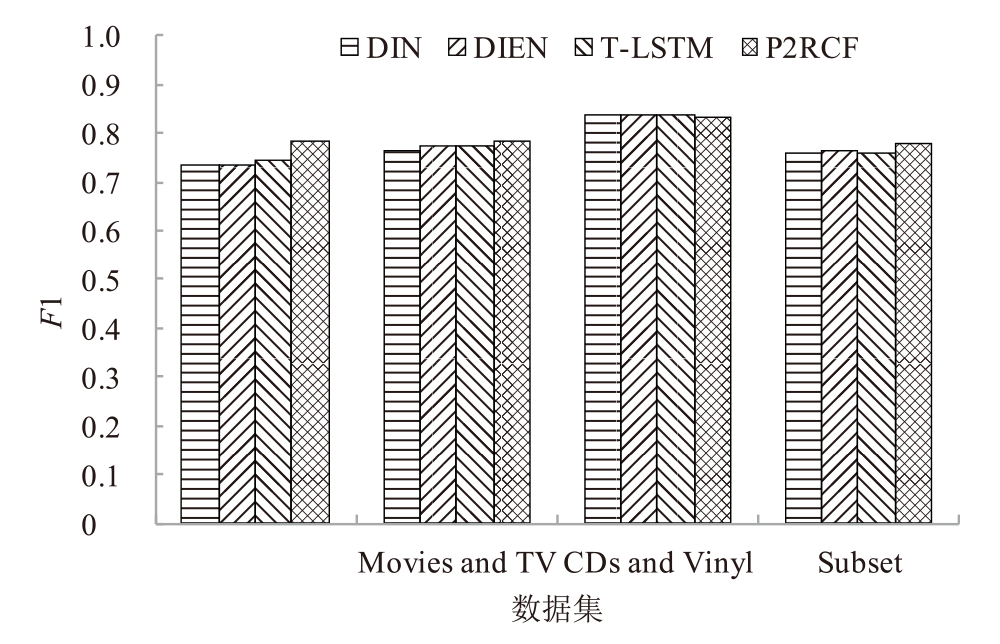
表3
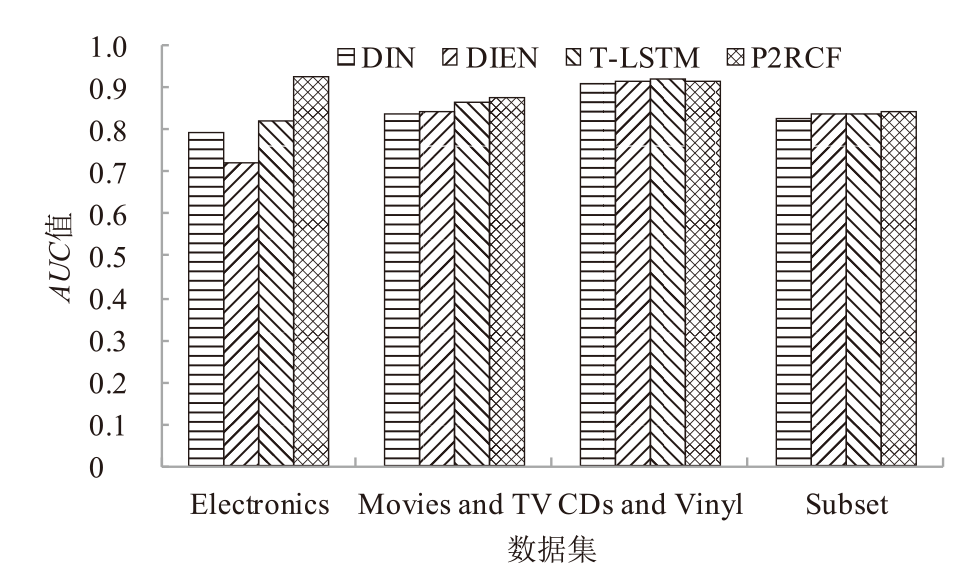
不同模型的AUC和F1指标
| 模型 | 评估指标 | Electronics | Movies and TV | CDs and Vinyl | Subset |
|---|---|---|---|---|---|
| ASVD | AUC | 0.7727 | 0.8156 | 0.8863 | 0.8060 |
| DIN | 0.7927 | 0.8388 | 0.9111 | 0.8293 | |
| DIEN | 0.7209 | 0.8438 | 0.9128 | 0.8361 | |
| T-LSTM | 0.8212 | 0.8660 | 0.9181 | 0.8387 | |
| PACA | 0.8913 | 0.8711 | 0.8832 | 0.8217 | |
| TLSAN | 0.9230 | 0.8986 | 0.9651 | 0.8451 | |
| RA-NGCF | 0.9254 | 0.8876 | 0.9400 | 0.8421 | |
| DEKGCN | 0.9014 | 0.8461 | 0.9036 | 0.8374 | |
| P2RCF | 0.9257 | 0.8751 | 0.9139 | 0.8451 | |
| ASVD | F1 | 0.7255 | 0.7539 | 0.8128 | 0.7427 |
| DIN | 0.7349 | 0.7660 | 0.8348 | 0.7599 | |
| DIEN | 0.7327 | 0.7755 | 0.8374 | 0.7632 | |
| T-LSTM | 0.7448 | 0.7742 | 0.8352 | 0.7591 | |
| PACA | 0.7434 | 0.7549 | 0.8492 | 0.7497 | |
| TLSAN | 0.7812 | 0.7820 | 0.8716 | 0.7737 | |
| RA-NGCF | 0.7816 | 0.7613 | 0.8543 | 0.7784 | |
| DEKGCN | 0.7423 | 0.7571 | 0.8293 | 0.7695 | |
| P2RCF | 0.7858 | 0.7820 | 0.8329 | 0.7785 |
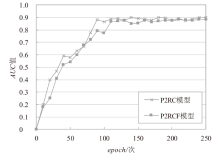
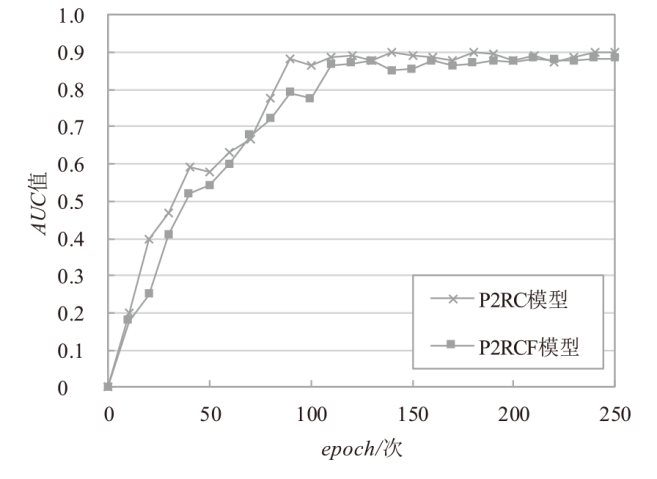
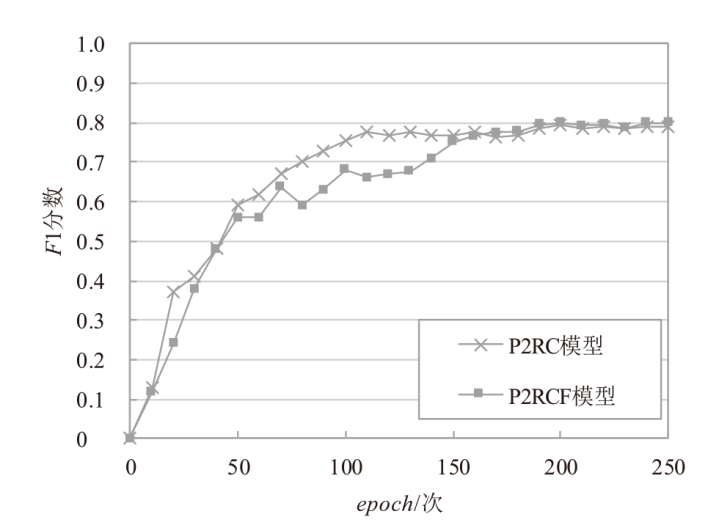
表4
P2RCF模型与P2RC模型实验结果
| 数据集 | 评估指标 | P2RC | P2RCF | diff |
|---|---|---|---|---|
| Electronics | AUC | 0.9296 | 0.9257 | 0.4195% |
| F1 | 0.7886 | 0.7858 | 0.3551% | |
| Movies and TV | AUC | 0.8769 | 0.8751 | 0.2053% |
| F1 | 0.7823 | 0.7820 | 0.0383% | |
| CDs and Vinyl | AUC | 0.9191 | 0.9139 | 0.5658% |
| F1 | 0.8406 | 0.8329 | 0.9160% | |
| Subset | AUC | 0.8453 | 0.8451 | 0.0237% |
| F1 | 0.7787 | 0.7785 | 0.0257% |
| [1] | SUN Ke, QIAN Tieyun, CHEN Tong, et al. Where to Go Next: Modeling Long-and Short-Term User Preferences for Point-of-Interest Recommendation[C]// AAAI. AAAI Conference on Artificial Intelligence. New York: AAAI, 2020: 214-221. |
| [2] | CHEN Ming, WEI Zhewei, HUANG Zengfeng, et al. Simple and Deep Graph Convolutional Networks[C]// IMLS. 37th International Conference on Machine Learning. Vienna: PMLR, 2020: 1725-1735. |
| [3] | WU Libing, QUAN Cong, LI Chenliang, et al. A Context-Aware User-Item Representation Learning for Item Recommendation[J]. ACM Transactions on Information Systems, 2019, 37(2): 1-29. |
| [4] | CHEN Xusong. Research on Recommendation Algorithm Based on User Behavior Sequence Modeling[D]. Hefei: University of Science and Technology of China, 2021. |
| 陈旭松. 基于用户行为序列建模的推荐算法研究[D]. 合肥: 中国科学技术大学, 2021. | |
| [5] | ZHANG Liyan. Research on Recommendation Algorithm Based on Sequence Feature Extraction[D]. Chengdu: University of Electronic Science and Technology, 2021. |
| 张李燕. 基于序列特征提取的推荐算法研究[D]. 成都: 电子科技大学, 2021. | |
| [6] |
LIN Guanyu, LIANG Feng, PAN Weike, et al. Fedrec: Federated Recommendation with Explicit Feedback[J]. IEEE Intelligent Systems, 2020, 36(5): 21-30.
doi: 10.1109/MIS.2020.3017205 URL |
| [7] | LIANG Feng, PAN Weike, MING Zhong. Fedrec++: Lossless Federated Recommendation with Explicit Feedback[C]// AAAI. The AAAI Conference on Artificial Intelligence. New York: AAAI, 2021: 4224-4231. |
| [8] | KHAN F K, FLANAGAN A, Tan K E, et al. A Payload Optimization Method for Federated Recommender Systems[C]// ACM. 15th ACM Conference on Recommender Systems. New York: ACM, 2021: 432-442. |
| [9] | LUO Sichun, XIAO Yuanzhang, SONG Linqi. Personalized Federated Recommendation via Joint Representation Learning, User Clustering, and Model Adaptation[C]// ACM. 31st ACM International Conference on Information& Knowledge Management. New York: ACM, 2022: 4289-4293. |
| [10] | SUN Zehua, XU Yonghui, LIU Yong, et al. A Survey on Federated Recommendation Systems[EB/OL]. (2023-03-09) [2023-03-15]. https://arxiv.org/abs/2301.00767. |
| [11] |
LI Xiaoli, LI Yuzheng, WANG Jining, et al. Decentralized Federated Meta-Learning Framework for Few-Shot Multitask Learning[J]. International Journal of Intelligent Systems, 2022, 37(11): 8490-8522.
doi: 10.1002/int.v37.11 URL |
| [12] |
ZHANG Feng, XUE Erkang, GUO Ruixin, et al. DS-ADMM++: A Novel Distributed Quantized Admm to Speed up Differentially Private Matrix Factorization[J]. IEEE Transactions on Parallel and Distributed Systems, 2022, 33(6): 1289-1302.
doi: 10.1109/TPDS.2021.3110104 URL |
| [13] | CHEN Chaochao, WU Huiwen, SU Jiajie, et al. Differential Private Knowledge Transfer for Privacy-Preserving Cross-Domain Recommendation[C]// ACM. The ACM Web Conference 2022. New York: ACM, 2022: 1455-1465. |
| [14] | DENG Wei, CHEN Xiuting, ZHANG Qinghua. Differential Privacy Protection Algorithm Based on Tree Model[J]. Journal of Chongqing University of Posts and Telecommunications, 2020, 32(5): 848-856. |
| 邓蔚, 陈秀婷, 张清华. 基于树模型的差分隐私保护算法[J]. 重庆邮电大学学报, 2020, 32(5):848-856. | |
| [15] |
GUO Taolin, LUO Junzhou, DONG Kai, et al. Locally Differentially Private Item-Based Collaborative Filtering[J]. Information Science. 2019, 502: 229-246.
doi: 10.1016/j.ins.2019.06.021 URL |
| [16] | CHEN Gao, CHAO Huang, LIN Dongsheng, et al. DPLCF Differentially Private Local Collaborative Filtering[C]// ACM. 43rd International ACM SIGIR Conference on Research and Development in Information Retrieval. New York: ACM, 2020: 961-970. |
| [17] |
WANG Yong, YIN Enming, RAN Xun. Differential Privacy Protection Recommendation Algorithm Based on BC Clustering[J]. Journal of Beijing University of Posts and Telecommunications, 2021, 44(2): 81-88.
doi: 10.13190/j.jbupt.2020-174 |
|
王永, 尹恩明, 冉旬. 基于BC聚类的差分隐私保护推荐算法[J]. 北京邮电大学学报, 2021, 44(2):81-88.
doi: 10.13190/j.jbupt.2020-174 |
|
| [18] | ZHOU Guorui, ZHU Xiaoqiang, SONG Chengru, et al. Deep Interest Network for Click-Through Rate Prediction[C]// ACM. 24th ACM SIGKDD International Conference on Knowledge Discovery& Data Mining. New York: ACM, 2018: 1059-1068. |
| [19] | ZHU Yu, LI Hao, LIAO Yikang, et al. What to Do Next: Modeling User Behaviors by Time-LSTM[C]// IJCAI. 26th International Joint Conference on Artificial Intelligence. New York: AAAI, 2017: 3602-3608. |
| [20] | ZHOU Guorui, MOU Na, FAN Ying, et al. Deep Interest Evolution Network for Click-Through Rate Prediction[C]// AAAI. 33th AAAI Conference on Artificial Intelligence. New York: AAAI, 2019: 5941-5948. |
| [21] |
MOU Luntian, ZHAO Pengfei, XIE Haitao, et al. T-LSTM: A Long Short-Term Memory Neural Network Enhanced by Temporal Information for Traffic Flow Prediction[J]. IEEE Access, 2019, 7: 98053-98060.
doi: 10.1109/ACCESS.2019.2929692 |
| [22] |
CAO Yi, ZHANG Weifeng, SONG Bo, et al. Position Aware Context Attention for Session-Based Recommendation[J]. Neurocomputing, 2020, 376: 65-72.
doi: 10.1016/j.neucom.2019.09.016 URL |
| [23] | ZHANG Jianqing, WANG Dongjing, YU Dongjin. TLSAN: Time-Aware Long-and Short-Term Attention Network for Next-Item Recommendation[J]. Neurocomputing, 2021, 44(2): 179-191. |
| [24] | TANG Jiakai, JIN Jiahui, MIAO Zijia, et al. Region-Aware POI Recommendation with Semantic Spatial Graph[C]// IEEE. 24th International Conference on Computer Supported Cooperative Work in Design. New York: IEEE, 2021: 214-219. |
| [25] | LI Xiang, YANG Xingyao, YU Jiong. Double End Knowledge Graph Convolutional Networks for Recommender Systems[J]. Journal of Frontiers of Computer Science and Technology, 2022, 16(1): 176-184. |
|
李想, 杨兴耀, 于炯. 基于知识图谱卷积网络的双端推荐算法[J]. 计算机科学与探索, 2022, 16(1):176-184.
doi: 10.3778/j.issn.1673-9418.2103072 |
| [1] | 蒋英肇, 陈雷, 闫巧. 基于双通道特征融合的分布式拒绝服务攻击检测算法[J]. 信息网络安全, 2023, 23(7): 86-97. |
| [2] | 陈晶, 彭长根, 谭伟杰, 许德权. 基于差分隐私和秘密共享的多服务器联邦学习方案[J]. 信息网络安全, 2023, 23(7): 98-110. |
| [3] | 赵佳, 高塔, 张建成. 基于改进贝叶斯网络的高维数据本地差分隐私方法[J]. 信息网络安全, 2023, 23(2): 19-25. |
| [4] | 李季瑀, 付章杰, 张玉斌. 一种基于跨域对抗适应的图像信息隐藏算法[J]. 信息网络安全, 2023, 23(1): 93-102. |
| [5] | 张光华, 刘永升, 王鹤, 于乃文. 基于BiLSTM和注意力机制的智能合约漏洞检测方案[J]. 信息网络安全, 2022, 22(9): 46-54. |
| [6] | 张光华, 闫风如, 张冬雯, 刘雪峰. 基于LSTM-Attention的内部威胁检测模型[J]. 信息网络安全, 2022, 22(2): 1-10. |
| [7] | 刘峰, 杨成意, 於欣澄, 齐佳音. 面向去中心化双重差分隐私的谱图卷积神经网络[J]. 信息网络安全, 2022, 22(2): 39-46. |
| [8] | 晏燕, 张雄, 冯涛. 大数据统计划分发布的等比差分隐私预算分配方法[J]. 信息网络安全, 2022, 22(11): 24-35. |
| [9] | 朱丽娜, 马铭芮, 朱东昭. 基于图神经网络和通用漏洞分析框架的C类语言漏洞检测方法[J]. 信息网络安全, 2022, 22(10): 59-68. |
| [10] | 石拓, 梁飞, 尚钢川, 田洋俊. 基于时序交易图注意力神经网络的以太坊恶意账户检测[J]. 信息网络安全, 2022, 22(10): 69-75. |
| [11] | 刘烁, 张兴兰. 基于双重注意力的入侵检测系统[J]. 信息网络安全, 2022, 22(1): 80-86. |
| [12] | 路宏琳, 王利明. 面向用户的支持用户掉线的联邦学习数据隐私保护方法[J]. 信息网络安全, 2021, 21(3): 64-71. |
| [13] | 代翔, 孙海春, 牛硕, 朱容辰. 融合互注意力机制与BERT的中文问答匹配技术研究[J]. 信息网络安全, 2021, 21(12): 102-108. |
| [14] | 张佳程, 彭佳, 王雷. 大数据环境下的本地差分隐私图信息收集方法[J]. 信息网络安全, 2020, 20(6): 44-56. |
| [15] | 彭长根, 赵园园, 樊玫玫. 基于最大信息系数的主成分分析差分隐私数据发布算法[J]. 信息网络安全, 2020, 20(2): 37-48. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||