信息网络安全 ›› 2023, Vol. 23 ›› Issue (5): 22-31.doi: 10.3969/j.issn.1671-1122.2023.05.003
无线传感器网络中虚假数据途中过滤技术研究
- 哈尔滨工程大学计算机科学与技术学院,哈尔滨 150001
-
收稿日期:2023-01-17出版日期:2023-05-10发布日期:2023-05-15 -
通讯作者:张盈希 E-mail:zyx19981028@163.com -
作者简介:冯光升(1980—),男,山东,教授,博士,主要研究方向为网络技术与信息安全、边缘计算、无线室内定位技术|张盈希(1998—),女,山东,硕士研究生,主要研究方向为网络技术与信息安全|任奕菲(1998—),女,辽宁,硕士研究生,主要研究方向为网络技术与信息安全|高素林(1998—),男,贵州,博士研究生,主要研究方向为网络技术与信息安全、边缘计算 -
基金资助:国家自然科学基金(61872104)
Research on En-Route False Data Filtering Technology in Wireless Sensor Network
FENG Guangsheng, ZHANG Yingxi( ), REN Yifei, GAO Sulin
), REN Yifei, GAO Sulin
- College of Computer Science and Technology, Harbin Engineering University, Harbin 150001, China
-
Received:2023-01-17Online:2023-05-10Published:2023-05-15 -
Contact:ZHANG Yingxi E-mail:zyx19981028@163.com
摘要:
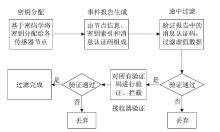
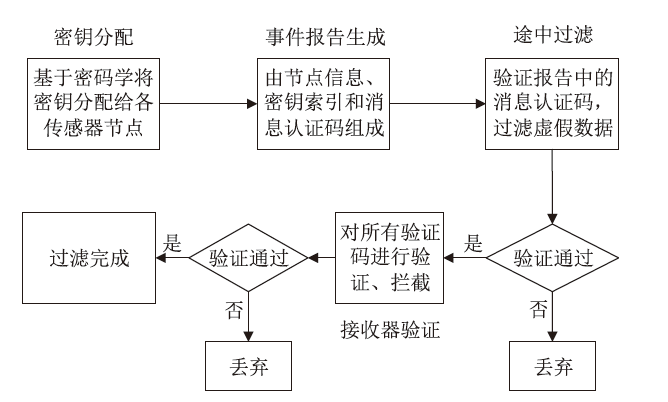
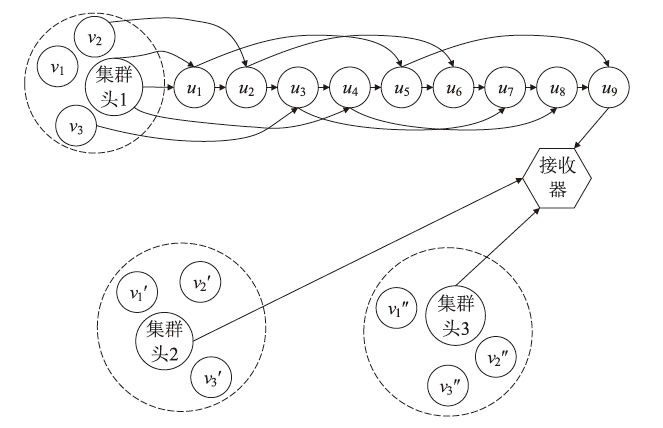
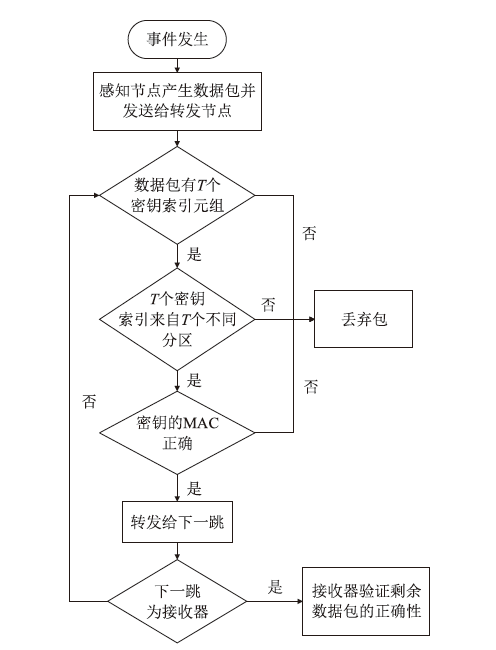
无线传感器网络具有实际应用环境相对复杂、自身节点通道脆弱等特点,因此传感器节点很容易受到虚假数据注入攻击,导致传感器能量和通信资源浪费,甚至造成系统瘫痪。途中过滤技术是解决以上问题的有效方法之一。文章首先介绍了途中过滤技术的基本原理;然后对途中过滤技术中密钥分配、事件报告生成、途中过滤和接收器验证4个步骤进行研究分析,并根据不同原则分别对密钥分配过程和途中过滤过程进行分类研究,详细分析了一些重要的过滤方法及其优缺点。
中图分类号:
引用本文
冯光升, 张盈希, 任奕菲, 高素林. 无线传感器网络中虚假数据途中过滤技术研究[J]. 信息网络安全, 2023, 23(5): 22-31.
FENG Guangsheng, ZHANG Yingxi, REN Yifei, GAO Sulin. Research on En-Route False Data Filtering Technology in Wireless Sensor Network[J]. Netinfo Security, 2023, 23(5): 22-31.
| [1] | REN Fengyuan, HUANG Haining, LIN Chuang. Wireless Sensor Networks[J]. Journal of Software, 2003, 14(7): 1282-1291. |
| 任丰原, 黄海宁, 林闯. 无线传感器网络[J]. 软件学报, 2003, 14(7):1282-1291. | |
| [2] | TAFA Z. WSNs in Environmental Monitoring: Data Acquisition and Dissemination Aspects[J]. Advances in Computers, 2022, 126: 65-149. |
| [3] |
KHAN T H F, KUMAR D S. Ambient Crop Field Monitoring for Improving Context Based Agricultural by Mobile Sink in WSN[J]. Journal of Ambient Intelligence and Humanized Computing, 2020, 11: 1431-1439.
doi: 10.1007/s12652-019-01177-6 |
| [4] |
IMRAN L B, LATIF R M A, FARHAN M, et al. Smart City Based Autonomous Water Quality Monitoring System Using WSN[J]. Wireless Personal Communications, 2020, 115: 1805-1820.
doi: 10.1007/s11277-020-07655-x |
| [5] |
BASHIR N, BOUDJIT S, ZEADALLY S. A Closed-Loop Control Architecture of UAV and WSN for Traffic Surveillance on Highways[J]. Computer Communications, 2022, 190: 78-86.
doi: 10.1016/j.comcom.2022.04.008 URL |
| [6] | JAIN U, HUSSAIN M. Security Mechanism for Maritime Territory and Frontier Surveillance in Naval Operations Using Wireless Sensor Networks[J]. Concurrency and Computation: Practice and Experience, 2021, 33(17): 1-15. |
| [7] | CHEN Dong. Research on Key Technologies for Privacy Protection of Source Nodes in Wireless Sensor Networks[D]. Beijing: Beijing Jiaotong University, 2021. |
| 陈栋. 无线传感器网络源节点位置隐私保护关键技术研究[D]. 北京: 北京交通大学, 2021. | |
| [8] |
KUMAR A, PAIS A R. En-Route Filtering Techniques in Wireless Sensor Networks: A Survey[J]. Wireless Personal Communications, 2017, 96(1): 697-739.
doi: 10.1007/s11277-017-4197-0 URL |
| [9] | MEHTA M, PATEL K. Experimental Study of Location Spoofing and Identity Spoofing Attack in Internet of Things Network[J]. International Journal of Intelligent Information Technologies, 2022, 18(3): 1-13. |
| [10] | ZHAI Lijing, VAMVOUDAKIS K G, HUGUES J. Switching Watermarking-Based Detection Scheme Against Replay Attacks[C]// IEEE. 60th IEEE Conference on Decision and Control(CDC). New York: IEEE, 2021: 4200-4205. |
| [11] | YLLI E, FEJZAJ J. Man in the Middle: Attack and Protection[C]// CEUR-WS. 4th International Conference on Recent Trends and Applications in Computer Science and Information Technology(RTA-CSIT). Tirana: CEUR-WS, 2021: 198-204. |
| [12] |
YE Fan, LUO Haiyun, LU Songwu, et al. Statistical En-Route Filtering of Injected False Data in Sensor Networks[J]. IEEE Journal on Selected Areas in Communications, 2005, 23(4): 839-850.
doi: 10.1109/JSAC.2005.843561 URL |
| [13] | DU Tianqi. Research on Wireless Sensor Network Security and Key Management Technology[J]. Wireless Internet Technology, 2021, 18(12): 13-14. |
| 杜天琦. 无线传感器网络安全与密钥管理技术研究[J]. 无线互联科技, 2021, 18(12):13-14. | |
| [14] | SUN Qian, WU Min. A Double Key-Sharing Based False Data Filtering Scheme in Wireless Sensor Networks[C]// IEEE. 10th IEEE International Conference on Trust, Security and Privacy in Computing and Communications. New York: IEEE, 2011: 509-516. |
| [15] | ZHANG Wensheng, CAO Guohong. Group Rekeying for Filtering False Data in Sensor Networks: A Predistribution and Local Collaboration-Based Approach[C]// IEEE. 24th Annual Joint Conference of the IEEE Computer and Communications Societies. New York: IEEE, 2005: 503-514. |
| [16] | LIU Zhixiong, WANG Jianxin, ZHANG Xi. A False Data Filtering Scheme Using Cluster-Based Organization in Sensor Networks[C]// IEEE. International Conference on Communications(ICC). New York: IEEE, 2011: 1-5. |
| [17] |
KUMAR A, PAIS A R. Deterministic En-Route Filtering of False Reports: A Combinatorial Design Based Approach[J]. IEEE Access, 2018, 6: 74494-74505.
doi: 10.1109/ACCESS.2018.2883474 URL |
| [18] |
CHOI H M, NAM S M, CHO T H. A Secure Routing Method for Detecting False Reports and Wormhole Attacks in Wireless Sensor Networks[J]. Wireless Sensor Network, 2013, 5(3): 33-40.
doi: 10.4236/wsn.2013.53005 URL |
| [19] | YANG Hao, YE Fan, YUAN Yuan, et al. Toward Resilient Security in Wireless Sensor Networks[C]// ACM. 6th ACM International Symposium on Mobile Ad Hoc Networking and Computing. New York: ACM, 2005: 34-45. |
| [20] | YU Lei, LI Jianzhong. Grouping-Based Resilient Statistical En-Route Filtering for Sensor Networks[C]// IEEE. INFOCOM. New York: IEEE, 2009: 1782-1790. |
| [21] |
REN Kui, LOU Wenjing, ZHANG Yanchao. LEDS: Providing Location-Aware End-to-End Data Security in Wireless Sensor Networks[J]. IEEE Transactions on Mobile Computing, 2008, 7(5): 585-598.
doi: 10.1109/TMC.2007.70753 URL |
| [22] | FAKHREY H, BOUSSAKTA S, TIWARI R, et al. Location-Dependent Key Management Protocol for a WSN with a Random Selected Cell Reporter[C]// IEEE. International Conference on Communications(ICC). New York: IEEE, 2015: 6300-6305. |
| [23] |
WANG Jianxin, LIU Zhixiong, ZHANG Shigeng, et al. Defending Collaborative False Data Injection Attacks in Wireless Sensor Networks[J]. Information Sciences, 2014, 254: 39-53
doi: 10.1016/j.ins.2013.08.019 URL |
| [24] |
KUMAR A, BANSAL N, PAIS A R. A Partial Key Pre-Distribution Based En-Route Filtering Scheme for Wireless Sensor Networks[J]. Journal of Ambient Intelligence and Humanized Computing, 2021, 12(1): 1471-1486.
doi: 10.1007/s12652-020-02216-3 |
| [25] | HU Yupeng, LIN Yaping, LIU Yonghe, et al. RAS: A Robust Authentication Scheme for Filtering False Data in Wireless Sensor Networks[C]// IEEE. 15th IEEE International Conference on Networks. New York: IEEE, 2007: 200-205. |
| [26] | ZHOU Li, RAVISHANKAR C V. A Fault Localized Scheme for False Report Filtering in Sensor Networks[C]// IEEE. International Conference on Pervasive Services. New York: IEEE, 2005: 59-68. |
| [27] | LIU Zhixiong, WANG Jiangtao, WANG Weiping, et al. One-Way Hash Chain Based Filtering Scheme in Wireless Sensor Networks[J]. Journal of Software, 2014, 25(10): 2385-2396. |
| 刘志雄, 王江涛, 王伟平, 等. 传感器网络中一种基于单向哈希链的过滤方案[J]. 软件学报, 2014, 25(10):2385-2396. | |
| [28] |
YU Zhen, GUAN Yong. A Dynamic En-Route Filtering Scheme for Data Reporting in Wireless Sensor Networks[J]. IEEE/ACM Transactions on Networking, 2009, 18(1): 150-163.
doi: 10.1109/TNET.2009.2026901 URL |
| [29] | YUAN Ting, ZHANG Shiyong, ZHONG Yiping, et al. KAEF: An En-Route Scheme of Filtering False Data in Wireless Sensor Networks[C]// IEEE. IEEE International Performance, Computing and Communications Conference. New York: IEEE, 2008: 193-200. |
| [30] | ZHU Sencun, SETIA S, JAJODIA S, et al. An Interleaved Hop-by-Hop Authentication Scheme for Filtering of Injected False Data in Sensor Networks[C]// IEEE. Symposium on Security and Privacy. New York: IEEE, 2004: 259-271. |
| [31] | KRAUB C, SCHNEIDER M, BAYAROU K, et al. STEF: A Secure Ticket-Based En-Route Filtering Scheme for Wireless Sensor Networks[C]// IEEE. The Second International Conference on Availability, Reliability and Security. New York: IEEE, 2007: 310-317. |
| [32] | KUMAR A, PAIS A R. Blockchain Based En-Route Filtering of False Data in Wireless Sensor Networks[C]// IEEE. 11th International Conference on Communication Systems & Networks. New York: IEEE, 2019: 1-6. |
| [33] | YANG Hao, LU Songwu. Commutative Cipher Based En-Route Filtering in Wireless Sensor Networks[C]// IEEE. 60th Vehicular Technology Conference, 2004. VTC2004-Fall. New York: IEEE, 2004: 1223-1227. |
| [34] |
WANG Haodong, LI Qun. Achieving Robust Message Authentication in Sensor Networks: A Public-Key Based Approach[J]. Wireless Networks, 2010, 16(4): 999-1009.
doi: 10.1007/s11276-009-0184-z URL |
| [35] | YU Hong, HE Jingsha. Authentication and En-Route Data Filtering for Wireless Sensor Networks in the Internet of Things Scenario[J]. International Journal of Grid and Distributed Computing, 2013, 6(1): 1-12. |
| [36] | HU Y C, PERRIG A, JOHNSON D B. Packet Leashes: A Defense Against Wormhole Attacks in Wireless Networks[C]// IEEE. Twenty-second Annual Joint Conference of the IEEE Computer and Communications Societies. New York: IEEE, 2003: 1976-1986. |
| [37] |
FAKHREY H, JOHNSTON M, ANGELINI F, et al. The Optimum Design of Location-Dependent Key Management Protocol for a Multiple Sink WSN Using a Random Selected Cell Reporter[J]. IEEE Sensors Journal, 2018, 18(24): 10163-10173.
doi: 10.1109/JSEN.2018.2871661 URL |
| [38] | WANG Jing. Tracing and Filtering Analysis of False Data Based on Python Crawler Technology[J]. Henan Science and Technology, 2021, 40(22): 27-30. |
| 王景. 基于Python爬虫技术的虚假数据溯源与途中过滤分析[J]. 河南科技, 2021, 40(22):27-30. | |
| [39] |
SONG Xiaoli, GONG Yunzhan, JIN Dahai, et al. Nodes Deployment Based on Directed Perception Model of Wireless Sensor Networks[J]. Journal of Beijing University of Posts and Telecommunications, 2017, 40(S1): 39-42.
doi: 10.13190/j.jbupt.2017.s.009 |
| 宋晓莉, 宫云战, 金大海, 等. 基于有向感知模型的无线传感器网络节点部署[J]. 北京邮电大学学报, 2017, 40(S1):39-42. | |
| [40] |
LIU Zhixiong, LI Limiao. Modeling and Simulation of False Report Filtering Scheme Based on Position in Wireless Sensor Networks[J]. Journal of System Simulation, 2019, 31(1): 27-35.
doi: 10.16182/j.issn1004731x.joss.17-0043E |
|
刘志雄, 黎梨苗. 传感器网络中基于位置的虚假数据过滤的建模与仿真[J]. 系统仿真学报, 2019, 31(1):27-35.
doi: 10.16182/j.issn1004731x.joss.17-0043E |
|
| [41] |
LIU Zhixiong, YE Hui, LI Fangmin. A Location and Optimal Coverage Based Filtering Scheme in Wireless Sensor Networks[J]. IEEE Access, 2020, 8: 41740-41748.
doi: 10.1109/Access.6287639 URL |
| [42] |
LU Rongxing, LIN Xiaodong, ZHU Haojin, et al. BECAN: A Bandwidth-Efficient Cooperative Authentication Scheme for Filtering Injected False Data in Wireless Sensor Networks[J]. IEEE Transactions on Parallel and Distributed Systems, 2011, 23(1): 32-43.
doi: 10.1109/TPDS.2011.95 URL |
| [43] | YI Chuanjun. En-Route Message Authentication Scheme for Filtering False Data in WSNs[EB/OL]. (2021-01-01)[2022-11-20]. https://doi.org/10.1155/2021/4068507. |
| [44] | LI Ronghua, YU J X, HUANG Xin, et al. Robust Reputation-Based Ranking on Bipartite Rating Networks[C]// SIAM. 2012 SIAM International Conference on Data Mining. Philadelphia: SIAM, 2012: 612-623. |
| [45] | FANG Baogang, ZHONG Bocheng, ZHANG Jialei. Data Security Aggregation Method in WSNs[J]. Transducer and Microsystem Technologies, 2022, 41(4): 146-148, 152. |
| 房保纲, 钟伯成, 张家磊. 无线传感器网络中数据安全聚合方法[J]. 传感器与微系统, 2022, 41(4):146-148,152. | |
| [46] |
DE K C, VAN D P. Iterative Filtering in Reputation Systems[J]. SIAM Journal on Matrix Analysis and Applications, 2010, 31(4): 1812-1834.
doi: 10.1137/090748196 URL |
| [47] |
YI Yeqing, LIN Yaping, LI Xiaolong, et al. False Data Filtering Algorithm Using Cooperation Watermarks for WSN[J]. Journal of Software, 2010, 21(1): 107-118.
doi: 10.3724/SP.J.1001.2010.03373 URL |
| 易叶青, 林亚平, 李小龙, 等. WSN中基于协作水印的虚假数据过滤算法[J]. 软件学报, 2010, 21(1):107-118. | |
| [48] | NATH S, GIBBONS P B, SESHAN S, et al. Synopsis Diffusion for Robust Aggregation in Sensor Networks[J]. ACM Transactions on Sensor Networks(TOSN), 2008, 4(2): 1-40. |
| [49] |
ROY S, CONTI M, SETIA S, et al. Secure Data Aggregation in Wireless Sensor Networks[J]. IEEE Transactions on Information Forensics and Security, 2012, 7(3): 1040-1052.
doi: 10.1109/TIFS.2012.2189568 URL |
| [50] |
MA Miao. Resilience of Sink Filtering Scheme in Wireless Sensor Networks[J]. Computer Communications, 2006, 30(1): 55-65.
doi: 10.1016/j.comcom.2006.07.015 URL |
| [1] | 周婧怡, 李红娇. 针对PMU测量的虚假数据注入攻击检测方法[J]. 信息网络安全, 2022, 22(5): 75-83. |
| [2] | 张永棠. 一种基于安全区域的WSN流量分析聚合方法[J]. 信息网络安全, 2021, 21(9): 80-89. |
| [3] | 肖帅, 张翰林, 咸鹤群, 陈飞. 一种面向物联网设备的口令认证密钥协商协议[J]. 信息网络安全, 2021, 21(10): 83-89. |
| [4] | 江金芳, 韩光洁. 无线传感器网络中信任管理机制研究综述[J]. 信息网络安全, 2020, 20(4): 12-20. |
| [5] | 亢保元, 王佳强, 邵栋阳, 李春青. 一种适用于异构Ad Hoc无线传感器网络的身份认证与密钥共识协议[J]. 信息网络安全, 2018, 18(1): 23-30. |
| [6] | 章红艳, 许力, 林丽美. 无线传感器网络中基于超立方体的对密钥建立方案研究[J]. 信息网络安全, 2017, 17(12): 1-5. |
| [7] | 钟敦昊, 张冬梅, 张玉. 一种基于相似度计算的无线传感器网络入侵检测方法[J]. 信息网络安全, 2016, 16(2): 22-27. |
| [8] | 刘伟, 叶清, 王成. 基于动态密钥管理的改进LEACH路由算法[J]. 信息网络安全, 2015, 15(8): 41-46. |
| [9] | 苏彬庭, 方禾, 许力. 基于Q-Learning的无线传感器网络生命周期平衡路由[J]. 信息网络安全, 2015, 15(4): 74-77. |
| [10] | 龚婉婉, 刘士兴, 冯婷婷. 基于无线传感器网络的智能家居监控平台设计[J]. 信息网络安全, 2015, 15(3): 79-83. |
| [11] | 仇各各, 汪学明, 张言胜. 基于HECC的WSN身份认证协议研究[J]. 信息网络安全, 2015, 26(12): 54-58. |
| [12] | 杨骏玮, 方杰, 张仕斌, 陈建钧. WSNs中基于重复博弈的信任评价方法研究[J]. 信息网络安全, 2014, 14(8): 82-87. |
| [13] | 佟鑫;张利;戴明. 物联网感知层安全威胁建模研究[J]. , 2013, 13(Z): 0-0. |
| [14] | 郎为民;陈林;王昊. 无线传感器网络云连接认证研究[J]. , 2013, 13(3): 0-0. |
| [15] | 高立兵. 基于无线传感器网络的井下定位系统研究[J]. , 2013, 13(2): 0-0. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||