信息网络安全 ›› 2022, Vol. 22 ›› Issue (12): 57-66.doi: 10.3969/j.issn.1671-1122.2022.12.007
基于LSTM的CAN入侵检测模型研究
- 1.上海交通大学网络安全技术研究院,上海 200240
2.上海市信息安全综合管理技术研究重点实验室,上海 200240
3.上海交通大学网络空间安全学院,上海 200240
-
收稿日期:2022-10-09出版日期:2022-12-10发布日期:2022-12-30 -
通讯作者:银鹰 E-mail:yyin@sjtu.edu.cn -
作者简介:银鹰(1977—),女,湖南,助理研究员,硕士,主要研究方向为网络安全检测与风险评估、密码应用安全和车联网安全|周志洪(1979—),男,江西,讲师,博士,主要研究方向为网络安全检测与风险评估、密码应用安全和车联网安全|姚立红(1974—),女,江苏,高级工程师,博士,主要研究方向为操作系统与移动端安全、车联网安全 -
基金资助:国家自然科学基金(U20B2048)
Research on LSTM-Based CAN Intrusion Detection Model
YIN Ying1,2( ), ZHOU Zhihong1,2, YAO Lihong3
), ZHOU Zhihong1,2, YAO Lihong3
- 1. Institute of Cyber Science and Technology, Shanghai Jiao Tong University, Shanghai 200240, China
2. Shanghai Key Laboratory of Integrated Administration Technologies for Information Security, Shanghai 200240, China
3. School of Cyber Science and Engineering, Shanghai Jiao Tong University, Shanghai 200240, China
-
Received:2022-10-09Online:2022-12-10Published:2022-12-30 -
Contact:YIN Ying E-mail:yyin@sjtu.edu.cn
摘要:
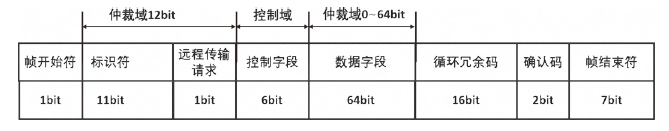
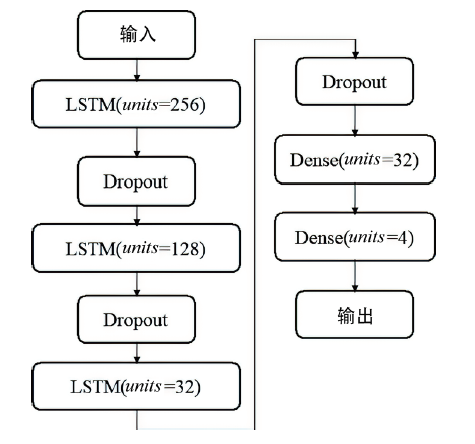
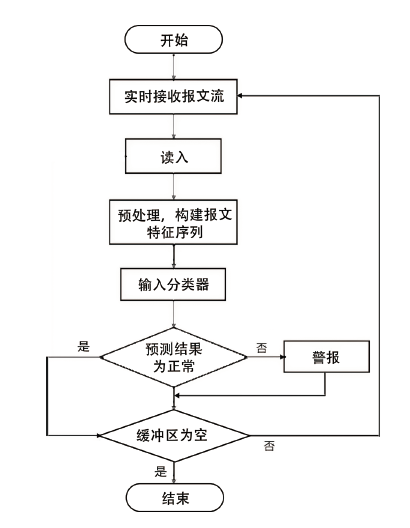
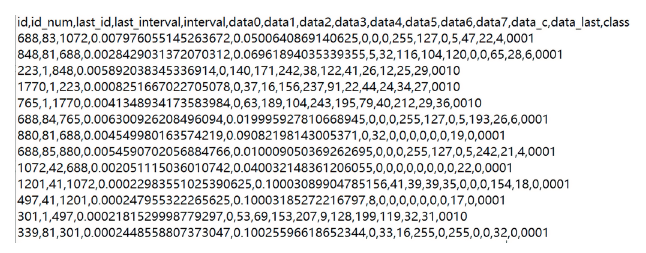
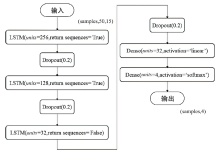
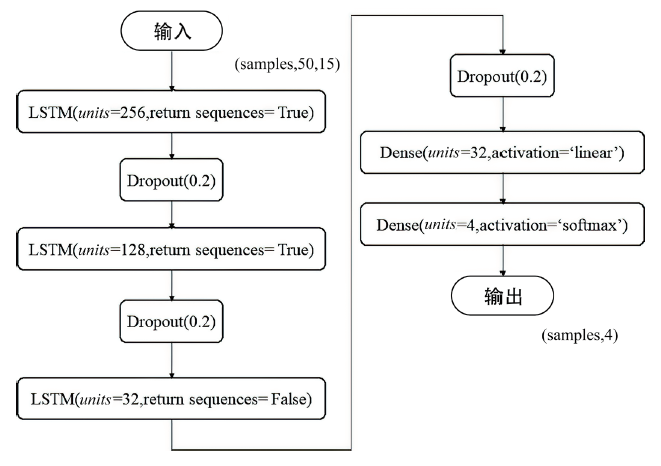
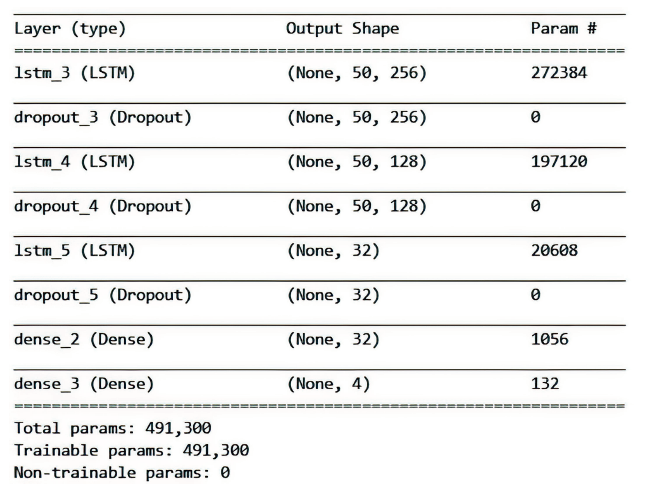
车载控制器局域网(Controller Area Network,CAN)连接着智能网联汽车系统的核心电子控制单元,对于保证汽车系统的安全性至关重要。由于其缺乏足够的信息安全措施,容易遭受拒绝服务(Denial of Service,DoS)攻击、重放攻击、模糊攻击等,给汽车系统及驾乘人员带来严重安全威胁。文章通过分析车载CAN面临的信息安全威胁,提取CAN报文在报文ID、时间间隔、数据字段中的通信特征,提出一种基于长短期记忆(Long Short Term Memory,LSTM)的CAN入侵检测模型,该模型能有效保留CAN报文的时序特征,在CAN遭受攻击时检测攻击行为以及对应的攻击类型。实验结果表明,该模型的攻击检测精度达99.99%。
中图分类号:
引用本文
银鹰, 周志洪, 姚立红. 基于LSTM的CAN入侵检测模型研究[J]. 信息网络安全, 2022, 22(12): 57-66.
YIN Ying, ZHOU Zhihong, YAO Lihong. Research on LSTM-Based CAN Intrusion Detection Model[J]. Netinfo Security, 2022, 22(12): 57-66.
| [1] | Upstream. Upstream’s 2022 Global Automotive Cybersecurity Report[EB/OL]. (2022-01-26) [2022-09-08]. https://upstream.auto/2022report/. |
| [2] | XIA Ziyan, ZHOU Zhitong, LI Xiang, et al. Feasibility Study on Automobile Electronic Control System of ECU Intrusion and Virus[J]. Netinfo Security, 2014, 14(9): 193-195. |
| 夏子焱, 周之童, 李响, 等. 汽车ECU电控系统入侵与汽车病毒编写的可行性研究[J]. 信息网络安全, 2014, 14(9):193-195. | |
| [3] | FENG Cong. Research on the Governance and Law Enforcement of Network Security of Intelligent Connected Vehicles[J]. Netinfo Security, 2020(S1):44-47. |
| 冯聪. 智能网联汽车网络安全问题的治理与执法探索[J]. 信息网络安全, 2020(S1):44-47. | |
| [4] | Security Guest. 360 Network Attack and Defense Lab Has Revealed a Second High Risk Vulnerability in a Tesla Vehicle-The Ability to Open the Vehicle Without a Key[EB/OL]. (2015-01-21) [2022-09-08]. https://anyun.org/a/yejiezixun/2015/0129/4460.html. |
| 安全客. 360网络攻防实验室公布第二例特斯拉高危漏洞—无需钥匙开启车辆[EB/OL].(2015-01-21) [2022-09-08]. https://anyun.org/a/yejiezixun/2015/0129/4460.html. | |
| [5] | Tencent Technology. Tencent Cohen Lab Successfully Invaded Tesla Remotely for the First Time in the World[EB/OL]. (2016-09-20) [2022-09-08]. https://news.mydrivers.com/1/500/500287.htm. |
| 腾讯科技. 腾讯科恩实验室成功远程入侵特斯拉为全球首次[EB/OL].(2016-09-20) [2022-09-08]. https://news.mydrivers.com/1/500/500287.htm. | |
| [6] | LI Yilin, YAN Zheng, XIE Haomeng. Survey of Privacy Preservation in VANET[J]. Netinfo Security, 2019, 19(4): 63-72. |
| 李怡霖, 闫峥, 谢皓萌. 车载自组织网络的隐私保护综述[J]. 信息网络安全, 2019, 19(4):63-72. | |
| [7] |
CHOI W, JO H J, WOO S, et al. Identifying ECUs Using Inimitable Characteristics of Signals in Controller Area Networks[J]. IEEE Transactions on Vehicular Technology, 2018, 67(6): 4757-4770.
doi: 10.1109/TVT.2018.2810232 URL |
| [8] | NILSSON D K, LARSON U E, JONSSON E. Efficient in-Vehicle Delayed Data Authentication Based on Compound Message Authentication Codes[C]// IEEE. 2008 IEEE 68th Vehicular Technology Conference. New York: IEEE, 2008: 1-5. |
| [9] | HAZEM A, FAHMY H A. LCAP-a Lightweight Can Authentication Protocol for Securing in-Vehicle Networks[EB/OL]. (2012-06-20) [2022-09-08]. http://www.eece.cu.edu.eg/-hfahmy/publish/escar2012.pdf. |
| [10] | GMIDEN M, GMIDEN M H, TRABELSI H. An Intrusion Detection Method for Securing in-Vehicle CAN Bus[C]// IEEE. 2016 17th International Conference on Sciences and Techniques of Automatic Control and Computer Engineering (STA). New York: IEEE, 2016: 176-180. |
| [11] | MARCHETTI M, STABILI D. Anomaly Detection of CAN Bus Messages through Analysis of ID Sequences[C]// IEEE. 2017 IEEE Intelligent Vehicles Symposium (IV). New York: IEEE, 2017: 1577-1583. |
| [12] | MÜTER M, ASAJ N. Entropy-Based Anomaly Detection for in-Vehicle Networks[C]// IEEE. 2011 IEEE Intelligent Vehicles Symposium (IV). New York: IEEE, 2011: 1110-1115. |
| [13] | STABILI D, MARCHETTI M, COLAJANNI M. Detecting Attacks to Internal Vehicle Networks through Hamming Distance[C]// IEEE. 2017 AEIT International Annual Conference. New York: IEEE, 2017: 1-6. |
| [14] | CHO K T, SHIN K G. Fingerprinting Electronic Control Units for Vehicle Intrusion Detection[C]// USENIX. 25th USENIX Security Symposium (USENIX Security 16). Berkeley:USENIX, 2016: 911-927. |
| [15] | SEO E, SONG H M, KIM H K. Gids: GAN Based Intrusion Detection System for in-Vehicle Network[C]// IEEE. 2018 16th Annual Conference on Privacy, Security and Trust (PST). New York: IEEE, 2018: 1-6. |
| [16] |
ZHU Konglin, CHEN Zhicheng, PENG Yuyang, et al. Mobile Edge Assisted Literal Multi-Dimensional Anomaly Detection of in-Vehicle Network Using LSTM[J]. IEEE Transactions on Vehicular Technology, 2019, 68(5): 4275-4284.
doi: 10.1109/TVT.2019.2907269 URL |
| [17] | GAZDAG A, NEUBRANDT D, BUTTYÁN L, et al. Detection of Injection Attacks in Compressed CAN Traffic Logs[C]// Springer. 2018 Security and Safety Interplay of Intelligent Software Systems. New York: Springer, 2018: 111-124. |
| [18] | KANG M J, KANG J W. Intrusion Detection System Using Deep Neural Network for in-Vehicle Network Security[EB/OL]. (2016-06-07) [2022-09-08]. https://pubmed.ncbi.nlm.nih.gov/27271802/. |
| [19] | MO Xiuliang, CHEN Pengyuan, WANG Jianing, et al. Anomaly Detection of Vehicle CAN Network Based on Message Content[C]// Springer. International Conference on Security and Privacy in New Computing Environments. New York: Springer, 2019: 96-104. |
| [20] | SONG H M, WOO J, KIM H K. In-Vehicle Network Intrusion Detection Using Deep Convolutional Neural Network[EB/OL]. (2019-10-03) [2022-09-08]. https://www.sciencedirect.com/science/article/abs/pii/S2214209619302451. |
| [21] |
HOCHREITER S, SCHMIDHUBER J. Long Short-Term Memory[J]. Neural Computation, 1997, 9(8): 1735-1780.
pmid: 9377276 |
| [22] | MALHOTRA P, VIG L, SHROFF G, et al. Long Short Term Memory Networks for Anomaly Detection in Time Series[EB/OL]. (2015-04-22) [2022-09-08]. https://www.researchgate.net/publication/304782562_Long_Short_Term_Memory_Networks_for_Anomaly_Detection_in_Time_Series. |
| [23] | MARKOVITZ M, WOOL A. Field Classification, Modeling and Anomaly Detection in Unknown CAN Bus Networks[J]. Vehicular Communications, 2017(9): 43-52. |
| [24] | LIU Xin, WANG Jiayin, YANG Haorui, et al. An Internet of Vehicles Authentication Protocol Based on Blockchain and SecGear Framework[J]. Netinfo Security, 2022, 22(1): 27-36. |
| 刘忻, 王家寅, 杨浩睿, 等. 一种基于区块链和SecGear框架的车联网认证协议[J]. 信息网络安全, 2022, 22(1):27-36. | |
| [25] | HCRL. Car Hacking for Intrusion Detection[EB/OL]. (2018-08-01) [2022-09-08]. https://ocslab.hksecurity.net/Dataset/CAN-intrusion-dataset. |
| [1] | 张光华, 刘永升, 王鹤, 于乃文. 基于BiLSTM和注意力机制的智能合约漏洞检测方案[J]. 信息网络安全, 2022, 22(9): 46-54. |
| [2] | 张兴兰, 付娟娟. 基于辅助熵减的神经常微分方程入侵检测模型[J]. 信息网络安全, 2022, 22(6): 1-8. |
| [3] | 王浩洋, 李伟, 彭思维, 秦元庆. 一种基于集成学习的列车控制系统入侵检测方法[J]. 信息网络安全, 2022, 22(5): 46-53. |
| [4] | 沈卓炜, 范琳丽, 华童, 王科翔. 异常权限配置下的角色挖掘方案[J]. 信息网络安全, 2022, 22(11): 7-16. |
| [5] | 白宏鹏, 邓东旭, 许光全, 周德祥. 基于联邦学习的入侵检测机制研究[J]. 信息网络安全, 2022, 22(1): 46-54. |
| [6] | 何红艳, 黄国言, 张炳, 贾大苗. 基于极限树特征递归消除和LightGBM的异常检测模型[J]. 信息网络安全, 2022, 22(1): 64-71. |
| [7] | 刘烁, 张兴兰. 基于双重注意力的入侵检测系统[J]. 信息网络安全, 2022, 22(1): 80-86. |
| [8] | 李群, 董佳涵, 关志涛, 王超. 一种基于聚类分类的物联网恶意攻击检测方法[J]. 信息网络安全, 2021, 21(8): 82-90. |
| [9] | 任涛, 金若辰, 罗咏梅. 融合区块链与联邦学习的网络入侵检测算法[J]. 信息网络安全, 2021, 21(7): 27-34. |
| [10] | 杜晔, 王子萌, 黎妹红. 基于优化核极限学习机的工控入侵检测方法[J]. 信息网络安全, 2021, 21(2): 1-9. |
| [11] | 王华忠, 程奇. 基于改进鲸鱼算法的工控系统入侵检测研究[J]. 信息网络安全, 2021, 21(2): 53-60. |
| [12] | 沈也明, 李贝贝, 刘晓洁, 欧阳远凯. 基于主动学习的工业互联网入侵检测研究[J]. 信息网络安全, 2021, 21(1): 80-87. |
| [13] | 李桥, 龙春, 魏金侠, 赵静. 一种基于LMDR和CNN的混合入侵检测模型[J]. 信息网络安全, 2020, 20(9): 117-121. |
| [14] | 徐国天. 网络入侵检测中K近邻高速匹配算法研究[J]. 信息网络安全, 2020, 20(8): 71-80. |
| [15] | 姜楠, 崔耀辉, 王健, 吴晋超. 基于上下文特征的IDS告警日志攻击场景重建方法[J]. 信息网络安全, 2020, 20(7): 1-10. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||