信息网络安全 ›› 2021, Vol. 21 ›› Issue (5): 39-47.doi: 10.3969/j.issn.1671-1122.2021.05.005
基于改进保留格式加密的民航旅客数据脱敏方法
- 1.中国民航大学信息安全测评中心,天津 300300
2.中国民航大学计算机科学与技术学院,天津 300300
3.中国民航信息网络股份有限公司,北京 101318
-
收稿日期:2020-10-13出版日期:2021-05-10发布日期:2021-06-22 -
通讯作者:蔡畅 E-mail:18822129196@163.com -
作者简介:顾兆军(1966—),男,山东,教授,博士,主要研究方向为网络与信息安全、民航信息系统|蔡畅(1996—),女,山东,硕士研究生,主要研究方向为网络信息安全、数据安全|王明(1981—),男,北京,工程师,本科,主要研究方向为数据安全、安全开发、自动化安全测试、渗透测试 -
基金资助:国家自然科学基金(61601467);国家自然科学基金(U1533104);民航科技项目(MHRD20140205);民航科技项目(MHRD20150233);民航安全能力建设项目(PESA170003);民航安全能力建设项目(PESA2018079);民航安全能力建设项目(PESA2018082);民航安全能力建设项目(PESA2019073);民航安全能力建设项目(PESA2019074)
The Masking Method of Civil Aviation Passenger Data Based on Improved Format-preserving Encryption
GU Zhaojun1,2, CAI Chang1,2( ), WANG Ming3
), WANG Ming3
- 1. Information Security Evaluation Center, Civil Aviation University of China, Tianjin 300300, China
2. College of Computer Science and Technology, Civil Aviation University of China, Tianjin 300300, China
3. TravelSky Technology Limited, Beijing 101318, China
-
Received:2020-10-13Online:2021-05-10Published:2021-06-22 -
Contact:CAI Chang E-mail:18822129196@163.com
摘要:
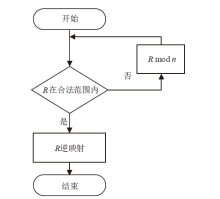
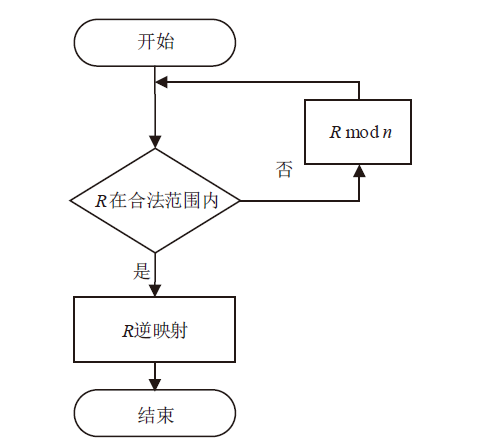
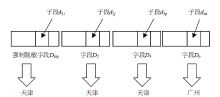
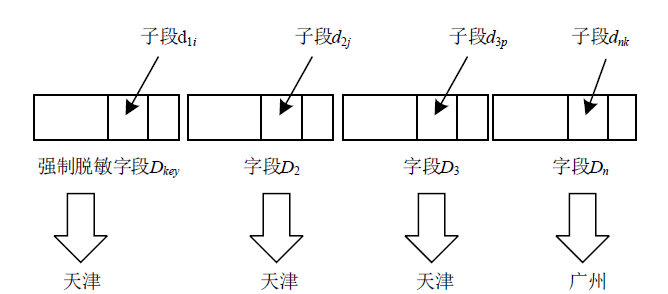
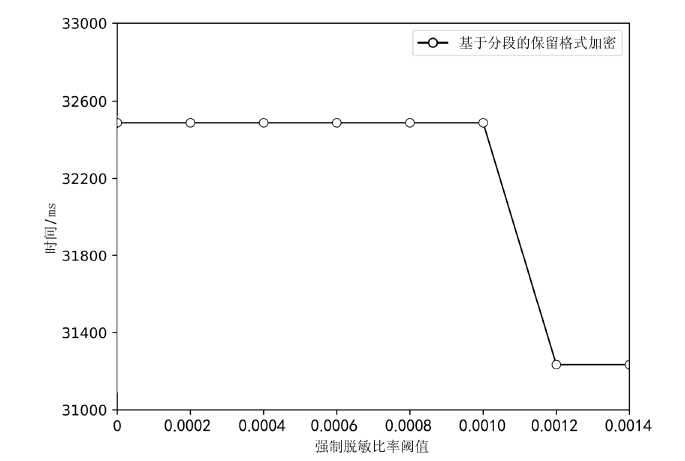
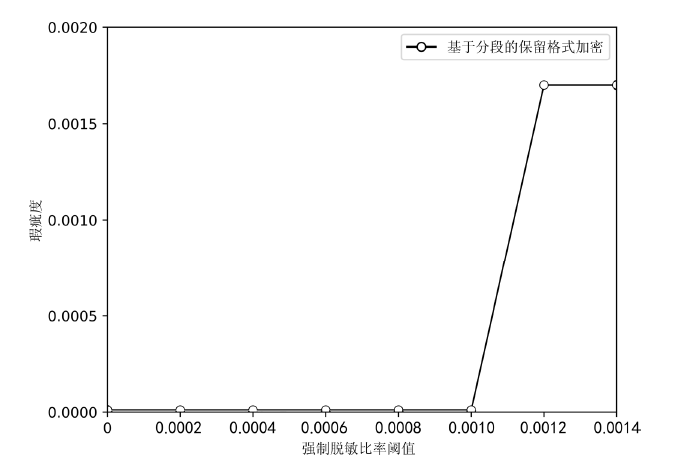
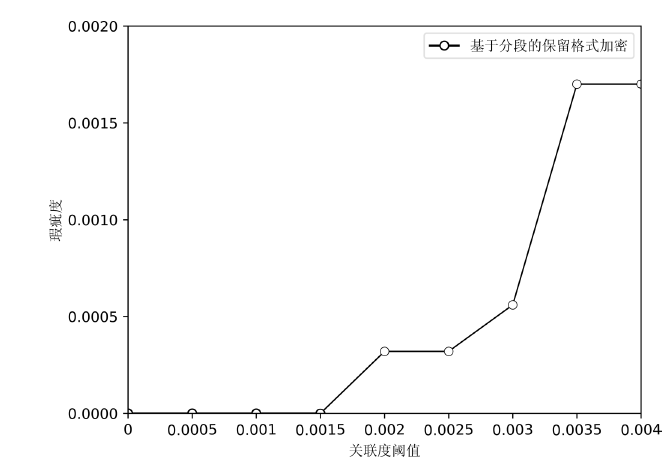
文章提出逆推检验法和瑕疵度指标,以量化和检验脱敏后数据的关联性。同时提出消除基于保留格式加密的数据关联性敏感子段模型,通过计算各个子段之间的关联性并设置阈值消除关联性,筛选合理的脱敏子段。理论分析和实验结果表明,改进后保留格式加密方法脱敏的数据的瑕疵度降低,在有效降低数据泄露风险的同时保证了数据的可用性。
中图分类号:
引用本文
顾兆军, 蔡畅, 王明. 基于改进保留格式加密的民航旅客数据脱敏方法[J]. 信息网络安全, 2021, 21(5): 39-47.
GU Zhaojun, CAI Chang, WANG Ming. The Masking Method of Civil Aviation Passenger Data Based on Improved Format-preserving Encryption[J]. Netinfo Security, 2021, 21(5): 39-47.
表3
明文模拟数据
| 身份证号 | 姓名 | 手机号 | 邮箱 | 出发 机场 | 目的 机场 | 航班 |
|---|---|---|---|---|---|---|
| 372522*** ***0014 | 汪*山 | 1506886**** | dfsg7266d@ qq.com | HGH | DLC | CZ6328 |
| 420226*** ***3011 | 宋* | 1810501**** | Zfisrg1@ 163.com | SHA | XMN | FM9261 |
| 370602*** ***091X | 刘* | 1390535**** | 4sgf45874@ qq.com | CAN | YNT | CZ3509 |
| 410103**** ***2921 | 王*圣 | 1822551**** | xujsh2404@ yahoo.com.cn | SHA | ZUH | 9C8819 |
| 320183*** ***6015 | 李*男 | 1802410**** | 7gdr25564@ qq.com | SHE | TAO | TZ185 |
表3
表4
保留格式加密后的数据
| 身份证号 | 姓名 | 手机号 | 邮箱 | 出发 机场 | 目的 机场 | 航班 |
|---|---|---|---|---|---|---|
| 372522*** ***0011 | 方*比 | 1509066**** | pxtfjob.m@ qq.com | LXA | YUS | CZ5221 |
| 420226*** ***3017 | 李*凯 | 1818755**** | 7r140ga@ 163.com | WUH | HRB | ZH2487 |
| 370602*** ***0914 | 并* | 1398794**** | zsb.qgp1q@ qq.com | CSX | HAK | GS8244 |
| 410103*** ***2924 | 郑*达 | 1827378**** | 591oioys.@ yahoo.com.cn | WUH | HRB | FM9620 |
| 320183*** ***6019 | 宋*共 | 1801267**** | i36ndq9e9@ qq.com | CSX | HAK | KU167 |
表4
表5
基于效率的关联性值计算表
| 序号 | Cor(Dkey,D2) | Cor(Dkey,D3) | Cor(Dkey,Dn) | w |
|---|---|---|---|---|
| 0 | 0 | 0 | 0 | 0 |
| 1 | 0 | 0 | 0 | 0 |
| 2 | 0 | 0 | 0 | 0 |
| 3 | 0 | 0 | 0 | 0 |
| 4 | 0 | 0 | 0 | 0 |
| 5 | 0 | 0 | 0 | 0 |
| 6 | 0 | 0 | 0 | 0 |
| 7 | 0 | 0 | 0 | 0 |
| 8 | 0 | 0 | 0 | 0 |
| 9 | 1 | 0 | 0 | 2 |
| 10 | 0 | 0 | 0 | 0 |
| 11 | 0 | 0 | 0 | 0 |
| 12 | 0 | 0 | 0 | 0 |
| 13 | 0 | 0 | 0 | 0 |
| 14 | 0 | 0 | 0 | 0 |
| 15 | 0 | 0 | 0 | 0 |
| 16 | 1 | 0 | 1 | 2 |
| 17 | 0 | 0 | 0 | 0 |
| 18 | 0 | 0 | 0 | 0 |
| 19 | 0 | 0 | 0 | 0 |
| 20 | 0 | 0 | 0 | 0 |
| … | … | … | … | … |
| 11143 | 1 | 0 | 1 | 2 |
| 11144 | 0 | 0 | 0 | 0 |
| 11145 | 0 | 0 | 0 | 0 |
| 11146 | 0 | 0 | 0 | 0 |
| 11147 | 0 | 0 | 0 | 0 |
| 11148 | 0 | 0 | 0 | 0 |
| 11149 | 0 | 1 | 0 | 1 |
| 关联度 | B1=0.003043 | B2=0.00206 | B3=0.00278 |
表5
表6
基于安全性的关联性值计算表
| 序号 | Cor(Dkey,D2) | Cor(Dkey,D3) | Cor(Dkey,Dn) | Cor(D2,D3) | Cor(D2,Dn) | Cor(D3,Dn) | w |
|---|---|---|---|---|---|---|---|
| 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| 2 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| 3 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| 4 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| 5 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| 6 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| 7 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| 8 | 0 | 0 | 0 | 0 | 1 | 0 | 1 |
| 9 | 1 | 0 | 0 | 0 | 0 | 0 | 1 |
| 10 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| 11 | 0 | 0 | 0 | 0 | 1 | 0 | 1 |
| 12 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| 13 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| 14 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| 15 | 0 | 0 | 0 | 0 | 0 | 0 | |
| 16 | 1 | 0 | 1 | 0 | 1 | 0 | 3 |
| 17 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| 18 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| 19 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| 20 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| … | … | … | … | … | … | … | … |
| 11143 | 1 | 0 | 1 | 0 | 0 | 0 | 2 |
| 11144 | 0 | 0 | 0 | 1 | 0 | 0 | 1 |
| 11145 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| 11146 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| 11147 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| 11148 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| 11149 | 0 | 1 | 0 | 0 | 0 | 0 | 1 |
| 关联度 | B1=0.003043 | B2=0.00206 | B3=0.00278 | B4=0.001704 | B5=0.00296 | B6=0 |
表6
表8
脱敏结果
| 身份证号 | 姓名 | 手机号 | 邮箱 | 出发 机场 | 目的 机场 | 航班 |
|---|---|---|---|---|---|---|
| 150203*** ***0012 | 方*比 | 1509066 **** | pxtfjob.m@ qq.com | LXA | YUS | CZ5221 |
| 370783*** ***3013 | 李* | 1818755 **** | 7r140ga@ 163.com | WUH | HRB | ZH2487 |
| 630102*** ***0915 | 并* | 1398794 **** | zsb.qgp1q@ qq.com | CSX | HAK | FZ5209 |
| 421302*** ***2550 | 郑*达 | 1827378 **** | 591oioys.@ yahoo.com.cn | WUH | HRB | FM9620 |
| 131102*** ***0016 | 宋*共 | 1801267 **** | i36ndq9e9@ qq.com | CSX | HAK | KU167 |
表8
| [1] | WU Ying, ZOU Yu, WEI Changhui, et al. Government and Enterprise Big Data Security[J]. Secrecy Science and Technology, 2019,10(12):41-44. |
| 吴迎, 邹彧, 魏常辉, 等. 政企大数据安全[J]. 保密科学技术, 2019,10(12):41-44. | |
| [2] | ME Yikun. Information Security in E-commerce[J]. Economy and Technology of Civil Aviation, 2000,7(6):60-62. |
| 么轶堃. 浅谈民航电子商务及其信息安全[J]. 民航经济与技术, 2000,7(6):60-62. | |
| [3] | ZHANG Yuguang, HU Ying. International Dynamic Review of Data Security in 2019[J]. Secrecy Science and Technology, 2019,10(12):32-35. |
| 张宇光, 胡影. 2019年数据安全国际动态综述[J]. 保密科学技术, 2019,10(12):32-35. | |
| [4] | ADAM N R, WORTHMANN J C. Security-control Methods for Statistical Databases: A Comparative Study[J]. ACM Computing Surveys(CSUR), 1989,21(4):515-556. |
| [5] |
RADHAKRISHNAN R, KHARRAZI M, MEMON N. Data Masking: A New Approach for Steganography?[J]. Journal of VLSI Signal Processing Systems for Signal, Image and Video Technology, 2005,41(3):293-303.
doi: 10.1007/s11265-005-4153-1 URL |
| [6] | STÜTZ T, UHL A. Efficient Format-compliant Encryption of Regular Languages: Block-based Cycle-walking[C]// IFIP. International Conference on Communications and Multimedia Security, May 31-June 2, 2010, Linz, Austria. Heidelberg: Springer, 2010: 81-92. |
| [7] | PAUKER M J, SPIES T, MARTIN L W. Data Processing Systems with Format-preserving Encryption and Decryption Engines: US, Patent 7, 864, 952[P]. 2011-01-04. |
| [8] | CUI Baojiang, ZHANG Baihui, WANG Kaiyue. A Data Masking Scheme for Sensitive Big Data Based on Format-preserving Encryption[C]// IEEE. 2017 IEEE International Conference on Computational Science and Engineering(CSE) and IEEE International Conference on Embedded and Ubiquitous Computing(EUC), July 21-24, 2017, Guangzhou, China. New York: IEEE, 2017: 518-524. |
| [9] | WANG Peng. Research and Implementation on Multi-type Format-preserving Encryption Techniques[D]. Beijing: Beijing University of Posts and Telecommunications, 2017. |
| 王鹏. 多类型数据保留格式加密技术的研究与实现[D]. 北京:北京邮电大学, 2017. | |
| [10] | LENK A, MARCUS P, POVOA I. GeoFPE: Format Preserving Encryption of Geospatial Data for the Internet of Things[C]// IEEE. 2018 IEEE International Congress on Internet of Things(ICIOT), July 2-7, 2018, San Francisco, CA, USA. New York: IEEE, 2018: 172-175. |
| [11] | BLACK J, ROGAWAY P. Ciphers with Arbitrary Finite Domains[C]// Springer. Cryptographers’ Track at the RSA Conference, February 18-22, 2002, San José, CA, USA. Heidelberg: Springer, 2002: 114-130. |
| [12] | BEAULIEU R, SHORS D, SMITH J, et al. The SIMON and SPECK Families of Lightweight Block Ciphers[J]. IACR Cryptology ePrint Archive, 2013(1):404-449. |
| [13] | EUR-lex Regulation(EU) 2016/679 of the European Parliament and of the Council of 27 April 2016[EB/OL]. https://eur-lex.europa.eu/legal-content/EN/ТXT/?uri=CELEX%3A32016R0679, 2016-04-27. |
| [14] | FANG Yuejian, ZHU Jinzhong, ZHOU Wen, et al. A Survey on Data Mining Privacy Protection Algorithms[J]. Netinfo Security, 2017,17(2):6-11. |
| 方跃坚, 朱锦钟, 周文, 等. 数据挖掘隐私保护算法研究综述[J]. 信息网络安全, 2017,17(2):6-11. | |
| [15] |
LI Jingwei, LIU Zheli, XU Li, et al. An Efficient Format-preserving Encryption Mode for Practical Domains[J]. Wuhan University Journal of Natural Sciences, 2012,17(5):428-434.
doi: 10.1007/s11859-012-0865-9 URL |
| [16] |
LIU Zheli, JIA Chunfu, LI Jingwei. Research on the Format-preserving Encryption Modes[J]. Journal on Communications, 2011,32(6):184-190.
doi: 10.1111/j.1460-2466.1982.tb02510.x URL |
| 刘哲理, 贾春福, 李经纬. 保留格式加密模型研究[J]. 通信学报, 2011,32(6):184-190. | |
| [17] | LI Peng, WANG Ming, ZHANG Haiyang. Research on Desensitization Technology of Passenger Sensitive Data in Civil Aviation Important Information System[J]. Modern Information Technology, 2019,3(5):150-152. |
| 李鹏, 王明, 张海洋. 民航重要信息系统旅客敏感数据的脱敏技术研究[J]. 现代信息科技, 2019,3(5):150-152. | |
| [18] | LIU Jun, LI Zehao, SU Guoyu, et al. Application of Reserved Format Encryption Technology in Information Processing of Civil Aviation Information System[J]. Computer Science, 2019,46(S1):571-576. |
| 刘俊, 李泽昊, 苏国宇, 等. 保留格式加密技术在民航信息系统数据处理中的应用研究[J]. 计算机科学, 2019,46(S1):571-576. | |
| [19] | BELLARE M, RISTENPART T, ROGAWAY P, et al. Format-preserving Encryption[C]// Springer. 16th Annual International Workshop on Selected Areas in Cryptography, August 13-14, 2009, Calgary, Alberta, Canada. Heidelberg: Springer, 2009: 295-312. |
| [20] |
LIU Zheli, JIA Chunfu, LI Jingwei. Research on the Format-preserving Encryption Techniques[J]. Journal of Software, 2012,23(1):152-170.
doi: 10.3724/SP.J.1001.2012.04096 URL |
| 刘哲理, 贾春福, 李经纬. 保留格式加密技术研究[J]. 软件学报, 2012,23(1):152-170. | |
| [21] | SINGH G. A Study of Encryption Algorithms(RSA, DES, 3DES and AES) for Information Security[J]. International Journal of Computer Applications, 2013,67(19):33-38. |
| [22] | GB/T 35273-2017 Information Security Technology-personal Information Security Specification[S] Beijing: Standards Press of China, 2017. |
| GB/T 35273-2017 信息安全技术个人信息安全规范[S] 北京: 中国标准出版社, 2017. |
| [1] | 胡荣磊, 何艳琼, 曾萍, 范晓红. 一种大数据环境下医疗隐私保护方案设计与实现[J]. 信息网络安全, 2018, 18(9): 48-54. |
| [2] | 张建标, 杨石松, 涂山山, 王晓. 面向云计算环境的vTPCM可信管理方案[J]. 信息网络安全, 2018, 18(4): 9-14. |
| [3] | 任晓贤, 陈洁, 李晨阳, 杨义先. 基于风险矩阵的物联网系统漏洞关联性危害评估[J]. 信息网络安全, 2018, 18(11): 81-88. |
| [4] | 李彦果. 浅谈光盘刻录来源关联性分析[J]. , 2010, (11): 0-0. |
| [5] | 李佟鸿;麦永浩. 数据挖掘在网络取证中的应用方法研究[J]. , 2008, 8(8): 0-0. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||