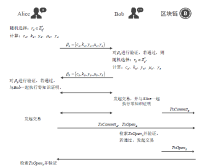
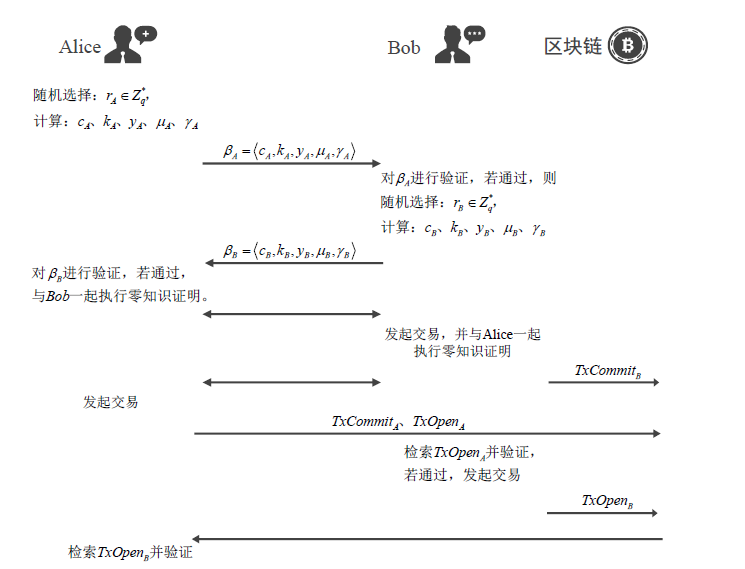
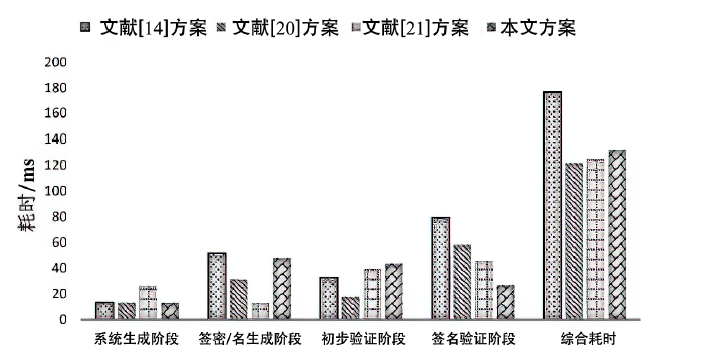
信息网络安全 ›› 2021, Vol. 21 ›› Issue (5): 19-30.doi: 10.3969/j.issn.1671-1122.2021.05.003
基于区块链的公平交换方案
- 1.重庆邮电大学计算机科学与技术学院,重庆 400065
2.重庆邮电大学网络空间安全与信息法学院,重庆 400065
-
收稿日期:2021-01-20出版日期:2021-05-10发布日期:2021-06-22 -
通讯作者:周由胜 E-mail:zhouys@cqupt.edu.cn -
作者简介:周由胜(1979—),男,湖北,副教授,博士,主要研究方向为公钥密码、区块链、移动互联网安全、云安全和物联网安全|钟天琦(1994—),男,重庆,硕士研究生,主要研究方向为公平交换协议、区块链技术 -
基金资助:国家自然科学基金(61702067);重庆市自然科学基金(cstc2020joymsxmX0343);重庆市留学人员回国创业创新支持计划(CX2018122)
Blockchain-based Fair Exchange Scheme
ZHOU Yousheng1,2( ), ZHONG Tianqi1
), ZHONG Tianqi1
- 1. College of Computer Science and Technology, Chongqing University of Posts and Telecommunications, Chongqing 400065, China
2. College of Cyber Security and Information Law, Chongqing University of Posts and Telecommunications, Chongqing 400065, China
-
Received:2021-01-20Online:2021-05-10Published:2021-06-22 -
Contact:ZHOU Yousheng E-mail:zhouys@cqupt.edu.cn
摘要:
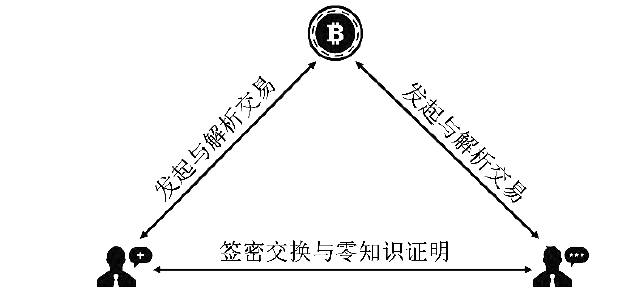
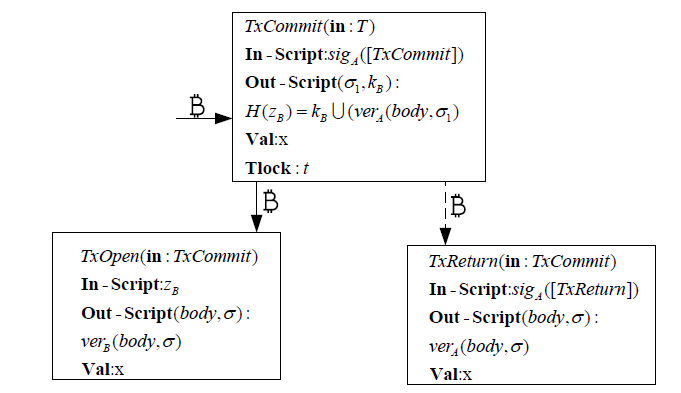
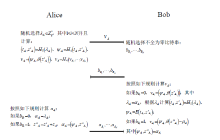
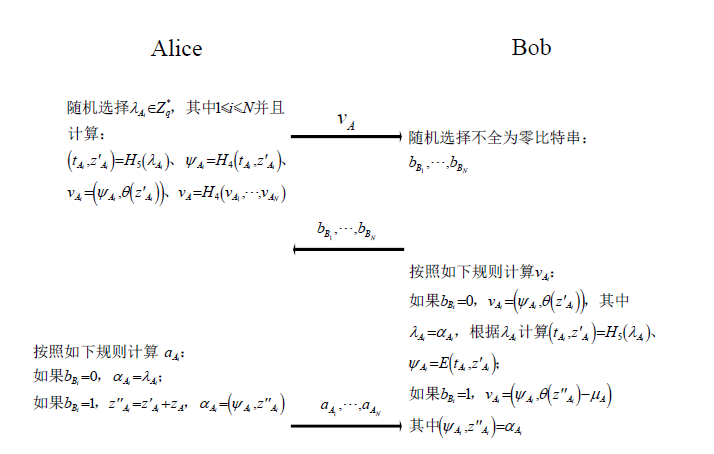
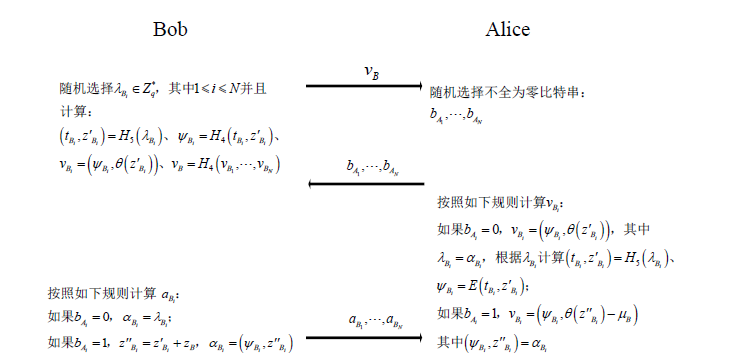
随着电子商务、电子政务等在线服务的普及,衍生出大量的合同签署业务。由于在互联网环境中,业务双方往往没有物理联系,双方互不信任,这给合同签署的公平交换带来巨大挑战。并且在开放的互联网环境中,合同签署不仅要满足认证功能,在一些应用中需要同时保证数据传输的机密性。文章提出的基于签密实现的公平交换方案,采用区块链技术代替传统方案中的可信第三方来实现方案的公平性,同时可以保证数据的机密性和认证功能。
中图分类号:
引用本文
周由胜, 钟天琦. 基于区块链的公平交换方案[J]. 信息网络安全, 2021, 21(5): 19-30.
ZHOU Yousheng, ZHONG Tianqi. Blockchain-based Fair Exchange Scheme[J]. Netinfo Security, 2021, 21(5): 19-30.
| [1] | ASOKAN N. Fairness in Electronic Commerce[D]. Waterloo: University of Waterloo, 1998. |
| [2] |
EVEN S, GOLDREICH O, LEMPEL A. A Randomized Protocol for Signing Contracts[J]. Communications of the ACM, 1985,28(6):637-647.
doi: 10.1145/3812.3818 URL |
| [3] | OKAMOTO T, OHTA K. How to Simultaneously Exchange Secrets by General Assumptions[C]// ACM. 2nd ACM Conference on Computer & Communications Security. November 2-4, 1994, Fairfax, Virginia, USA. New York: ACM, 1994: 184-192. |
| [4] | BLUM M. How to Exchange(secret) Keys[J]. ACM Transactions on Computer Systems(Tocs), 1983,1(2):175-193. |
| [5] |
BEN-OR M, GOLDREICH O, MICALI S, et al. A Fair Protocol for Signing Contracts[J]. IEEE Transactions on Information Theory, 1990,36(1):40-46.
doi: 10.1109/18.50372 URL |
| [6] |
RABIN M O. Transaction Protection by Beacons[J]. Journal of Computer and System Sciences, 1983,27(2):256-267.
doi: 10.1016/0022-0000(83)90042-9 URL |
| [7] | BAHREMAN A, TYGAR J D. Certified Electronic Mail[EB/OL]. https://people.eecs.berkeley.edu/~tygar/papers/Certified_Electronic_Mail/Certified_electronic_mail.pdf, 2012-01-02. |
| [8] |
DENG R H, GONG L, LAZAR A A, et al. Practical Protocols for Certified Electronic Mail[J]. Journal of Network and Systems Management, 1996,4(3):279-297.
doi: 10.1007/BF02139147 URL |
| [9] | ZHOU J, GOLLMAN D. A Fair Non-repudiation Protocol[C]// IEEE. 1996 IEEE Symposium on Security and Privacy, May 6-8 1996, Oakland, CA, USA. New York: IEEE, 1996: 55-61. |
| [10] | ASOKAN N, SHOUP V, WAIDNER M. Asynchronous Protocols for Optimistic Fair Exchange[C]// IEEE. 1998 IEEE Symposium on Security and Privacy, May 6, 1998, Oakland, CA, USA. New York: IEEE, 1998: 86-99. |
| [11] | DODIS Y, REYZIN L. Breaking and Repairing Optimistic Fair Exchange from PODC 2003[C]// ACM. 10th ACM Conference on Computer and Communications Security. October 27, 2003. Washington, DC, USA. New York: ACM, 2003: 47-54. |
| [12] | PARK J M, CHONG E K P, SIEGEL H J. Constructing Fair-exchange Protocols for E-commerce via Distributed Computation of RSA Signatures[C]// ACM. Twenty-Second Annual ACM Symposium on Principles of Distributed Computing, July 13-16, 2003, Boston, Massachusetts, USA. New York: ACM, 2003: 172-181. |
| [13] | CHEN L, KUDLA C, PATERSON K G. Concurrent Signatures[C]// Springer. International Conference on the Theory and Applications of Cryptographic Techniques, May 2-6, 2004, Interlaken, Switzerland. Berlin: Springer, 2004: 287-305. |
| [14] | LUO Ming, ZOU Chunhua, HU Jun, et al. Signcryption-based Fair Exchange Protocol[J]. Journal on Communications, 2010,31(S1):87-93. |
| 罗铭, 邹春华, 胡军, 等. 基于签密的公平交易协议[J]. 通信学报, 2010,31(S1):87-93. | |
| [15] | EVEN S, YACOBI Y. Relations among Public Key Signature Systems[R]. Computer Science Department, Technion. No. CS Technion report CS0175, 1980. |
| [16] |
ZHANG Yinghui, DENG R H, LIU Ximeng, et al. Blockchain Based Efficient and Robust Fair Payment for Outsourcing Services in Cloud Computing[J]. Information Sciences, 2018,462(9):262-277.
doi: 10.1016/j.ins.2018.06.018 URL |
| [17] | HUANG Hui, LI Kuan-ching, CHEN Xiaofeng. Blockchain-based Fair Three-party Contract Signing Protocol for Fog Computing[EB/OL]. https://www.researchgate.net/publication/324577631_Blockchain-based_fair_three-party_contract_signing_protocol_for_fog_computing, 2021-01-02. |
| [18] | CAMPANELLI M, GENNARO R, GOLDFEDER S, et al. Zero-knowledge Contingent Payments Revisited: Attacks and Payments for Services[C]// ACM. 2017 ACM SIGSAC Conference on Computer and Communications Security, October 30-November 3, 2017, Dallas, Texas, USA. New York: ACM, 2017: 229-243. |
| [19] | LIU Jian, LI Wenting, KARAME G O, et al. Toward Fairness of Cryptocurrency Payments[J]. IEEE Security & Privacy, 2018,16(3):81-89. |
| [20] | TIAN Haibo, HE Jiejie, FU Liqing. A Privacy Preserving Fair Contract Signing Protocol Based on Public Blcokchains[J]. Journal of Cryptologic Research, 2017,4(2):187-198. |
| 田海博, 何杰杰, 付利青. 基于公开区块链的隐私保护公平合同签署协议[J]. 密码学报, 2017,4(2):187-198. | |
| [21] |
ZHANG Liang, ZHANG Hanlin, YU Jia, et al. Blockchain-based Two-party Fair Contract Signing Scheme[J]. Information Sciences, 2020,535(10):142-155.
doi: 10.1016/j.ins.2020.05.054 URL |
| [22] | NAKAMOTO S, BITCOIN A. A Peer-to-peer Electronic Cash System[EB/OL]. https://bitcoin.org/bitcoin.pdf, 2021-01-02. |
| [23] | ZHENG Yuliang. Digital Signcryption or How to Achieve Cost(Signature & Encryption)《 Cost(Signature)+ Cost(Encryption)[C]// Springer. 17th Annual International Cryptology Conference, August 17-21, 1997, Santa Barbara, California, USA. Berlin: Springer, 1997: 165-179. |
| [24] | ANTONOPOULOS A M. Mastering Bitcoin: Programming the Open Blockchain[M]. Sebastopol CA: O'Reilly Media, Inc. , 2017. |
| [25] |
SCHNORR C P. Efficient Signature Generation by Smart Cards[J]. Journal of Cryptology, 1991,4(3):161-174.
doi: 10.1007/BF00196725 URL |
| [26] | FRANKLIN M K, REITER M K. Verifiable Signature Sharing[C]// Springer. International Conference on the Theory and Applications of Cryptographic Techniques, May 21-25, 1995, Saint-Malo, France. Berlin: Springer, 1995: 50-63. |
| [27] | CARO D A, IOVINO V. jPBC: Java Pairing Based Cryptography[C]// IEEE. 2011 IEEE Symposium on Computers and Communications(ISCC), June 28-July 1, 2011, Kerkyra, Greece. New York: IEEE, 2011: 850-855. |
| [1] | 李鹏, 郑田甜, 徐鹤, 朱枫. 基于区块链技术的RFID安全认证协议[J]. 信息网络安全, 2021, 21(5): 1-11. |
| [2] | 刘子昂, 黄缘缘, 马佳利, 周睿. 基于区块链的医疗数据滥用监控平台设计与实现[J]. 信息网络安全, 2021, 21(5): 58-66. |
| [3] | 芦效峰, 付淞兵. 属性基加密和区块链结合的可信数据访问控制方案[J]. 信息网络安全, 2021, 21(3): 7-8. |
| [4] | 张应辉, 朱甜, 郑东. 基于区块链的多关键字细粒度可搜索加密方案[J]. 信息网络安全, 2021, 21(2): 34-44. |
| [5] | 储志强, 仵冀颖, 徐磊, 杜聪. 基于区块链的分布式离链存储框架设计[J]. 信息网络安全, 2021, 21(2): 87-93. |
| [6] | 刘峰, 杨杰, 齐佳音. 基于哈希证明系统的区块链两方椭圆曲线数字签名算法研究[J]. 信息网络安全, 2021, 21(1): 19-26. |
| [7] | 韩磊, 陈武平, 曾志强, 曾颖明. 区块链层级网络结构与应用研究[J]. 信息网络安全, 2020, 20(9): 112-116. |
| [8] | 汪金苗, 谢永恒, 王国威, 李易庭. 基于属性基加密的区块链隐私保护与访问控制方法[J]. 信息网络安全, 2020, 20(9): 47-51. |
| [9] | 石润华, 石泽. 基于区块链技术的物联网密钥管理方案[J]. 信息网络安全, 2020, 20(8): 1-8. |
| [10] | 李莉, 曾庆贤, 文义红, 王士成. 基于区块链与代理重加密的数据共享方案[J]. 信息网络安全, 2020, 20(8): 16-24. |
| [11] | 边玲玉, 张琳琳, 赵楷, 石飞. 基于LightGBM的以太坊恶意账户检测方法[J]. 信息网络安全, 2020, 20(4): 73-80. |
| [12] | 毛志来, 刘亚楠, 孙惠平, 陈钟. 区块链性能扩展与安全研究[J]. 信息网络安全, 2020, 20(3): 56-64. |
| [13] | 郎为民, 张汉, 赵毅丰, 姚晋芳. 一种基于区块链的物联网行为监控和活动管理方案[J]. 信息网络安全, 2020, 20(2): 22-29. |
| [14] | 姚萌萌, 唐黎, 凌永兴, 肖卫东. 基于串空间的安全协议形式化分析研究[J]. 信息网络安全, 2020, 20(2): 30-36. |
| [15] | 姜楠, 王玮琦, 王健. 基于智能合约的个人隐私数据保护方法研究[J]. 信息网络安全, 2020, 20(11): 22-31. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||