信息网络安全 ›› 2021, Vol. 21 ›› Issue (5): 1-11.doi: 10.3969/j.issn.1671-1122.2021.05.001
基于区块链技术的RFID安全认证协议
- 1.南京邮电大学计算机学院,南京 210023
2.江苏省无线传感网络高技术研究重点实验室,南京 210023
-
收稿日期:2020-12-19出版日期:2021-05-10发布日期:2021-06-22 -
通讯作者:李鹏 E-mail:lipeng@njupt.edu.cn -
作者简介:李鹏(1979—),男,福建,教授,博士,主要研究方向为网络安全、隐私保护|郑田甜(1997—),女,安徽,硕士研究生,主要研究方向为物联网安全|徐鹤(1985—),男,安徽,副教授,博士,主要研究方向为物联网技术、信息安全|朱枫(1986—),男,江苏,讲师,博士,主要研究方向为系统安全 -
基金资助:国家自然科学基金(61872196);国家自然科学基金(61872194);国家自然科学基金(61902196);江苏省科技支撑计划(BE2017166);江苏省科技支撑计划(BE2019740);江苏省高等学校自然科学研究(18KJA520008);江苏省高等学校自然科学研究(20KJB520001);江苏省六大人才高峰高层次人才计划(RJFW-111)
RFID Security Authentication Protocol Based on Blockchain Technology
LI Peng1,2( ), ZHENG Tiantian1, XU He1,2, ZHU Feng1,2
), ZHENG Tiantian1, XU He1,2, ZHU Feng1,2
- 1. School of Computer Science, Nanjing University of Posts and Telecommunications, Nanjing 210023, China
2. Jiangsu High Technology Research Key Laboratory for Wireless Sensor Networks, Nanjing 210023, China
-
Received:2020-12-19Online:2021-05-10Published:2021-06-22 -
Contact:LI Peng E-mail:lipeng@njupt.edu.cn
摘要:
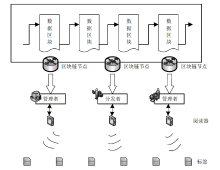
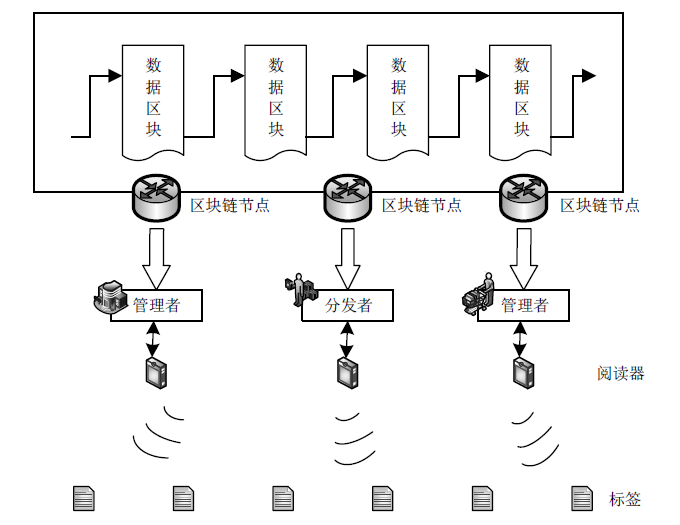
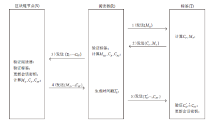
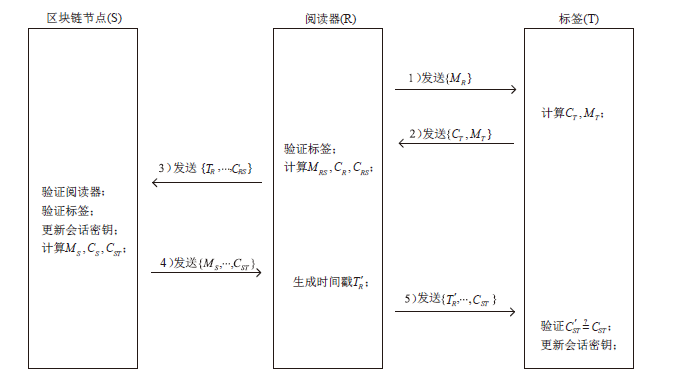
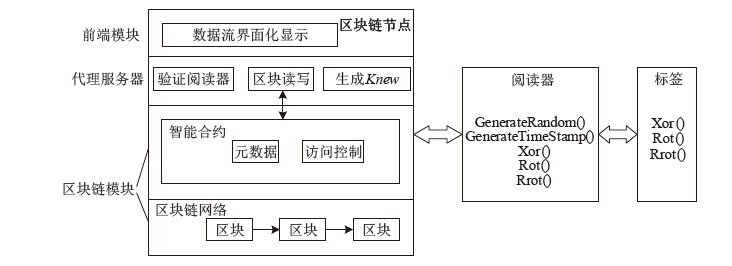
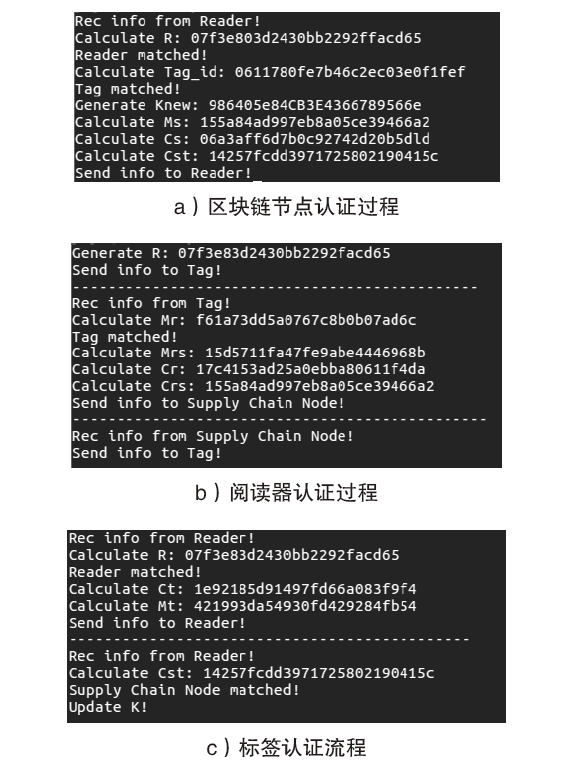
传统RFID应用领域中的安全认证协议主要基于中心化数据库,而基于中心化数据库的RFID安全认证协议存在数据丢失、篡改等问题。区块链作为一种分布式技术具备去中心化特性以及更高的可靠性、透明度等特性,可有效解决传统RFID安全认证协议中心服务器可能导致的数据安全问题。将区块链与RFID相结合,文章提出一个基于区块链技术的RFID安全认证协议,使用异或、位旋转等操作对数据进行加密,将验证计算转移至阅读器和区块链节点中,有效降低标签的计算成本;在协议中加入对恶意阅读器的判别,减少无效计算成本。此外,文章通过智能合约、truffle模拟协议数据交换过程验证该协议的可行性,并通过理论分析和GNY证明协议的安全性。在低成本的前提下,文章协议能够有效防止窃听、重放、去中心化等多种攻击。
中图分类号:
引用本文
李鹏, 郑田甜, 徐鹤, 朱枫. 基于区块链技术的RFID安全认证协议[J]. 信息网络安全, 2021, 21(5): 1-11.
LI Peng, ZHENG Tiantian, XU He, ZHU Feng. RFID Security Authentication Protocol Based on Blockchain Technology[J]. Netinfo Security, 2021, 21(5): 1-11.
表1
协议符号说明
| 符号 | 说明 |
|---|---|
| $I{{D}_{T}},I{{D}_{R}},I{{D}_{S}}$ | 标签、阅读器、区块链节点的唯一标识 |
| $R,{{R}_{S}}$ | 阅读器、区块链节点生成的随机数 |
| $K,{{K}_{new}}$ | 标签和区块链节点之间的会话密钥、更新后的会话密钥 |
| ${{T}_{R}}$ | 阅读器发送给区块链节点的时间戳 |
| $T{{'}_{R}}$ | 阅读器发送给标签的时间戳 |
| $\Delta T,\Delta N$ | 时间戳阈值、失败通信阈值 |
| ${{N}_{I{{D}_{R}}}}$ | $I{{D}_{R}}$对应失败通信次数 |
| ${{H}_{RS}}$ | ${{H}_{RS}}=h(I{{D}_{S}}||I{{D}_{R}})$ |
| $Rot(X,{{Y}_{HM}})$ | X向左旋转汉明权重Y |
| $RRot(X,{{Y}_{HM}})$ | X向右旋转汉明权重Y |
| $h(\cdot )$ | 哈希函数 |
| $\oplus $ | 异或 |
| $\parallel $ | 或 |
表2
协议性能对比
| 协议 | 计算成本 | 通信成本/bit | 窃听 攻击 | 重放 攻击 | 中间人攻击 | 去同步攻击 | 追踪 攻击 | 支持 区块链 | 恶意 阅读器 |
|---|---|---|---|---|---|---|---|---|---|
| 文献[ 协议 | (n+k+2)Txor+ (n+k+6)Thash | 1440 | √ | √ | √ | √ | × | × | × |
| 文献[ 协议 | 29Trot+29Txor+ 1Thm | 960 | × | √ | × | × | √ | × | × |
| 文献[ 协议 | 15Trot+25Txor+ 12Thash | 2240 | √ | √ | √ | √ | √ | √ | × |
| 文献[ 协议 | 11Trot+11Txor+ 15Thm | 1760 | × | √ | × | √ | √ | √ | × |
| 本文协议 | 10Trot+9Txor+ 11Thm | 2144 | √ | √ | √ | √ | √ | √ | √ |
| [1] |
SUN Hong, SU Cheng, CHEN Shiping. A High Security RFID System Authentication Protocol Design Based on Cloud Computer[J]. Wireless Personal Communications, 2018,102(2):1255-1267.
doi: 10.1007/s11277-017-5192-1 URL |
| [2] |
CHIEN Hungyu, HUANG Chenwei. A Lightweight Authentication Protocol for Low-cost RFID[J]. Journal of Signal Processing Systems, 2010,59(1):95-102.
doi: 10.1007/s11265-008-0281-8 URL |
| [3] |
ZENG Shiqin, HUO Ru, HUANG Tao, et al. Survey of Blockchain: Principle, Progress and Application[J]. Journal on Communications, 2020,41(1):134-151.
doi: 10.1111/j.1460-2466.1991.tb02297.x URL |
| 曾诗钦, 霍如, 黄韬, 等. 区块链技术研究综述:原理、进展与应用[J]. 通信学报, 2020,41(1):134-151. | |
| [4] |
HE Debiao, KUMAR N, CHILAMKURTI N, et al. Lightweight ECC Based RFID Authentication Integrated with an ID Verifier Transfer Protocol[J]. Journal of Medical Systems, 2014,38(10):1-6.
doi: 10.1007/s10916-013-0001-1 URL |
| [5] | LEE Chini, CHIEN Hungyu. An Elliptic Curve Cryptography-based RFID Authentication Securing E-health System[J]. International Journal of Distributed Sensor Networks, 2015,12(11):1-7. |
| [6] |
FAN Kai, GONG Yuanyuan, LIANG Chen, et al. Lightweight and Ultralightweight RFID Mutual Authentication Protocol with Cache in the Reader for IoT in 5G[J]. Security and Communication Networks, 2016,9(16):3095-3104.
doi: 10.1002/sec.v9.16 URL |
| [7] |
LI Nan, SUSILO W, VARADHARAJAN V, et al. Vulnerabilities of An ECC-based RFID Authentication Scheme[J]. Security and Communication Networks, 2015,8(17):3262-3270.
doi: 10.1002/sec.1250 URL |
| [8] | HA J, KIM H, PARK J, et al. HGLAP-hierarchical Group-index Based Lightweight Authentication Protocol for Distributed RFID System[EB/OL]. https://xueshu.baidu.com/usercenter/paper/show?paperid=1x240gd0hy6c0pw0dj7700r0aq265758&site=xueshu_se, 2020-12-06. |
| [9] | RHEE K, KWAK J, KIM S, et al. Challenge-response Based RFID Authentication Protocol for Distributed Database Environment[C]// Springer. International Conference on Security in Pervasive Computing, July 13-15, 2005, Boppard. Berlin: Springer, 2005: 70-84. |
| [10] | MUJAHID U, ISLAM M, SARWAR S. A New Ultralightweight RFID Authentication Protocol for Passive Low Cost Tags: KMAP[J]. Wireless Personal Communications, 2017,3(9):725-744. |
| [11] | TOYODA K, MATHIOPOULOS Pt, SASASE I, et al. A Novel Blockchain-based Product Ownership Management System (POMS) for Anti-counterfeits in the Post Supply Chain[J]. IEEE Access, 2017,17(5):17465-17477. |
| [12] | ZHANG Xiaohan. Research on Identity Authentication Protocol of Internet of Things Equipment Based on Blockchain[D]. Hefei: University of Science and Technology of China, 2019. |
| 张霄涵. 基于区块链的物联网设备身份认证协议研究[D]. 合肥:中国科学技术大学, 2019. | |
| [13] | SIDOROV M, ONG M, SRIDHARAN R, et al. Ultralightweight Mutual Authentication RFID Protocol for Blockchain Enabled Supply Chains[J]. IEEE Access, 2019,19(7):7273-7285. |
| [14] |
JANGIRALA S, DAS A, VASILAKOS A. Designing Secure Lightweight Blockchain-enabled RFID-based Authentication Protocol for Supply Chains in 5G Mobile Edge Computing Environment[J]. IEEE Transactions on Industrial Informatics, 2019,16(11):7081-7093.
doi: 10.1109/TII.9424 URL |
| [15] |
PREMNATH S, HAAS Z. Security and Privacy in the Internet-of-things Under Time-and-budget-limited Adversary Model[J]. IEEE Wireless Communications Letters, 2015,4(3):277-280.
doi: 10.1109/LWC.2015.2408609 URL |
| [16] | FERNÁNDEZ C, FRAGA L P. Reverse Engineering the Communications Protocol of an RFID Public Transportation Card[C]// IEEE. 2017 IEEE International Conference on RFID, May 9-11, 2017, Phoenix, AZ, USA. New York: IEEE, 2017: 30-35. |
| [17] | ZHAO Guogang, YU Haiye, WANG Guowei, et al. Applied Research of IOT and RFID Technology in Agricultural Product Traceability System[C]// Springer. International Conference on Computer and Computing Technologies in Agriculture, October 23-25, 2015, Cham. New York: Springer, 2015: 506-514. |
| [18] |
GOPE P, LEE J, QUEK T. Lightweight and Practical Anonymous Authentication Protocol for RFID Systems Using Physically Unclonable Functions[J]. IEEE Transactions on Information Forensics and Security, 2018,13(11):2831-2843.
doi: 10.1109/TIFS.2018.2832849 URL |
| [19] | WANG Siye, ZHU Shaoyi, ZHANG Yangfang. Blockchain-based Mutual Authentication Security Protocol for Distributed RFID Systems[C]// IEEE. 2018 IEEE Symposium on Computers and Communications (ISCC), June 25-28, 2018, Natal, Brazil. New York: IEEE, 2018: 74-77. |
| [20] |
LU Yang. The Blockchain: State-of-the-art and Research Challenges[J]. Journal of Industrial Information Integration, 2019,15(2):80-90.
doi: 10.1016/j.jii.2019.04.002 URL |
| [21] | ZHENG Zibin, XIE Shaoan, DAI Hongning, et al. An Overview of Blockchain Technology: Architecture, Consensus, and Future Trends[J]. IEEE International Congress on Big Data, 2017,27(1):557-564. |
| [22] |
BURROWS M, ABADI M, NEEDHAM R. A Logic of Authentication[J]. ACM SIGOPS Operating Systems Review, 1989,23(5):1-13.
doi: 10.1145/74851.74852 URL |
| [23] | ABADI M, TUTTLE M. A Semantics for a Logic of Authentication[C]// Association for Computing Machinery. Proceedings of the Tenth Annual ACM Symposium on Principles of Distributed Computing, August 21-24, 1991, Montreal, Quebec, Canada. New York: ACM, 1991: 201-216. |
| [24] | GONG L, NEEDHAM R, YAHALOM R. Reasoning about Belief in Cryptographic Protocols[C]//IEEE Computer Society Press. the 1990 IEEE Computer Society Symposium on Research in Security and Privacy, May 7-9, 1990, Los Alamitos, California. New York: IEEE Computer Society Press, 1990: 234-248. |
| [1] | 周由胜, 钟天琦. 基于区块链的公平交换方案[J]. 信息网络安全, 2021, 21(5): 19-30. |
| [2] | 刘子昂, 黄缘缘, 马佳利, 周睿. 基于区块链的医疗数据滥用监控平台设计与实现[J]. 信息网络安全, 2021, 21(5): 58-66. |
| [3] | 王开轩, 滕亚均, 王琼霄, 王伟. 隐式证书的国密算法应用研究[J]. 信息网络安全, 2021, 21(5): 74-81. |
| [4] | 张昱, 孙光民, 李煜. 基于SM9算法的移动互联网身份认证方案研究[J]. 信息网络安全, 2021, 21(4): 1-9. |
| [5] | 王健, 赵曼莉, 陈志浩, 石波. 基于假名的智能交通条件隐私保护认证协议[J]. 信息网络安全, 2021, 21(4): 49-61. |
| [6] | 芦效峰, 付淞兵. 属性基加密和区块链结合的可信数据访问控制方案[J]. 信息网络安全, 2021, 21(3): 7-8. |
| [7] | 张应辉, 朱甜, 郑东. 基于区块链的多关键字细粒度可搜索加密方案[J]. 信息网络安全, 2021, 21(2): 34-44. |
| [8] | 储志强, 仵冀颖, 徐磊, 杜聪. 基于区块链的分布式离链存储框架设计[J]. 信息网络安全, 2021, 21(2): 87-93. |
| [9] | 刘峰, 杨杰, 齐佳音. 基于哈希证明系统的区块链两方椭圆曲线数字签名算法研究[J]. 信息网络安全, 2021, 21(1): 19-26. |
| [10] | 董锵, 罗国明, 史宏逵, 张永跃. 基于IMS的移动通信专网认证和密钥协商方法研究[J]. 信息网络安全, 2021, 21(1): 88-96. |
| [11] | 沈金伟, 赵一, 梁春林, 张萍. 基于循环分组的RFID群组标签所有权转移协议[J]. 信息网络安全, 2020, 20(9): 102-106. |
| [12] | 韩磊, 陈武平, 曾志强, 曾颖明. 区块链层级网络结构与应用研究[J]. 信息网络安全, 2020, 20(9): 112-116. |
| [13] | 汪金苗, 谢永恒, 王国威, 李易庭. 基于属性基加密的区块链隐私保护与访问控制方法[J]. 信息网络安全, 2020, 20(9): 47-51. |
| [14] | 余果, 王冲华, 陈雪鸿, 李俊. 认证视角下的工业互联网标识解析安全[J]. 信息网络安全, 2020, 20(9): 77-81. |
| [15] | 石润华, 石泽. 基于区块链技术的物联网密钥管理方案[J]. 信息网络安全, 2020, 20(8): 1-8. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||