信息网络安全 ›› 2021, Vol. 21 ›› Issue (3): 7-8.doi: 10.3969/j.issn.1671-1122.2021.03.002
属性基加密和区块链结合的可信数据访问控制方案
- 北京邮电大学网络空间安全学院,北京 100876
-
收稿日期:2021-01-06出版日期:2021-03-10发布日期:2021-03-16 -
通讯作者:芦效峰 E-mail:luxf@bupt.edu.cn -
作者简介:芦效峰(1976—),男,山西,副教授,博士,主要研究方向为人工智能、物联网安全、区块链|付淞兵(1996—),男,江西,硕士研究生,主要研究方向为区块链、隐私保护 -
基金资助:国家自然科学基金(61472046)
A Trusted Data Access Control Scheme Combining Attribute-based Encryption and Blockchain
- School of Cyberspace Security, Beijing University of Posts and Telecommunications, Beijing 100876, China
-
Received:2021-01-06Online:2021-03-10Published:2021-03-16 -
Contact:LU Xiaofeng E-mail:luxf@bupt.edu.cn
摘要:
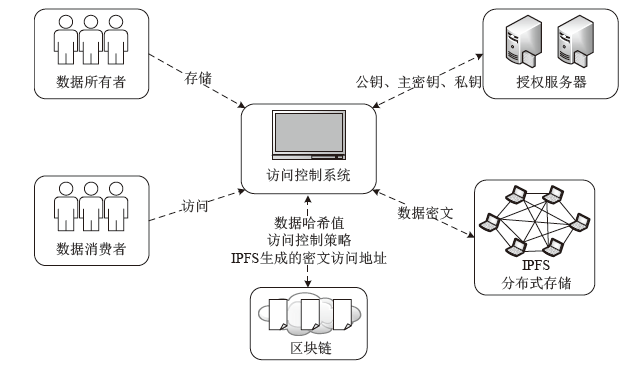
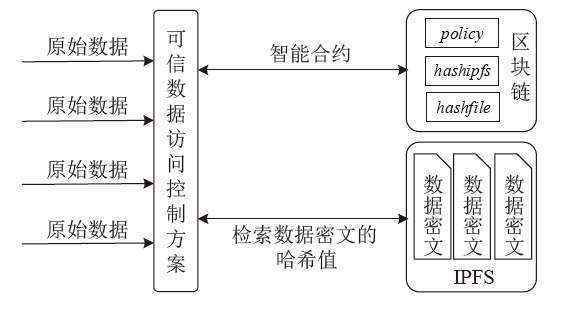
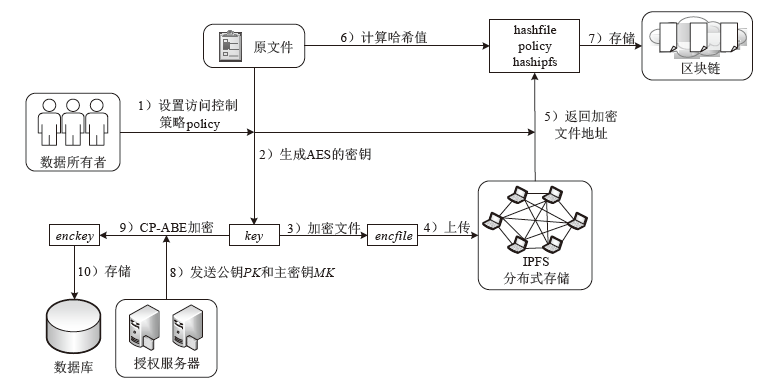
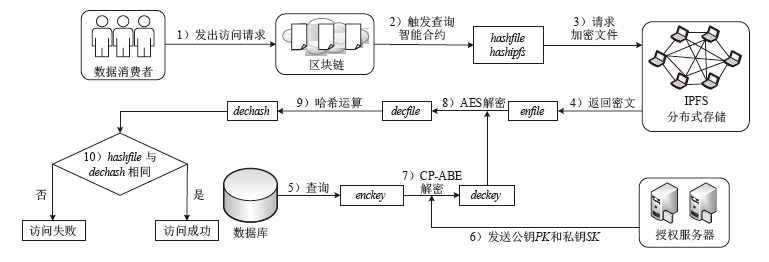
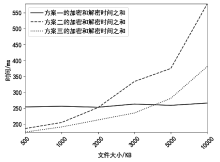
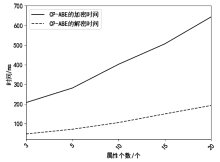
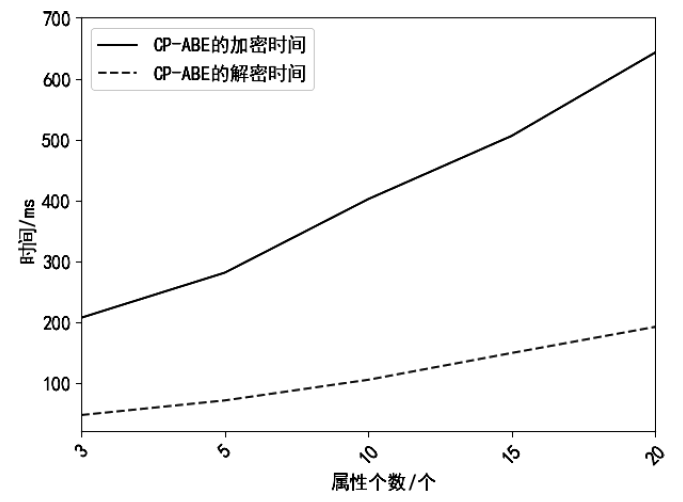
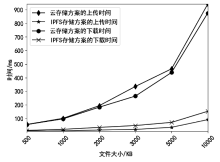
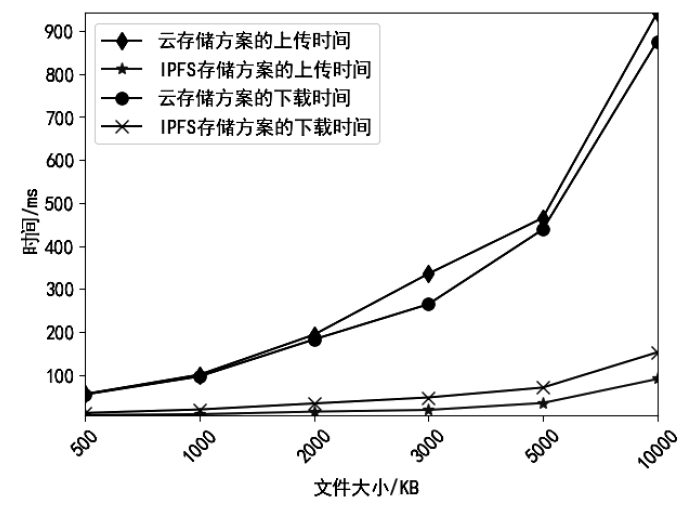
传统的数据存储方式往往采用集中式架构,这种集中式存储架构容易产生信任和安全问题。文章提出一种属性基加密和区块链结合的可信数据访问控制方案,将对称加密算法和属性基加密算法结合,实现了数据所有者对数据的细粒度访问控制,保障了数据所有者的隐私保护权利。同时,文章将区块链技术和分布式存储相结合,区块链上仅存储数据及密文位置的哈希值和访问控制策略等信息,解决了区块链系统的存储瓶颈。实验表明,该方案能有效保护数据所有者的安全和隐私,实现数据的安全共享。
中图分类号:
引用本文
芦效峰, 付淞兵. 属性基加密和区块链结合的可信数据访问控制方案[J]. 信息网络安全, 2021, 21(3): 7-8.
LU Xiaofeng, FU Songbing. A Trusted Data Access Control Scheme Combining Attribute-based Encryption and Blockchain[J]. Netinfo Security, 2021, 21(3): 7-8.
| [1] | WANG Zuan, TIAN Youliang, ZHU Jianming. Data Sharing and Tracing Scheme Based on Blockchain [C]//IEEE. 2018 8th International Conference on Logistics, Informatics and Service Sciences (LISS), August 3-6, 2018, Toronto, ON, Canada. New York: IEEE, 2018: 1-6. |
| [2] | LIU Fangfei, GE Qian, YAROM Y, et al. Catalyst: Defeating Last-level Cache Side Channel Attacks in Cloud Computing [C]//IEEE. IEEE International Symposium on High Performance Computer Architecture (HPCA), April 4, 2016, Barcelona spain. New York: IEEE, 2016: 406-418. |
| [3] | SHAO Qifeng, JIN Cheqing, ZHANG Zhao, et al. Blockchain Technology: Architecture and Progress[J]. Journal of Computing, 2018,41(5):969-988. |
| 邵奇峰, 金澈清, 张召, 等. 区块链技术:架构及进展[J]. 计算机学报, 2018,41(5):969-988. | |
| [4] | GE Chunpeng, LIU Zhe, FANG Liming. A Blockchain Based Decentralized Data Security Mechanism for the Internet of Things[J]. Journal of Parallel and Distributed Computing, 2020,141(5):1-9. |
| [5] | ZHANG Guochao, WANG Ruijin. Blockchain Sharding Storage Model Based on Threshold Secret Sharing[J]. Computer Applications, 2019,39(9):2617-2622. |
| 张国潮, 王瑞锦. 基于门限秘密共享的区块链分片存储模型[J]. 计算机应用, 2019,39(9):2617-2622. | |
| [6] | SAHAI A, WATERS B. Fuzzy Identity-based Encryption [C]//Springer-Verlag. Proceedings of the 24th annual international conference on Theory and Applications of Cryptographic Techniques, May 22-26, 2005, Aarhus, Denmark. Berlin: Springer-Verlag, 2005: 457-473. |
| [7] | LI Hongyu, ZHU Liehuang, Shen Meng, et al. Blockchain-based Data Preservation System for Medical Data[EB/OL]. https://www.onacademic.com/detail/journal_1000040406193710_05ee.html, 2020-10-08. |
| [8] | NOVO O. Blockchain Meets IoT: An Architecture for Scalable Access Management in IoT[J]. IEEE Internet of Things Journal, 2018,5(2):1184-1195. |
| [9] | LI Dongxi, PENG Wei, DENG Wenping, et al. A Blockchain-based Authentication and Security Mechanism for IoT [C]//IEEE. 2018 27th International Conference on Computer Communication and Networks (ICCCN), July 30-August 2, 2018, Hangzhou, China. New York: IEEE, 2018: 1-6. |
| [10] | DING Sheng, CAO Jin, LI Chen, et al. A Novel Attribute-Based Access Control Scheme Using Blockchain for IoT[EB/OL]. https://xueshu.baidu.com/usercenter/paper/show?paperid=141f04x0se6y00u0tu2u0ph03p650563&site=xueshu_se, 2020-10-18. |
| [11] | JEMEL M, SERHROUCHNI A. Decentralized Access Control Mechanism with Temporal Dimension Based on Blockchain [C]//IEEE. Proceedings of the IEEE 14th International Conference on E-business Engineering, November 4-6, 2017, Shanghai, China. New York: IEEE, 2017: 177-182. |
| [12] | DAI Mingjun, ZHANG Shengli, WANG Hui, et al.A Low Storage Room Requirement Framework for Distributed Ledger in Blockchain[EB/OL].https://xueshu.baidu.com/usercenter/paper/show?paperid=6c168128a081cd96512b5eff4b30a3a5&site=xueshu_se, 2020-10-22. |
| [13] | CHENG Guanjie, HUANG Zhengjie, DENG Shuiguang. Internet of Things Data Management Based on Block Chain and Edge Computing[J]. Journal of Internet of Things, 2020,4(2):1-9. |
| 程冠杰, 黄诤杰, 邓水光. 基于区块链与边缘计算的物联网数据管理[J]. 物联网学报, 2020,4(2):1-9. | |
| [14] | CONFAIS B, LEBRE A, PARREIN B. An Object Store Service for a Fog/Edge Computing Infrastructure Based on IPFS and A Scale-out NAS [C]//IEEE. 2017 IEEE 1st International Conference on Fog and Edge Computing (ICFEC), May 14-15, 2017, Madrid. New York: IEEE, 2017: 41-50. |
| [15] | BETHENCOURT J, SAHAI A, WATERS B. Ciphertext-policy Attribute-based Encryption [C]//IEEE. 2007 IEEE Symposium on Security and Privacy, May 20, 2007, Berkeley, USA. New York: IEEE, 2007: 321-334. |
| [1] | 张应辉, 朱甜, 郑东. 基于区块链的多关键字细粒度可搜索加密方案[J]. 信息网络安全, 2021, 21(2): 34-44. |
| [2] | 储志强, 仵冀颖, 徐磊, 杜聪. 基于区块链的分布式离链存储框架设计[J]. 信息网络安全, 2021, 21(2): 87-93. |
| [3] | 刘峰, 杨杰, 齐佳音. 基于哈希证明系统的区块链两方椭圆曲线数字签名算法研究[J]. 信息网络安全, 2021, 21(1): 19-26. |
| [4] | 韩磊, 陈武平, 曾志强, 曾颖明. 区块链层级网络结构与应用研究[J]. 信息网络安全, 2020, 20(9): 112-116. |
| [5] | 汪金苗, 谢永恒, 王国威, 李易庭. 基于属性基加密的区块链隐私保护与访问控制方法[J]. 信息网络安全, 2020, 20(9): 47-51. |
| [6] | 石润华, 石泽. 基于区块链技术的物联网密钥管理方案[J]. 信息网络安全, 2020, 20(8): 1-8. |
| [7] | 李莉, 曾庆贤, 文义红, 王士成. 基于区块链与代理重加密的数据共享方案[J]. 信息网络安全, 2020, 20(8): 16-24. |
| [8] | 吴云坤, 姜博, 潘瑞萱, 刘玉岭. 一种基于零信任的SDN网络访问控制方法[J]. 信息网络安全, 2020, 20(8): 37-46. |
| [9] | 施国峰, 张兴兰. 面向云存储的支持范围密文搜索的属性基加密方案[J]. 信息网络安全, 2020, 20(6): 75-81. |
| [10] | 杜义峰, 郭渊博. 一种基于信任值的雾计算动态访问控制方法[J]. 信息网络安全, 2020, 20(4): 65-72. |
| [11] | 边玲玉, 张琳琳, 赵楷, 石飞. 基于LightGBM的以太坊恶意账户检测方法[J]. 信息网络安全, 2020, 20(4): 73-80. |
| [12] | 毛志来, 刘亚楠, 孙惠平, 陈钟. 区块链性能扩展与安全研究[J]. 信息网络安全, 2020, 20(3): 56-64. |
| [13] | 刘鹏, 何倩, 刘汪洋, 程序. 支持撤销属性和外包解密的CP-ABE方案[J]. 信息网络安全, 2020, 20(3): 90-97. |
| [14] | 郎为民, 张汉, 赵毅丰, 姚晋芳. 一种基于区块链的物联网行为监控和活动管理方案[J]. 信息网络安全, 2020, 20(2): 22-29. |
| [15] | 姚萌萌, 唐黎, 凌永兴, 肖卫东. 基于串空间的安全协议形式化分析研究[J]. 信息网络安全, 2020, 20(2): 30-36. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||