信息网络安全 ›› 2020, Vol. 20 ›› Issue (2): 91-97.doi: 10.3969/j.issn.1671-1122.2020.02.012
基于认证树的外包数据库连接查询验证方案
- 东北大学软件学院,沈阳110169
-
收稿日期:2019-10-23出版日期:2020-02-10发布日期:2020-05-11 -
作者简介:作者简介:侯林(1983—),男,黑龙江,工程师,硕士,主要研究方向为网络与信息安全;冯达(1993—),男,吉林,博士研究生,主要研究方向为信息安全;玄鹏开(1994—),男,河北,硕士,主要研究方向为信息安全;周福才(1964—),男,辽宁,教授,博士,主要研究方向为信息安全。
-
基金资助:国家自然科学基金[61872069];中央高校基本科研业务费项目[N130317002]
Outsourcing Database Join Query Verification Scheme Based on Authentication Tree
HOU Lin, FENG Da( ), XUAN Pengkai, ZHOU Fucai
), XUAN Pengkai, ZHOU Fucai
- Software College of Northeastern University, Shenyang 110169, China
-
Received:2019-10-23Online:2020-02-10Published:2020-05-11
摘要:
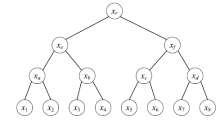
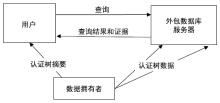
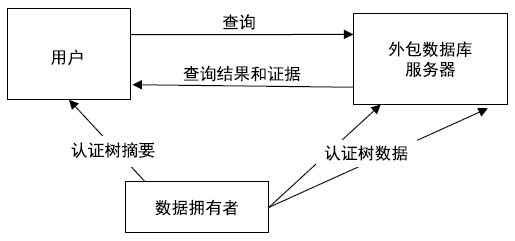
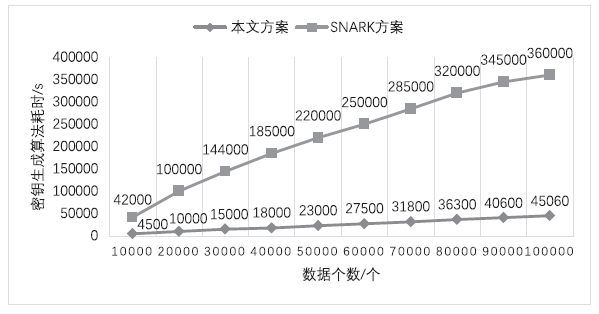
在外包数据库广泛应用的同时,其安全性受到了很大的挑战。用户在查询数据时无法保证查询结果的正确性和完整性。文章针对现有的外包数据库不能支持连接查询验证问题,提出一种基于认证树的外包数据库连接查询验证模型,并给出了模型的形式化定义以及模型的正确性和安全性定义。文章利用双线性映射累加器、认证树等技术构建了基于认证树的外包数据库连接查询验证方案,利用密码学的VBDHE和q-BSDH困难性假设给出了安全性分析;通过证明敌手不能通过伪造错误结果来使得验证通过,从而证明了方案的正确性。实验结果及性能分析表明,文章方案在密钥生成、查询验证、通信开销、存储开销等方面比其他方案有更高的效率。
中图分类号:
引用本文
侯林, 冯达, 玄鹏开, 周福才. 基于认证树的外包数据库连接查询验证方案[J]. 信息网络安全, 2020, 20(2): 91-97.
HOU Lin, FENG Da, XUAN Pengkai, ZHOU Fucai. Outsourcing Database Join Query Verification Scheme Based on Authentication Tree[J]. Netinfo Security, 2020, 20(2): 91-97.
| [1] | XIAN Hequn, FENG Dengguo.An Integrity Checking Scheme in Outsourced Database Model[J]. Journal of Computer Research and Development, 2010, 47(6): 1107-1115. |
| 咸鹤群,冯登国.外包数据库模型中的完整性检测方案[J]. 计算机研究与发展, 2010, 47(6):1107-1115. | |
| [2] | GUPTA R.Above the Clouds: A View of Cloud Computing[J]. Eecs Department University of California Berkeley, 2012, 53(4): 50-58. |
| [3] | RIVEST R L, SHAMIR A, ADLEMAN L.A Method for Obtaining Digital Signatures and Public-key Cryptosystems[J]. Communications of the ACM, 1978, 21(2): 120-126. |
| [4] | LI Feifei, HADJIELEFTHERIOU M, KOLLIOS G, et al.Dynamic Authenticated Index Structures for Outsourced Databases[C]//ACM. International Conference on Management of Data and Symposium on Principles Database and Systems, June 27-29, 2006, Chicago, IL, USA. New York: ACM, 2006: 121-132. |
| [5] | YANG Yin, PAPADOPOULOS S, PAPADIAS D, et al.Authenticated Indexing for Outsourced Spatial Databases[J]. The VLDB Journal, 2009, 18(3): 631-648. |
| [6] | YIU M L, LO E, YUNG D.Authentication of Moving kNN Queries[C]// IEEE. IEEE 27th International Conference on Data Engineering, April 11-16, 2011, Hannover, Germany. NJ: IEEE, 2011: 565-576. |
| [7] | LI Feifei, HADJIELEFTHERIOU M, KOLLIOS G, et al.Authenticated Index Structures for Aggregation Queries[J]. ACM Transactions on Information & System Security, 2010, 13(4): 1-35. |
| [8] | HU Haibo, XU Jianliang, CHEN Qian, et al.Authenticating Location-based Services without Compromising Location Privacy[C]//ACM. International Conference on Management of Data, May 20-25, 2012, Scottsdale Arizona, USA. New York: ACM, 2012: 301-312. |
| [9] | CHEN Qian, HU Haibo, XU Jianliang.Authenticating Top-k Queries in Location-based Services with Confidentiality[J]. Proceedings of the Vldb Endowment, 2014, 7(1): 49-60. |
| [10] | PAPADOPOULOS S, WANG Lixing, YANG Yin, et al.Authenticated Multistep Nearest Neighbor Search[J]. IEEE Transactions on Knowledge & Data Engineering, 2011, 23(5): 641-654. |
| [11] | HUANG Qingyuan, WANG Yongjun, SU Jinshu.A Bilinear Pairing-based Key Agreement Protocol in MANET[J]. Computer Science, 2008, 35(2): 78-80. |
| 黄清元,王勇军,苏金树.一种基于双线性配对的移动自组网密钥协商协议[J]. 计算机科学, 2008, 35(2):78-80. | |
| [12] | CHEN Anlin, PAN Jin, GUO Chao.Research on Authenticated Key Agreement Protocol in Cross-domain Two-party for Mobile Ad Hoc Network[J]. Application Research of Computers, 2011, 28(7): 2734-2737. |
| 陈安林,潘进,郭超.移动自组网中跨域两方认证密钥协商协议研究[J]. 计算机应用研究, 2011, 28(7):2734-2737. | |
| [13] | AU M H, TSANG P P, SUSILO W, et al.Dynamic Universal Accumulators for DDH Groups and Their Application to Attribute-based Anonymous Credential Systems[M]// Springer. Topics in Cryptology - CT-RSA 2009. Heidelberg: Springer-Verlag, 2009: 295-308. |
| [14] | NGUYEN L.Accumulators from Bilinear Pairings and Applications[M]// Springer. Topics in Cryptology - CT-RSA 2005. Heidelberg: Springer Berlin, 2005: 275-292. |
| [15] | BITANSKY N, CANETTI R, CHIESA A, et al. Recursive Composition and Bootstrapping for SNARKs and Proof-carrying Data[EB/OL]. , 2019-9-20. |
| [1] | 周枝凝, 王斌君, 翟一鸣, 仝鑫. 基于ALBERT动态词向量的垃圾邮件过滤模型[J]. 信息网络安全, 2020, 20(9): 107-111. |
| [2] | 沈金伟, 赵一, 梁春林, 张萍. 基于循环分组的RFID群组标签所有权转移协议[J]. 信息网络安全, 2020, 20(9): 102-106. |
| [3] | 夏天雨, 顾益军. 一种基于改进DynamicTriad模型的动态链路预测方法[J]. 信息网络安全, 2020, 20(9): 97-101. |
| [4] | 王湘懿, 张健. 基于图像和机器学习的虚拟化平台异常检测[J]. 信息网络安全, 2020, 20(9): 92-96. |
| [5] | 李世斌, 李婧, 唐刚, 李艺. 基于HMM的工业控制系统网络安全状态预测与风险评估方法[J]. 信息网络安全, 2020, 20(9): 57-61. |
| [6] | 徐瑜, 周游, 林璐, 张聪. 无监督机器学习在游戏反欺诈领域的应用研究[J]. 信息网络安全, 2020, 20(9): 32-36. |
| [7] | 毋泽南, 田立勤, 陈楠. 基于随机Petri网的系统安全性量化分析研究[J]. 信息网络安全, 2020, 20(9): 27-31. |
| [8] | 仝鑫, 王罗娜, 王润正, 王靖亚. 面向中文文本分类的词级对抗样本生成方法[J]. 信息网络安全, 2020, 20(9): 12-16. |
| [9] | 吴警, 芦天亮, 杜彦辉. 基于Char-RNN改进模型的恶意域名训练数据生成技术[J]. 信息网络安全, 2020, 20(9): 6-11. |
| [10] | 余小军, 吴亚飚, 张玉清. 云安全体系结构设计研究[J]. 信息网络安全, 2020, 20(9): 62-66. |
| [11] | 刘文懋, 尤扬. 5G新型基础设施的安全防护思路和技术转换[J]. 信息网络安全, 2020, 20(9): 67-71. |
| [12] | 毕亲波, 赵呈东. 基于STRIDE-LM的5G网络安全威胁建模研究与应用[J]. 信息网络安全, 2020, 20(9): 72-76. |
| [13] | 余果, 王冲华, 陈雪鸿, 李俊. 认证视角下的工业互联网标识解析安全[J]. 信息网络安全, 2020, 20(9): 77-81. |
| [14] | 刘红, 谢永恒, 王国威, 蒋帅. 基于跨领域本体的信息安全分析[J]. 信息网络安全, 2020, 20(9): 82-86. |
| [15] | 王文华, 郝新, 刘焱, 王洋. AI系统的安全测评和防御加固方案[J]. 信息网络安全, 2020, 20(9): 87-91. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||