信息网络安全 ›› 2019, Vol. 19 ›› Issue (9): 125-129.doi: 10.3969/j.issn.1671-1122.2019.09.026
基于共享存储的OpenStack虚拟机应用分发策略
王紫璇1,2, 吕良双1,2, 李肖坚1,4, 王天博1,3
- 1.北京航空航天大学网络技术北京市重点实验室,北京 100191
2.北京航空航天大学计算机学院,北京 100191
3.北京航空航天大学网络空间安全学院,北京 100191
4.广西师范大学计算机科学与信息工程学院,广西桂林 541004
-
收稿日期:2019-07-15出版日期:2019-09-10发布日期:2020-05-11 -
作者简介:作者简介:王紫璇(1995—),女,辽宁,硕士研究生,主要研究方向为云计算;吕良双(1965—),男,湖北,副教授,硕士,主要研究方向为网络与信息安全;李肖坚(1961—),男,广西,教授,博士,主要研究方向为信息系统安全、计算机网络、隐蔽通信等;王天博(1986—),男,黑龙江,讲师,博士,主要研究方向为网络攻防、入侵检测。
-
基金资助:国家自然科学基金[U1636208, 61862008]
A Shared Storage-based Virtual Machine Application Distribution Strategy for OpenStack
Zixuan WANG1,2, Liangshuang LV1,2, Xiaojian LI1,4, Tianbo WANG1,3
- 1. Beijing Key Laboratory of Network Technology, Beihang University, Beijing 100191, China
2. School of Computer Science and Engineering, Beihang University, Beijing 100191, China
3. School of Cyber Science and Technology, Beihang University, Beijing 100191, China
4. School of Computer Science and Information Engineering,Guangxi Normal University, Guilin Guangxi 541004, China
-
Received:2019-07-15Online:2019-09-10Published:2020-05-11
摘要:
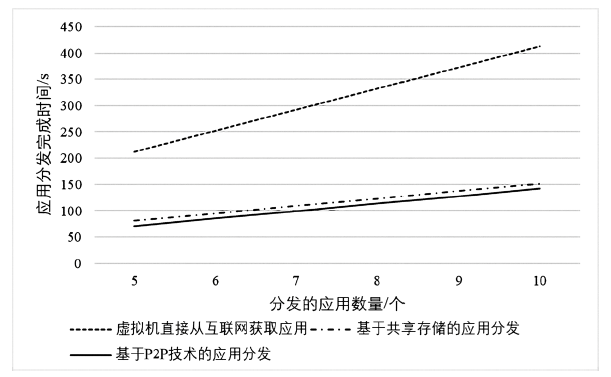
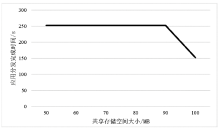
云计算是21世纪互联网的发展趋势之一,在实验和生产环境中被广泛应用。云平台的服务可以以虚拟机的形式提供。为了提供用户需求的服务,需要在交付虚拟机之前或在提供服务的过程中对虚拟机进行按需定制的应用部署。OpenStack是开源云平台的典型代表,针对OpenStack平台,研究如何高效、稳定地对虚拟机进行应用部署,对提高云服务质量具有借鉴意义。文章分析了OpenStack平台中虚拟机应用部署的特点,结合内容分发网络思想,提出了以计算节点内部的共享存储为基础的OpenStack平台虚拟机应用分发策略,并通过仿真实验验证了这一策略的有效性。
中图分类号:
引用本文
王紫璇, 吕良双, 李肖坚, 王天博. 基于共享存储的OpenStack虚拟机应用分发策略[J]. 信息网络安全, 2019, 19(9): 125-129.
Zixuan WANG, Liangshuang LV, Xiaojian LI, Tianbo WANG. A Shared Storage-based Virtual Machine Application Distribution Strategy for OpenStack[J]. Netinfo Security, 2019, 19(9): 125-129.
| [1] | TANG Hong, XU Guangxia.Summary of Cloud Computing Research and Development[J]. Digital Communication, 2010, 37(3): 23-28. |
| 唐红,徐光侠.云计算研究与发展综述[J].数字通信,2010,37(3):23-28. | |
| [2] | MELL P M, GRANCE T.The NIST Definition of Cloud Computing[M]. Maryland: NIST Special Publication, 2011. |
| [3] | WANG Wei, CHANG Jinda, GUO Dong.Research and Implement on a PaaS Platform Management System Based on Cloud Software[J]. Netinfo Security, 2018, 18(2): 10-19. |
| 王伟,常进达,郭栋.一种基于云端软件的PaaS平台管理系统设计与实现[J].信息网络安全,2018,18(2):10-19. | |
| [4] | HE Yue, CHEN Ming.The Security System of Obtaining Evidence and Analyzing SaaS Cloud and the Research on Key Technology[J]. Netinfo Security, 2012, 12(8): 83-85. |
| 何月,陈明.取证分析SaaS云的安全体系及关键技术研究[J].信息网络安全,2012,12(8):83-85. | |
| [5] | LIU Siyao, LI Qiang, LI Bin.Research on Isolation of Container Based on Docker Technology[J]. Computer Engineering & Software, 2015, 36(4): 110-113. |
| 刘思尧,李强,李斌.基于Docker技术的容器隔离性研究[J].软件, 2015,36(4):110-113. | |
| [6] | TAGLIABUE C, ARIAS E, IYENGAR A, et al. Automated Application Delivery with OpenStack Heat Patterns[EB/OL]. , 2016-11-21. |
| [7] | YAMATO Y, MUROI M, TANAKA K, et al.Development of Template Management Technology for Easy Deployment of Virtual resources on OpenStack[J]. Journal of Cloud Computing Advances Systems & Applications, 2014, 3(1): 1-12. |
| [8] | AIFTIMIEI D C, FATTIBENE E, GARGANA R, et al. Abstracting Application Deployment on Cloud Infrastructures[EB/OL]. , 2018-3-20. |
| [9] | CHEN Hao.Automatic deploy Hadoop Cluser on Amazon Elastic Compute Cloud[D]. Newark: University of Delaware, 2015. |
| [10] | KONG Wei, LUO Yu.Multi-level Image Software Assembly Technology Based on OpenStack and Ceph[C]//IEEE. 2016 IEEE Information Technology, Networking, Electronic and Automation Control Conference, May 20-22, 2016, Chongqing, China. NJ: IEEE, 2016: 307-310. |
| [11] | ZHANG Hanying.The Research and Implementation of Virtual Machine System On-demand Key Technologies[D]. Changsha: National University of Defense Technology, 2012. |
| 张含颖. 虚拟机系统按需定制关键技术研究与实现[D].长沙:国防科学技术大学,2012. | |
| [12] | REICH J, LAADAN O, BROSH E, et al.VMTorrent: Scalable P2P Virtual Machine Streaming[C]//ACM. Proceedings of the 8th International Conference on Emerging Networking Experiments and Technologies, December 10-13, 2012, Nice, France. New York: ACM, 2012: 289-300. |
| [13] | ZHANG Zhaoning, LI Ziyang, WU Kui, et al.VMThunder: Fast Provisioning of Large-Scale Virtual Machine Clusters[J]. IEEE Transactions on Parallel & Distributed Systems, 2014, 25(12): 3328-3338. |
| [14] | ZHAO Wenju.Research and Implementation on Integrating P2P Technology into Fast Content Distribution Mechanism in Cloud Platform[D]. Hohhot: Inner Mongolia University, 2016. |
| 赵文举. 融合P2P技术的云平台快速内容分发机制研究与实现[D].呼和浩特:内蒙古大学,2016. | |
| [15] | LIU Hao, YANG Siqing, CHEN Zhigang.Research on Incentive Mechanism with Resisting Fraudulent Conduct for P2P File Sharing in Cloud Computing[J]. Netinfo Security, 2017, 17(11): 37-43. |
| 刘浩,羊四清,陈志刚.云计算环境中抗欺诈行为的P2P文件共享激励机制研究[J].信息网络安全,2017,17(11):37-43. | |
| [16] | CHEN Jie, XU Saihong, ZHANG Haiyang, et al.A Virtual Machine Data Communication Mechanism on Openstack[C]//Springer. International Conference on Human Centered Computing, January 7-9, 2016, Colombo, Sri Lanka. Berlin: Springer, 2016: 1-11. |
| [17] | RENYi, LIU Ling, ZHANG Qi, et al.Shared-memory Optimizations for Inter-virtual-machine Communication[J]. ACM Computing Surveys(CSUR), 2016, 48(4): 49. |
| [18] | ZENG Lingfang, WANG Yang, KENT K B, et al.Naplus: A Software Distributed Shared Memory for Virtual Clusters in the Cloud[J]. Software: Practice and Experience, 2017, 47(9): 1201-1220. |
| [19] | LIAO Xiaofei, CHEN Kai, JIN Hai.AdaptIDC: Adaptive Inter-domain Communication in Virtualized Environments[J]. Computers & Electrical Engineering, 2013, 39(7): 2332-2341. |
| [20] | KURTADIKAR M, PATIL A, TOSHNIWAL P, et al.An inter-VM Communication Model Supporting Live Migration[C]//IEEE. 2013 International Conference on Cloud & Ubiquitous Computing & Emerging Technologies, November 15-16, 2013, Pune, India. NJ: IEEE, 2013: 63-68. |
| [21] | ZHANG Qi, LIU Ling, REN Yi, et al.Residency Aware Inter-VM Communication in Virtualized Xloud: Performance Measurement and Analysis[C]//IEEE. 2013 IEEE Sixth International Conference on Cloud Computing, June 27-July 2, 2013, Santa Clara Marriott, California, USA. NJ: IEEE, 2013: 204-211. |
| [22] | CECE F, FORMICOLA V, OLIVIERO F, et al.An extended ns-2 for Validation of Load Balancing Algorithms in Content Delivery Networks[C]//ACM. Proceedings of the 3rd International ICST Conference on Simulation Tools and Techniques, March 15-19, 2010, Malaga, Spain. New York: ACM, 2010: 32-37. |
| [1] | 刘渊, 乔巍. 云环境下基于Kubernetes集群系统的容器网络研究与优化[J]. 信息网络安全, 2020, 20(3): 36-44. |
| [2] | 白嘉萌, 寇英帅, 刘泽艺, 查达仁. 云计算平台基于角色的权限管理系统设计与实现[J]. 信息网络安全, 2020, 20(1): 75-82. |
| [3] | 任良钦, 王伟, 王琼霄, 鲁琳俪. 一种新型云密码计算平台架构及实现[J]. 信息网络安全, 2019, 19(9): 91-95. |
| [4] | 余奕, 吕良双, 李肖坚, 王天博. 面向移动云计算场景的动态网络拓扑描述语言[J]. 信息网络安全, 2019, 19(9): 120-124. |
| [5] | 崔艳鹏, 冯璐铭, 闫峥, 蔺华庆. 基于程序切片技术的云计算软件安全模型研究[J]. 信息网络安全, 2019, 19(7): 31-41. |
| [6] | 葛新瑞, 崔巍, 郝蓉, 于佳. 加密云数据上支持可验证的关键词排序搜索方案[J]. 信息网络安全, 2019, 19(7): 82-89. |
| [7] | 田春岐, 李静, 王伟, 张礼庆. 一种基于机器学习的Spark容器集群性能提升方法[J]. 信息网络安全, 2019, 19(4): 11-19. |
| [8] | 赵谱, 崔巍, 郝蓉, 于佳. 一种针对El-Gamal数字签名生成的安全外包计算方案[J]. 信息网络安全, 2019, 19(3): 81-86. |
| [9] | 张振峰, 张志文, 王睿超. 网络安全等级保护2.0云计算安全合规能力模型[J]. 信息网络安全, 2019, 19(11): 1-7. |
| [10] | 冯新扬, 沈建京. 一种基于Yarn云计算平台与NMF的大数据聚类算法[J]. 信息网络安全, 2018, 18(8): 43-49. |
| [11] | 陶源, 黄涛, 张墨涵, 黎水林. 网络安全态势感知关键技术研究及发展趋势分析[J]. 信息网络安全, 2018, 18(8): 79-85. |
| [12] | 张琦, 林喜军, 曲海鹏. 云计算中支持授权相等测试的基于身份加密方案[J]. 信息网络安全, 2018, 18(6): 52-60. |
| [13] | 张建标, 杨石松, 涂山山, 王晓. 面向云计算环境的vTPCM可信管理方案[J]. 信息网络安全, 2018, 18(4): 9-14. |
| [14] | 陈妍, 戈建勇, 赖静, 陆臻. 云上信息系统安全体系研究[J]. 信息网络安全, 2018, 18(4): 79-86. |
| [15] | 陈红松, 王钢, 宋建林. 基于云计算入侵检测数据集的内网用户异常行为分类算法研究[J]. 信息网络安全, 2018, 18(3): 1-7. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||