信息网络安全 ›› 2016, Vol. 16 ›› Issue (5): 78-84.doi: 10.3969/j.issn.1671-1122.2016.05.012
智能电网安全研究综述
- 暨南大学信息科学技术学院,广东广州 510632
-
收稿日期:2016-03-11出版日期:2016-05-20发布日期:2020-05-13 -
作者简介:刘家男(1992—),男,河南,博士研究生,主要研究方向为密码学、加密数据搜索;翁健(1976—),男,广东,教授,博士,主要研究方向为密码学与信息安全。
-
基金资助:国家自然科学基金面上项目[61272413,61472165].教育部高等学校博士学科点专项科研基金博导类项目[20134401110011]
Survey on Smart Grid Security
- School of Information Science and Technology, Jinan University, Guangzhou Guangdong 510632, China
-
Received:2016-03-11Online:2016-05-20Published:2020-05-13
摘要:
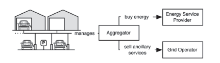
智能电网作为下一代电力网络,具有高可控性、高能源利用率、自愈性等特点。智能电网能给人们生活带来巨大的便利,各个国家和地区纷纷开展自己的智能电网建设。然而与此同时,智能电网中的隐私和安全问题也逐步暴露出来,并成为制约其继续发展的重要因素。智能电网是传统电网的智能化版本。为了实现智能化,在智能电网中引入了大量的新技术,但这些新技术由于缺乏较为成熟的研究,存在较多的安全隐患,从而成为攻击者对智能电网进行攻击的突破口之一。文章针对智能电网中智能测量、Vehicle-to-Grid和智能电网云这3项新技术的研究现状和它们当中存在的安全隐私问题进行介绍和分析,并提出了一些值得进一步研究的问题。
中图分类号:
引用本文
刘家男, 翁健. 智能电网安全研究综述[J]. 信息网络安全, 2016, 16(5): 78-84.
Jianan LIU, Jian WENG. Survey on Smart Grid Security[J]. Netinfo Security, 2016, 16(5): 78-84.
| [1] | JEFFREY T. The Intelligent Power Grid[EB/OL]. |
| [2] | PIEBALGS A.Green Paper - A European Strategy for Sustainable, Competitive and Secure Energy[J]. General Information, 2006, 7(2):8-20. |
| [3] | Federal Energy Regulatory Commission. Assessment of Demand Response and Advanced Metering[EB/OL]. . |
| [4] | FANG X, MISRA S, XUE G, et al.Smart grid-The New and Improved Power Grid: A Survey[J]. Communications Surveys & Tutorials, IEEE, 2012, 14(4): 944-980. |
| [5] | MCDANIEL P, MCLAUGHLIN S.Security and Privacy Challenges in the Smart grid[J]. IEEE Security & Privacy, 2009 (3): 75-77. |
| [6] | ROBERT L, ANTON C. BlackEnergy Trojan Strikes Again: Attacks Ukrainian Electric Power Industry[EB/OL]. . |
| [7] | METKE A R, EKL R L.Security Technology for Smart Grid Networks[J]. Smart Grid, IEEE Transactions on, 2010, 1(1): 99-107. |
| [8] | FADLULLAH Z M, KATO N. Security Challenge in the Smart Grid[EB/OL].. |
| [9] | LUAN Wenpeng.Advanced Metering Infrastructure[J]. Southern Power System Technology, 2009, 3(2): 6-10. |
| [10] | TERRUGGIA R,DONDOSSOLA G. Cyber Security Analysis of Smart Grid Communications with a Network Simulator[EB/OL].. |
| [11] | FHOM H S, BAYAROU K M.Towards a Holistic Privacy Engineering Approach for Smart Grid Systems[C]// IEEE. International Conference on Trust, Security and Privacy in Computing and Communications, November 16-18, 2011. Changsha, China.NJ:IEEE, 2011:234-241. |
| [12] | BOHLI J M, SORGE C, UGUS O.A Privacy Model for Smart Metering[C]// IEEE. IEEE International Conference on Communications Workshops, May 23-27, 2010.Cape Town, South Africa.NJ: IEEE. 2010:1-5. |
| [13] | RAJAGOPALAN S R, SANKAR L, MOHAJER S, et al.Smart Meter Privacy: A Utility-privacy Framework[C]// IEEE. 2011 IEEE International Conference on Smart Grid Communications (SmartGridComm), October 17-20, 2011. Brussels, Belgium.NJ:IEEE, 2011: 190-195. |
| [14] | WANG W, XU Y, KHANNA M.A Survey on the Communication Architectures in Smart Grid[J]. Computer Networks, 2011, 55(15): 3604-3629. |
| [15] | DIAO F, ZHANG F, CHENG X.A Privacy-Preserving Smart Metering Scheme Using Linkable Anonymous Credential[J]. Smart Grid, IEEE Transactions on, 2015, 6(1): 461-467. |
| [16] | CAMENISCH J, LYSYANSKAYA A.A Signature Scheme with Efficient Protocols[EB/OL].. |
| [17] | KIM T T, POOR H V.Scheduling Power Consumption with Price Uncertainty[J]. Smart Grid, IEEE Transactions on, 2011, 2(3): 519-527. |
| [18] | LIANG X, LI X, LU R, et al.UDP: Usage-based Dynamic Pricing with Privacy Preservation for Smart grid[J]. Smart Grid, IEEE Transactions on, 2013, 4(1): 141-150. |
| [19] | NAEHRIG M, LAUTER K, VAIKUNTANATHAN V.Can Homomorphic Encryption Be Practical?[C]//ACM. Proceedings of the 3rd ACM Workshop on Cloud Computing Security Workshop. October 17-21, 2011.Chicago, IL, USA. New York: ACM, 2011: 113-124. |
| [20] | KHURANA H, HADLEY M, LU N, et al.Smart-grid Security Issues[J]. IEEE Security & Privacy, 2010 (1): 81-85. |
| [21] | PEARSON I L G. Smart Grid Cyber Security for Europe[J]. Energy Policy, 2011, 39(9):5211-5218. |
| [22] | LI X, LIANG X, LU R, et al.Securing Smart Grid: Cyber Attacks, Countermeasures, and Challenges[J]. Communications Magazine, IEEE, 2012, 50(8): 38-45. |
| [23] | RAWAT D B, BAJRACHARYA C.Cyber Security for Smart Grid Systems: Status, Challenges and Perspectives[C]// IEEE.SoutheastCon 2015. April 9-12, 2015, Lauderdale, FL, USA.NJ:IEEE, 2015: 1-6. |
| [24] | FARHANGI H.The Path of the Smart Grid[J]. Power and Energy Magazine, IEEE, 2010, 8(1): 18-28. |
| [25] | Smart Grid Interoperability Panel Cyber Security Working Group. Introduction to NISTIR7628 Guidelines for Smart Grid Cyber Security[R]. NIST Special Publication, 2010 (800-53 Revision 3). |
| [26] | GARCIA M, GIANI A, Baldick R.Smart Grid Data Integrity Attacks: Observable Islands[C]// IEEE. Power & Energy Society General Meeting, 2015 IEEE, July 26-30, 2015. Denver, Colorado, USA.NJ:IEEE, 2015: 1-5. |
| [27] | TANAKA Y, TERASHIMA Y, KANDA M, et al.A Security Architecture for Communication between Smart Meters and HAN Devices[C]// IEEE. Smart Grid Communications (SmartGridComm), 2012 IEEE Third International Conference on, November 5-8, 2012.Tainan, China. NJ: IEEE, 2012: 460-464. |
| [28] | ZHANG Y, WANG L, SUN W, et al.Distributed Intrusion Detection System in a Multi-layer Network Architecture of Smart Grids[J]. Smart Grid, IEEE Transactions on, 2011, 2(4): 796-808. |
| [29] | LU R, LIANG X, LI X, et al.Eppa: An Efficient and Privacy-preserving Aggregation Scheme for Secure Smart Grid Communications[J]. Parallel and Distributed Systems, IEEE Transactions on, 2012, 23(9): 1621-1631. |
| [30] | PAILLIER P.Public-Key Cryptosystems Based on Composite Degree Residuosity Classes[C]// IACR. International Conference on Theory and Application of Cryptographic Techniques. May 2-6, 1999. Prague, Czech Republic. Berlin:Springer-Verlag, 1999:223-238. |
| [31] | LIU X, ZHU P, ZHANG Y, et al.A Collaborative Intrusion Detection Mechanism Against False Data Injection Attack in Advanced Metering Infrastructure[J]. IEEE Transactions on Smart Grid, 2015, 6(5): 2435-2443. |
| [32] | KOUNEV V, TIPPER D, YAVUZ A A, et al.A Secure Communication Architecture for Distributed Microgrid Control[J]. IEEE Transactions on Smart Grid, 2015, 6(5): 2484-2492. |
| [33] | HATZIARGYRIOU N, ASANO H, IRAVANI R, et al.Microgrids[J]. Power and Energy Magazine, IEEE, 2007, 5(4): 78-94. |
| [34] | LIU R, VELLAITHURAI C, BISWAS S S, et al.Analyzing the Cyber-Physical Impact of Cyber Events on the Power Grid[J]. IEEE Transactions on Smart Grid, 2015, 6(5):1. |
| [35] | CARYN Colgan. Networx: Guide to Selling Power Back to the Grid[EB/OL].. |
| [36] | KEMPTON W, TOMIĆ J.Vehicle-to-grid Power Fundamentals: Calculating Capacity and Net Revenue[J]. Journal of Power Sources, 2005, 144(1): 268-279. |
| [37] | STEGELMANN M,KESDOGAN D. V2GPriv: Vehicle-to-grid Privacy in the Smart grid[EB/OL].. |
| [38] | YANG Z, YU S, LOU W, et al.P2: Privacy-preserving Communication and Precise Reward Architecture for V2G Networks in Smart grid[J]. Smart Grid, IEEE Transactions on, 2011, 2(4): 697-706. |
| [39] | CHIM T W, YIU S M, HUI L C K, et al. Selling Power Back to the Grid in a Secure and Privacy-preserving Manner[EB/OL].. |
| [40] | LIU H, NING H, ZHANG Y, et al.Role-dependent Privacy Preservation for Secure V2G Networks in the Smart grid[J]. IEEE Transactions on Information Forensics and Security, 2014, 9(2): 208-220. |
| [41] | VAIDYA B,MAKRAKIS D,MOUFTAH H T.Security and Privacy-Preserving Mechanism for Aggregator Based Vehicle-to-Grid Network[EB/OL].. |
| [42] | ROTTONDI C, FONTANA S, VERTICALE G. A Privacy-friendly Framework for Vehicle-to-Grid Interactions[EB/OL].. |
| [43] | LIU J K, MAN H A, SUSILO W, et al.Enhancing Location Privacy for Electric Vehicles (at the Right time)[J]. Lecture Notes in Computer Science, 2012(7459):397-414. |
| [44] | WANG H, QIN B, WU Q, et al.TPP: Traceable Privacy-Preserving Communication and Precise Reward for Vehicle-to-Grid Networks in Smart Grids[J]. Information Forensics and Security, IEEE Transactions on, 2015, 10(11): 2340-2351. |
| [45] | MARKOVIC D S, ZIVKOVIC D, BRANOVIC I, et al.Smart Power Grid and Cloud Computing[J]. Renewable and Sustainable Energy Reviews, 2013(24): 566-577. |
| [46] | YIGIT M, GUNGOR V C, BAKTIR S.Cloud Computing for Smart Grid Applications[J]. Computer Networks, 2014( 70): 312-329. |
| [47] | MAHESHWARI K, LIM M, WANG L, et al.Toward a Reliable, Secure and Fault Tolerant Smart Grid State Estimation in the Cloud[C]// IEEE. Innovative Smart Grid Technologies (ISGT), 2013 IEEE PES, February 24-27, 2013. Washington, DC, USA.NJ:IEEE, 2013: 1-6. |
| [48] | FANG B, YIN X, TAN Y, et al.The Contributions of Cloud Technologies to Smart Grid[J]. Renewable and Sustainable Energy Reviews, 2016(59): 1326-1331. |
| [49] | YANG Y, WU L, HU W.Security Architecture and Key Technologies for Power Cloud Computing[C]// IEEE.Transportation, Mechanical, and Electrical Engineering (TMEE), 2011 International Conference on. December 16-18, 2011.Changchun, China. NJ:IEEE, 2011: 1717-1720. |
| [50] | SINGH A K.Smart Grid Cloud[J]. International Journal of Engineering Research and Applications, 2012, 2(7): 674-704. |
| [51] | BERA S, MISRA S, RODRIGUES J J P C. Cloud Computing Applications for Smart Grid: A Survey[J]. Parallel and Distributed Systems, IEEE Transactions on, 2015, 26(5): 1477-1494. |
| [52] | RUSITSCHKA S, EGER K, GERDES C.Smart Grid Data Cloud: A Model for Utilizing Cloud Computing in the Smart Grid Domain[C]// IEEE. Smart Grid Communications (SmartGridComm), 2010 First IEEE International Conference on. October 4-6, 2010. Gaithersburg, Maryland, USA.NJ: IEEE, 2010:483-488. |
| [53] | BAEK J, VU Q H, LIU J K, et al.A Secure Cloud Computing- based Framework for Big Data Information Management of Smart Grid[J]. IEEE Transactions on Cloud Computing, 2015, 3(2): 233-244. |
| [54] | WANG Yanliang, DENG Song, LIN Weimin, et al.Research of Electric Power Information Security Protection on Cloud Security[C]//IEEE. Power System Technology (POWERCON), 2010 International Conference on. October 24-28, 2010, Hangzhou, China. NJ:IEEE, 2010: 1-6. |
| [55] | MUTTIK I, BARTON C.Cloud Security Technologies[J]. Information Security Technical Report, 2009, 14(1): 1-6. |
| [56] | CALIFANO A, DINCELLI E, GOEL S. Using Features of Cloud Computing to Defend Smart Grid against DDoS Attacks[EB/OL]. https://www.researchgate.net/publication/280577839_Using_Features_of_Cloud_Computing_to_Defend_Smart_Grid_against_DDoS_Attacks,2015-07-31. |
| [57] | ZHANG Y, GJESSING S, LIU H, et al.Securing Vehicle-to-grid Communications in the Smart Grid[J]. Wireless Communications, IEEE, 2013, 20(6): 66-73. |
| [1] | 刘渊, 乔巍. 云环境下基于Kubernetes集群系统的容器网络研究与优化[J]. 信息网络安全, 2020, 20(3): 36-44. |
| [2] | 唐春明, 林旭慧. 隐私保护集合交集计算协议[J]. 信息网络安全, 2020, 20(1): 9-15. |
| [3] | 董威, 李永刚. 基于复杂网络的智能电网网络攻击影响分析研究[J]. 信息网络安全, 2020, 20(1): 52-60. |
| [4] | 白嘉萌, 寇英帅, 刘泽艺, 查达仁. 云计算平台基于角色的权限管理系统设计与实现[J]. 信息网络安全, 2020, 20(1): 75-82. |
| [5] | 汪金苗, 王国威, 王梅, 朱瑞瑾. 面向雾计算的隐私保护与访问控制方法[J]. 信息网络安全, 2019, 19(9): 41-45. |
| [6] | 任良钦, 王伟, 王琼霄, 鲁琳俪. 一种新型云密码计算平台架构及实现[J]. 信息网络安全, 2019, 19(9): 91-95. |
| [7] | 余奕, 吕良双, 李肖坚, 王天博. 面向移动云计算场景的动态网络拓扑描述语言[J]. 信息网络安全, 2019, 19(9): 120-124. |
| [8] | 王紫璇, 吕良双, 李肖坚, 王天博. 基于共享存储的OpenStack虚拟机应用分发策略[J]. 信息网络安全, 2019, 19(9): 125-129. |
| [9] | 郝文江, 林云. 互联网企业社会责任现状与启示研究[J]. 信息网络安全, 2019, 19(9): 130-133. |
| [10] | 刘玉岭, 唐云善, 张琦, 李枫. 电力调度自动化软件安全态势评估方法[J]. 信息网络安全, 2019, 19(8): 15-21. |
| [11] | 周权, 许舒美, 杨宁滨. 一种基于ABGS的智能电网隐私保护方案[J]. 信息网络安全, 2019, 19(7): 25-30. |
| [12] | 崔艳鹏, 冯璐铭, 闫峥, 蔺华庆. 基于程序切片技术的云计算软件安全模型研究[J]. 信息网络安全, 2019, 19(7): 31-41. |
| [13] | 葛新瑞, 崔巍, 郝蓉, 于佳. 加密云数据上支持可验证的关键词排序搜索方案[J]. 信息网络安全, 2019, 19(7): 82-89. |
| [14] | 田春岐, 李静, 王伟, 张礼庆. 一种基于机器学习的Spark容器集群性能提升方法[J]. 信息网络安全, 2019, 19(4): 11-19. |
| [15] | 李怡霖, 闫峥, 谢皓萌. 车载自组织网络的隐私保护综述[J]. 信息网络安全, 2019, 19(4): 63-72. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||