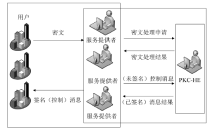
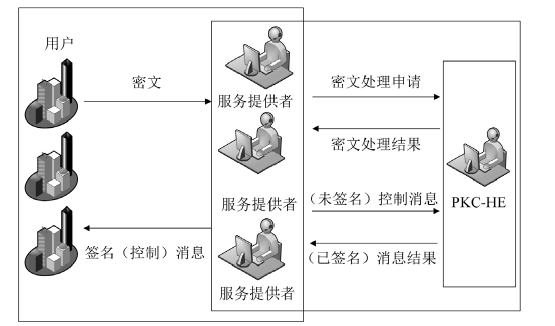
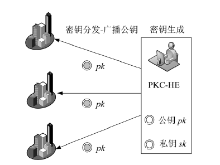
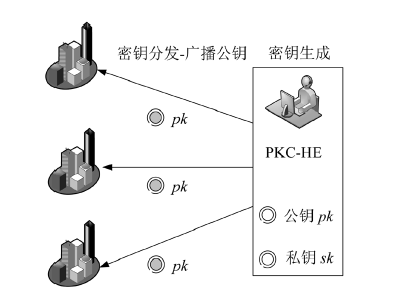
信息网络安全 ›› 2016, Vol. 16 ›› Issue (3): 1-7.doi: 10.3969/j.issn.1671-1122.2016.03.001
• • 下一篇
一种基于全同态加密的智能电网数据交换隐私保护方案
- 1.哈尔滨工程大学计算科学与技术学院,黑龙江哈尔滨 150001
2.黑龙江省招生考试委员会办公室,黑龙江哈尔滨 150090
3.佳木斯大学信息电子技术学院,黑龙江佳木斯154007
-
收稿日期:2016-01-26出版日期:2016-03-25发布日期:2020-05-13 -
作者简介:作者简介: 李增鹏(1989--),男,山东,博士研究生,主要研究方向为密码学;邹岩(1978--),男,辽宁,工程师,硕士,主要研究方向为信息安全管理与信息处理;张磊(1982--),男,黑龙江,助理研究员,博士研究生,主要研究方向为隐私保护;马春光(1974--),男,黑龙江,教授,博士,主要研究方向为网络安全.
-
基金资助:国家自然科学基金[61472097];黑龙江省自然科学基金[F2015022];高等学校博士学科点专项科研基金(博导类)[20132304110017]
A Privacy Preservation Scheme for Data Exchange of Smart Grid Based on Homomorphic Encryption
Zengpeng LI1, Yan ZOU2, Lei ZHANG1,3, Chunguang MA1( )
)
- 1. College of Computer Science and Technology, Harbin Engineering University, Harbin Heilongjiang 150001, China
2. Admission Examination Committee Office of Heilongjiang, Harbin Heilongjiang 150090, China
3. College of Information Science and Electronic Technology, Jiamusi University, Jiamusi Heilongjiang 154007, China
-
Received:2016-01-26Online:2016-03-25Published:2020-05-13
摘要:
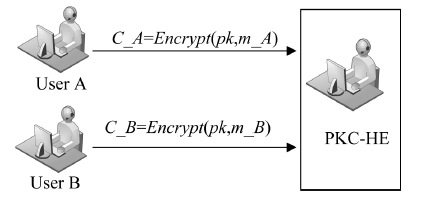
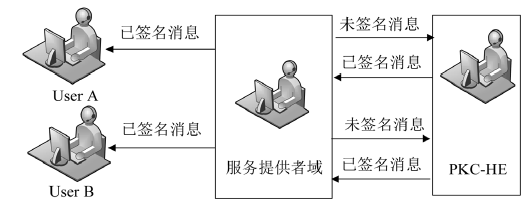
文章结合智能电网的特征和发展趋势,分析了目前智能电表中用户隐私保护主要包括的电表实时发送数据阶段和记账阶段两部分,通过加密和认证等技术对智能电网中用户的隐私信息进行保护.然而,现有的智能电网隐私保护认证技术大多不够完善,通过公钥加密系统保护智能电网的安全愈发重要,而基于全同态加密的安全和高效的智能电网数据交换是当前信息安全研究热点问题之一.因此,文章针对数据交换方案,提出一个基于全同态加密技术的加密系统.文章所构造的智能电网隐私保护方案具有强安全性和高效的用户隐私保护特性,保证了用户隐私数据的机密性和完整性.
中图分类号:
引用本文
李增鹏, 邹岩, 张磊, 马春光. 一种基于全同态加密的智能电网数据交换隐私保护方案[J]. 信息网络安全, 2016, 16(3): 1-7.
Zengpeng LI, Yan ZOU, Lei ZHANG, Chunguang MA. A Privacy Preservation Scheme for Data Exchange of Smart Grid Based on Homomorphic Encryption[J]. Netinfo Security, 2016, 16(3): 1-7.
| [1] | 石沙沙,孙文红,江明建,等.基于分布式数据聚合的智能电网隐私保护协议研究[J]. 信息网络安全,2015(12):59-65. |
| [2] | 张东霞,苗新,刘丽平,等. 智能电网大数据技术发展研究[J]. 中国电机工程学报,2015(1):2-12. |
| [3] | 李兴源,魏巍,王渝红,等.坚强智能电网发展技术的研究[J]. 电力系统保护与控制,2009,37(17):1-7. |
| [4] | 陈福臻,程久军,廖竞学,等. 基于网络编码的同态HASH抗污染攻击系统研究[J]. 信息网络安全,2015(6):33-40. |
| [5] | MCDANIEL P, MCLAUGHLIN S.Security and Privacy Challenges in the Smart Grid[J]. IEEE Security & Privacy, 2009, 7(3): 75-77. |
| [6] | SKOPIK F.Security Is Not Enough! On Privacy Challenges in Smart Grids[J]. International Journal of Smart Grid Clean Energy, 2012, 1(1): 7-14. |
| [7] | ZEADALLY S, PATHAN A S K, ALCARAZ C, et al. Towards Privacy Protection in Smart Grid[J]. Wireless Personal Communications, 2013, 73(1): 23-50. |
| [8] | METKE A R, EKL R L.Security Technology For Smart Grid Networks[J]. IEEE Transactions on Smart Grid, 2010, 1(1): 99-107. |
| [9] | 李斌,白淑君,宋怀刚.具备多级安全机制的在线数据库同态加密方案[J]. 信息网络安全,2014(12):12-15. |
| [10] | LI Fengjun, LUO Bo, LIU Peng.Secure Information Aggregation for Smart Grids Using Homomorphic Encryption[C]//IEEE. 2010 First IEEE International Conference on Smart Grid Communications (SmartGridComm), October 4-6, 2010, Gaithersburg, MD. New Jersey: IEEE, 2010:327-332. |
| [11] | GENTRY C.A Fully Homomorphic Encryption Scheme[D]. Palo Alto: Stanford University, 2009. |
| [12] | 龚凡. 基于群签名的智能电网用电量统计及电费的缴纳方案[D]. 西安:西安电子科技大学,2013. |
| [13] | DIJK M V, GENTRY C, HALEVI S, et al.Fully Homomorphic Encryption over the Integers[C]//IACR. 29th Annual International Conference on the Theory and Applications of Cryptographic Techniques, May 30-June 3, 2010, Riviera, French. Heidelberg: Springer, 2010: 24-43. |
| [14] | LU Rongxing, LIANG Xiaohui, LI Xu, et al.Eppa: An Efficient And Privacy-Preserving Aggregation Scheme for Secure Smart Grid Communications[J]. IEEE Transactions on Parallel and Distributed Systems, 2012, 23(9): 1621-1631. |
| [15] | 吕海峰,丁勇,代洪艳,等. LWE上的全同态加密方案研究[J]. 信息网络安全,2015(1):32-38. |
| [16] | STEHLÉ D, STEINFELD R.Faster Fully Homomorphic Encryption[C]//IACR. 16th International Conference on the Theory and Application of Cryptology and Information Security, December 5-9, 2010, Singapore. Heidelberg: Springer, 2010: 377-394. |
| [17] | CORON J S, MANDAL A, NACCACHE D, et al.Fully Homomorphic Encryption over the Integers with Shorter Public Keys[C]//IACR. 31st Annual Cryptology Conference, August 14-18, 2011, Santa Barbara, CA, USA. Heidelberg: Springer, 2011: 487-504. |
| [18] | CORON J S, NACCACHE D, TIBOUCHI M.Public Key Compression and Modulus Switching for Fully Homomorphic Encryption over the Integers[C]//IACR. 31st Annual International Conference on the Theory and Applications of Cryptographic Techniques, April 15-19, 2012, Cambridge, UK. Heidelberg: Springer, 2012: 446-464. |
| [19] | CHEON J H, CORON J S, KIM J, et al.Batch Fully Homomorphic Encryption over the Integers[C]//IACR. 32nd Annual International Conference on the Theory and Applications of Cryptographic Techniques, May 26-30, 2013, Athens, Greece. Heidelberg: Springer, 2013: 315-335. |
| [20] | FAN Junfeng, VERCAUTEREN F. Somewhat Practical Fully Homomorphic Encryption[EB/OL]. . |
| [21] | CORON J S, LEPOINT T, TIBOUCHI M.Scale-Invariant Fully Homomorphic Encryption over the Integers[C]//IACR. 17th International Conference on Practice and Theory in Public-Key Cryptography, March 26-28, 2014, Buenos Aires, Argentina. Heidelberg: Springer, 2014: 311-328. |
| [22] | CHEON J H, STEHLÉ D.Fully Homomophic Encryption over the Integers Revisited[C]//IACR. 34th Annual International Conference on the Theory and Applications of Cryptographic Techniques, April 26-30, 2015, Sofia, Bulgaria. Heidelberg: Springer, 2015: 513-536. |
| [23] | NUIDA K, KUROSAWA K.(Batch) Fully Homomorphic Encryption over Integers for Non-Binary Message Spaces[C]//IACR. 34th Annual International Conference on the Theory and Applications of Cryptographic Techniques, April 26-30, 2015, Sofia, Bulgaria. Heidelberg: Springer, 2015: 537-555. |
| [24] | HIROMASA R, ABE M, OKAMOTO T.Packing Messages and Optimizing Bootstrapping in GSW-FHE[C]//IACR. 18th IACR International Conference on Practice and Theory in Public-Key Cryptography, March 30-April 1, 2015, Gaithersburg, MD, USA. Heidelberg: Springer, 2015: 699-715. |
| [25] | COHEN J D, FISCHER M J.A Robust and Verifiable Cryptographically Secure Election Scheme[C]//IEEE. 26th Annual Symposium on Foundations of Computer Science, October 21-23, 1985, Portland, OR, USA. New Jersey: IEEE, 1985: 372-382. |
| [26] | HOWGRAVE-GRAHAM N. Approximate Integer Common Divisors[EB/OL]. . |
| [27] | GENTRY C, HALEVI S.Implementing Gentry's Fully-Homomorphic Encryption Scheme[C]//IACR. 30th Annual International Conference on the Theory and Applications of Cryptographic Techniques, May 15-19, 2011, Tallinn, Estonia. Heidelberg: Springer, 2011: 129-148. |
| [28] | BRAKERSKI Z, GENTRY C, VAIKUNTANATHAN V.(Leveled) Fully Homomorphic Encryption without Bootstrapping[J]. Acm Transactions on Computation Theory, 2011, 18(3): 169-178. |
| [29] | CHEN Yuanmi, NGUYEN P Q.Faster Algorithms for Approximate Common Divisors: Breaking Fully-Homomorphic-Encryption Challenges over the Integers[C]//IACR. 31st Annual International Conference on the Theory and Applications of Cryptographic Techniques, April 15-19, 2012, Cambridge, UK. Heidelberg: Springer, 2015: 502-519. |
| [30] | BRAKERSKI Z.Fully Homomorphic Encryption without Modulus Switching from Classical GapSVP[C]//IACR. 32nd Annual Cryptology Conference, August 19-23, 2012, Santa Barbara, CA, USA. Heidelberg: Springer, 2015: 868-886. |
| [31] | REGEV O. On Lattices, Learning with Errors, Random Linear Codes, and Cryptography[J]. Journal of the Acm, 2005, 56(6): 84-93. |
| [32] | 王志刚,马春光,史晓倩. 基于Binary LWE的全同态加密方案研究[J]. 信息网络安全,2015(7):41-50. |
| [1] | 唐春明, 林旭慧. 隐私保护集合交集计算协议[J]. 信息网络安全, 2020, 20(1): 9-15. |
| [2] | 董威, 李永刚. 基于复杂网络的智能电网网络攻击影响分析研究[J]. 信息网络安全, 2020, 20(1): 52-60. |
| [3] | 汪金苗, 王国威, 王梅, 朱瑞瑾. 面向雾计算的隐私保护与访问控制方法[J]. 信息网络安全, 2019, 19(9): 41-45. |
| [4] | 郝文江, 林云. 互联网企业社会责任现状与启示研究[J]. 信息网络安全, 2019, 19(9): 130-133. |
| [5] | 刘玉岭, 唐云善, 张琦, 李枫. 电力调度自动化软件安全态势评估方法[J]. 信息网络安全, 2019, 19(8): 15-21. |
| [6] | 周权, 许舒美, 杨宁滨. 一种基于ABGS的智能电网隐私保护方案[J]. 信息网络安全, 2019, 19(7): 25-30. |
| [7] | 刘文超, 潘峰, 杨晓元, 周潭平. 基于GPU的全同态加密软件库调试与分析[J]. 信息网络安全, 2019, 19(6): 76-83. |
| [8] | 李怡霖, 闫峥, 谢皓萌. 车载自组织网络的隐私保护综述[J]. 信息网络安全, 2019, 19(4): 63-72. |
| [9] | 傅彦铭, 李振铎. 基于拉普拉斯机制的差分隐私保护k-means++聚类算法研究[J]. 信息网络安全, 2019, 19(2): 43-52. |
| [10] | 黎妹红, 齐小晨, 吴倩倩. 基于动态密钥的智能电网无线通信数据加密传输方案[J]. 信息网络安全, 2019, 19(12): 10-21. |
| [11] | 赵志岩, 吴剑, 康凯. 一种兼顾业务数据安全的隐私保护世系发布方法[J]. 信息网络安全, 2019, 19(12): 29-37. |
| [12] | 田秀霞, 陈希, 田福粮. 基于区块链的社区分布式电能安全交易平台方案[J]. 信息网络安全, 2019, 19(1): 51-58. |
| [13] | 胡荣磊, 何艳琼, 曾萍, 范晓红. 一种大数据环境下医疗隐私保护方案设计与实现[J]. 信息网络安全, 2018, 18(9): 48-54. |
| [14] | 李佩丽, 徐海霞, 马添军, 穆永恒. 区块链技术在网络互助中的应用及用户隐私保护[J]. 信息网络安全, 2018, 18(9): 60-65. |
| [15] | 马蓉, 陈秀华, 刘慧, 熊金波. 移动群智感知中用户隐私度量与隐私保护研究[J]. 信息网络安全, 2018, 18(8): 64-72. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||