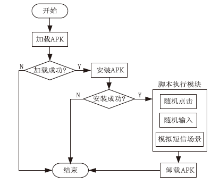
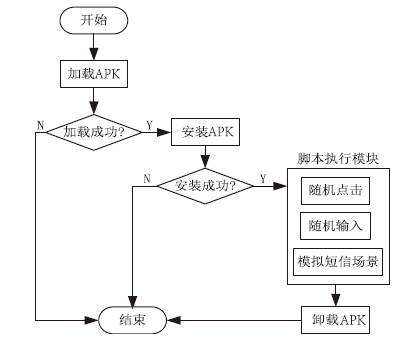
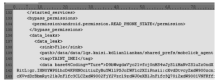
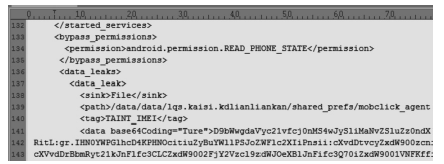
| [1] |
姬炳帅,李虎,韩伟红,等. 面向电子商务的用户异常行为检测研究[J]. 信息网络安全,2014(9):80-85.
|
| [2] |
文伟平, 梅瑞, 宁戈,等. Android恶意软件检测技术分析和应用研究[J]. 通信学报,2014,35(8):78-85.
|
| [3] |
BATYUK L, HERPICH M, Camtepe S A, et al.Using Static Analysis for Automatic Assessment and Mitigation of Unwanted and Malicious Activities within Android Applications[C]//IEEE Computer Society. IEEE 6th International Conference on Malicious and Unwanted Software, October18-19, 2011,Fajardo, Puerto Rico,USA.Piscataway, NJ: IEEE. 2011: 18-19.
|
| [4] |
赵洋,胡龙,熊虎,等.基于沙盒的Android恶意软件动态分析方案[J]. 信息网络安全,2014(12):21-26.
|
| [5] |
BURGUERA I, ZURUTUZA U, Nadjm-Tehrani S.Crowdroid: Behavior-based Malware Detection System for Android[C]//ACM. Proceedings of the 1st ACM workshop on Security and privacy in smartphones and mobile devices, Octobor 17-21, 2011, Chicago, Illinois, USA. New York: ACM, 2011:15-26.
|
| [6] |
王丽娜, 谈诚, 陈栋,等. Android系统中基于移动支付行为特征的恶意检测研究与实现[EB/OL]. .
|
| [7] |
FUN T S, BENG L Y, LIKOH J, et al.A Lightweight and Private Mobile Payment Protocol by Using Mobile Network Operator[C]// IEEE Computer Society. IEEE International Conference on Computer and Communication Engineering,May 13-15, 2008, International Islamic University, Kuala Lumpur,Malaysia. Piscataway, NJ: IEEE, 2008: 162-166.
|
| [8] |
ZHOU Y, JIANG X.Dissecting Android Malware: Characterization and Evolution[C]// IEEE Computer Society. IEEE Symposium on Security and Privacy, May 20-23, 2012, San Francisco,California,USA. Piscataway, NJ: IEEE,2012: 95-109.
|
| [9] |
兰芸,李宝林. 木马恶意软件的电子数据勘查与取证分析初探[J]. 信息网络安全,2014(5):87-91.
|
| [10] |
REHMAN S U, Abid M.An Empirical Research on the User Acceptance of Mobile Payment System[C]//IEEE Computer Society. IEEE International Conference on Information Society, November 10-12, 2014, London,United Kingdom.Piscataway, NJ: IEEE, 2014: 329-335.
|
| [11] |
JACOB G, DEBAR H, FILIOL E.Behavioral Detection of Malware: from a Survey towards an Established Taxonomy[J]. Journal in Computer Virology, 2008, 4(3): 251-266.
|
| [12] |
ZHOU T.An Empirical Examination of Initial Trust in Mobile Payment[J]. Wireless Personal Communications, 2014, 77(2): 1519-1531.
|
| [13] |
胡文君, 赵双, 陶敬,等. 一种针对Android平台恶意代码的检测方法及系统实现[J]. 西安交通大学学报,2013,47(10):37-43.
|
 ), Anmin FU1,2, Zhentao HUANG1
), Anmin FU1,2, Zhentao HUANG1