信息网络安全 ›› 2025, Vol. 25 ›› Issue (8): 1302-1312.doi: 10.3969/j.issn.1671-1122.2025.08.010
基于RBF机制的无痕区块链隐蔽通信方案
佘维1,2,3,4, 马天祥1,4, 冯海格3,4, 刘炜1,4( )
)
- 1.郑州大学网络空间安全学院,郑州 450002
2.嵩山实验室,郑州 450002
3.郑州大学计算机与人工智能学院,郑州 450002
4.郑州市区块链与数据智能重点实验室,郑州 450002
-
收稿日期:2024-05-28出版日期:2025-08-10发布日期:2025-09-09 -
通讯作者:刘炜 E-mail:wliu@zzu.edu.cn -
作者简介:佘维(1977—),男,湖南,教授,博士,CCF会员,主要研究方向为区块链技术、信息安全和智能系统|马天祥(2000—),男,河北,硕士研究生,主要研究方向为区块链技术和信息安全|冯海格(2000—),女,河南,硕士研究生,主要研究方向为区块链技术和信息安全|刘炜(1981—),男,河南,教授,博士,主要研究方向为区块链技术、信息安全和智慧医疗 -
基金资助:国家重点研发计划(31703-3);嵩山实验室预研项目(YYYY022022003)
Tracing-Free Blockchain Covert Communication Method Based on RBF Mechanism
SHE Wei1,2,3,4, MA Tianxiang1,4, FENG Haige3,4, LIU Wei1,4( )
)
- 1. School of Cyber Science and Engineering, Zhengzhou University, Zhengzhou 450002, China
2. Songshan Laboratory, Zhengzhou 450002, China
3. School of Computer and Artificial Intelligence, Zhengzhou University, Zhengzhou 450002, China
4. Zhengzhou Key Laboratory of Blockchain and Data Intelligence, Zhengzhou 450002, China
-
Received:2024-05-28Online:2025-08-10Published:2025-09-09
摘要:
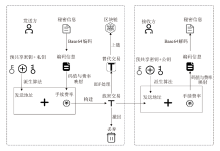
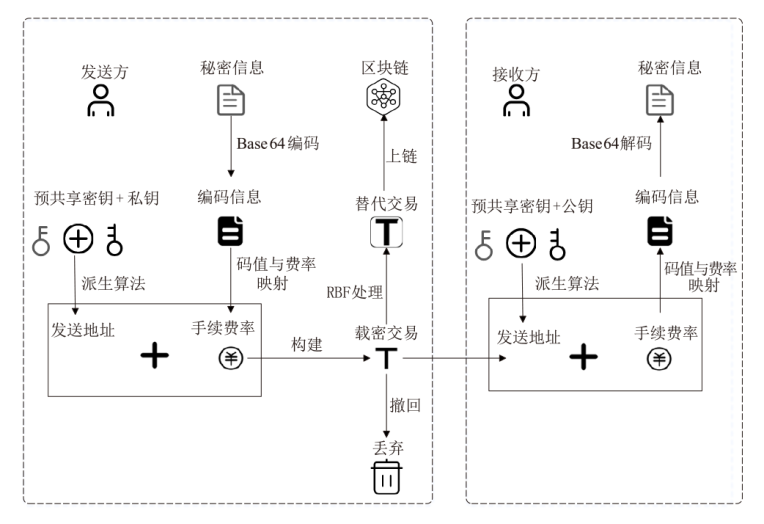
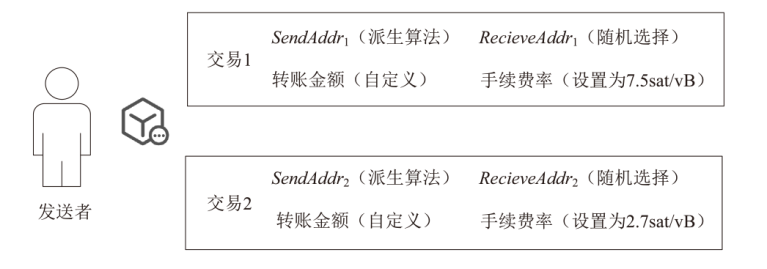
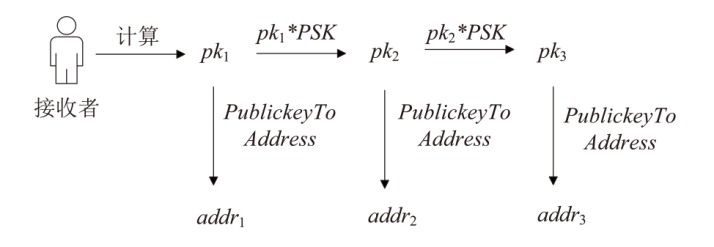
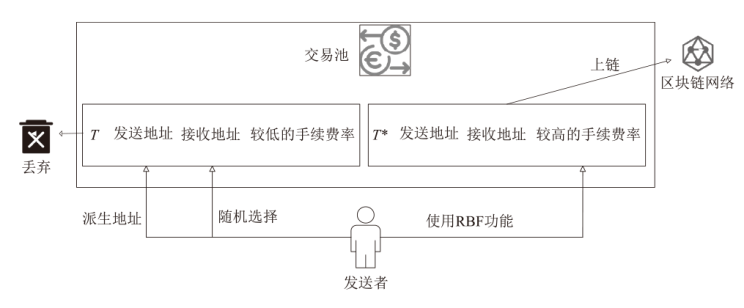
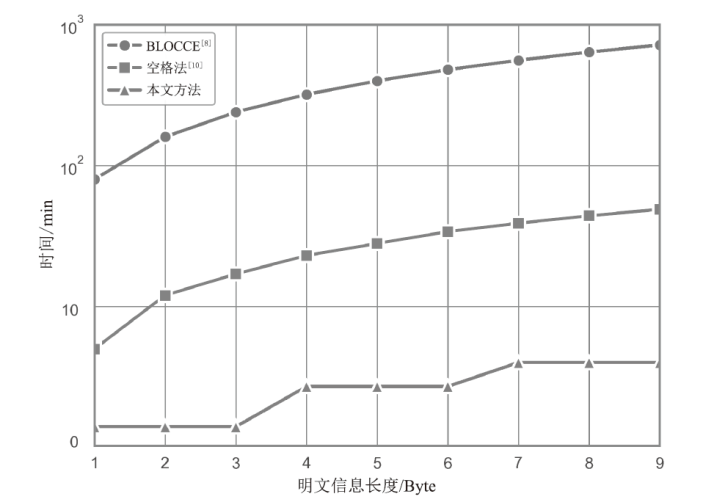
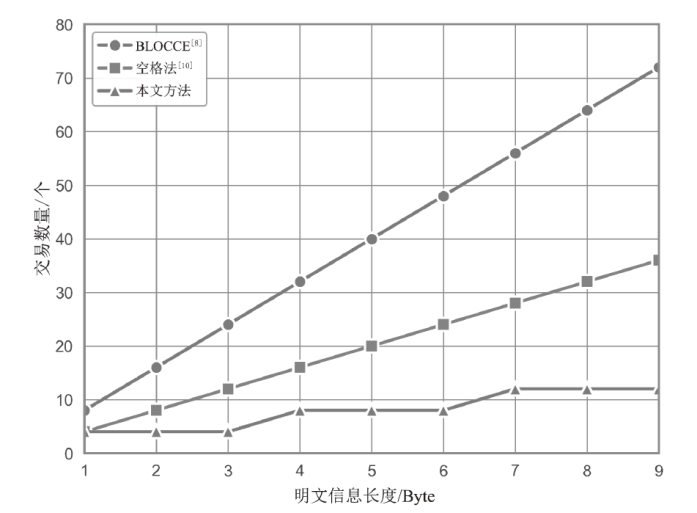
针对现有区块链隐蔽通信技术存在的载密交易信息永久存储、提取效率低、嵌入强度不足及隐蔽性差等问题,文章提出一种基于比特币交易替换(RBF)机制的解决方案。首先,发送方对秘密信息进行Base64编码,并通过建立码值与交易手续费率的映射关系,利用交易费率传递秘密信息,显著提升单笔交易的信息嵌入容量;然后,发送方在载密交易被确认前,通过RBF机制生成替代交易并废弃原始载密交易,最终仅使替代交易上链,实现载密交易的零留存,从而避免信息永久存储带来的安全风险;‘后,接收方通过追踪载密交易的发送地址,实时监听交易状态,在原始交易被废弃前快速查询并提取嵌入信息。实验结果表明,该方法平均每字节信息的嵌入与提取时间从分钟级缩短至秒级,单笔交易的平均信息嵌入量达到6比特。该系统在隐蔽性和抗溯源能力上显著优于现有方案。
中图分类号:
引用本文
佘维, 马天祥, 冯海格, 刘炜. 基于RBF机制的无痕区块链隐蔽通信方案[J]. 信息网络安全, 2025, 25(8): 1302-1312.
SHE Wei, MA Tianxiang, FENG Haige, LIU Wei. Tracing-Free Blockchain Covert Communication Method Based on RBF Mechanism[J]. Netinfo Security, 2025, 25(8): 1302-1312.
表1
Base64编码
| 码值 | 字符 | 码值 | 字符 | 码值 | 字符 | 码值 | 字符 |
|---|---|---|---|---|---|---|---|
| 0 | A | 16 | Q | 32 | g | 48 | w |
| 1 | B | 17 | R | 33 | h | 49 | x |
| 2 | C | 18 | S | 34 | i | 50 | y |
| 3 | D | 19 | T | 35 | j | 51 | z |
| 4 | E | 20 | U | 36 | k | 52 | 0 |
| 5 | F | 21 | V | 37 | l | 53 | 1 |
| 6 | G | 22 | W | 38 | m | 54 | 2 |
| 7 | H | 23 | X | 39 | n | 55 | 3 |
| 8 | I | 24 | Y | 40 | o | 56 | 4 |
| 9 | J | 25 | Z | 41 | p | 57 | 5 |
| 10 | K | 26 | a | 42 | q | 58 | 6 |
| 11 | L | 27 | b | 43 | r | 59 | 7 |
| 12 | M | 28 | c | 44 | s | 60 | 8 |
| 13 | N | 29 | d | 45 | t | 61 | 9 |
| 14 | O | 30 | e | 46 | u | 62 | + |
| 15 | P | 31 | f | 47 | v | 63 | / |
表3
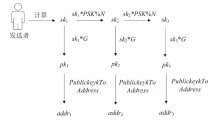
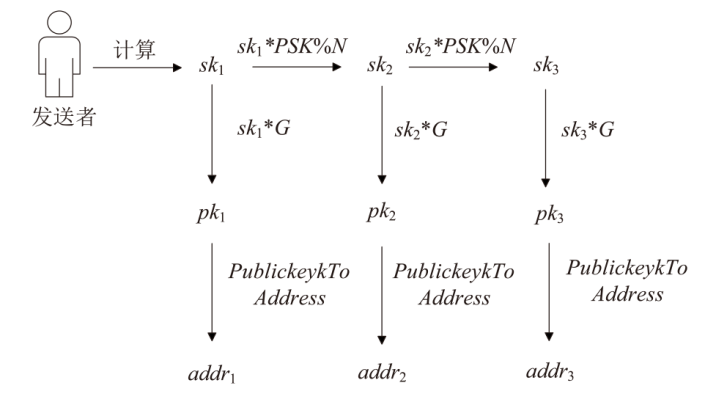
派生实验数据信息
| 参数 | 值 |
|---|---|
| PSK | 76438561322594816937592661675008834131284340043820951912939840865026908677795 |
| pk1 | X:73442749537236419893675063490678586239136868616312090663972655544918591719861 |
| Y:51439161098480415867844876072863013710639021169466611798444914279677986184605 | |
| addr1 | mnNZGSuwStubRDumjDTr7Jgdu64j9xBhqc |
| pk2 | X:44167725728286626423507031731064295266930000403734932314255429566860271285632 |
| Y:41552797760144518979373303401903505428033605608469850166436936337431722181384 | |
| addr2 | mimtNz1vYFnxzf6GFeX4153eoH4zVYP5qE |
| pk3 | X:70382021197554170460884922229825554099758891352679201990718096667486893308080 |
| Y:59170546560708766210752917907066594932387772256704441115142735642473816628444 | |
| addr3 | n3VQ3fCvoEM7rMgJbNEMQGhcwjfZ6JSTPq |
| pk4 | X:101011145969842785069698398671332317973937492068109339606340767344578450439906 |
| Y:11067298237285078033656396816366755687742255597163549082791846567176847571705 | |
| addr4 | n4cycgTYNKvRd3NjyNmz6kf95ra95Qfrcj |
表4
载密交易信息
| 序号 | 载密交易ID | 手续费率 |
|---|---|---|
| 1 | c5613a06739045b40439e87f8e67a2091e32fca4c49e7654f51e74223f30f4f7 | 3.0 sat/vB |
| 2 | ed8785b332e90a158c31224a427eb2a4128cdb7cf4ed5388bca9408c1eaf98ce | 3.9 sat/vB |
| 3 | 9ed66d81f8eb67e10a55d0779536dbbfe184283f40d7489d77362b151e679646 | 4.1 sat/vB |
| 4 | 76f0919ee2dc9e29c24f486ec4328631dc4d6c5c4ef993005fc29a7fced15e19 | 5.3 sat/vB |
表5
替代交易信息
| 序号 | 替代交易ID | 手续费率 |
|---|---|---|
| 1 | 60126b06b40b76e926f69010ee638c4152af38ed588c9fb3599a11289134f223 | 20.1 sat/vB |
| 2 | fbb75772873feded5c2f9760a0d70cc0d78b7eaabaa580623788dc2ec662b62f | 18.1 sat/vB |
| 3 | 0511343117d77bd816afb8e4643de634e7f72d4b3331963534de73e4bb5e7049 | 18.7 sat/vB |
| 4 | c512a278b968860c38917b6ac30765a1dbd3a7473fd78bc7f8bb78d74f4eb878 | 17.3 sat/vB |
| [1] | LAMPSON B W. A Note on the Confinement Problem[J]. Communications of the ACM, 1973, 16(10): 613-615. |
| [2] | SIMMONS G J. The Prisoners' Problem and the Subliminal Channel[C]// Springer. The Advances in Cryptology. Heidelberg: Springer, 1984: 51-67. |
| [3] |
LI Leixiao, DU Jinze, LIN Hao, et al. Research Progress of Blockchain Network Covert Channel[J]. Journal on Communications, 2022, 43(9): 209-223.
doi: 10.11959/j.issn.1000-436x.2022146 |
|
李雷孝, 杜金泽, 林浩, 等. 区块链网络隐蔽信道研究进展[J]. 通信学报, 2022, 43(9): 209-223.
doi: 10.11959/j.issn.1000-436x.2022146 |
|
| [4] | SANKA A I, IRFAN M, HUANG I, et al. A Survey of Breakthrough in Blockchain Technology: Adoptions, Applications, Challenges and Future Research[J]. Computer Communications, 2021, 169: 179-201. |
| [5] | ALI O, JARADAT A, KULAKLI A, et al. A Comparative Study: Blockchain Technology Utilization Benefits, Challenges and Functionalities[J]. IEEE Access, 2021, 9: 12730-12749. |
| [6] | CHEN Lei, ZHOU Yanqiu. Blockchain Development Trends, Security Risk Prevention, and Top-Level Institutional Design[J]. Reform, 2020(6): 44-57. |
| 陈蕾, 周艳秋. 区块链发展态势、安全风险防范与顶层制度设计[J]. 改革, 2020(6): 44-57. | |
| [7] | YUAN Wenxin, CHEN Xingshu, ZHU Yi, ZENG Xuemei. HTTP Payload Covert Channel Detection Method Based on Deep Learning[J]. Netinfo Security, 2023, 23(7): 53-63. |
| 苑文昕, 陈兴蜀, 朱毅, 曾雪梅. 基于深度学习的HTTP负载隐蔽信道检测方法[J]. 信息网络安全, 2023, 23(7): 53-63. | |
| [8] | PARTALA J. Provably Secure Covert Communication on Blockchain[J]. Cryptography, 2018, 2(3): 18-29. |
| [9] | SONG Shang, PENG Wei. BLOCCE+: An Improved Blockchain-Based Covert Communication Approach[J]. Journal of Chongqing University of Technology (Natural Science), 2020, 34(9): 238-244. |
| 宋上, 彭伟. BLOCCE+:一种改进的基于区块链的隐蔽通信方法[J]. 重庆理工大学学报(自然科学), 2020, 34(9): 238-244. | |
| [10] |
SHE Wei, HUO Lijuan, TIAN Zhao, et al. Blockchain Covert Communication Model for Plain Text Information Hiding[J]. Computer Science, 2022, 49(1): 345-352.
doi: 10.11896/jsjkx.201000112 |
|
佘维, 霍丽娟, 田钊, 等. 面向纯文本信息隐藏的区块链隐蔽通信模型[J]. 计算机科学, 2022, 49(1): 345-352.
doi: 10.11896/jsjkx.201000112 |
|
| [11] |
SHE Wei, HUO Lijuan, LIU Wei, et al. A Blockchain-Based Covert Communication Model for Hiding Sensitive Documents and Sender Identity[J]. Acta Electronica Sinica, 2022, 50(4): 1002-1013.
doi: 10.12263/DZXB.20211021 |
|
佘维, 霍丽娟, 刘炜, 等. 一种可隐藏敏感文档和发送者身份的区块链隐蔽通信模型[J]. 电子学报, 2022, 50(4): 1002-1013.
doi: 10.12263/DZXB.20211021 |
|
| [12] |
XIONG Lizhi, ZHU Rong, FU Zhangjie. Covert Communication Method of Blockchain Network Based on Transaction Construction and Forwarding Mechanism[J]. Journal on Communications, 2022, 43(8): 176-187.
doi: 10.11959/j.issn.1000-436x.2022161 |
|
熊礼治, 朱蓉, 付章杰. 基于交易构造和转发机制的区块链网络隐蔽通信方法[J]. 通信学报, 2022, 43(8): 176-187.
doi: 10.11959/j.issn.1000-436x.2022161 |
|
| [13] | GUO Rui, YANG Xin, WANG Junming. Verifiable and Revocable Attribute Encryption Scheme Based on Blockchain[J]. Netinfo Security, 2024, 24(6): 863-878. |
| 郭瑞, 杨鑫, 王俊茗. 基于区块链的可验证可撤销属性加密方案[J]. 信息网络安全, 2024, 24(6): 863-878. | |
| [14] | NAKAMOTO S. Bitcoin: A Peer-to-Peer Electronic Cash System[J]Decentralized Business Review, 2008: 21260-21268. |
| [15] | LIU Haifang, WU Yuxin. Overview of the Bitcoin System[J]. Modern Computer, 2020(19): 45-51. |
| 刘海房, 吴雨芯. 比特币系统综述[J]. 现代计算机, 2020(19): 45-51. | |
| [16] | ZHANG Lihua, HUANG Yang, JIANG Tengfei. High-Speed Railway Environmental Monitoring Data Identity Authentication Scheme Based on Consortium Blockchain[C]// ACM.The 2nd International Conference on Blockchain Technology and Applications. New York: ACM, 2019: 7-13. |
| [17] |
ZENG Shiqin, HUO Ru, HUANG Tao, et al. Survey of Blockchain: Principle, Progress and Application[J]. Journal on Communications, 2020, 41(1): 134-151.
doi: 10.11959/j.issn.1000-436x.2020027 |
| [18] | TIAN Jing, GOU Gaopeng, LIU Chang, et al. DLchain: A Covert Channel Overblockchain Based on Dynamic Labels[C]// Springer. Information and Communications Security:21st International Conference, ICICS 2019. Heidelberg: Springer, 2020: 814-830. |
| [19] | WOOD G. Ethereum: A Secure Decentralised Generalised Transaction Ledger[J]. Ethereum Project Yellow Paper, 2014, 151: 1-32. |
| [20] | ANDROULAKI E, BARGER A, BORTNIKOV V, et al. Hyperledger Fabric: A Distributed Operating System for Permissioned Blockchains[C]// ACM.The Thirteenth EuroSys Conference. New York: ACM, 2018: 1-15. |
| [21] | GAD I, ABDELKADER H, HAROUN A. Double Spending Attacks in Decentralized Digital Currencies: Challenges and Countermeasures[J]. International Journal of Computers and Information, 2023, 10(3): 142-146. |
| [22] | MASTEIKA S, REBZDYS E, DRIAUNYS K, et al. Bitcoin Double-Spending Risk and Countermeasures at Physical Retail Locations[J]. International Journal of Information Management, 2024, 79: 727-738. |
| [23] | SHI Chunhong. Information Steganalysis Based on Base64 Encoding[J]. Information and Computer (Theoretical Edition), 2020, 32(1): 118-119. |
| 石春宏. 基于Base64编码实现信息隐写分析[J]. 信息与电脑(理论版), 2020, 32(1): 118-119. | |
| [24] | TANG Wusheng, TIAN Lihong, CAO Wei. Research on Implementation and Application of Base64 Encoding[J]. Journal of Changchun University, 2006(4): 69-72. |
| 唐武生, 田立红, 曹伟. Base64编码的实现与应用研究[J]. 长春大学学报, 2006(4): 69-72. |
| [1] | 刘峰, 黄灏. 一种基于智能合约预言机技术的主动式去中心化监管传感网络架构[J]. 信息网络安全, 2025, 25(6): 898-909. |
| [2] | 叶佳骏, 高翠凤, 薛吟兴. 基于静态分析的价格预言机操纵源代码检测方法研究[J]. 信息网络安全, 2025, 25(5): 732-746. |
| [3] | 秦金磊, 康毅敏, 李整. 智能电网中轻量级细粒度的多维多子集隐私保护数据聚合[J]. 信息网络安全, 2025, 25(5): 747-757. |
| [4] | 朱晓强, 张皓文, 林彦孜, 刘吉强. 基于可信数字身份的轻量级分布式认证方案[J]. 信息网络安全, 2025, 25(5): 817-827. |
| [5] | 杨亚涛, 丁渝诚, 刘培鹤, 桑鹏. 基于区块链的隐私保护和数字认证研究[J]. 信息网络安全, 2025, 25(4): 640-653. |
| [6] | 张雨轩, 黄诚, 柳蓉, 冷涛. 结合提示词微调的智能合约漏洞检测方法[J]. 信息网络安全, 2025, 25(4): 664-673. |
| [7] | 王勇, 武一帆, 万前程. 基于中国剩余定理的可编辑区块链方案研究[J]. 信息网络安全, 2025, 25(1): 36-47. |
| [8] | 余礼苏, 李彪, 姚元志, 温家进, 黎子鹏, 王振. 区块链辅助无人机移动边缘计算系统的性能优化[J]. 信息网络安全, 2024, 24(9): 1432-1443. |
| [9] | 吕秋云, 周凌飞, 任一支, 周士飞, 盛春杰. 一种全生命周期可控的公共数据共享方案[J]. 信息网络安全, 2024, 24(8): 1291-1305. |
| [10] | 张继威, 王文俊, 牛少彰, 郭向阔. 区块链扩展解决方案:ZK-Rollup综述[J]. 信息网络安全, 2024, 24(7): 1027-1037. |
| [11] | 郭瑞, 杨鑫, 王俊茗. 基于区块链的可验证可撤销属性加密方案[J]. 信息网络安全, 2024, 24(6): 863-878. |
| [12] | 凌治, 杨明, 余江银. 基于IPFS和区块链技术的电力安全交易平台研究[J]. 信息网络安全, 2024, 24(6): 968-976. |
| [13] | 田钊, 牛亚杰, 佘维, 刘炜. 面向车联网的车辆节点信誉评估方法[J]. 信息网络安全, 2024, 24(5): 719-731. |
| [14] | 石润华, 杨婧怡, 王鹏博, 刘华伟. V2G中基于区块链的在线/离线跨域身份认证方案[J]. 信息网络安全, 2024, 24(4): 587-601. |
| [15] | 胡海洋, 刘畅, 王栋, 魏旭. 基于区块链的清洁能源数据溯源机制[J]. 信息网络安全, 2024, 24(4): 626-639. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||