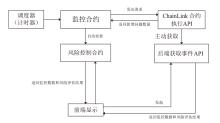
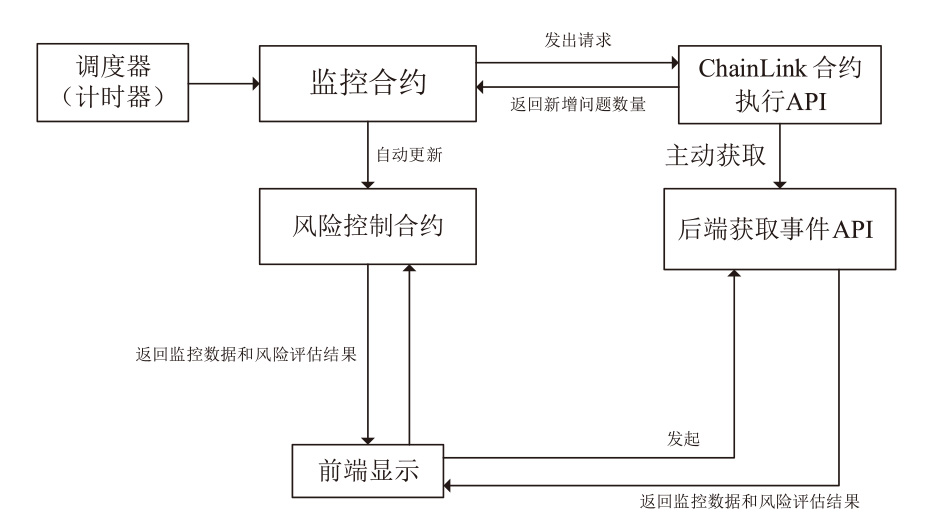
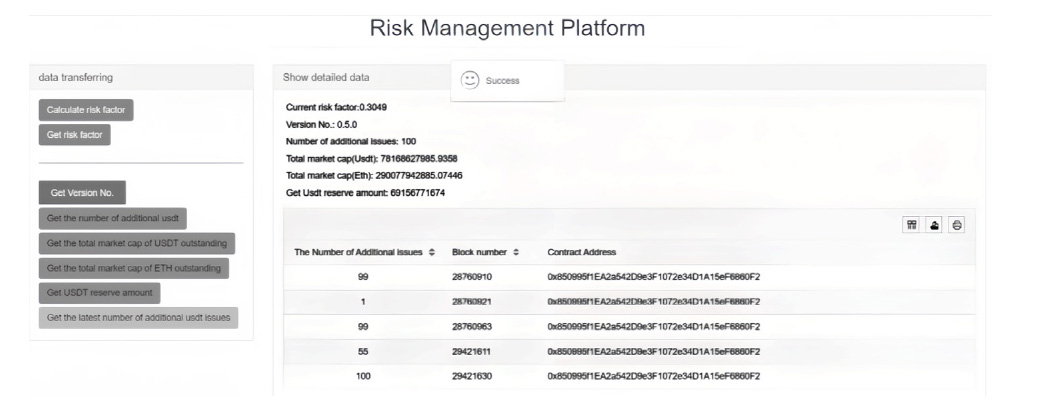
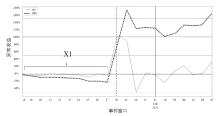
信息网络安全 ›› 2025, Vol. 25 ›› Issue (6): 898-909.doi: 10.3969/j.issn.1671-1122.2025.06.005
一种基于智能合约预言机技术的主动式去中心化监管传感网络架构
- 1.上海交通大学心理学院,上海 200030
2.华东师范大学计算机科学与技术学院,上海 200062
-
收稿日期:2025-01-21出版日期:2025-06-10发布日期:2025-07-11 -
通讯作者:刘峰 liu.feng@sjtu.edu.cn -
作者简介:刘峰(1988—),男,湖北,助理研究员,博士,CCF高级会员,主要研究方向为可计算情感、区块链技术、人工智能|黄灏(2003—),女,江苏,本科,主要研究方向为区块链技术、人工智能。 -
基金资助:国家自然科学基金(72293580)
A Decentralized Regulatory Architecture Based on Smart Contracts and Prophecy Machines with Active Sensor Networks
- 1. School of Psychology, Shanghai Jiao Tong University, Shanghai 200030, China
2. School of Computer Science and Technology, East China Normal University, Shanghai 200062, China
-
Received:2025-01-21Online:2025-06-10Published:2025-07-11
摘要:
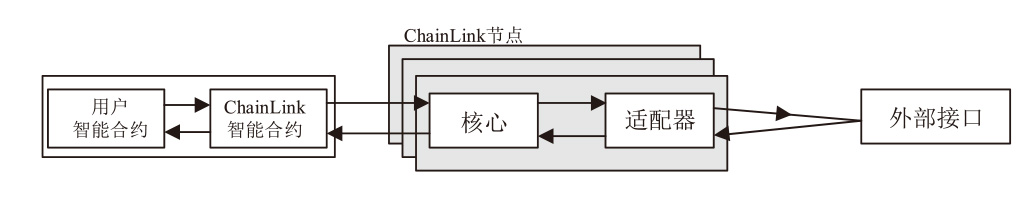
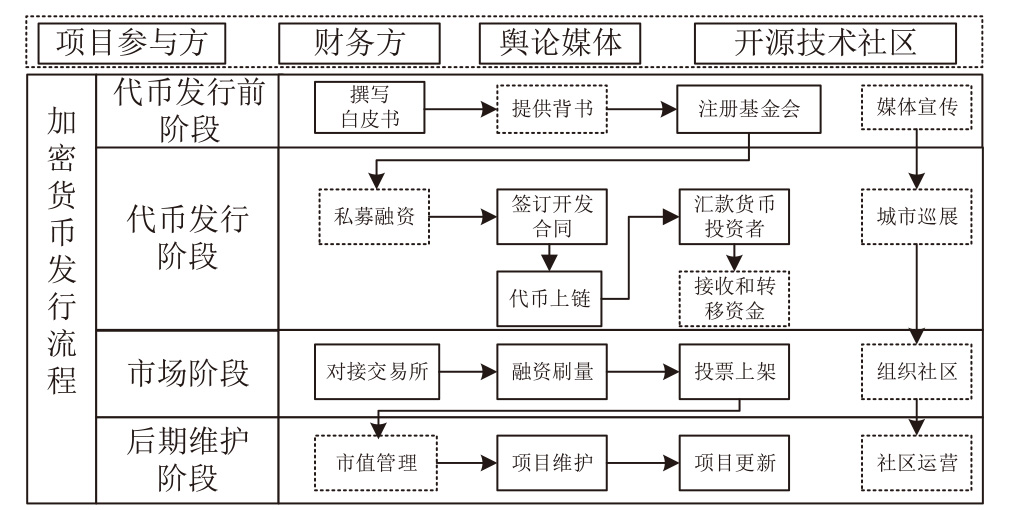
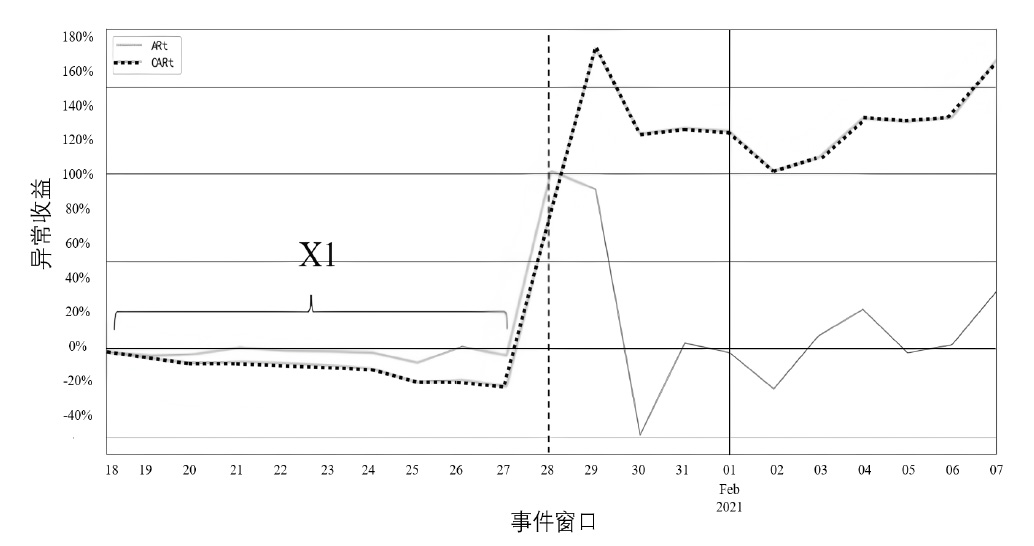
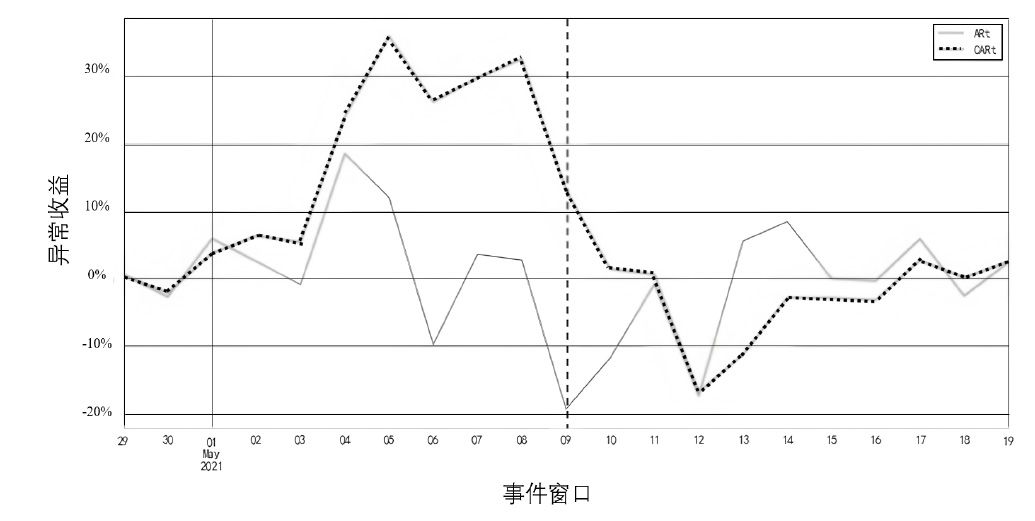
区块链在外部数据主动获取上存在短板,基于此,文章提出一种基于智能合约预言机技术的主动式去中心化监管传感网络架构(DR-ASNet),并进一步探讨了意见领袖在区块链代币经济中的影响力及其对资产价格的影响。文章采用事件分析法,以马斯克(MUSK)在社交媒体上对狗狗币(Dogecoin)的影响为例,分析意见领袖如何通过ICO影响代币资产价格。结果显示,意见领袖能利用社交网络中的资金和数据流量影响代币价格,获得超额回报。基于此,文章设计了结合智能合约与ChainLink预言机的监管框架,实现对代币发行的风险评估和预警。研究为监管机构和企业提供区块链金融产品研发思路,并为相关治理工作提供参考。
中图分类号:
引用本文
刘峰, 黄灏. 一种基于智能合约预言机技术的主动式去中心化监管传感网络架构[J]. 信息网络安全, 2025, 25(6): 898-909.
LIU Feng, HUANG Hao. A Decentralized Regulatory Architecture Based on Smart Contracts and Prophecy Machines with Active Sensor Networks[J]. Netinfo Security, 2025, 25(6): 898-909.
表2
部分意见领袖的数据统计
| 代币名称 | 相关意见 领袖 | 开始 价格 | 开始时间 | 结束 价格 | 结束 时间 | 最大 价格 | 最大 时间 |
|---|---|---|---|---|---|---|---|
| Dogecoin | MUSK(Tesla) | $0.0074 820000 | 1/27/2021 8:00AM | $0.1708 000000 | 7/20/2021 8:00AM | $0.6848 000000 | 5/7/2021 8:00AM |
| Ethereum Max | KARDA- SHIAN(Internet celebrity)、 MAYWE- ATHER(Boxing champion) | $0.0000 000024 | 5/28/2021 12:00AM | $0.0000 000772 | 6/12/2021 4:00PM | $0.0000 08546 | 5/30/2021 12:00AM |
| Constitution DAO | MUSK(Tesla) | $0.0044 000000 | 11/24/2021 8:00AM | $0.0436 100000 | 12/3/2021 8:00AM | $0.1108 000000 | 11/27/2021 8:00AM |
| TRON | Sun Chenyu(TRX) | $0.0020 850000 | 12/5/2017 8:00AM | $0.0301 600000 | 2/5/2018 8:00AM | $0.2206 000000 | 1/5/2018 8:00AM |
| Stox | SUAREZ(Footballer) | $0.9431 000000 | 8/6/2017 8:00AM | $0.4477 000000 | 9/23/2017 8:00AM | $2.5925 000000 | 8/25/2017 8:00AM |
| Squid Game | Netflix (The Squid Game) | $38.110 0000000 | 1/11/2021 1:00PM | $0.0033 990000 | 1/11/2021 5:00PM | $523.30 00000000 | 1/11/2021 4:00PM |
表2
| [1] | LIANG Xin, GUI Xiaolin, DAI Huijun, et al. Research on Cache Side-Channel Attacks Across Virtual Machines in Cloud Environment[J]. Chinese Journal of Computer, 2017, 40(2): 317-336. |
| 梁鑫, 桂小林, 戴慧珺, 等. 云环境中跨虚拟机的Cache侧信道攻击技术研究[J]. 计算机学报, 2017, 40(2): 317-336. | |
| [2] | NAKAMOTO S. Bitcoin: A Peer-to-Peer Electronic Cash System[J]. Decentralized Business Review, 2008(1): 1-9. |
| [3] | HOWELL S T, NIESSNER M, YERMACK D. Initial Coin Offerings: Financing Growth with Cryptocurrency Token Sales[J]. The Review of Financial Studies, 2020, 33(9): 3925-3974. |
| [4] | CHOHAN U W. Initial Coin Pfferings (ICOs): Risks, Regulation, and Accountability[M]. Heidelberg: Springer, 2019. |
| [5] | FISCH C, MASIAK C, VISMARA S, et al. Motives and Profiles of ICO Investors[J]. Journal of Business Research, 2021, 125: 564-576. |
| [6] | ZHONG Weiqiang, JIANG Tingfeng. Can Internet Finance Alleviate the Exclusiveness of Traditional Finance? Evidence from Chinese P2P Lending Markets[EB/OL]. (2020-08-01)[2025-01-19]. https://ideas.repec.org/a/eee/finlet/v40y2021ics1544612319308001.html. |
| [7] | LIU Feng, JIANG Jiaqi, HUANG Hao. Security Overview of Cryptocurrency Trading Media and Processes[J]. Netinfo Security, 2024, 24(3): 330-351. |
| 刘峰, 江佳齐, 黄灏. 面向加密货币交易介质及过程的安全综述[J]. 信息网络安全, 2024, 24(3): 330-351. | |
| [8] | HE Haiwu, YAN An, CHEN Zehua. A Survey on Blockchain-Based Smart Contract Technologies and Applications[J]. Journal of Computer Research and Development, 2018, 55(11): 2452-2466. |
| 贺海武, 延安, 陈泽华. 基于区块链的智能合约技术与应用综述[J]. 计算机研究与发展, 2018, 55(11): 2452-2466. | |
| [9] | AFJAL M. Bridging the Financial Divide: A Bibliometric Analysis on the Role of Digital Financial Services within Fintech in Enhancing Financial Inclusion and Economic Development[J]. Humanities and Social Sciences Communications, 2023, 10(1): 1-27. |
| [10] | HU Tianyuan, LI Zecheng, LI Bixin, et al. A Review of Smart Contract Security and Privacy Protection[J]. Chinese Journal of Computer, 2021, 44(12): 2485-2514. |
| 胡甜媛, 李泽成, 李必信, 等. 智能合约的合约安全和隐私安全研究综述[J]. 计算机学报, 2021, 44(12): 2485-2514. | |
| [11] | BENIICHE A. A Study of Blockchain Oracles[EB/OL]. (2020-04-15)[2024-07-19]. https://arxiv.org/abs/2004.07140. |
| [12] | LIU Feng, YANG Jie, QI Jiayin. Two-Party ECDS for Blockchain Based on Hash Proof Systems[J]. Netinfo Security, 2021, 21(1): 19-26. |
| 刘峰, 杨杰, 齐佳音. 基于哈希证明系统的区块链两方椭圆曲线数字签名算法研究[J]. 信息网络安全, 2021, 21(1): 19-26. | |
| [13] | LIU Feng, YANG Jie, QI Jiayin. A Review on Cryptographic Privacy Protection Technologies in Blockchain[J]. Journal of Cybersecurity and Information Security, 2022, 8(4): 29-44. |
| [14] | LIU Feng, YANG Jie, LI Zhibin, et al. A General Privacy-Preserving MPC Protocol Based on Blockchain[J]. Journal of Computer Research and Development, 2021, 58(2): 281-290. |
| 刘峰, 杨杰, 李志斌, 等. 一种基于区块链的泛用型数据隐私保护的安全多方计算协议[J]. 计算机研究与发展, 2021, 58(2): 281-290. | |
| [15] | WANG Shuai, YUAN Yong, WANG Xiao, et al. An Overview of Smart Contract: Architecture, Applications, and Future Trends[C]// IEEE. 2018 IEEE Intelligent Vehicles Symposium. New York: IEEE, 2018: 108-113. |
| [16] | BUTERIN V. A Next-Generation Smart Contract and Decentralized Application Platform[EB/OL]. (2014-11-06)[2025-01-03]. https://ethereum.org/en/whitepaper/. |
| [17] |
BI Dingyu, ZHANG Yuwen, BI Yongqi. Trusted Data Feed Technology based on Oracle[J]. Information and Communications Technology and Policy, 2021, 47(9): 79-84.
doi: 10.12267/j.issn.2096-5931.2021.09.013 |
| 毕丁宇, 张玉文, 毕永琪. 基于预言机的可信数据源技术[J]. 信息通信技术与政策, 2021, 47(9): 79-84. | |
| [18] | YUE C A, CHUNG Y J, KELLEHER T, et al. How CEO Social Media Disclosure and Gender Affect Perceived CEO Attributes, Relationship Investment, and Engagement Intention[J]. Journalism & Mass Communication Quarterly, 2021, 98(4): 1157-1180. |
| [19] | KATZ E, LAZARSFELD P F. Personal Influence: The Part Played by People in the Flow of Mass Communications[M]. New York: Free Press, 1955. |
| [20] | SHILLER R J. Irrational Exuberance[M]. Princeton: Princeton University Press, 2015. |
| [21] | VARCHEV FINANCE. The FOMO Effect on Dogecoin: How Fear of Missing Out Drives the Price[N]. Varchev Finance, 2024-11-29(5). |
| [22] | Securities and Exchange Commission. SEC Charges Kim Kardashian for Unlawfully Touting Crypto Security[R]. Washington, D.C.: Securities and Exchange Commission, SEC Press Release No. 2022-183, 2022. |
| [23] | FISCH C, MASIAK C, VISMARA S, et al. Motives and Profiles of ICO Investors[J]. Journal of Business Research, 2021, 125: 564-576. |
| [24] | XU Kunpeng, LIU Feng, QI Jiayin. Vulnerability of Cryptocurrency Markets: A Study of the Relationship between High-impact Users and Bitcoin Market Price Volatility[EB/OL]. (2022-03-02)[2025-01-03]. https://www.atlantis-press.com/proceedings/icbbem-22/125979207. |
| [25] | Securities and Exchange Commission. Floyd Mayweather Jr. and DJ Khaled Settle Charges over ICO Promotions[EB/OL]. (2018-11-29) [2025-01-03]. https://www.sec.gov/news/press-release/2018-268. |
| [26] | ELENDNER H, TRIMBORN S, ONG B, et al. The Cross-Section of Crypto-Currencies as Financial Assets: An Overview[EB/OL]. (2016-10-09)[2025-01-03]. https://www.semanticscholar.org/paper/The-Cross-Section-of-Crypto-Currencies-as-Financial-Elendner-Trimborn/10cf312dcfecdfe3dac42a31945ed1357cd894d7. |
| [27] | ROZMAN N, DIACI J, CORN M. Scalable framework for blockchain- based shared manufacturing[EB/OL]. (2021-06-05)[2025-01-03]. https://doi.org/10.1016/j.rcim.2021.102139. |
| [28] | BIHARI A, DASH M, KAR S K, et al. Exploring Behavioural Bias Affecting Investment Decision-Making: A Network Cluster Based Conceptual Analysis for Future Research[J]. International Journal of Industrial Engineering and Operations Management, 2022, 4(1/2): 19-43. |
| [1] | 叶佳骏, 高翠凤, 薛吟兴. 基于静态分析的价格预言机操纵源代码检测方法研究[J]. 信息网络安全, 2025, 25(5): 732-746. |
| [2] | 秦金磊, 康毅敏, 李整. 智能电网中轻量级细粒度的多维多子集隐私保护数据聚合[J]. 信息网络安全, 2025, 25(5): 747-757. |
| [3] | 朱晓强, 张皓文, 林彦孜, 刘吉强. 基于可信数字身份的轻量级分布式认证方案[J]. 信息网络安全, 2025, 25(5): 817-827. |
| [4] | 杨亚涛, 丁渝诚, 刘培鹤, 桑鹏. 基于区块链的隐私保护和数字认证研究[J]. 信息网络安全, 2025, 25(4): 640-653. |
| [5] | 张雨轩, 黄诚, 柳蓉, 冷涛. 结合提示词微调的智能合约漏洞检测方法[J]. 信息网络安全, 2025, 25(4): 664-673. |
| [6] | 王勇, 武一帆, 万前程. 基于中国剩余定理的可编辑区块链方案研究[J]. 信息网络安全, 2025, 25(1): 36-47. |
| [7] | 余礼苏, 李彪, 姚元志, 温家进, 黎子鹏, 王振. 区块链辅助无人机移动边缘计算系统的性能优化[J]. 信息网络安全, 2024, 24(9): 1432-1443. |
| [8] | 吕秋云, 周凌飞, 任一支, 周士飞, 盛春杰. 一种全生命周期可控的公共数据共享方案[J]. 信息网络安全, 2024, 24(8): 1291-1305. |
| [9] | 张继威, 王文俊, 牛少彰, 郭向阔. 区块链扩展解决方案:ZK-Rollup综述[J]. 信息网络安全, 2024, 24(7): 1027-1037. |
| [10] | 张立强, 路梦君, 严飞. 一种基于函数依赖的跨合约模糊测试方案[J]. 信息网络安全, 2024, 24(7): 1038-1049. |
| [11] | 郭瑞, 杨鑫, 王俊茗. 基于区块链的可验证可撤销属性加密方案[J]. 信息网络安全, 2024, 24(6): 863-878. |
| [12] | 凌治, 杨明, 余江银. 基于IPFS和区块链技术的电力安全交易平台研究[J]. 信息网络安全, 2024, 24(6): 968-976. |
| [13] | 田钊, 牛亚杰, 佘维, 刘炜. 面向车联网的车辆节点信誉评估方法[J]. 信息网络安全, 2024, 24(5): 719-731. |
| [14] | 石润华, 杨婧怡, 王鹏博, 刘华伟. V2G中基于区块链的在线/离线跨域身份认证方案[J]. 信息网络安全, 2024, 24(4): 587-601. |
| [15] | 胡海洋, 刘畅, 王栋, 魏旭. 基于区块链的清洁能源数据溯源机制[J]. 信息网络安全, 2024, 24(4): 626-639. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||