信息网络安全 ›› 2025, Vol. 25 ›› Issue (1): 98-109.doi: 10.3969/j.issn.1671-1122.2025.01.009
基于多权威属性基加密的智能电网数据安全共享模型
- 西南交通大学计算机与人工智能学院,成都 611756
-
收稿日期:2024-09-15出版日期:2025-01-10发布日期:2025-02-14 -
通讯作者:刘庆夫 E-mail:qfliu_caly@163.com -
作者简介:张新有(1971—),男,河南,副教授,博士,主要研究方向为分布式计算与应用、网络安全|刘庆夫(2001—),男,山东,硕士研究生,主要研究方向为区块链和网络信息安全|冯力(1974—),男,四川,教授,博士,主要研究方向为人工智能和网络安全|邢焕来(1984—),男,河北,副教授,博士,CCF 会员,主要研究方向为人工智能和网络安全 -
基金资助:国家自然科学基金(62172342)
Smart Grid Data Security Sharing Model Based on Multi-Authority Attribute-Based Encryption
ZHANG Xinyou, LIU Qingfu( ), FENG Li, XING Huanlai
), FENG Li, XING Huanlai
- School of Computing and Artificial Intelligence, Southwest Jiaotong University, Chengdu 611756, China
-
Received:2024-09-15Online:2025-01-10Published:2025-02-14 -
Contact:LIU Qingfu E-mail:qfliu_caly@163.com
摘要:
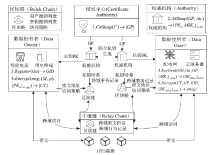
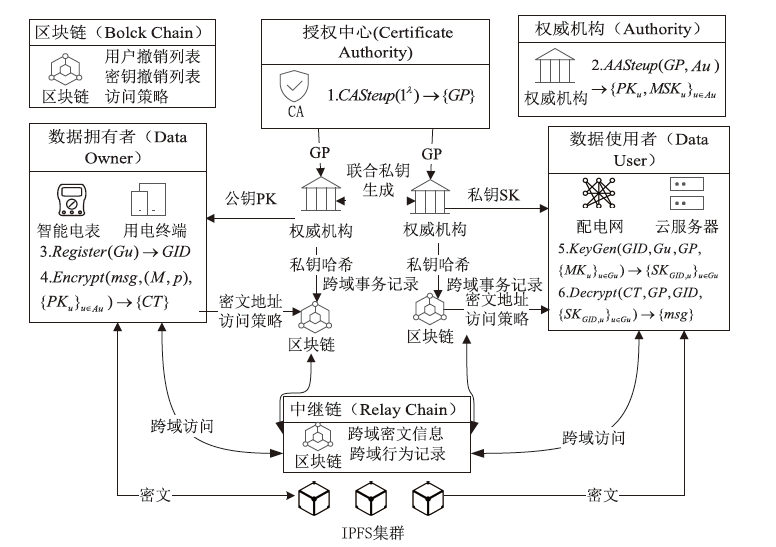
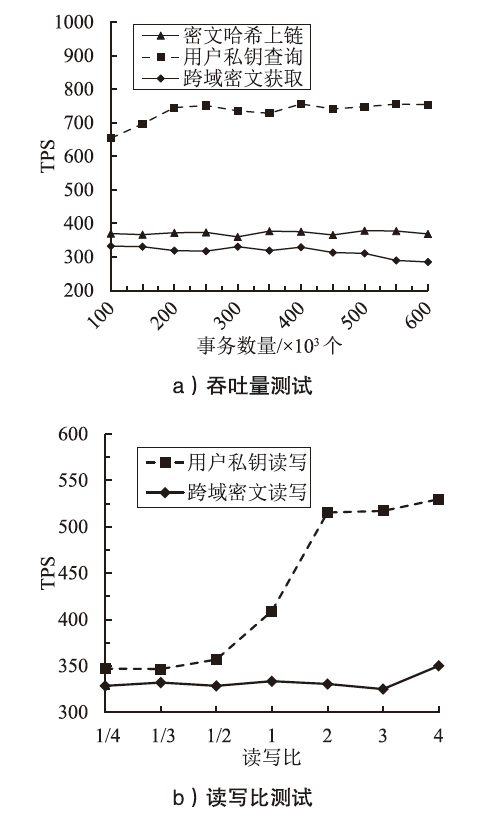
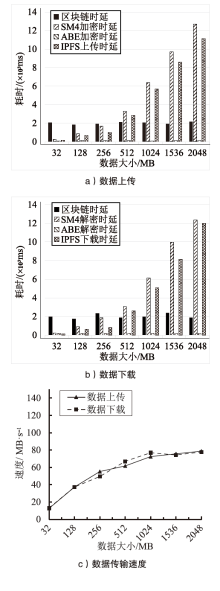
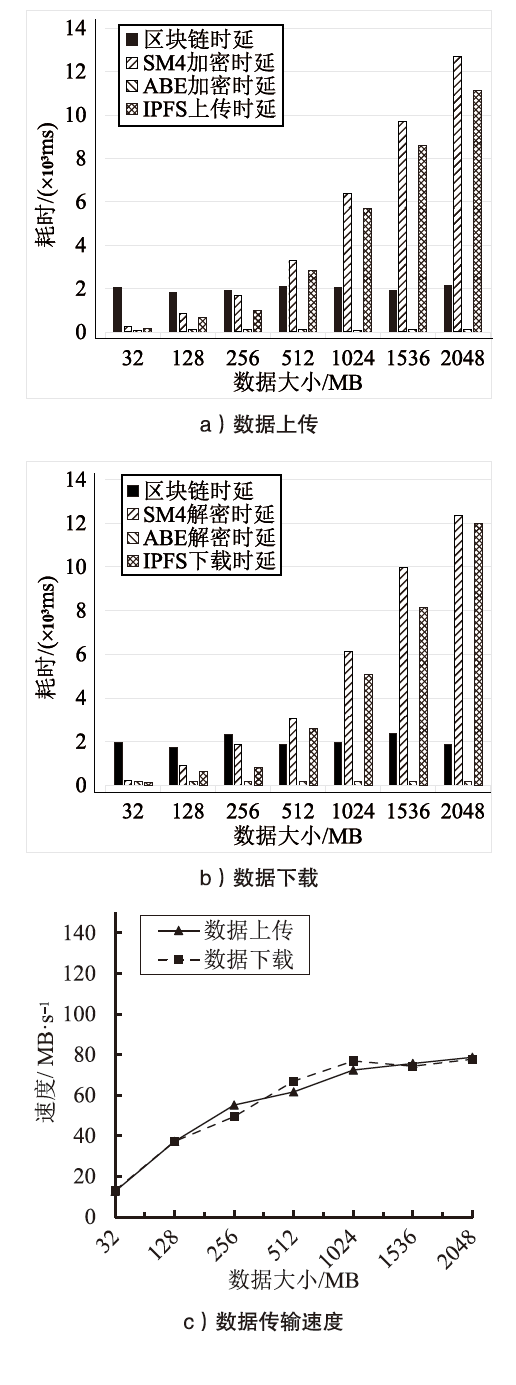
智能电网通过共享把数据的潜在价值转化为实际利益,因此保障数据共享的安全至关重要。文章面向智能电网场景中数据的细粒度访问控制,提出一种基于多权威属性基加密(MA-ABE)的数据安全共享模型。文章使用线性整数秘密共享方案(LSSS)构建MA-ABE方案,实现一个属性可被多个权威监控,多个权威可联合生成用户私钥,使得方案可抵抗针对属性权威机构(AA)的合谋攻击。将每个权威与一条区块链关联,并利用中继技术实现多链协同,保障数据跨域共享灵活性。通过安全规约证明了所提MA-ABE方案在基于判定性双线Diffie-Hellman假设的前提下满足选择明文攻击下的不可区分性(IND-CPA)安全性。文章通过理论分析和对比实验说明了MA-ABE方案在存储、计算以及功能性方面均有一定的优势。仿真结果表明,模型的吞吐量和时延满足了智能电网数据共享的需求,能够在保证智能电网数据共享性能的情况下,适用于智能电网的细粒度访问控制。
中图分类号:
引用本文
张新有, 刘庆夫, 冯力, 邢焕来. 基于多权威属性基加密的智能电网数据安全共享模型[J]. 信息网络安全, 2025, 25(1): 98-109.
ZHANG Xinyou, LIU Qingfu, FENG Li, XING Huanlai. Smart Grid Data Security Sharing Model Based on Multi-Authority Attribute-Based Encryption[J]. Netinfo Security, 2025, 25(1): 98-109.
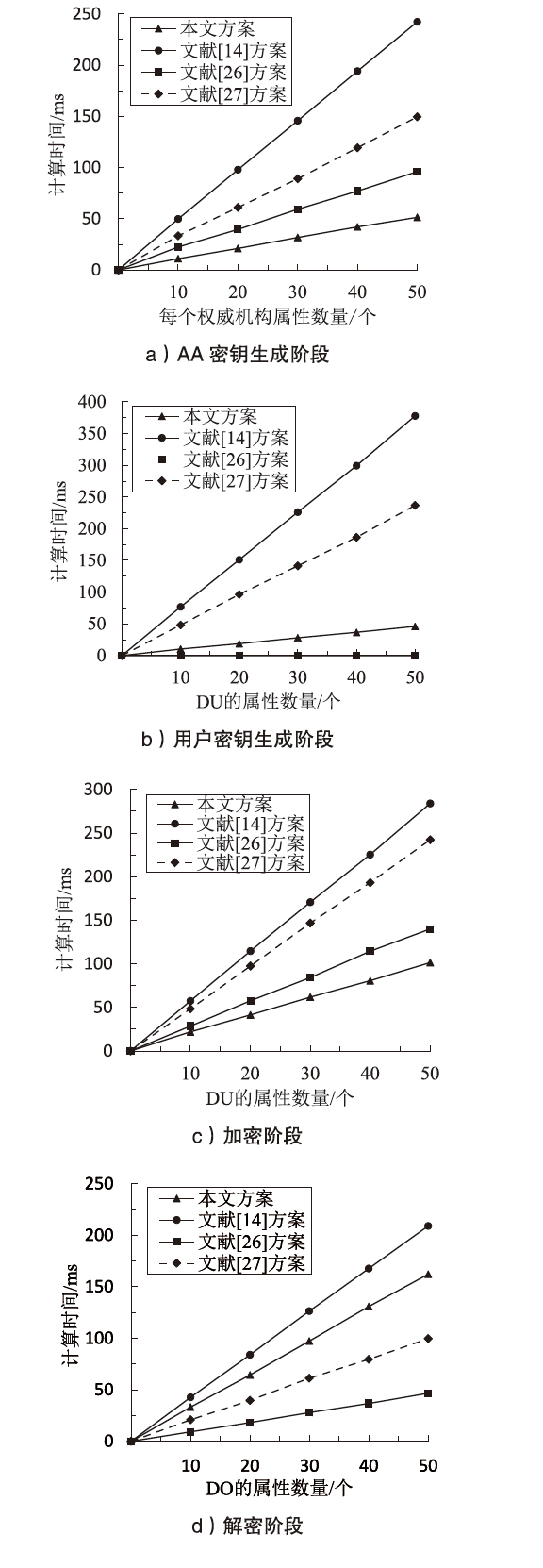
表5
不同方案的计算开销比较
| 方案 | AA密钥 生成开销 | 用户密钥 生成开销 | DO加密开销 | DU解密开销 |
|---|---|---|---|---|
| 本文 方案 | UExp+UMap | 2GUExp+ GUMul+ UHash | (1+2GU)+(2Exp+ Mul)+Map | GU(2Map+Exp)+ (1+2GU)Mul |
| 文献[ 方案 | SmaxUExp+ AUMap | GUSmax(Exp+ Mul)-GUMul | GUSmaxMul+(1+ GU(2Smax+ 3))Exp+Map | (2GU+1)Mul+GuExp+ GuSmaxMap |
| 文献[ 方案 | (2AU+U)Exp+ UHash | — | (GU+AU)Mul+ (4GU+1)Exp | (AU+GU+1)Exp+ (2GU+1)Mul) |
| 文献[ 方案 | UMul+(2U+ 3AU)Exp+ Map+UHash | (AU+GU)Mul+ (3AU+3GU)Exp+ GUHash | (AU+GU)Mul+ (AU+4GU+3)Exp+ GUMap+GUHash | (2GU+AU+1)Mul+ (GU+1)Exp+(AU+ 4GU)Map |
| [1] | POWELL J, MCCAFFERTY-LEROUX A, HILAL W, et al. Smart Grids: A Comprehensive Survey of Challenges, Industry Applications, and Future Trends[J]. Energy Reports, 2024, 11: 5760-5785. |
| [2] | QIN Sihang, DAI Weiqi, ZENG Haiyan, et al. Secure Sharing of Power Application Data Based on Blockchain[J]. Netinfo Security, 2023, 23(8): 52-65. |
| 覃思航, 代炜琦, 曾海燕, 等. 基于区块链的电力应用数据安全共享研究[J]. 信息网络安全, 2023, 23(8): 52-65. | |
| [3] | ZHANG Ming, LIU Yutong, CHENG Qian, et al. Smart Grid Security Based on Blockchain and Smart Contract[J]. Peer-to-Peer Networking and Applications, 2024, 17(4): 2167-2184. |
| [4] | MOLLAH M B, ZHAO Jun, NIYATO D, et al. Blockchain for Future Smart Grid: A Comprehensive Survey[J]. IEEE Internet of Things Journal, 2021, 8(1): 18-43. |
| [5] | CHEN Ningyu, LI Jiguo, ZHANG Yichen, et al. Efficient CP-ABE Scheme with Shared Decryption in Cloud Storage[J]. IEEE Transactions on Computers, 2022, 71(1): 175-184. |
| [6] | MU Tianshi, LAI Yuyang, FENG Guocong, et al. A User-Friendly Attribute-Based Data Access Control Scheme for Smart Grids[J]. Alexandria Engineering Journal, 2023, 67: 209-217. |
| [7] |
YANG Wenti, GUAN Zhitao, WU Longfei, et al. Secure Data Access Control with Fair Accountability in Smart Grid Data Sharing: An Edge Blockchain Approach[J]. IEEE Internet of Things Journal, 2021, 8(10): 8632-8643.
doi: 10.1109/JIOT.2020.3047640 |
| [8] | XIA Zhe, LUO Bin, XU Guibin, et al. Privacy-Preserving Data Aggregation with Fine Grained Access Control for Smart Grid[J]. Netinfo Security, 2021, 21(11): 28-39. |
| 夏喆, 罗宾, 徐桂彬, 等. 智能电网中支持细粒度访问控制的隐私保护数据聚合方案[J]. 信息网络安全, 2021, 21(11): 28-39. | |
| [9] | SAHAI A, WATERS B. Fuzzy Identity-Based Encryption[C]// Springer. Proceedings of the 24th Annual International Conference on Theory and Applications of Cryptographic Techniques. Heidelberg: Springer, 2005: 457-473. |
| [10] | ZHOU Zhibin, HUANG Dijiang, WANG Zhijie. Efficient Privacy-Preserving Ciphertext-Policy Attribute Based-Encryption and Broadcast Encryption[J]. IEEE Transactions on Computers, 2015, 64(1): 126-138. |
| [11] | YANG Dan, WAGN Baocang, BAN Xuehua. Fully Secure Non-Monotonic Access Structure CP-ABE Scheme[J]. KSII Transactions on Internet and Information Systems, 2018, 12(3): 1315-1329. |
| [12] |
DING Sheng, CAO Jin, LI Hui. Efficient Pairing-Free CP-ABE Based on Ordered Binary Decision Diagram[J]. Journal on Communications, 2019, 40(12): 1-8.
doi: 10.11959/j.issn.1000-436x.2019234 |
|
丁晟, 曹进, 李晖. 基于OBDD访问结构的无配对CP-ABE方案[J]. 通信学报, 2019, 40(12): 1-8.
doi: 10.11959/j.issn.1000-436x.2019234 |
|
| [13] | LEWKO A, WATERS B. Decentralizing Attribute-Based Encryption[C]// Springer. Proceedings of the 24th Annual International Conference on the Theory and Applications of Cryptographic Techniques. Heidelberg: Springer, 2011: 568-588. |
| [14] | DATTA P, KOMARGODSKI I, WATERS B. Decentralized Multi-Authority ABE for NC^1 from BDH[J]. Journal of Cryptology, 2023, 36(2): 1432-1378. |
| [15] | SUN Keshuo, GAO Haiying, SONG Yang. Multi-Authority Attribute-Based Encryption Scheme for Private Blockchain over Public Blockchain[EB/OL]. (2024-03-04)[2024-05-08]. http://kns.cnki.net/kcms/detail/51.1307.TP.20240229.1614.006.html. |
| 孙科硕, 高海英, 宋杨. 面向公有区块链上的私有区块链的多权威属性加密方案[EB/OL]. (2024-03-04)[2024-05-08]. http://kns.cnki.net/kcms/detail/51.1307.TP.20240229.1614.006.html. | |
| [16] | CHRISTIDIS K, DEVETSIKIOTIS M. Blockchains and Smart Contracts for the Internet of Things[J]. IEEE Access, 2016, 4: 2292-2303. |
| [17] | ZHENG Hui, SHAO Jun, WEI Guiyi. Attribute-Based Encryption with Outsourced Decryption in Blockchain[J]. Peer-to-Peer Networking and Applications, 2020, 13(5): 1643-1655. |
| [18] | LI Jian, QI Yong. Blockchain Data Access Control Method with Revocable Attribute Encryption[J]. Computer Engineering and Design, 2024, 45(2): 348-355. |
| 李健, 戚湧. 可撤销属性加密的区块链数据访问控制方法[J]. 计算机工程与设计, 2024, 45(2): 348-355. | |
| [19] | MENG Bo, WANG Yibing, ZHAO Can, et al. Survey on Crosschain Protocols of Blockchain[J]. Journal of Frontiers of Computer Science and Technology, 2022, 16(10): 2177-2192. |
| [20] | BEIMEL A. Secure Schemes for Secret Sharing and Key Distribution[D]. Haifa: Technion-Israel Institute of Technology, 1996. |
| [21] | GENCER A E, BASU S, EYAL I, et al. Decentralization in Bitcoin and Ethereum Networks[EB/OL]. (2018-01-11)[2024-05-08]. https://arxiv.org/abs/1801.03998v2. |
| [22] | YU Keping, TAN Liang, ALOQAILY M, et al. Blockchain-Enhanced Data Sharing with Traceable and Direct Revocation in IIoT[J]. IEEE Transactions on Industrial Informatics, 2021, 17(11): 7669-7678. |
| [23] | WATERS B. Ciphertext-Policy Attribute-Based Encryption:An Expressive, and Provably Secure Realization[C]// Springer. Lecture Notes in Computer Science. Heidelberg: Springer, 2011: 53-70. |
| [24] | ZHENG Zibin, XIE Shaoan, DAI Hongning, et al. An Overview on Smart Contracts: Challenges, Advances and Platforms[J]. Future Generation Computer Systems, 2020, 105: 475-491. |
| [25] | LING Zhi, YANG Ming, YU Jiangyin,. Research on Power Security Trading Platform Based on IPFS and Blockchain Technology[J]. Netinfo Security, 2024, 24(6): 968-976. |
| 凌治, 杨明, 余江银. 基于IPFS和区块链技术的电力安全交易平台研究[J]. 信息网络安全, 2024, 24(6): 968-976. | |
| [26] | MING Yang, HE Baokang, WANG Chenhao. Efficient Revocable Multi-Authority Attribute-Based Encryption for Cloud Storage[J]. IEEE Access, 2021, 9: 42593-42603. |
| [27] |
MING Yang, HE Baokang. Attribute Revocation and Verifiable Outsourcing Supported Multi-Authority Attribute-Based Encryption Scheme[J]. Journal of Computer Applications, 2019, 39(12): 3556-3562.
doi: 10.11772/j.issn.1001-9081.2019061019 |
|
明洋, 何宝康. 支持属性撤销的可验证外包的多授权属性加密方案[J]. 计算机应用, 2019, 39(12): 3556-3562.
doi: 10.11772/j.issn.1001-9081.2019061019 |
|
| [28] | BUTERIN V. Ethereum: A Next-Generation Smart Contract and Decentralized Application Platform[EB/OL]. [2024-05-08]. https://blockchainlab.com/pdf/Ethereum_white_paper-a_next_generation_smart_contract_and_decentralized_application_platform-vitalik-buterin.pdf. |
| [29] | CHOI W, HONG J W K. Performance Evaluation of Ethereum Private and Testnet Networks Using Hyperledger Caliper[C]// IEEE. 2021 the 22nd Asia-Pacific Network Operations and Management Symposium (APNOMS). New York: IEEE, 2021: 325-329. |
| [30] | GUO Zhenzhen, WANG Gaoli, DUNKELMAN O, et al. Tweakable SM4: How to Tweak SM4 into Tweakable Block Ciphers?[EB/OL]. (2022-10-20)[2024-05-08]. https://doi.org/10.1016/j.jisa.2022.103406. |
| [1] | 吕秋云, 周凌飞, 任一支, 周士飞, 盛春杰. 一种全生命周期可控的公共数据共享方案[J]. 信息网络安全, 2024, 24(8): 1291-1305. |
| [2] | 郭瑞, 杨鑫, 王俊茗. 基于区块链的可验证可撤销属性加密方案[J]. 信息网络安全, 2024, 24(6): 863-878. |
| [3] | 王巍, 胡永涛, 刘清涛, 王凯崙. 铁路运行环境下ERT可信根实体的软件化技术研究[J]. 信息网络安全, 2024, 24(5): 794-801. |
| [4] | 周权, 陈民辉, 卫凯俊, 郑玉龙. 基于SM9的属性加密的区块链访问控制方案[J]. 信息网络安全, 2023, 23(9): 37-46. |
| [5] | 覃思航, 代炜琦, 曾海燕, 顾显俊. 基于区块链的电力应用数据安全共享研究[J]. 信息网络安全, 2023, 23(8): 52-65. |
| [6] | 石润华, 谢晨露. 云边缘环境中基于属性加密的可验证EMR外包解决方案[J]. 信息网络安全, 2023, 23(7): 9-21. |
| [7] | 张晓旭, 石润华. EHR系统中一种验证外包加密数据正确性的访问控制方案[J]. 信息网络安全, 2023, 23(5): 85-94. |
| [8] | 刘长杰, 石润华. 基于安全高效联邦学习的智能电网入侵检测模型[J]. 信息网络安全, 2023, 23(4): 90-101. |
| [9] | 朱怡昕, 苗张旺, 甘静鸿, 马存庆. 基于细粒度访问控制的勒索软件防御系统设计[J]. 信息网络安全, 2023, 23(10): 31-38. |
| [10] | 金志刚, 刘凯, 武晓栋. 智能电网AMI领域IDS研究综述[J]. 信息网络安全, 2023, 23(1): 1-8. |
| [11] | 王健, 黄俊. 基于智能合约的日志安全存储与公平访问方法[J]. 信息网络安全, 2022, 22(7): 27-36. |
| [12] | 于克辰, 郭莉, 阴宏伟, 燕雪松. 面向数据中心场景的基于区块链与博弈论的高价值数据共享模型[J]. 信息网络安全, 2022, 22(6): 73-85. |
| [13] | 郭宝霞, 王佳慧, 马利民, 张伟. 基于零信任的敏感数据动态访问控制模型研究[J]. 信息网络安全, 2022, 22(6): 86-93. |
| [14] | 刘嘉微, 马兆丰, 王姝爽, 罗守山. 基于区块链的隐私信用数据受限共享技术研究[J]. 信息网络安全, 2022, 22(5): 54-63. |
| [15] | 冯景瑜, 时翌飞, 王腾. 智能电网中抗主次合谋攻击的群智频谱感知加固方案[J]. 信息网络安全, 2022, 22(3): 1-9. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||