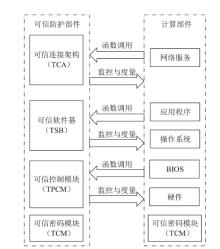
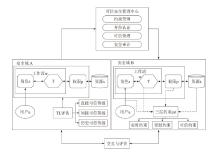
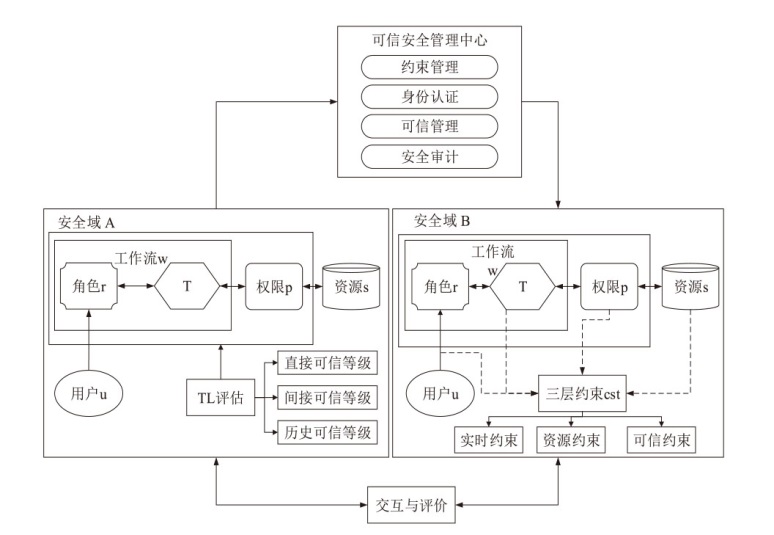
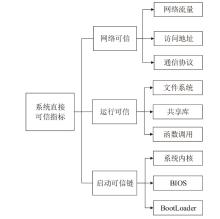
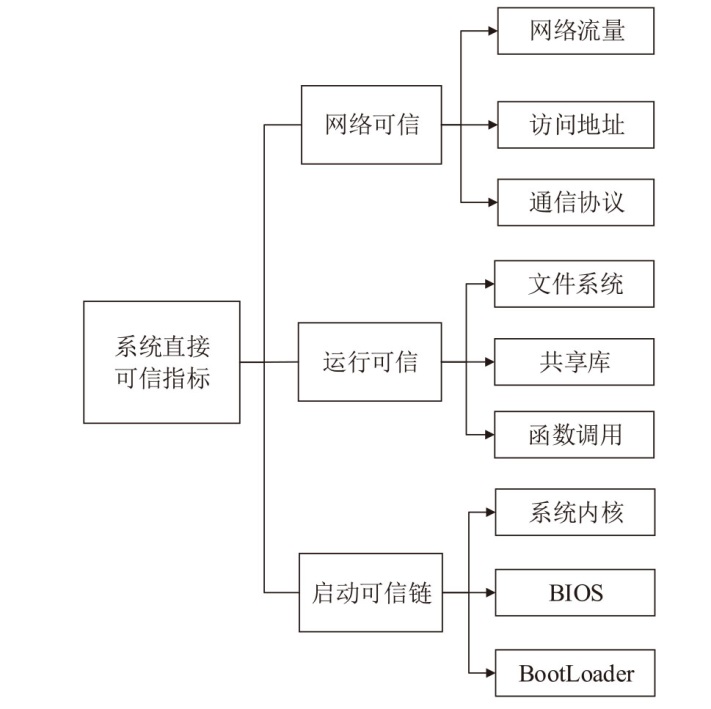
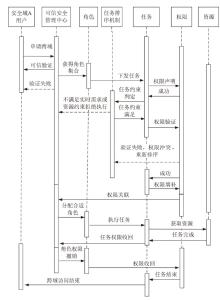
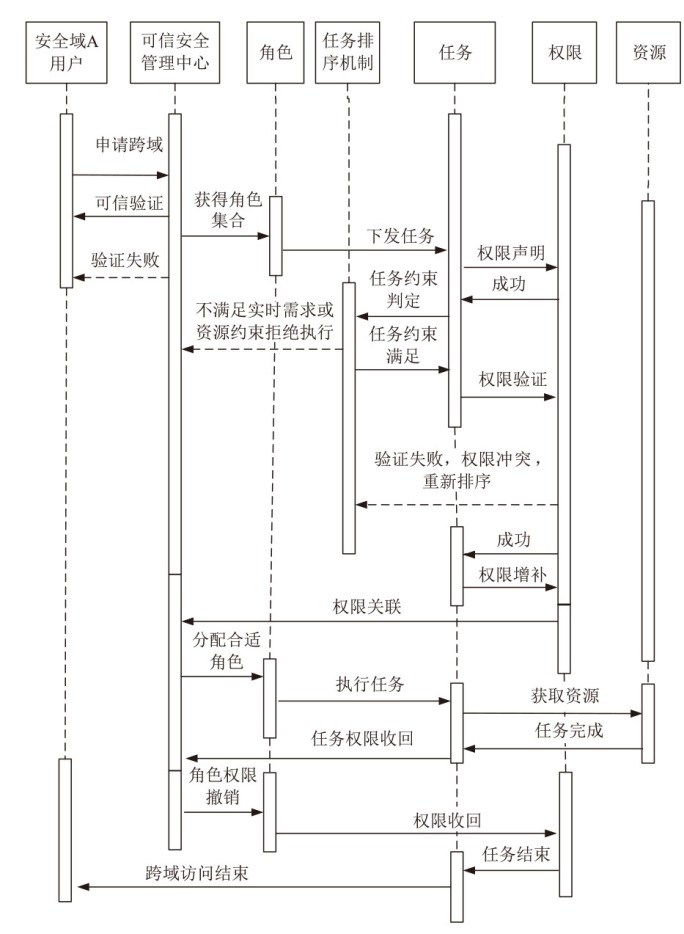
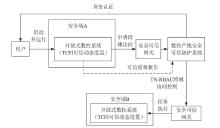
| [1] |
DONG Yue, WANG Ji, LI Yi. Network Security Threats and Protection of CNC Machine in the Industrial Internet[J]. Automation Panorama, 2022, 39(9): 32-35.
|
|
董悦, 王吉, 李艺. 工业互联网场景下数控机床网络安全威胁与防护[J]. 自动化博览, 2022, 39(9): 32-35.
|
| [2] |
XIA Xiaofeng, XIANG Hong, XIAO Zhenyu, et al. Research and Security Evaluation of AUTH-VRF Model for NCS Network Based on Domestic Cryptographic Algorithms[J]. Journal of Electronics & Information Technology, 2020, 42(8): 1846-1852.
|
|
夏晓峰, 向宏, 肖震宇, 等. 基于国产密码算法的数控网络的认证与验证方法研究及安全评估[J]. 电子与信息学报, 2020, 42(8): 1846-1852.
|
| [3] |
ISO/IEC 18028-3 Information Technology Security Techniques. IT Network Security Part 3: Securing Communications Between Networks Using Security Gateways[S]. Switzerland: ISO/IEC, 2005.
|
| [4] |
SHAHRAKI A S, RUDOLPH C, GROBLER M. A Dynamic Access Control Policy Model for Sharing of Healthcare Data in Multiple Domains[C]// IEEE. 2019 18th IEEE International Conference on Trust, Security And Privacy in Computing and Communications/13th IEEE International Conference on Big Data Science and Engineering. New York: IEEE, 2019: 618-625.
|
| [5] |
BAI Wei, PAN Zhisong, GUO Shize, et al. RMMDI: A Novel Framework for Role Mining Based on the Multi-Domain Information[J]. Security and Communication Networks, 2019(1): 1-15.
|
| [6] |
FENG Chaosheng, LIU Bin, GUO Zhen, et al. Blockchain-Based Cross-Domain Authentication for Intelligent 5G-Enabled Internet of Drones[J]. IEEE Internet of Things Journal, 2022, 9(8): 6224-6238.
|
| [7] |
WANG Miaomiao, RUI Lanlan, YANG Yang, et al. A Blockchain-Based Multi-CA Cross-Domain Authentication Scheme in Decentralized Autonomous Network[J]. IEEE Transactions on Network and Service Management, 2022, 19(3): 2664-2676.
|
| [8] |
SHEN Meng, LIU Huisen, ZHU Liehuang, et al. Blockchain-Assisted Secure Device Authentication for Cross-Domain Industrial IoT[J]. IEEE Journal on Selected Areas in Communications, 2020, 38(5): 942-954.
|
| [9] |
RAO K R, NAYAK A, RAY I G, et al. Role Recommender-RBAC: Optimizing User-Role Assignments in RBAC[J]. Computer Communications, 2021, 166: 140-153.
|
| [10] |
CHEN H C. Collaboration IoT-Based RBAC with Trust Evaluation Algorithm Model for Massive IoT Integrated Application[J]. Mobile Networks and Applications, 2019, 24(3): 839-852.
|
| [11] |
YANG Yuhan, WEI Lijun, WU Jing, et al. A Blockchain-Based Multidomain Authentication Scheme for Conditional Privacy Preserving in Vehicular Ad-Hoc Network[J]. IEEE Internet of Things Journal, 2022, 9(11): 8078-8090.
|
| [12] |
GUPTA M, SANDHU R, MAWLA T, et al. Reachability Analysis for Attributes in ABAC with Group Hierarchy[J]. IEEE Transactions on Dependable and Secure Computing, 2022, 20(1): 841-858.
|
| [13] |
KIM H, KIM D K, ALAERJAN A. ABAC-Based Security Model for DDS[J]. IEEE Transactions on Dependable and Secure Computing, 2022, 19: 3113-3124.
|
| [14] |
SHIH D H, WU Tingwei, SHILH M H, et al. Hyperledger Fabric Access Control for Industrial Internet of Things[EB/OL]. (2022-01-30)[2024-04-12]. https://www.mdpi.com/2076-3417/12/6/3125.
|
| [15] |
ZHANG Yuanyu, YUTAKA M, SASABE M, et al. Attribute-Based Access Control for Smart Cities: A Smart-Contract-Driven Framework[J]. IEEE Internet of Things Journal, 2021, 8(8): 6372-6384.
|
| [16] |
SHEN Changxiang, TIAN Nan. According to “DJCP 2.0”, the Network Security Defense Line of “New Infrastructure” is Built with Active Immunity and Trusted Computing[J]. Information Security and Communication Confidentiality, 2020(10): 2-9.
|
|
沈昌祥, 田楠. 按“等保2.0”用主动免疫可信计算筑牢“新基建”网络安全防线[J]. 信息安全与通信保密, 2020(10): 2-9.
|
 ), DONG Zeyang1,2, HAN Wenjun1,2
), DONG Zeyang1,2, HAN Wenjun1,2