信息网络安全 ›› 2024, Vol. 24 ›› Issue (4): 491-508.doi: 10.3969/j.issn.1671-1122.2024.04.001
基于半监督学习的网络异常检测研究综述
张浩1,2( ), 谢大智1,2, 胡云晟1,2, 叶骏威1,2
), 谢大智1,2, 胡云晟1,2, 叶骏威1,2
- 1.福州大学计算机与大数据学院,福州 350116
2.福建省网络计算与智能信息处理重点实验室,福州 350116
-
收稿日期:2023-10-26出版日期:2024-04-10发布日期:2024-05-16 -
通讯作者:张浩zhanghao@fzu.edu.cn -
作者简介:张浩(1981—),男,安徽,副教授,博士,CCF高级会员,主要研究方向为信息安全、安全大数据分析和计算智能算法|谢大智(2001—),男,安徽,硕士研究生,主要研究方向为网络安全、机器学习|胡云晟(2001—),男,安徽,硕士研究生,主要研究方向为网络安全、机器学习|叶骏威(2000—),男,福建,硕士研究生,主要研究方向为网络安全、机器学习 -
基金资助:国家自然科学基金重点项目(U1804263);国家自然科学基金重点项目(U21A20472);国家留学基金青年骨干教师出国研修项目(202006655011);福建省自然科学基金(2021J01616);福建省自然科学基金(2020J01130167);福建省自然科学基金(2021J01625)
A Review of Network Anomaly Detection Based on Semi-Supervised Learning
ZHANG Hao1,2( ), XIE Dazhi1,2, HU Yunsheng1,2, YE Junwei1,2
), XIE Dazhi1,2, HU Yunsheng1,2, YE Junwei1,2
- 1. College of Computer and Data Science, Fuzhou University, Fuzhou 350116, China
2. Fujian Key Laboratory of Network Computing and Intelligent Information Processing, Fuzhou 350116, China
-
Received:2023-10-26Online:2024-04-10Published:2024-05-16
摘要:
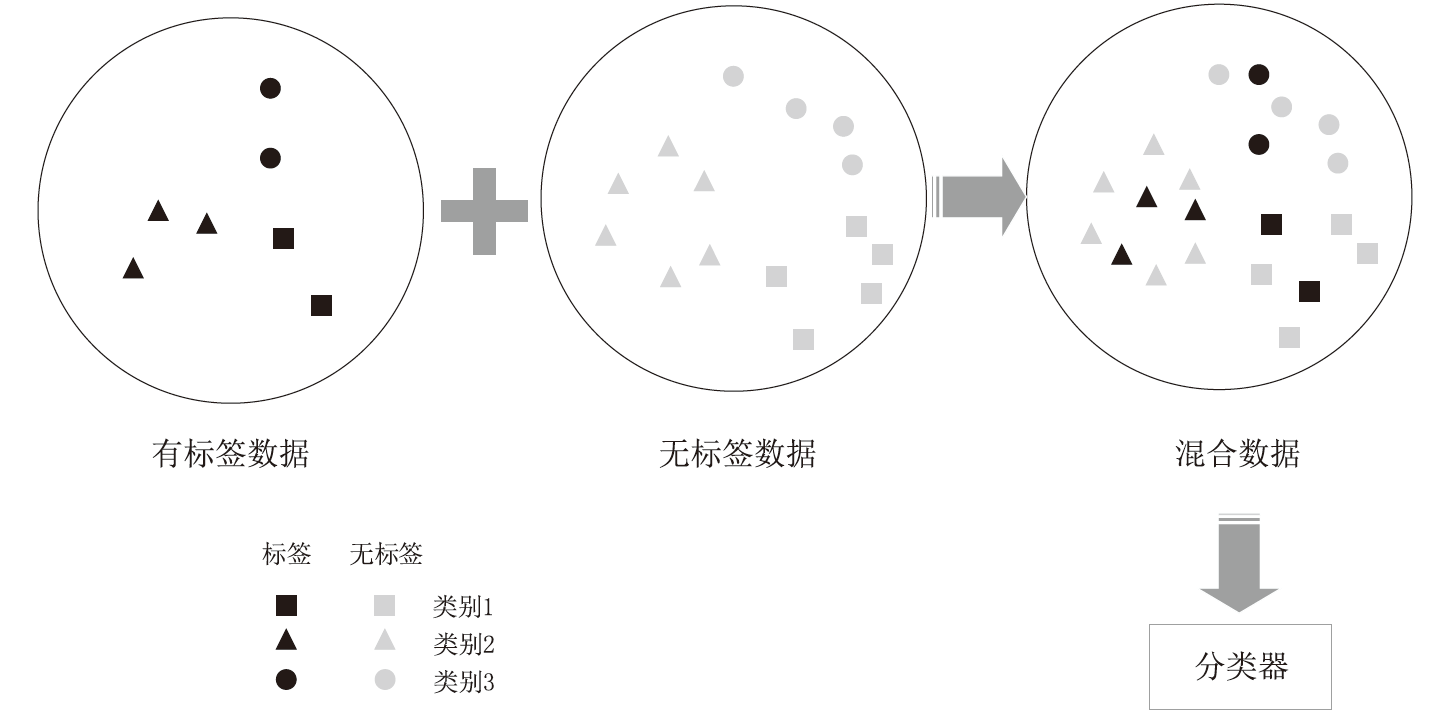
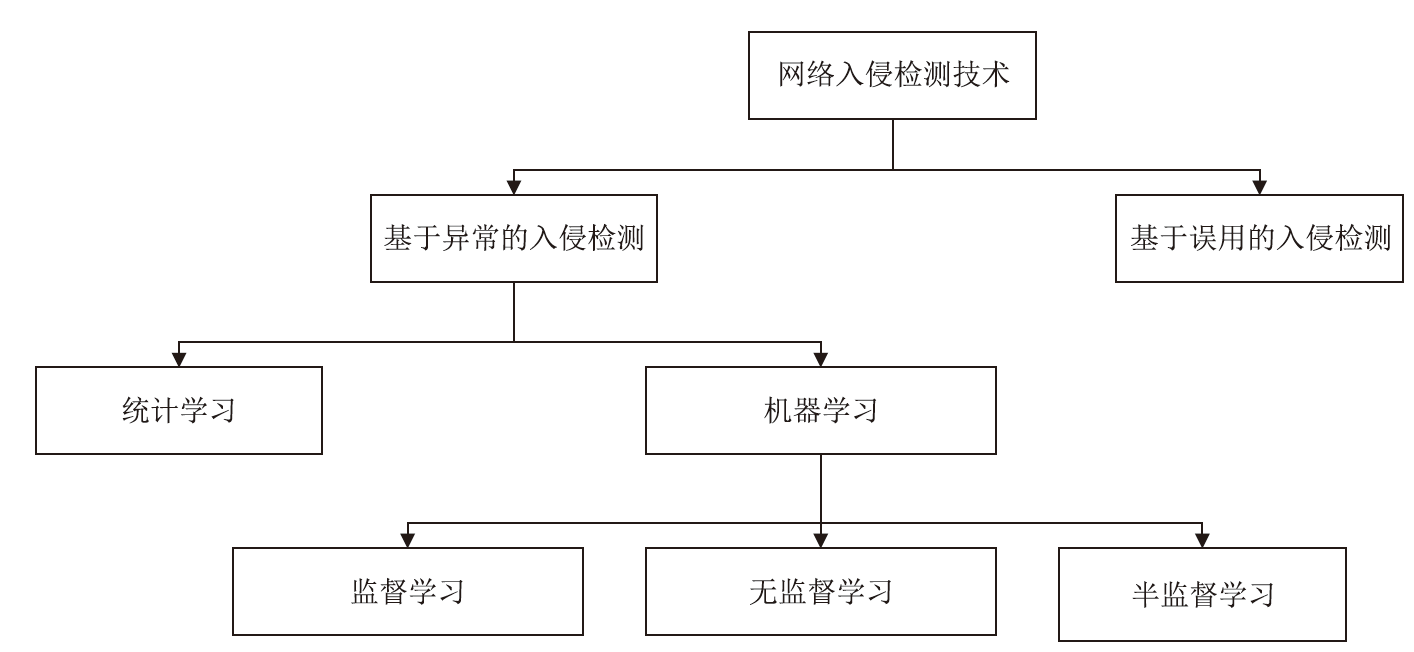
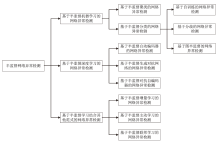
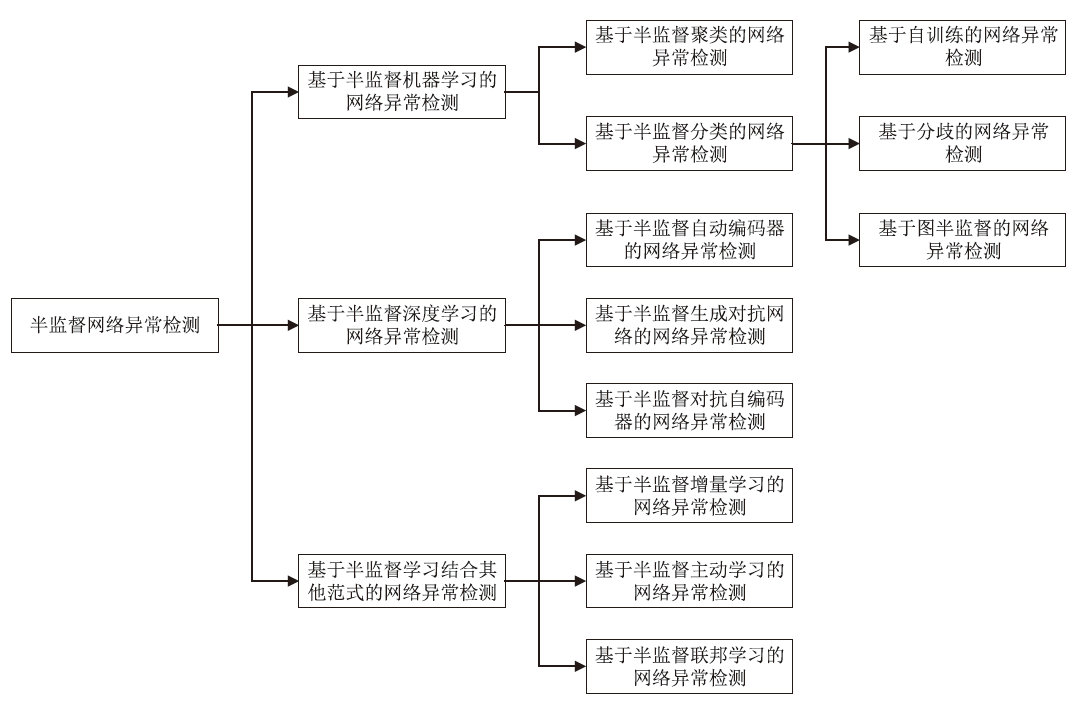
网络流量数据的获取较为容易,而对流量数据进行标记相对困难。半监督学习利用少量有标签数据和大量无标签数据进行训练,减少了对有标签数据的需求,能较好适应海量网络流量数据下的异常检测。文章对近年来的半监督网络异常检测领域的论文进行深入调研。首先,介绍了一些基本概念,并深入剖析了网络异常检测中使用半监督学习策略的必要性;然后,从半监督机器学习、半监督深度学习和半监督学习结合其他范式三个方面,分析和比较了半监督网络异常检测领域近年来的论文,并进行归纳和总结;最后,对当前半监督网络异常检测领域进行了现状分析和未来展望。
中图分类号:
引用本文
张浩, 谢大智, 胡云晟, 叶骏威. 基于半监督学习的网络异常检测研究综述[J]. 信息网络安全, 2024, 24(4): 491-508.
ZHANG Hao, XIE Dazhi, HU Yunsheng, YE Junwei. A Review of Network Anomaly Detection Based on Semi-Supervised Learning[J]. Netinfo Security, 2024, 24(4): 491-508.
表2
常用网络异常检测数据集
| 应用 场景 | 时间 | 数据集 | 攻击类型 |
|---|---|---|---|
| 传统 网络 | 1999 | KDD CUP99[ | DoS,Probe,U2R,R2L |
| 2004 | NSL-KDD[ | DoS,Probe,U2R,R2L | |
| 2015 | UNSW-NB15[ | Fuzzers,Analysis,Backdoors,DoS,Exploits,Generic,Reconnaissance,Shellcode,Worms | |
| 2017 | CIC-IDS2017[ | Brute Force,Heartbleed,Botnet,DoS,DDoS,Web Attack,Infiltration | |
| 2018 | CSE-CIC-IDS2018[ | Brute Force,Heartbleed,Botnet,DoS,DDoS,Web Attack,Infiltration | |
| 2011 | Kyoto2006+[ | Attack Session | |
| 2012 | ISCX-2012[ | Brute Force,Infiltration,DoS,DDoS | |
| 2018 | CTU[ | Sathurbot,Trickster,TrickBot,Dridex,WebCompanion,Viaxmr,Trojan,CoinMiner,HTBot,Ursnif | |
| 物联网 | 2020 | TON_IoT[ | Scanning,DoS,DDoS,Ransomware,Backdoor,Injection,XSS,Password,MITM |
| 2018 | N-BaIoT[ | BASHLITE Attacks, Mirai Attacks | |
| 2018 | Kitsune[ | Active Wiretap,ARP MitM,Fuzzing,Mirai Botnet,OS Scan,SSDP Flood,SSL Renegotiation,SYN DoS,Video Injection | |
| 2015 | SWaT[ | False Data Injection | |
| 2014 | SCADA[ | Reconnaissance,Response Injection,Command Injection,DoS | |
| 2019 | Car Hacking[ | DoS,Fuzzy,Gear Spoofing,RPM Spoofing |
表4
基于半监督聚类的网络异常检测
| 方案 | 网络 类型 | 方法 | 数据集 | 主要评价指标 |
|---|---|---|---|---|
| 文献[ | 传统 网络 | 采用半监督聚类方法进行特征选择 | UNSW-NB15 | Accuracy=98.81%、FPR=0.78%、DR=98.88% |
| 文献[ | 传统 网络 | 半监督K-Means算法 | CIC-IDS2017 | Accuracy=79.60% |
| 文献[ | 传统 网络 | 半监督加权K-Means算法 | DARPA、CAIDA、 CIC-IDS2017、real-world dataset | DARPA: FPR=1.40%、Recall=99.68% CAIDA: FPR=0%、Recall=99.00% CICIDS: FPR=28.72%、Recall=98.86% real-world dataset: FPR=0.20%、Recall=99.75% |
| 文献[ | 传统 网络 | 半监督多层 聚类模型 | NSL-KDD、Kyoto2006+ | NSL-KDD: Accuracy=99.59%、DR=99.51%、FAR=0.34% Kyoto2006+: Accuracy=99.39%、DR=99.72%、FAR=0.89% |
表5
基于半监督分类的网络异常检测
| 方案 | 网络 类型 | 方法 | 数据集 | 主要评价指标 |
|---|---|---|---|---|
| 文献[ | 传统 网络 | 一种基于自训练和标准增强的半监督学习方法 | NSL-KDD | Accuracy=82.87% |
| 文献[ | 传统 网络 | 自训练支持向量机 | NSL-KDD、KDD CUP99 | NSL-KDD: Accuracy=99.6%、Precision=99%、Recall=99%、F1-Score=99% KDD corrected: Accuracy=99.11%、Precision=98%、Recall=99%、F1-Score=99% |
| 文献[ | 传统 网络 | 自训练混合决策树 | CIC-IDS2017、 Kitsune、 Stratosphere IPS 5a、Stratosphere IPS 5b | CIC-IDS2017: Precision=65.0%、 Recall=83.3%:、 F1-Score=68.5% Kitsune: Precision=86.1%、 Recall=88.3%、 F1-Score=85.9% Stratosphere IPS 5a: Precision=79.1%、 Recall=71.5%、 F1-Score=74.2% Stratosphere IPS 5b: Precision=80.2%、 Recall=72.0%、 F1-Score=74.9% |
| 文献[ | 物联网 | 基于分歧的半监督学习 | KDD CUP99、Real-world IoT network environment | KDD CUP99: Error rate=10.5%、 Hit rate=92.48% Real-world IoT network environment: Error rate=7.3%、Hit rate=94.23% |
| 文献[ | 传统 网络 | 改进的基于分层采样的Tri-LightGBM | UNSW-NB15、 CIC-IDS2017 | UNSW-NB15: Accuracy=94.48%、Recall=94.25%、Precision=93.57%、F-measure=93.91%、FPR=5.01% CIC-IDS2017: Accuracy=98.04%、Recall=97.85%、Precision=99.06%、F-measure=98.44%、FPR=1.61% |
| 文献[ | 物联网 | 标签扩散 算法 | TON_IoT | Accuracy=99.84% |
| 文献[ | 智能 电网 | 标签传播 算法 | CER dataset | Attack-1: Accuracy=98.5%、Precision=89.0%、 F1-Score=97.0% Attack-2: Accuracy=75.7%、Precision=69.23%、 F1-Score=89.5% |
表6
基于半监督自动编码器的网络异常检测
| 方案 | 网络类型 | 方法 | 数据集 | 主要评价指标 |
|---|---|---|---|---|
| 文献[ | 传统网络 | 半监督自动编码器 | NSL-KDD、KDD CUP99 | NSL-KDD: Accuracy=97.2%、DR=91.6%、Precision=96.1%、FPR=0.8%、 F1-Score=93.5% KDD CUP99: Accuracy=96.8%、DR=90.5%、Precision=95.2%、FPR=0.9%、 F1-Score=93.3% |
| 文献[ | 传统网络 | 半监督堆叠稀疏 自编码器 | A network section from Universidad Del Cauca | Accuracy=89.09%、F-measure=89.05%、Precision=89.51%、Recall=88.35% |
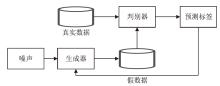
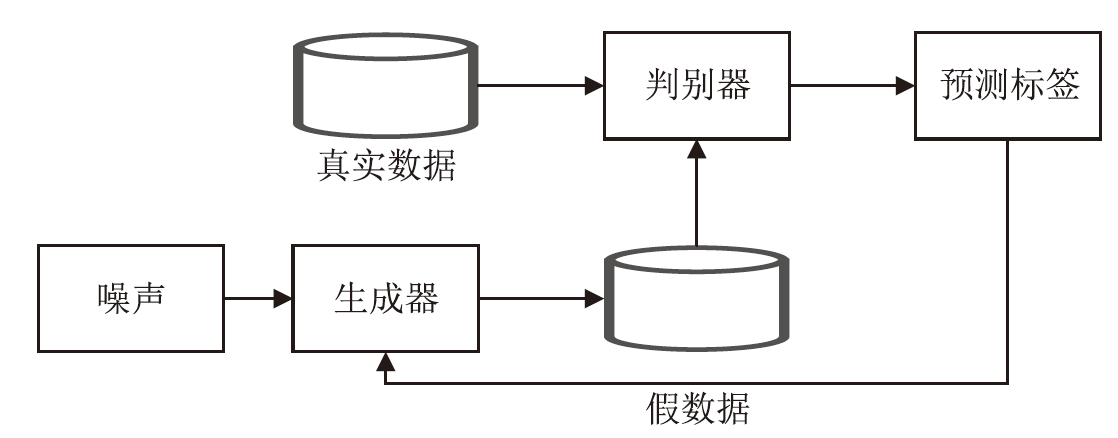
| 文献[ | 传统网络 | 半监督堆叠稀疏 自编码器 | UNSW-NB15 | Accuracy=93.5%、 F1-Score=94.5% |
| 文献[ | 传统网络 | 半监督判别自编码器 | CSE-CIC-IDS2018 | Accuracy=81.4%、Precision=82.1%、Recall=82.0%、 F1-Score=81.9% |
| 文献[ | 传统网络 | 半监督重构异常检测框架MANomaly | NSL-KDD、UNSW-NB15 | NSL-KDD: Accuracy=92.74% UNSW-NB15: Accuracy=92.07% |
表8
基于半监督对抗自编码器的网络异常检测
| 方案 | 网络类型 | 方法 | 数据集 | 主要评价指标 |
|---|---|---|---|---|
| 文献[ | 传统网络 | 半监督对抗自编码器 | NSL-KDD | Accuracy=83.11% |
| 文献[ | 控制器局域网 | 半监督卷积对抗 自编码器 | Car hacking | Error rate=0.1%、Recall=99.72%、Precision=99.97%、 F1-Score=99.84% |
| 文献[ | 传统网络 | 半监督对抗自编码器 | NSL-KDD | Accuracy=87.89%、Precision=90.06%、Recall=86.76%、F1-Score=88.34%、FPR=9.94% |
| 文献[ | 传统网络 | 半监督对抗自编码器 | CSE-CIC-IDS2018、UNSW-NB15 | CSE-CIC-IDS2018: Accuracy=98%、Recall=88.3%、Precision=94.7%、 F1-Score=91.4% UNSW-NB15: Accuracy=98.5%、Recall=75%、Precision=85.4%、 F1-Score=80% |
表9
基于半监督增量学习的网络异常检测
| 方案 | 网络类型 | 方法 | 数据集 | 主要评价指标 |
|---|---|---|---|---|
| 文献[ | 传统网络 | 一种增量式半监督训练框架 | NSL-KDD | DR=75.3%、 FAR=6.99% |
| 文献[ | 传统网络 | 一种新的半监督流分类方法的入侵检测系统 | KDD CUP99、Moore、Sperotto | KDD CUP99: TPR=85%、FPR=0.9%、MCC=83% |
| 文献[ | 传统网络 | 一种网络流量流上的密度感知和特征偏差的主动入侵检测框架 | CIC-IDS2017、ISCX-2012 | CIC-IDS2017、ISCX-2012: Precision=95.5%、Recall=96.7%、 F1-score=95.9% |
表10
基于半监督主动学习的网络异常检测
| 方案 | 网络类型 | 方法 | 数据集 | 主要评价指标 |
|---|---|---|---|---|
| 文献[ | 传统网络 | 一种混合半监督技术,将主动学习支持向量机结合模糊C均值聚类结合 | NSL-KDD | Detection rate=99.6% |
| 文献[ | 传统网络 | 一种基于主动半监督学习的网络异常检测算法 | CTU、CIC-IDS2017 | Accuracy=90.97%、Precision=90.85、Recall=90.91%、 F1-score=90.88% CIC-IDS2017: Accuracy=99.36%、Precision=90.85%、Recall=90.91%、 F1-score=90.88% |
| 文献[ | 信息物理系统 | 一种基于集成半监督主动学习的异常检测方法 | NSL-KDD、SWaT | NSL-KDD: Precision=99.02%、Recall=99.03%、 F1-score=99.01% SWaT: Precision=99.02%、Recall=99.03%、 F1-score=99.01% |
表11
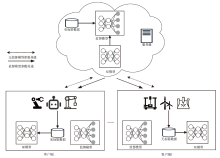
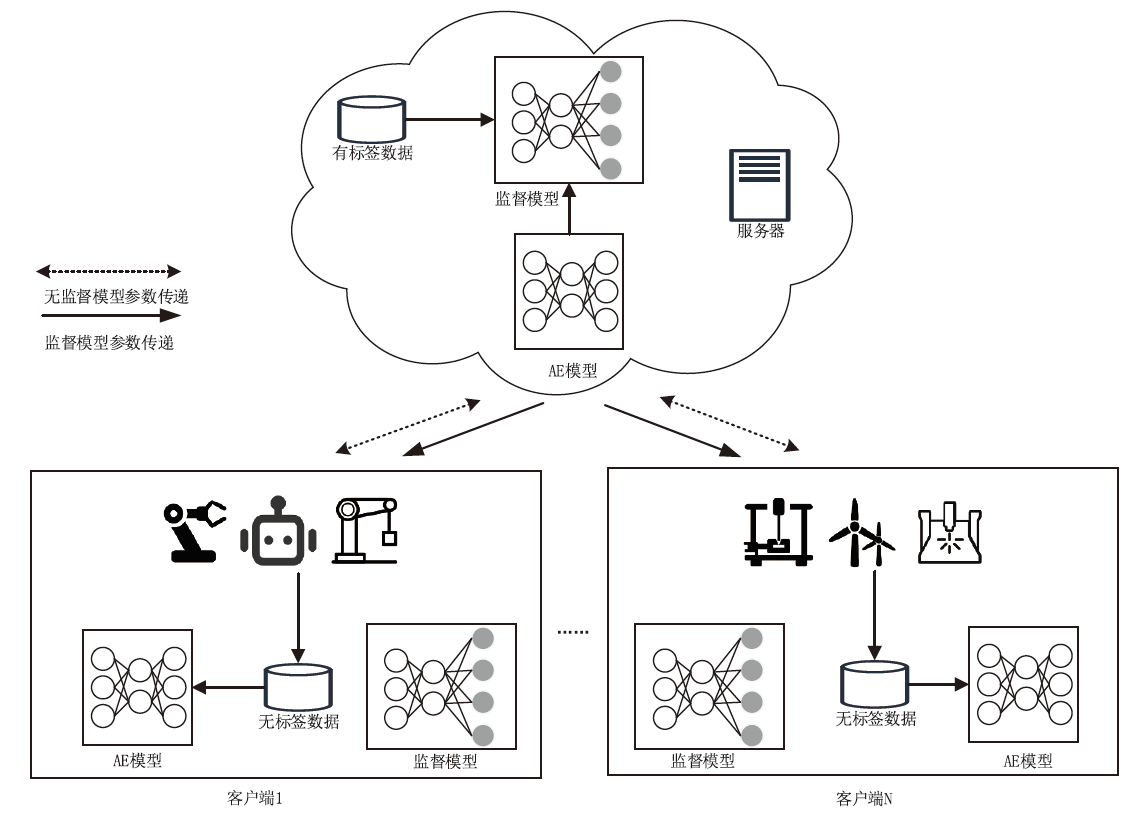
基于半监督联邦学习的网络异常检测
| 方案 | 网络类型 | 方法 | 数据集 | 主要评价指标 |
|---|---|---|---|---|
| 文献[ | 传统网络 | 一种半监督联邦学习的网络异常检测方法 | UNSW-NB15 | Accuracy=84.32%、Precision=86.19%、Recall=83.10%、 F1-score=83.63% |
| 文献[ | 工业 物联网 | 一种用于工业物联网攻击检测的半监督联邦学习方法 | SCADA | Accuracy=95.84%、Precision=97.89%、Recall=87.15% |
| 文献[ | 物联网 | 一种基于半监督联邦学习的网络异常检测方法 | N-BaIoT | Accuracy=86.70%、F1-score=84.95%、Recall=86.70%、Precision=91.73% |
| 文献[ | 物联网 | 一种基于知识蒸馏的半监督联邦学习的网络异常 检测方法 | N-BaIoT | Recall=87.40%、Precision=86.50%、 F1-score=92.33% |
| 文献[ | 传统网络 | 一种新的联邦学习支持的半监督主动学习框架 | CSE-CIC-IDS2018 | Accuracy=95%、S2C cost=42%、C2S cost=53% |
| [1] | AHMETOGLU H, DAS R. A Comprehensive Review on Detection of Cyber-Attacks: Data Sets, Methods, Challenges, and Future Research Directions[EB/OL]. (2022-09-20)[2023-09-03]. https://doi.org/10.1016/j.iot.2022.100615. |
| [2] | ABDULGANIYU O H, AIT T, SAHEED Y K. A Systematic Literature Review for Network Intrusion Detection System (IDS)[J]. International Journal of Information Security, 2023, 22(5): 1125-1162. |
| [3] | DEORE B, BHOSALE S. Hybrid Optimization Enabled Robust CNN-LSTM Technique for Network Intrusion Detection[J]. IEEE Access, 2022, 10: 65611-65622. |
| [4] | REN Huajuan, TANG Yonghe, DONG Weiyu, et al. DUEN: Dynamic Ensemble Handling Class Imbalance in Network Intrusion Detection[EB/OL]. (2023-05-13)[2023-09-03]. https://doi.org/10.1016/j.eswa.2023.120420. |
| [5] | MAZUMDER M, KADIR M, SHARMIN S, et al. cFEM: A Cluster Based Feature Extraction Method for Network Intrusion Detection[J]. International Journal of Information Security, 2023, 22(5): 1355-1369. |
| [6] | HAMMAD M, HEWAHI N, ELMEDANY W, et al. MMM-RF: A Novel High Accuracy Multinomial Mixture Model for Network Intrusion Detection Systems[EB/OL]. (2022-05-26)[2023-09-03]. https://doi.org/10.1016/j.cose.2022.102777. |
| [7] | WU Zhijun, GAO Pan, CUI Lei, et al. An Incremental Learning Method Based on Dynamic Ensemble RVM for Intrusion Detection[J]. IEEE Transactions on Network and Service Management, 2021, 19(1): 671-685. |
| [8] |
ZHANG Shipeng, LI Yongzhong, DU Xiangtong. Intrusion Detection Model Based on Semi-Supervised Learning and Three-Way Decision[J]. Journal of Computer Applications, 2021, 41(9): 2602-2608.
doi: 10.11772/j.issn.1001-9081.2020111883 |
|
张师鹏, 李永忠, 杜祥通. 基于半监督学习和三支决策的入侵检测模型[J]. 计算机应用, 2021, 41(9): 2602-2608.
doi: 10.11772/j.issn.1001-9081.2020111883 |
|
| [9] | THAKKAR A, LOHIYA R. Fusion of Statistical Importance for Feature Selection in Deep Neural Network-Based Intrusion Detection System[J]. Information Fusion, 2023, 90: 353-363. |
| [10] | FITRIANI S, MANDALA S, MURTI M. Review of Semi-Supervised Method For Intrusion Detection System[C]// IEEE. Asia Pacific Conference on Multimedia and Broadcasting (APMediaCast). New York: IEEE, 2016: 36-41. |
| [11] |
PANG Xinglong, ZHU Guosheng. Survey of Network Traffic Analysis Based on Semi Supervised Learning[J]. Computer Science, 2022, 49(6A): 544-554.
doi: 10.11896/jsjkx.210600131 |
|
庞兴龙, 朱国胜. 基于半监督学习的网络流量分析研究[J]. 计算机科学, 2022, 49(6A): 544-554.
doi: 10.11896/jsjkx.210600131 |
|
| [12] | DUARTE J M, BERTON L. A Review of Semi-Supervised Learning for Text Classification[J]. Artificial Intelligence Review, 2023, 56(9): 9401-9469. |
| [13] | DE V, THIERENS D. A Reliable Ensemble Based Approach to Semi-Supervised Learning[EB/OL]. (2021-01-14)[2023-09-03]. https://doi.org/10.1016/j.knosys.2021.106738. |
| [14] | ZHANG Hao, CHEN Long, WEI Zhiqiang. Abnormal Traffic Detection Technology Based on Data Augmentation and Model Update[J]. Netinfo Security, 2020, 20(2): 66-74. |
| 张浩, 陈龙, 魏志强. 基于数据增强和模型更新的异常流量检测技术[J]. 信息网络安全, 2020, 20(2): 66-74. | |
| [15] | JIAN Shijie, LU Zhigang, DU Dan, et al. Overview of Network Intrusion Detection Technology[J]. Journal of Cyber Security, 2020, 5(4): 96-122. |
| 蹇诗婕, 卢志刚, 杜丹, 等. 网络入侵检测技术综述[J]. 信息安全学报, 2020, 5(4): 96-122. | |
| [16] | JAIN M, KAUR G, SAXENA V. A K-Means Clustering and SVM Based Hybrid Concept Drift Detection Technique for Network Anomaly Detection[EB/OL]. (2022-01-02)[2023-09-03]. https://doi.org/10.1016/j.eswa.2022.116510. |
| [17] | KHAN A R, KASHIF M, JHAVERI R, et al. Deep Learning for Intrusion Detection and Security of Internet of Things (IoT): Current Analysis, Challenges, and Possible Solutions[EB/OL]. (2022-07-09)[2023-09-03]. https://doi.org/10.1155/2022/4016073. |
| [18] | Information and Computer Science University of California. KDD Cup 1999 Data[EB/OL]. (1999-10-28)[2023-09-03]. http://kdd.ics.uci.edu/databases/kddcup99/kddcup99.html. |
| [19] | TAVALLAEE M, BAGHERI E, LU W, et al. A Detailed Analysis of the KDD Cup 99 Data Set[C]// IEEE. 2009 IEEE Symposium on Computational Intelligence for Security and Defense Applications. New York: IEEE, 2009: 1-6. |
| [20] | MOUSTAFA N, SLAY J. UNSW-NB15: A Comprehensive Data Set for Network Intrusion Detection Systems (UNSW-NB15 Network Data Set)[C]// IEEE. 2015 Military Communications and Information Systems Conference (MilCIS). New York: IEEE, 2015: 1-6. |
| [21] | SHARAFALDIN I, LASHKARI A H, GHORBANI A A. Toward Generating a New Intrusion Detection Dataset and Intrusion Traffic Characterization[C]// Springer. 4th International Conference on Information Systems Security and Privacy. Heidelberg: Springer, 2018: 108-116. |
| [22] | LEEVY J L, KHOSHGOFTAAR T M. A Survey and Analysis of Intrusion Detection Models Based on CSE-CIC-IDS2018 Big Data[J]. Journal of Big Data, 2020, 7(1): 1-19. |
| [23] | SONG J, TAKAKURA H, OKABE Y, et al. Statistical Analysis of Honeypot Data and Building of Kyoto 2006+ Dataset for NIDS Evaluation[C]// ACM. Proceedings of the First Workshop on Building Analysis Datasets and Gathering Experience Returns for Security. New York: ACM, 2011: 29-36. |
| [24] | SHIRAVI A, SHIRAVI H, TAVALLAEE M, et al. Toward Developing a Systematic Approach to Generate Benchmark Datasets for Intrusion Detection[J]. Computers & Security, 2012, 31(3): 357-374. |
| [25] | ZHANG Yong, CHEN Xu, JIN Lei, et al. Network Intrusion Detection: Based on Deep Hierarchical Network and Original Flow Data[J]. IEEE Access, 2019, 7: 37004-37016. |
| [26] | ALSAEDI A, MOUSTAFA N, TARI Z, et al. TON_IoT Telemetry Dataset: A New Generation Dataset of IoT and IIoT for Data-Driven Intrusion Detection Systems[J]. IEEE Access, 2020, 8: 165130-165150. |
| [27] | MEIDAN Y, BOHADANA M, MATHOV Y, et al. N-BaIoT Network-Based Detection of IoT Botnet Attacks Using Deep Autoencoders[J]. IEEE Pervasive Computing, 2018, 17(3): 12-22. |
| [28] | MIRSKY Y, DOITSHMAN T, ELOVICI Y, et al. Kitsune: An Ensemble of Autoencoders for Online Network Intrusion Detection[EB/OL]. (2018-05-27)[2023-09-03]. https://doi.org/10.48550/arXiv.1802.09089. |
| [29] | GOH J, ADEPU S, JUNEJO K N, et al. A Dataset to Support Research in the Design of Secure Water Treatment Systems[C]// Springer. 11th International Conference on Critical Information Infrastructures Security. Heidelberg: Springer, 2017: 88-99. |
| [30] | MORRIS T, GAO W. Industrial Control System Traffic Data Sets for Intrusion Detection Research[J]. IFIP Advances in Information and Communication Technology, 2014, 441: 65-78. |
| [31] | SONG H M, WOO J, KIM H K. In-Vehicle Network Intrusion Detection Using Deep Convolutional Neural Network[EB/OL]. (2020-01-01)[2023-09-03]. https://doi.org/10.1016/j.vehcom.2019.100198. |
| [32] | GUPTA N, JINDAL V, BEDI P. CSE-IDS: Using Cost-Sensitive Deep Learning and Ensemble Algorithms to Handle Class Imbalance in Network-Based Intrusion Detection Systems[EB/OL]. (2021-10-07)[2023-09-03]. https://doi.org/10.1016/j.cose.2021.102499. |
| [33] | LIU Jingmei, GAO Yuanbo, HU Fengjie. A Fast Network Intrusion Detection System Using Adaptive Synthetic Oversampling and LightGBM[EB/OL]. (2021-04-17)[2023-09-03]. https://doi.org/10.1016/j.cose.2021.102289. |
| [34] | SOLEYMANPOUR S, SADR H, SOLEIMANDARABI M. CSCNN: Cost-Sensitive Convolutional Neural Network for Encrypted Traffic Classification[J]. NEURAL PROCESSING LETTERS, 2021, 53: 3497-3523. |
| [35] | JIA Weikuan, SUN Meili, LIAN Jian, et al. Feature Dimensionality Reduction: A Review[J]. Complex & Intelligent Systems, 2022, 8(3): 2663-2693. |
| [36] | LI Xukui, CHEN Wei, ZHANG Qianru, et al. Building Auto-Encoder Intrusion Detection System Based on Random Forest Feature Selection[EB/OL]. (2020-04-29)[2023-09-03]. https://doi.org/10.1016/j.cose.2020.101851. |
| [37] | MAZUMDER M, KADIR M, SHARMIN S, et al. CFEM: A Cluster Based Feature Extraction Method for Network Intrusion Detection[J]. International Journal of Information Security, 2023, 22(5): 1355-1369. |
| [38] | NAZIR A, KHAN R. A Novel Combinatorial Optimization Based Feature Selection Method for Network Intrusion Detection[EB/OL]. (2020-12-31)[2023-09-03]. https://doi.org/10.1016/j.cose.2020.102164. |
| [39] | JIA Weifeng, LI Jie, TONG Bin. Network Intrusion Detection Method Based on Semi-Supervised Dimensionality Reduction[J]. Computer Applications and Software, 2013, 30(10): 133-135. |
| 贾伟峰, 李杰, 童彬. 基于半监督降维技术的网络入侵检测方法[J]. 计算机应用与软件, 2013, 30(10): 133-135. | |
| [40] | XIANG Zhiyang, XIAO Zhu, HUANG Yourong, et al. Unsupervised and Semi-Supervised Dimensionality Reduction with Self-Organizing Incremental Neural Network and Graph Similarity Constraints[C]// Springer. Advances in Knowledge Discovery and Data Mining. Heidelberg: Springer, 2016: 191-202. |
| [41] | LI Jieling, ZHANG Hao, LIU Yanhua, et al. Semi-Supervised Machine Learning Framework for Network Intrusion Detection[J]. The Journal of Supercomputing, 2022, 78(11): 13122-13144. |
| [42] |
QIN Yue, DING Shifei, WANG Lijuan, et al. Research Progress on Semi-Supervised Clustering[J]. Cognitive Computation, 2019, 11(5): 599-612.
doi: 10.1007/s12559-019-09664-w |
| [43] | POOBALAN P, PANNIRSELVAM S. Semi-Supervised Clustering Based Feature Selection with Multiobjective Genomic Search Class-Based Classification Method for NIDPS[J]. Indian Journal of Science and Technology, 2022, 15(19): 948-955. |
| [44] | JASIM M, GAATA M. K-Means Clustering-Based Semi-Supervised for DDoS Attacks Classification[J]. Bulletin of Electrical Engineering and Informatics, 2022, 11(6): 3570-3576. |
| [45] |
GU Yonghao, LI Kaiyue, GUO Zhenyang, et al. Semi-Supervised K-Means DDoS Detection Method Using Hybrid Feature Selection Algorithm[J]. IEEE Access, 2019, 7: 64351-64365.
doi: 10.1109/ACCESS.2019.2917532 |
| [46] | AL-JARRAH O Y, AL-HAMMDI Y, YOO P D, et al. Semi-Supervised Multi-Layered Clustering Model for Intrusion Detection[J]. Digital Communications and Networks, 2018, 4(4): 277-286. |
| [47] | JIANG E P. A Semi-Supervised Learning Model for Intrusion Detection[J]. Intelligent Decision Technologies, 2019, 13(3): 343-353. |
| [48] | SAHU S K, MOHAPATRA D P, PANDA S K. A Self-Trained Support Vector Machine Approach for Intrusion Detection[C]// Springer. Advances in Distributed Computing and Machine Learning:Proceedings of ICADCML 2020. Heidelberg: Springer, 2021: 391-402. |
| [49] | HOU Yubo, TEO S G, CHEN Zhenghua, et al. Handling Labeled Data Insufficiency: Semi-Supervised Learning with Self-Training Mixup Decision Tree for Classification of Network Attacking Traffic[EB/OL]. (2022-08-01)[2023-09-03]. https://doi.org/10.1109/TDSC.2022.3195534. |
| [50] | ZHOU Zhihua. Machine Learning[M]. Beijing: Tsinghua University Press, 2016. |
| 周志华. 机器学习[M]. 北京: 清华大学出版社, 2016. | |
| [51] | ZHOU Zhihua, LI Ming. Tri-Training: Exploiting Unlabeled Data Using Three Classifiers[J]. IEEE Transactions on Knowledge Data Engineering, 2005, 17(11): 1529-1541. |
| [52] | LI Wenjuan, MENG Weizhi, AU M H. Enhancing Collaborative Intrusion Detection via Disagreement-Based Semi-Supervised Learning in IoT Environments[EB/OL]. (2020-03-20)[2023-09-03]. https://doi.org/10.1016/j.jnca.2020.102631. |
| [53] | REDDY D K K, NAYAK J, BEHERA H. A Hybrid Semi-Supervised Learning with Nature-Inspired Optimization for Intrusion Detection System in IoT Environment[C]// Springer. International Conference on Computational Intelligence in Pattern Recognition. Heidelberg: Springer, 2022: 580-591. |
| [54] | SHARMA R, JOSHI A M, SAHU C, et al. Semi Supervised Cyber Attack Detection System For Smart Grid[C]// IEEE. 2022 30th Southern African Universities Power Engineering Conference (SAUPEC). New York: IEEE, 2022: 1-5. |
| [55] | LEE S-W, MOHAMMADI M, RASHIDI S, et al. Towards Secure Intrusion Detection Systems Using Deep Learning Techniques: Comprehensive Analysis and Review[EB/OL]. (2021-05-09)[2023-09-03]. https://doi.org/10.1016/j.jnca.2021.103111. |
| [56] | ZHAO Ruijie, TANG Tiantian, GUI Guan, et al. A Lightweight Semi-Supervised Learning Method Based on Consistency Regularization for Intrusion Detection[C]// IEEE. ICC 2022-IEEE International Conference on Communications. New York: IEEE, 2022: 3124-3129. |
| [57] | GAO Feng, LI Jing, CHENG Ruiying, et al. ConNet: Deep Semi-Supervised Anomaly Detection Based on Sparse Positive Samples[J]. IEEE Access, 2021, 9: 67249-67258. |
| [58] | CAI Shaokang, HAN Dezhi, LI Dun. A Feedback Semi-Supervised Learning with Meta-Gradient for Intrusion Detection[J]. IEEE Systems Journal, 2023, 17(1): 1158-1169. |
| [59] | DONG Shi, XIA Yuanjun, PENG Tao. Network Abnormal Traffic Detection Model Based on Semi-Supervised Deep Reinforcement Learning[J]. IEEE Transactions on Network and Service Management, 2021, 18(4): 4197-4212. |
| [60] |
LI Haitao, WANG Ruimin, DONG Weiyu, et al. Semi-Supervised Network Traffic Anomaly Detection Method Based on GRU[J]. Computer Science, 2023, 50(3): 380-390.
doi: 10.11896/jsjkx.220100032 |
|
李海涛, 王瑞敏, 董卫宇, 等. 一种基于 GRU 的半监督网络流量异常检测方法[J]. 计算机科学, 2023, 50(3): 380-390.
doi: 10.11896/jsjkx.220100032 |
|
| [61] | BASATI A, FAGHIH M M. PDAE: Efficient Network Intrusion Detection in IoT Using Parallel Deep Auto-Encoders[J]. Information Sciences, 2022, 598: 57-74. |
| [62] | DU Xiangtong, Li Yongzhong, Feng Zunlei. A Semi-Supervised Intrusion Detection Algorithm Based on Auto-Encoder[C]// Springer. Security, Privacy, and Anonymity in Computation, Communication, and Storage. Heidelberg: Springer, 2021: 188-199. |
| [63] | AOUEDI O, PIAMRAT K, BAGADTHEY D. A Semi-Supervised Stacked Autoencoder Approach for Network Traffic Classification[C]// IEEE. 2020 IEEE 28th International Conference on Network Protocols (ICNP). New York: IEEE, 2020: 1-6. |
| [64] | LEE J H, KIM J W, CHOI M J. SSAE-DeepCNN Model for Network Intrusion Detection[C]// IEEE. 2021 22nd Asia-Pacific Network Operations and Management Symposium (APNOMS). New York: IEEE, 2021: 78-83. |
| [65] | ZHAO Feng, ZHANG Hao, PENG Jia, et al. A Semi-Self-Taught Network Intrusion Detection System[J]. Neural Computing and Applications, 2020, 32(23): 17169-17179. |
| [66] | ZHANG Lianming, XIE Xiaowei, XIAO Kai, et al. MANomaly: Mutual Adversarial Networks for Semi-Supervised Anomaly Detection[J]. Information Sciences, 2022, 611: 65-80. |
| [67] | DING Shanshuo, KOU Liang, WU Ting. A GAN-Based Intrusion Detection Model for 5G Enabled Future Metaverse[J]. Mobile Networks and Applications, 2022, 27(6): 2596-2610. |
| [68] | CHEN Yixin, WANG Shuai. TraCGAN: An Efficient Traffic Classification Framework Based on Semi-Supervised Learning with Deep Conventional Generative Adversarial Network[C]// Springer. 1st International Conference on Emerging Networking Architecture and Technologies. Heidelberg: Springer, 2023: 286-297. |
| [69] | SAURABH K, SINGH A, SINGH U, et al. GANIBOT: A Network Flow Based Semi Supervised Generative Adversarial Networks Model for IoT Botnets Detection[C]// IEEE. 2022 IEEE International Conference on Omni-Layer Intelligent Systems (COINS). New York: IEEE, 2022: 1-5. |
| [70] | JEONG H, YU J, LEE W. Poster Abstract: A Semi-Supervised Approach for Network Intrusion Detection Using Generative Adversarial Networks[C]// IEEE. IEEE INFOCOM 2021-IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS). New York: IEEE, 2021: 1-2. |
| [71] | VU L, NGUYEN Q U, NGUYEN D N, et al. Deep Generative Learning Models for Cloud Intrusion Detection Systems[J]. IEEE Transactions on Cybernetics, 2023, 53(1): 565-577. |
| [72] | HARA K, SHIOMOTO K. Intrusion Detection System Using Semi-Supervised Learning with Adversarial Auto-Encoder[C]// IEEE. NOMS 2020-2020 IEEE/IFIP Network Operations and Management Symposium. New York: IEEE, 2020: 1-8. |
| [73] | HOANG T-N, KIM D. Detecting In-Vehicle Intrusion via Semi-Supervised Learning-Based Convolutional Adversarial Autoencoders[EB/OL]. (2022-09-06)[2023-09-03]. https://doi.org/10.1016/j.vehcom.2022.100520. |
| [74] | LIU Xiaobing, LUO Entao, YANG Jie, et al. Semi-Supervised Intrusion Detection Method Based on Adversarial Autocoder[C]// IEEE. 2021 IEEE Intl Conf on Dependable, Autonomic and Secure Computing, Intl Conf on Pervasive Intelligence and Computing, Intl Conf on Cloud and Big Data Computing, Intl Conf on Cyber Science and Technology Congress (DASC/PiCom/CBDCom/CyberSciTech). New York: IEEE, 2021: 637-643. |
| [75] | THAI H H, HIEU N D, THO N V, et al. Adversarial AutoEncoder and Generative Adversarial Networks for Semi-Supervised Learning Intrusion Detection System[C]// IEEE. 2022 RIVF International Conference on Computing and Communication Technologies (RIVF). New York: IEEE, 2022: 584-589. |
| [76] | XIANG Zhiyang, XIAO Zhu, WANG Dong, et al. Incremental Semi-Supervised Kernel Construction with Self-Organizing Incremental Neural Network and Application in Intrusion Detection[J]. Journal of Intelligent & Fuzzy Systems, 2016, 31(2): 815-823. |
| [77] | NOORBEHBAHANI F, FANIAN A, MOUSAVI R, et al. An Incremental Intrusion Detection System Using a New Semi-Supervised Stream Classification Method[EB/OL]. (2017-03-10)[2023-09-03]. https://doi.org/10.1002/dac.3002. |
| [78] | LI Bin, WANG Yijie, XU Kele, et al. DFAID: Density-Aware and Feature-Deviated Active Intrusion Detection over Network Traffic Streams[EB/OL]. (2022-04-10)[2023-09-03]. https://doi.org/10.1016/j.cose.2022.102719. |
| [79] | KUMARI V V, VARMA P R K. A Semi-Supervised Intrusion Detection System Using Active Learning SVM and Fuzzy C-Means Clustering[C]// IEEE. 2017 International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud)( I-SMAC). New York: IEEE, 2017: 481-485. |
| [80] | ZHANG Yong, NIU Jie, HE Guojian, et al. Network Intrusion Detection Based on Active Semi-Supervised Learning[C]// IEEE. 51st Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN). New York: IEEE, 2021: 129-135. |
| [81] | NIU Zequn, GUO Wenjie, XUE Jingfeng, et al. A Novel Anomaly Detection Approach Based on Ensemble Semi-Supervised Active Learning (ADESSA)[EB/OL]. (2023-03-21)[2023-09-03]. https://doi.org/10.1016/j.cose.2023.103190. |
| [82] | AOUEDI O, PIAMRAT K, MULLER G, et al. Intrusion Detection for Softwarized Networks with Semi-Supervised Federated Learning[C]// IEEE. ICC 2022-IEEE International Conference on Communications. New York: IEEE, 2022: 5244-5249. |
| [83] | AOUEDI O, PIAMRAT K, MULLER G, et al. Federated Semisupervised Learning for Attack Detection in Industrial Internet of Things[J]. IEEE Transactions on Industrial Informatics, 2023, 19(1): 286-295. |
| [84] | ZHAO Ruijie, YANG Linbo, WANG Yijun, et al. A Semi-Supervised Federated Learning Scheme via Knowledge Distillation for Intrusion Detection[C]// IEEE. ICC 2022-IEEE International Conference on Communications. New York: IEEE, 2022: 2688-2693. |
| [85] | ZHAO Ruijie, WANG Yijun, XUE Zhi, et al. Semisupervised Federated-Learning-Based Intrusion Detection Method for Internet of Things[J]. IEEE Internet of Things Journal, 2023, 10(10): 8645-8657. |
| [86] | NAEEM F, ALI M, KADDOUM G. Federated-Learning-Empowered Semi-Supervised Active Learning Framework for Intrusion Detection in ZSM[J]. IEEE Communications Magazine, 2023, 61(2): 88-94. |
| [1] | 王健, 陈琳, 王凯崙, 刘吉强. 基于时空图神经网络的应用层DDoS攻击检测方法[J]. 信息网络安全, 2024, 24(4): 509-519. |
| [2] | 江荣, 刘海天, 刘聪. 基于集成学习的无监督网络入侵检测方法[J]. 信息网络安全, 2024, 24(3): 411-426. |
| [3] | 冯光升, 蒋舜鹏, 胡先浪, 马明宇. 面向物联网的入侵检测技术研究新进展[J]. 信息网络安全, 2024, 24(2): 167-178. |
| [4] | 金志刚, 丁禹, 武晓栋. 融合梯度差分的双边校正联邦入侵检测算法[J]. 信息网络安全, 2024, 24(2): 293-302. |
| [5] | 孙红哲, 王坚, 王鹏, 安雨龙. 基于Attention-BiTCN的网络入侵检测方法[J]. 信息网络安全, 2024, 24(2): 309-318. |
| [6] | 宋玉涵, 祝跃飞, 魏福山. 一种基于AdaBoost模型的区块链异常交易检测方案[J]. 信息网络安全, 2024, 24(1): 24-35. |
| [7] | 秦中元, 马楠, 余亚聪, 陈立全. 基于双重图神经网络和自编码器的网络异常检测[J]. 信息网络安全, 2023, 23(9): 1-11. |
| [8] | 沈华, 田晨, 郭森森, 慕志颖. 基于对抗性机器学习的网络入侵检测方法研究[J]. 信息网络安全, 2023, 23(8): 66-75. |
| [9] | 彭翰中, 张珠君, 闫理跃, 胡成林. 联盟链下基于联邦学习聚合算法的入侵检测机制优化研究[J]. 信息网络安全, 2023, 23(8): 76-85. |
| [10] | 蒋英肇, 陈雷, 闫巧. 基于双通道特征融合的分布式拒绝服务攻击检测算法[J]. 信息网络安全, 2023, 23(7): 86-97. |
| [11] | 刘长杰, 石润华. 基于安全高效联邦学习的智能电网入侵检测模型[J]. 信息网络安全, 2023, 23(4): 90-101. |
| [12] | 施园, 李杨, 詹孟奇. 一种面向微服务的多维度根因定位算法[J]. 信息网络安全, 2023, 23(3): 73-83. |
| [13] | 高庆官, 张博, 付安民. 一种基于攻击图的高级持续威胁检测方法[J]. 信息网络安全, 2023, 23(12): 59-68. |
| [14] | 吴圣麟, 刘汪根, 严明, 吴杰. 基于无监督系统调用规则生成的容器云实时异常检测系统[J]. 信息网络安全, 2023, 23(12): 91-102. |
| [15] | 廖丽云, 张伯雷, 吴礼发. 基于代价敏感学习的物联网异常检测模型[J]. 信息网络安全, 2023, 23(11): 94-103. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||