信息网络安全 ›› 2023, Vol. 23 ›› Issue (8): 86-98.doi: 10.3969/j.issn.1671-1122.2023.08.008
面向多源异构数据融合的隐私集合求交研究
- 1.山东大学网络空间安全学院,青岛 266237
2.山东区块链研究院,济南 250102
3.山东浪潮科学研究院有限公司,济南 250101
4.泉城实验室,济南 250100
-
收稿日期:2023-01-30出版日期:2023-08-10发布日期:2023-08-08 -
通讯作者:王梅 E-mail:wangmeiz@sdu.edu.cn -
作者简介:丁江(1998—),男,安徽,硕士研究生,主要研究方向为隐私信息检索|张国艳(1977—),女,山东,副教授,博士,主要研究方向为区块链及隐私计算|魏子重(1984—),男,山东,高级工程师,硕士,主要研究方向为密码协议及计算机安全|王梅(1990—),女,山东,助理研究员,博士,主要研究方向为隐私集合求交集及安全认证 -
基金资助:国家重点研发计划(2022YFB2702800);山东省自然科学基金(ZR2023MF045);山东省自然科学基金青年项目(ZR2023QF088);青岛市自然科学基金原创探索类项目(23-2-1-152-zyyd-jch)
Multi-Source Heterogeneous Data Collaboration via Private Set Intersection
DING Jiang1, ZHANG Guoyan1,2, WEI Zichong3, WANG Mei1,4( )
)
- 1. School of Cyber Science and Technology, Shandong University, Qingdao 266237, China
2. Shandong Institute of Blockchain, Jinan 250102, China
3. Inspur Academy of Science and Technology, Jinan 250101, China
4. Quancheng Laboratory, Jinan 250100, China
-
Received:2023-01-30Online:2023-08-10Published:2023-08-08 -
Contact:WANG Mei E-mail:wangmeiz@sdu.edu.cn
摘要:
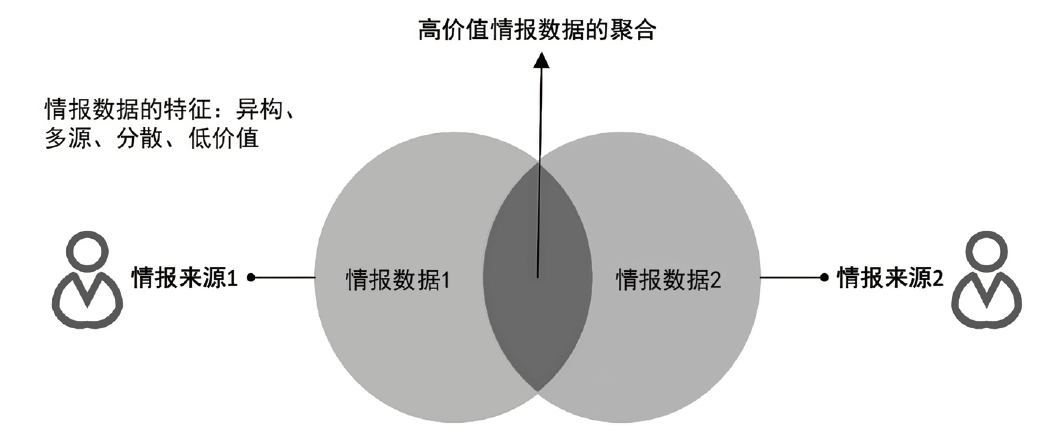
多源异构数据融合的痛点在于数据的低价值密度性和分散性。数据的多源异构性增加了数据聚合的难度,导致数据价值极度零散,使得数据融合方法面对多源异构大数据无的放矢,无法有效关联零散价值的数据。隐私集合求交(Private Set Intersection,PSI)不但可以使数据方放心提供数据,还可以将多源异构数据价值有效融合,是挖掘有效数据开展数据融合工作的新工具。为此,文章针对异构数据的整合、数据的多源以及大规模数据的并行处理3类问题,给出多源异构数据融合的3个新思路。
中图分类号:
引用本文
丁江, 张国艳, 魏子重, 王梅. 面向多源异构数据融合的隐私集合求交研究[J]. 信息网络安全, 2023, 23(8): 86-98.
DING Jiang, ZHANG Guoyan, WEI Zichong, WANG Mei. Multi-Source Heterogeneous Data Collaboration via Private Set Intersection[J]. Netinfo Security, 2023, 23(8): 86-98.
| [1] | FREEDMAN M J, NISSIM K, PINKAS B. Efficient Private Matching and Set Intersection[C]//Springer. International Conference on the Theory and Applications of Cryptographic Techniques. Berlin: Springer, 2004: 1-19. |
| [2] | JARECKI S, LIU Xiaomin. Efficient Oblivious Pseudorandom Function with Applications to Adaptive OT and Secure Computation of Set Intersection[C]//Springer. Theory of Cryptography Conference. Berlin: Springer, 2009: 577-594. |
| [3] | CAMENISCH J, ZAVERUCHA G M. Private Intersection of Certified Sets[C]//Springer. International Conference on Financial Cryptography and Data Security. Berlin: Springer, 2009: 108-127. |
| [4] | CRISTOFARO E D, TSUDIK G. Practical Private Set Intersection Protocols with Linear Complexity[C]//Springer. International Conference on Financial Cryptography and Data Security. Berlin: Springer, 2010: 143-159. |
| [5] |
HAZAY C, LINDELL Y. Efficient Protocols for Set Intersection and Pattern Matching with Security Against Malicious and Covert Adversaries[J]. Journal of Cryptology, 2010, 23(3): 422-456.
doi: 10.1007/s00145-008-9034-x URL |
| [6] | HUANG Yan, DAVID E, JONATHAN K. Private Set Intersection:Are Garbled Circuits Better than Custom Protocols[C]//ISOC. Network and Distributed System Security. NewYork: ISOC, 2012: 1-15. |
| [7] | DONG Changyu, CHEN Liqun, WEN Zikai. When Private Set Intersection Meets Big Data:An Efficient and Scalable Protocol[C]//ACM. Proceedings of the 2013 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2013: 789-800. |
| [8] | PINKAS B, SCHNEIDER T, ZOHNER M. Faster Private Set Intersection Based on OT Extension[C]//ACM. Proceedings of the 23rd USENIX Security Symposium. Berkeley: USENIX Association, 2014: 797-812. |
| [9] | PINKAS B, SCHNEIDER T, SEGEV G, et al. Phasing:Private Set Intersection Using Permutation-Based Hashing[C]//ACM. Proceedings 24th USENIX Conference on Security Symposium. New York: ACM, 2015: 515-530. |
| [10] | DEBNATH S K, DUTTA R. Secure and Efficient Private Set Intersection Cardinality Using Bloom Filter[C]//Springer. Proceedings of the International Conference on Information Security. Berlin: Springer, 2015: 209-226. |
| [11] | BRADLEY T, FABER S, TSUDIK G. Bounded Size-Hiding Private Set Intersection[C]//Springer. International Conference on Security and Cryptography for Networks. Berlin: Springer, 2016: 449-467. |
| [12] | KOLESNIKOV V, KUMARESAN R, ROSULEK M, et al. Efficient Batched Oblivious PRF with Applications to Private Set Intersection[C]//ACM. Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2016: 818-829. |
| [13] |
FREEDMAN, MICHAEL J, BENNY P, et al. Efficient Set Intersection with Simulation-Based Security[J]. Journal of Cryptology, 2016, 29(1): 115-155.
doi: 10.1007/s00145-014-9190-0 URL |
| [14] | DEBNATH S K, DUTTA R. How to Meet Big Data When Private Set Intersection Realizes Constant Communication Complexity[C]//Springer. International Conference on Information and Communications Security. Berlin: Springer, 2016: 445-454. |
| [15] | ABADI A, TERZIS S, DONG Changyu. VD-PSI: Verifiable Delegated Private Set Intersection on Outsourced Private Datasets[C]//Springer. International Conference on Financial Cryptography and Data Security. Berlin: Springer, 2016: 149-168. |
| [16] |
DONG Changyu, LOUKIDES G. Approximating Private Set Union/Intersection Cardinality with Logarithmic Complexity[J]. IEEE Transactions on Information Forensics and Security, 2017, 12(11): 2792-2806.
doi: 10.1109/TIFS.2017.2721360 URL |
| [17] | CHEN Hao, LAINE K, RINDAL P. Fast Private Set Intersection from Homomorphic Encryption[C]//ACM. Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2017: 1243-1255. |
| [18] | RINDAL P, ROSULEK M. Improved Private Set Intersection Against Malicious Adversaries[C]//Springer. Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques. Berlin: Springer, 2017: 235-259. |
| [19] | SHI Runhua, MU Yi, ZHONG Hong, et al. Quantum Private Set Intersection Cardinality and Its Application to Anonymous Authentication[J]. Information Sciences, 2016, 370(C): 147-158. |
| [20] |
AYDIN A, TERZIS S, METERE R, et al. Efficient Delegated Private Set Intersection on Outsourced Private Datasets[J]. IEEE Transactions on Dependable and Secure Computing, 2019, 16(4): 608-624.
doi: 10.1109/TDSC.8858 URL |
| [21] | HEINRICH A, HOLLICK M, SCHNEIDER T, et al. PrivateDrop:Practical Privacy-Preserving Authentication for Apple AirDrop[C]//ACM. USENIX Security Symposium. Berkeley: USENIX Association, 2021: 3577-3594. |
| [22] | SAHAI A, WATERS B. Fuzzy Identity Based Encryption[C]//IACR. European Cryptology Conference. New York: ACM, 2005: 457-473. |
| [23] | GOYAL V, PANDEY O, SAHAI A, et al. Attribute-Based Encryption for Fifine-Grained Access Control of Encrypted Data[C]//ACM. Proceedings of the 13th ACM Conference on Computer and Communications Security. New York: ACM, 2006: 89-98. |
| [24] | OSTROVSKY R, SAHAI A, WATERS B. Attribute-Based Encryption with Non-Monotonic Access Structures[C]//ACM. Proceedings of the 14th ACM Conference on Computer and Communications Security. New York: ACM, 2007: 195-203. |
| [25] | BETHENCOURT J, SAHAI A, WATERS B. Ciphertext-Policy Attribute-Based Encryption[C]//IEEE. Proceedings of IEEE Symposium on Security and Privacy. New York: IEEE, 2007: 321-334. |
| [26] | SONG D X, WAGNER D, PERRIG A. Practical Techniques for Searches on Encrypted Data[C]//IEEE. 2000 IEEE Symposium on Security and Privacy. New York: IEEE, 2000: 44-55. |
| [27] | GOH E J. Secure Index[EB/OL]. (2003-10-07)[2022-12-20]. https://eprint.iacr.org/archive/2003/216/1079467296.pdf. |
| [28] | BONEH D, CRESCENZO D G, OSTROVSKY R, et al. Public Key Encryption with Keyword Search[C]//Springer. International Conference on the Theory and Applications of Cryptographic Techniques. Berlin: Springer, 2004: 506-522. |
| [29] | CRESCENZO G D, SARASWAT V. Public Key Encryption with Searchable Keywords Based on Jacobi Symbols[C]//Springer. International Conference on Cryptology in India. Berlin: Springer, 2007: 282-296. |
| [30] | BAEK J, SAFAVI-NAINI R, SUSILO W. Public Key Encryption with Keyword Search Revisited[C]//IEEE. International Conference on Computational Science and lts Applications. New York: IEEE, 2008: 1249-1259. |
| [31] |
EMURA K, MIYAJI A, RAHMAN M S, et al. Generic Constructions of Secure Channel Free Searchable Encryption with Adaptive Security[J]. Security and Communication Networks, 2015, 8(8): 1547-1560.
doi: 10.1002/sec.1103 URL |
| [32] | BYUN J W, RHEE H S, PARK H A, et al. Off-Line Keyword Guessing Attacks on Recent Keyword Search Schemes over Encrypted Data[C]//Springer. The 3rd VLDB Workshop on Secure Data Management. Berlin: Springer, 2006: 75-83. |
| [33] | PARK D J, KIM K, LEE P J. Public Key Encryption with Conjunctive Field Keyword Search[C]//Springer. International Workshop on Information Security Applications. Berlin: Springer, 2004: 73-86. |
| [34] | BRINGER J, CHABANNE H, KINDARJI B. Error-Tolerant Searchable Encryption[C]//IEEE. 2009 IEEE International Conference on Communications. New York: IEEE, 2009: 1-35. |
| [35] | ZHENG Qingji, XU Shouhuai, ATENIESE G. VABKS:Verifiable Attribute-Based Keyword Search over Outsourced Encrypted Data[C]//IEEE. 2014 IEEE Conference on Computer Communications. New York: IEEE, 2014: 522-530. |
| [36] | LIU Pengliang, WANG Jianfeng, MA Hua, et al. Efficient Verifiable Public Key Encryption with Keyword Search Based on KP-ABE[C]//ACM. The 9th International Conference on Broadband and Wireless Computing. New York: ACM, 2014: 584-589. |
| [37] | KISSNER L, SONG D. Privacy-Preserving Set Operations[C]//Springer. Annual International Cryptology Conference. Berlin: Springer, 2005: 241-257. |
| [38] | SANG Yingpeng, SHEN Hong, TAN Yasuo, et al. Efficient Protocols for Privacy Preserving Matching Against Distributed Datasets[C]//Springer. International Conference on Information and Communications Security. Berlin: Springer, 2006: 210-227. |
| [39] | WANG Boyang, LI Baochun, LI Hui. Gmatch:Secure and Privacy-Preserving Group Matching in Social Networks[C]//IEEE. 2012 IEEE Global Communications Conference (GLOBECOM). New York: IEEE, 2012: 726-731. |
| [40] | KAMARA S, MOHASSEL P, RAYKOVA M, et al. Scaling Private Set Intersection to Billion-Element Sets[C]//Springer. International Conference on Financial Cryptography and Data Security. Berlin: Springer, 2014: 195-215. |
| [41] |
THAPA A, LI Ming, SALINAS S. Asymmetric Social Proximity Based Private Matching Protocols for Online Social Networks[J]. IEEE Transactions on Parallel and Distributed Systems, 2015, 26 (6): 1547-1559.
doi: 10.1109/TPDS.71 URL |
| [42] | YARLAGADDA N R, NARESH B. Improved Privacy Preserving Profile Matching in Online Social Networks[J]. Ijseat, 2015, 3(1): 1112-1115. |
| [43] | PATSAKIS C, ZIGOMITROS A, SOLANAS A. Privacy-Aware Genome Mining:Server-Assisted Protocols for Private Set Intersection and Pattern Matching[C]//IEEE. 2015 IEEE 28th International Symposium on Computer-Based Medical Systems. New York: IEEE, 2015: 276-279. |
| [44] | KOLESNIKOV V, MATANIA N, PINKAS B, et al. Practical Multi-Party Private Set Intersection from Symmetric-Key Techniques[C]//ACM. ACM Sigsac Conference on Computer & Communications Security. New York: ACM, 2017: 1257-1272. |
| [45] |
ZHANG En, LI Fenghua, NIU Ben, et al. Server-Aided Private Set Intersection Based on Reputation[J]. Information Sciences, 2017, 387: 180-194.
doi: 10.1016/j.ins.2016.09.056 URL |
| [46] | PINKAS B, SCHNEIDER T, WEINERT C, et al. Efficient Circuit-Based PSI via Cuckoo Hashing[C]//Springer. Annual International Conference on the Theory and Applications of Cryptographic Techniques. Berlin: Springer, 2018: 125-157. |
| [47] | NEVO O, TRIEU N, YANAI A S. Fast Malicious Multiparty Private Set Intersection[C]//ACM. 2021 ACM SIGSAC Conference on Computer and Communication Security. New York: ACM, 2021: 1151-1165. |
| [48] | FELLOWS M, KOBLITZ N. Combinatorial Cryptosystems Galore[J]. Contemporary Mathematics, 1994, 168: 1-12. |
| [49] | GENTRY C. A Fully Homomorphic Encryption Scheme[M]. Palo Alto: Stanford University, 2009. |
| [50] | BRAKERSKI Z, VAIKUNTANATHAN V. Fully Homomorphic Encryption from Ring-LWE and Security for Key Dependent Messages[C]//Springer. In Advances in Cryptology (CRYPTO’11). Berlin: Springer, 505-524. |
| [51] | BRAKERSKI Z, GENTRY C, VAIKUNTANATHAN V. Fully Homomorphic Encryption Without Bootstrapping[J]. ACM Transactions on Computation Theory, 2014, 6(3): 1-36. |
| [52] | FAN Junfeng, VERCAUTEREN F. Somewhat Practical Fully Homomorphic Encryption[EB/OL]. (2012-01-07)[2022-12-20]. https://eprint.iacr.org/2012/144.pdf. |
| [53] | CHEON J H, KIM A, KIM M, et al. Homomorphic Encryption for Arithmetic of Approximate NumbersC//Springer. In International Conference on the Theory and Application of Cryptology and Information Security. Berlin: Springer, 2017: 409-437. |
| [54] | CHEN Hao, LAINE K, RINDAL P. Fast Private Set Intersection from Homomorphic Encryption[C]//ACM. In Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2017: 1243-1255. |
| [55] | CHEN Hao, HUANG Zhicong, LAINE K, et al. Labeled PSI from Fully Homomorphic Encryption with Malicious Security[C]//ACM. Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2018: 1223-1237. |
| [56] | UZUN E, CHUNG S P, KOLESNIKOV V, et al. Fuzzy Labeled Private Set Intersection with Applications to Private Real-Time Biometric Search[C]//ACM. USENIX Security Symposium. Berkeley: USENIX Association, 2021: 911-928. |
| [57] | MANULIS M, PINKAS B, POETTERING B. Privacy-Preserving Group Discovery with Linear ComplexityC//Springer. International Conference on Applied Cryptography and Network Security(ACNS 2010). Berlin: Springer, 2010: 420-437. |
| [58] | CHO C, DACHMAN-SOLED D, JARECKI S. Efficient Concurrent Covert Computation of String Equality and Set Intersection. Berlin: Springer, 2016: 164-179. |
| [59] | PINKAS B, SCHNEIDER T, TKACHENKO O, et al. Efficient Circuit-Based PSI with Linear Communication[C]//Springer. Annual International Conference on the Theory and Applications of Cryptographic Techniques. Berlin: Springer, 2019: 122-153. |
| [60] | CHANDRAN N, GUPTA D, SHAH A. Circuit-PSI with Linear Complexity via Relaxed Batch OPPRF[C]//Springer. Proceedings on Privacy Enhancing Technologies. Berlin: Springer, 2021: 353-372. |
| [61] | CHANDRAN N, DASGUPTA N, GUPTA D, et al. Efficient Linear Multiparty PSI and Extensions to Circuit/Quorum PSI[C]//ACM. Proceedings of the 2021 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2021: 1182-1204. |
| [62] | BENNY P, MIKE R, NI T, et al. SpOT-Light: Lightweight Private Set Intersection from Sparse OT Extension[C]//Springer. In Advances in Cryptology. Berlin: Springer, 2019: 401-431. |
| [63] | ISHAI Y, KILIAN J, NISSIM K, et al. Extending Oblivious Transfers Efficiently[C]//Springer. In Advances in Cryptology(CRYPTO 2003). Berlin: Springer, 2003: 145-161. |
| [64] | KOLESNIKOV V, ROSULEK M, TRIEU N, et al. Scalable Private Set Union from Symmetric-Key Techniques[C]//Springer. International Conference on the Theory and Application of Cryptology and Information Security(ASIACRYPT 2019). Berlin: Springer, 2019: 636-666. |
| [65] | PINKAS B, ROSULEK M, TRIEU N, et al. PSI from PaXoS: Fast, Malicious Private Set Intersection[C]//Springer. Annual International Conference on the Theory and Applications of Cryptographic Techniques(EUROCRYPT 2020). Berlin: Springer, 2020: 739-767. |
| [66] | MARCELA S M, BLANKSTEIN A, BONNEAU J, et al. CONIKS:Bringing Key Transparency to End Users[C]//USENIX. USENIX Security 2015. Berkeley: USENIX, 2015: 383-398. |
| [67] | CASACUBERTA S, HESSE J, LEHMANN A. SoK:Oblivious Pseudorandom Functions[C]//IEEE. 2022 IEEE 7th European Symposium on Security and Privacy (EuroS&P). New York: IEEE, 2022: 625-646. |
| [68] | EVERSPAUGH A, CHATERJEE R, SCOTT S, et al. The Pythia PRF Service[C]//USENIX. USENIX Security Symposium. Berkeley: USENIX, 2015: 547-562. |
| [69] | JARECKI S, KIAYIAS A, KRAWCZYK H, et al. TOPPSS: Cost-Minimal Password-Protected Secret Sharing Based on Threshold OPRF[C]//Springer. International Conference on Applied Cryptography and Network Security. Berlin: Springer, 2017: 39-58. |
| [1] | 王智, 张浩, 顾建军. SDN网络中基于联合熵与多重聚类的DDoS攻击检测[J]. 信息网络安全, 2023, 23(10): 1-7. |
| [2] | 张玉臣, 李亮辉, 马辰阳, 周洪伟. 一种融合变量的日志异常检测方法[J]. 信息网络安全, 2023, 23(10): 16-20. |
| [3] | 仝鑫, 金波, 王斌君, 翟晗名. 融合对抗增强和多任务优化的恶意短信检测方法[J]. 信息网络安全, 2023, 23(10): 21-30. |
| [4] | 朱怡昕, 苗张旺, 甘静鸿, 马存庆. 基于细粒度访问控制的勒索软件防御系统设计[J]. 信息网络安全, 2023, 23(10): 31-38. |
| [5] | 张璐, 屠晨阳, 苗张旺, 甘静鸿. 位置信息端云可信传输方案设计[J]. 信息网络安全, 2023, 23(10): 39-47. |
| [6] | 陈星任, 熊焰, 黄文超, 付贵禄. 一种基于静态分析的多视图硬件木马检测方法[J]. 信息网络安全, 2023, 23(10): 48-57. |
| [7] | 王宇, 吕良双, 夏春和. 基于语义分析的Windows恶意软件检测方法[J]. 信息网络安全, 2023, 23(10): 58-63. |
| [8] | 邢凌凯, 张健. 基于HPC的虚拟化平台异常检测技术研究与实现[J]. 信息网络安全, 2023, 23(10): 64-69. |
| [9] | 秦一方, 张健, 梁晨. 基于神经网络的电子病历数据特征提取技术研究[J]. 信息网络安全, 2023, 23(10): 70-76. |
| [10] | 赵欣荷, 谢永恒, 万月亮, 汪金苗. 基于多模态数据的博彩网站检测识别模型[J]. 信息网络安全, 2023, 23(10): 77-82. |
| [11] | 叶桓荣, 李牧远, 姜波. 基于迁移学习和威胁情报的DGA恶意域名检测方法研究[J]. 信息网络安全, 2023, 23(10): 8-15. |
| [12] | 秦中元, 马楠, 余亚聪, 陈立全. 基于双重图神经网络和自编码器的网络异常检测[J]. 信息网络安全, 2023, 23(9): 1-11. |
| [13] | 公鹏飞, 谢四江, 程安东. 基于HotStuff改进的多主节点共识算法[J]. 信息网络安全, 2023, 23(9): 108-117. |
| [14] | 戴玉, 周非, 薛丹. 基于中国剩余定理秘密共享的切换认证协议[J]. 信息网络安全, 2023, 23(9): 118-128. |
| [15] | 张玉臣, 张雅雯, 吴越, 李程. 基于时频图与改进E-GraphSAGE的网络流量特征提取方法[J]. 信息网络安全, 2023, 23(9): 12-24. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||