信息网络安全 ›› 2023, Vol. 23 ›› Issue (3): 84-95.doi: 10.3969/j.issn.1671-1122.2023.03.009
支持国密算法的区块链交易数据隐私保护方案
- 1.北京邮电大学网络空间安全学院,北京 100876
2.杭州安存网络科技有限公司,杭州 310000
-
收稿日期:2022-10-19出版日期:2023-03-10发布日期:2023-03-14 -
通讯作者:马兆丰 E-mail:mzf@bupt.edu.cn -
作者简介:王晶宇(1999—),女,内蒙古,硕士研究生,主要研究方向为区块链与隐私保护技术|马兆丰(1974—),男,甘肃,副教授,博士,主要研究方向为区块链理论与技术、区块链核心创新及应用|徐单恒(1994—),男,杭州,硕士,主要研究方向为区块链技术与应用|段鹏飞(1995—),男,山东,博士研究生,主要研究方向为区块链及安全技术 -
基金资助:国家重点研发计划(2020YFB1005500);北京市自然科学基金(M21034)
Blockchain Transaction Data Privacy-Preserving Scheme Supporting National Cryptographic Algorithm
WANG Jingyu1, MA Zhaofeng1( ), XU Danheng2, DUAN Pengfei1
), XU Danheng2, DUAN Pengfei1
- 1. School of Cyberspace Security, Beijing University of Posts and Telecommunications, Beijing 100876, China
2. Hangzhou Ancun Network Technology Co., Ltd., Hangzhou 310000, China
-
Received:2022-10-19Online:2023-03-10Published:2023-03-14 -
Contact:MA Zhaofeng E-mail:mzf@bupt.edu.cn
摘要:
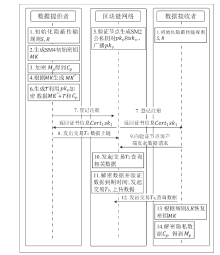
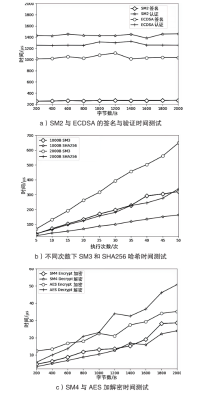
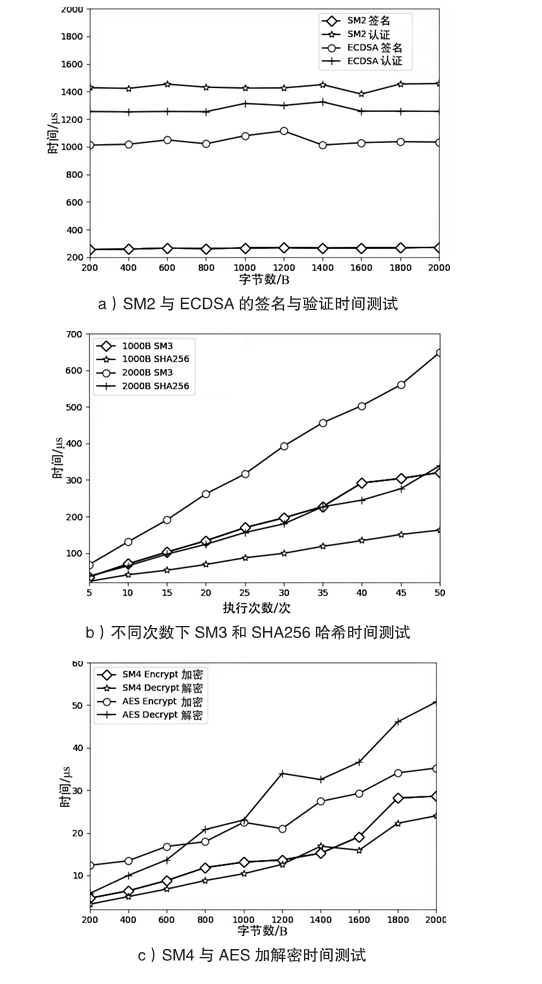
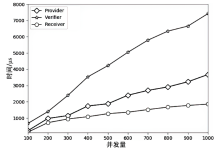
随着区块链技术的发展,链上数据共享越来越重要。当前区块链交易数据在链上公开透明,存在隐私数据共享受限问题,而且Hyperledger Fabric平台缺乏国密算法的支持,在国内应用中受限。文章首先采用国密算法改造Hyperledger Fabric平台;然后提出交易数据隐私保护方案,以国密算法完成对交易数据的安全和限时共享;最后对改造的Hyperledger Fabric平台和提出的方案做系统实现和性能测试。实验结果表明,文章方法实现了对Hyperledger Fabric平台的国密改造,该方案的执行效率和系统性能均满足实际需求。
中图分类号:
引用本文
王晶宇, 马兆丰, 徐单恒, 段鹏飞. 支持国密算法的区块链交易数据隐私保护方案[J]. 信息网络安全, 2023, 23(3): 84-95.
WANG Jingyu, MA Zhaofeng, XU Danheng, DUAN Pengfei. Blockchain Transaction Data Privacy-Preserving Scheme Supporting National Cryptographic Algorithm[J]. Netinfo Security, 2023, 23(3): 84-95.
表1
参数说明
| 符号 | 符号定义 |
|---|---|
| SM4中4个8字节的系统参数 | |
| SM4中32个8字节的固定参数 | |
| 待加密的用户隐私数据 | |
| SM4加密后的密文 | |
| SM4初始密钥 | |
| 经过编码调制后的对称密钥 | |
| CA机构向用户颁发的数字证书 | |
| 区块链中验证节点的SM2私钥 | |
| 区块链中验证节点的SM2公钥 | |
| 数据提供者客户端的SM2私钥 | |
| 数据提供者客户端的SM2公钥 | |
| SM2的加密算法 | |
| SM2的解密算法 | |
| 区块链交易ID | |
| 区块链交易数据内容 | |
| 区块链交易时间戳 |
| [1] | NAKAMOTO S. Bitcoin: A Peer-to-Peer Electronic Cash System[EB/OL]. [2022-09-06]. https://bitcoin.org/bitcoin.pdf. |
| [2] | XIA Yadong, CHE Lu, WANG Guanxiang, et al. Design of Passwordless Authentication System Using Decentralized Identity in Universities[EB/OL]. (2022-07-13)[2022-09-06]. http://kns.cnki.net/kcms/detail/61.1224.TN.20220712.1526.002.html. |
| 夏亚东, 车路, 王关祥, 等. 高校去中心化身份无密码认证系统设计[EB/OL]. (2022-07-13)[2022-09-06]. http://kns.cnki.net/kcms/detail/61.1224.TN.20220712.1526.002.html. | |
| [3] | LIN Chao, HE Debiao, HUANG Xinyi. Blockchain-Based Electronic Medical Record Secure Sharing[EB/OL]. (2022-01-17)[2022-09-06]. http://kns.cnki.net/kcms/detail/51.1307.TP.20220115.1014.002.html. |
| 林超, 何德彪, 黄欣沂. 基于区块链的电子医疗记录安全共享[EB/OL]. (2022-01-17)[2022-09-06]. http://kns.cnki.net/kcms/detail/51.1307.TP.20220115.1014.002.html. | |
| [4] | ZHAI Sheping, TONG Tong, BAI Xifang. Blockchain-Based Attribute Proxy Re-encryption Data Sharing Scheme[EB/OL]. (2022-07-20)[2022-09-21]. http://kns.cnki.net/kcms/detail/11.2127.TP.20220719.1534.004.html. |
| 翟社平, 童彤, 白喜芳. 基于区块链的属性代理重加密数据共享方案[EB/OL]. (2022-07-20)[2022-09-21]. http://kns.cnki.net/kcms/detail/11.2127.TP.20220719.1534.004.html. | |
| [5] |
AZZI R, CHAMOUN R K, SOKHN M. The Power of a Blockchain-Based Supply Chain[J]. Computers & Industrial Engineering, 2019, 135: 582-592.
doi: 10.1016/j.cie.2019.06.042 URL |
| [6] | JING Nan, LIU Qi, SUGUMARAN V. A Blockchain-Based Code Copyright Management System[EB/OL]. [2022-09-21]. https://xueshu.baidu.com/usercenter/paper/show?paperid=1u630e30dh420p90xj430270st462748&site=xueshu_se. |
| [7] |
MA Zhaofeng, JIANG Ming, GAO Hongmin, et al. Blockchain for Digital Rights Management[J]. Future Generation Computer Systems, 2018, 89: 746-764.
doi: 10.1016/j.future.2018.07.029 URL |
| [8] |
MA Zhaofeng, WANG Xiaochang, JAIN D K, et al. A Blockchain-Based Trusted Data Management Scheme in Edge Computing[J]. IEEE Transactions on Industrial Informatics, 2019, 16(3): 2013-2021.
doi: 10.1109/TII.9424 URL |
| [9] |
MA Zhaofeng, WANG Lingyun, WANG Xiaochang, et al. Blockchain-Enabled Decentralized Trust Management and Secure Usage Control of IoT Big Data[J]. IEEE Internet of Things Journal, 2019, 7(5): 4000-4015.
doi: 10.1109/JIoT.6488907 URL |
| [10] | ZHONG Sheng, HUANG Xinyi. Introduction to Security and Privacy in Blockchain Applications[J]. Chinese Science: Information Science, 2020, 50(3): 461-462. |
| 仲盛, 黄欣沂. 区块链应用中的安全隐私专题简介[J]. 中国科学:信息科学, 2020, 50(3): 461-462. | |
| [11] | SHI Kun, ZHOU Yong, ZHANG Qiliang, et al. Privacy-Preserving Scheme of Energy Trading Data Based on Consortium Blockchain[EB/OL]. (2022-08-12)[2022-09-13]. http://kns.cnki.net/kcms/detail/50.1075.tp.20220810.0952.024.html. |
| 时坤, 周勇, 张启亮, 等. 基于联盟链的能源交易数据隐私保护方案[EB/OL]. (2022-08-12)[2022-09-13]. http://kns.cnki.net/kcms/detail/50.1075.tp.20220810.0952.024.html. | |
| [12] | LI Li, DU Huina, LI Tao. Blockchain Supervisable Privacy Protection Scheme Based on Group Signature and Attribute Encryption[J]. Computer Engineering, 2022, 48(6): 132-138. |
| 李莉, 杜慧娜, 李涛. 基于群签名与属性加密的区块链可监管隐私保护方案[J]. 计算机工程, 2022, 48(6): 132-138. | |
| [13] | LIANG Wei, YANG Yang, YANG Ce, et al. PDPChain: A Consortium Blockchain-Based Privacy Protection Scheme for Personal Data[J]. IEEE Transactions on Reliability, 2022: 1-13. |
| [14] |
WANG Baocheng, LI Zetao. Healthchain: A Privacy Protection System for Medical Data Based on Blockchain[J]. Future Internet, 2021, 13(10): 247.
doi: 10.3390/fi13100247 URL |
| [15] | LUO Yurong, CAO Jin, LI Hui, et al. Electronic Invoice Public Verification Scheme based on SM2 Coalition Signature Algorithm[J]. Chinese Journal of Network and Information Security, 2022, 8(2): 122-131. |
| 罗玙榕, 曹进, 李晖, 等. 基于SM2联合签名的电子发票公开验证方案[J]. 网络与信息安全学报, 2022, 8(2): 122-131. | |
| [16] | HU Wei, WU Qiuhan, LIU Shengli, et al. Design of Secure eID and Identity Authentication Agreement in Mobile Terminal Based on Guomi Algorithm and Blockchain[J]. Netinfo Security, 2018, 18 (7): 7-15. |
| 胡卫, 吴邱涵, 刘胜利, 等. 基于国密算法和区块链的移动端安全eID及认证协议设计[J]. 信息网络安全, 2018, 18(7): 7-15. | |
| [17] | LI Min, CHEN Fulong, PANG Hui. Vehicle PEPS and EMS Security Certification Based on Encryption Algorithm SM4[J]. Journal of Nanjing University of Information Science & Technology(Natural Science Edition), 2022, 14(5): 543-550. |
| 李敏, 陈付龙, 庞辉. 基于国密算法SM4的车载PEPS和EMS安全认证方法研究[J]. 南京信息工程大学学报(自然科学版), 2022, 14(5): 543-550. | |
| [18] | WANG Xiaoyun, YU Hongbo. SM3 Cryptographic Hash Algorithm[J]. Journal of Information Security Research, 2016, 2(11): 983-994. |
| 王小云, 于红波. SM3密码杂凑算法[J]. 信息安全研究, 2016, 2(11): 983-994. | |
| [19] | SUN Rongyan, CAI Changshu, ZHOU Zhou, et al. The Comparision between Digital Signature Based on SM2 and ECDSA[J]. Network Security Technology & Application, 2013(2): 60-62. |
| 孙荣燕, 蔡昌曙, 周洲, 等. 国密SM2数字签名算法与ECDSA算法对比分析研究[J]. 网络安全技术与应用, 2013(2): 60-62. | |
| [20] | WU Zhihong, ZHAO Jianning, ZHU Yuan, et al. Comparative Study on Application of Chinese Cryptographic Algorithms and International Cryptographic Algorithms in Vehicle Microcotrollers[J]. Netinfo Security, 2019, 19(8): 68-75. |
| 吴志红, 赵建宁, 朱元, 等. 国密算法和国际密码算法在车载单片机上应用的对比研究[J]. 信息网络安全, 2019, 19(8): 68-75. | |
| [21] |
ALI O, JARADAT A, KULAKLI A, et al. A Comparative Study: Blockchain Technology Utilization Benefits, Challenges and Functionalities[J]. IEEE Access, 2021, 9: 12730-12749.
doi: 10.1109/Access.6287639 URL |
| [22] | MA Zhaofeng. Blockchain Technology Development Guide[M]. Beijing: Tsinghua University Press, 2020. |
| 马兆丰. 区块链技术开发指南[M]. 北京: 清华大学出版社, 2020. | |
| [23] |
BHUTTA M N M, KHWAJA A A, NADEEM A, et al. A Survey on Blockchain Technology: Evolution, Architecture and Security[J]. IEEE Access, 2021, 9: 61048-61073.
doi: 10.1109/ACCESS.2021.3072849 URL |
| [24] | WANG Huaqun, WU Tao. Cryptography on the Blockchain[J]. Journal of Nanjing University of Posts and Telecommunications(Natural Science Edition), 2017, 37(6): 61-67. |
| 王化群, 吴涛. 区块链中的密码学技术[J]. 南京邮电大学学报(自然科学版), 2017, 37(6): 61-67. | |
| [25] | YANG Long, HAN Dan, OUYANG Weile. Application of Commercial Cipher Algorithm in Blockchain Technology[J]. Computer Engineering and Applications, 2020(s): 29-35. |
| 杨龙, 韩丹, 欧阳维乐. 商用密码算法在区块链技术中的应用[J]. 计算机工程与应用, 2020(s): 29-35. | |
| [26] | GM/T 0003-2012 SM2 Elliptic Curve Public Key Cryptography:[S]. China: State Cryptography Administration, 2012. |
| GM/T 0003-2012 SM2椭圆曲线公钥密码算法[S]. 中国: 国家密码管理局, 2012. | |
| [27] | WANG Zhaohui, ZHANG Zhenfeng. Overview on Public Key Cryptographic Algorithm SM2 Based on Elliptic Curves[J]. Journal of Information Security Research, 2016, 2(11): 972-982. |
| 汪朝晖, 张振峰. SM2椭圆曲线公钥密码算法综述[J]. 信息安全研究, 2016, 2(11): 972-982. | |
| [28] | YANG Kai. IP Core Design Compatible with DES, AES and SM4 Algorithms[D]. Xi’an: Xidian University, 2017. |
| 杨凯. 兼容DES、AES和SM4算法的IP核设计[D]. 西安: 西安电子科技大学, 2017. | |
| [29] | LYU Shuwang, SU Bozhan, WANG Peng, et al. Overview on SM4 Algorithm[J]. Journal of Information Security Research, 2016, 2(11): 995-1007. |
| 吕述望, 苏波展, 王鹏, 等. SM4分组密码算法综述[J]. 信息安全研究, 2016, 2(11): 995-1007. | |
| [30] | Hyperledger Fabric Official Documentation[EB/OL]. [2022-08-21]. https://hyperledgerfabric.readthedocs.io/en/release-1.4. |
| [31] | XU Xiaoqiong, SUN Gang, LUO Long, et al. Latency Performance Modeling and Analysis for Hyperledger Fabric Blockchain Network[EB/OL]. (2021-01-12)[2022-07-21]. https://xueshu.baidu.com/usercenter/paper/show?paperid=1x5v0gc04w1q0aj0xy3y0cg00v032442&site=xueshu_se. |
| [32] |
CASTRO M, LISKOV B. Practical Byzantine Fault Tolerance and Proactive Recovery[J]. ACM Transactions on Computer Systems, 2002, 20(4): 398-461.
doi: 10.1145/571637.571640 URL |
| [33] | CAO Qi, RUAN Shuhua, CHEN Xingshu, et al. Embedding of National Cryptographic Algorithm in Hyperledger Fabric[J]. Chinese Journal of Network and Information Security, 2021, 7(1): 65-75. |
| 曹琪, 阮树骅, 陈兴蜀, 等. Hyperledger Fabric平台的国密算法嵌入研究[J]. 网络与信息安全学报, 2021, 7(1): 65-75. | |
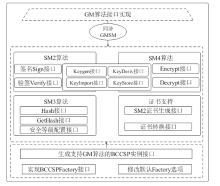
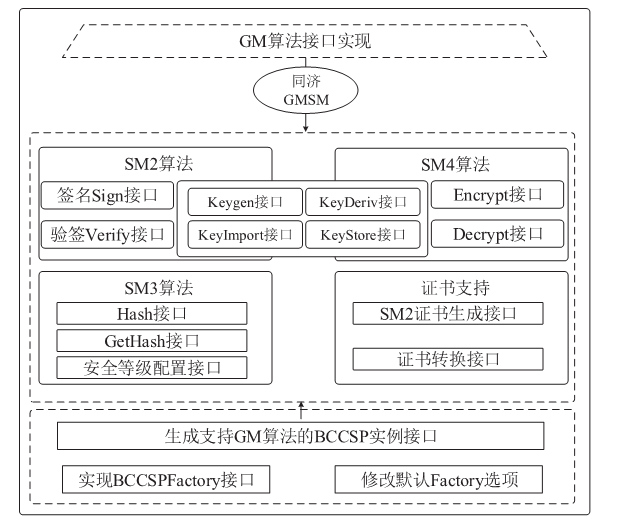
| [34] | Tongji Blockchain Research Institute. Implementation of State Secret SM2, SM3 and SM4 algorithms[EB/OL]. [2022-08-21]. https://github.com/tjfoc/gmsm. |
| 同济区块链研究院. 国密 SM2、SM3 和 SM4 算法实现[EB/OL]. [2022-08-21]. https://github.com/tjfoc/gmsm. | |
| [35] | Tongji Blockchain Research Institute. TLS/SSL Code Based on National Secret Algorithm[EB/OL]. [2022-08-26]. https://github.com/tjfoc/gmtls. |
| 同济区块链研究院. 基于国密算法的TLS/SSL代码库[EB/OL]. [2022-08-26]. https://github.com/tjfoc/gmtls. | |
| [36] |
LI Yanfeng, DING Liping, WU Jingzheng, et al. Research on a New Network Covert Channel Model in Blockchain Environment[J]. Journal on Communications, 2019, 40(5): 67-78.
doi: 10.11959/j.issn.1000-436x.2019111 |
|
李彦峰, 丁丽萍, 吴敬征, 等. 区块链环境下的新型网络隐蔽信道模型研究[J]. 通信学报, 2019, 40(5): 67-78.
doi: 10.11959/j.issn.1000-436x.2019111 |
| [1] | 郭瑞, 魏鑫, 陈丽. 工业物联网环境下可外包的策略隐藏属性基加密方案[J]. 信息网络安全, 2023, 23(3): 1-12. |
| [2] | 李春晓, 王耀飞, 徐恩亮, 赵钰. 基于双线性映射的区块链安全范围搜索技术研究[J]. 信息网络安全, 2023, 23(3): 22-34. |
| [3] | 李晓华, 王苏杭, 李凯, 徐剑. 一种支持隐私保护的传染病人际传播分析模型[J]. 信息网络安全, 2023, 23(3): 35-44. |
| [4] | 张学旺, 张豪, 姚亚宁, 付佳丽. 基于群签名和同态加密的联盟链隐私保护方案[J]. 信息网络安全, 2023, 23(3): 56-61. |
| [5] | 冯怡婷, 马兆丰, 徐单恒, 段鹏飞. 跨链接入的区块链安全强度评估方法[J]. 信息网络安全, 2023, 23(1): 84-92. |
| [6] | 于晶, 袁曙光, 袁煜琳, 陈驰. 基于k匿名数据集的鲁棒性水印技术研究[J]. 信息网络安全, 2022, 22(9): 11-20. |
| [7] | 张光华, 刘永升, 王鹤, 于乃文. 基于BiLSTM和注意力机制的智能合约漏洞检测方案[J]. 信息网络安全, 2022, 22(9): 46-54. |
| [8] | 张学旺, 刘宇帆. 可追踪身份的物联网感知层节点匿名认证方案[J]. 信息网络安全, 2022, 22(9): 55-62. |
| [9] | 胡艺, 佘堃. 基于区块链和智能合约的双链车联网系统[J]. 信息网络安全, 2022, 22(8): 26-35. |
| [10] | 黄保华, 赵伟宏, 彭丽, 谢统义. 基于MPT索引的高效链上PKI模型[J]. 信息网络安全, 2022, 22(8): 72-80. |
| [11] | KELEKET GOMA Christy Junior Yannick, 易文哲, 王鹃. 一种基于SGX的轻量Fabric链码可信执行环境构建方法[J]. 信息网络安全, 2022, 22(7): 73-83. |
| [12] | 秦宝东, 余沛航, 郑东. 基于双陷门同态加密的决策树分类模型[J]. 信息网络安全, 2022, 22(7): 9-17. |
| [13] | 王姝爽, 马兆丰, 刘嘉微, 罗守山. 区块链跨链安全接入与身份认证方案研究与实现[J]. 信息网络安全, 2022, 22(6): 61-72. |
| [14] | 于克辰, 郭莉, 阴宏伟, 燕雪松. 面向数据中心场景的基于区块链与博弈论的高价值数据共享模型[J]. 信息网络安全, 2022, 22(6): 73-85. |
| [15] | 冯景瑜, 张琪, 黄文华, 韩刚. 基于跨链交互的网络安全威胁情报共享方案[J]. 信息网络安全, 2022, 22(5): 21-29. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||