信息网络安全 ›› 2023, Vol. 23 ›› Issue (3): 35-44.doi: 10.3969/j.issn.1671-1122.2023.03.004
一种支持隐私保护的传染病人际传播分析模型
- 1.东北大学计算机科学与工程学院,沈阳110169
2.东北大学软件学院,沈阳 110169
3.国网新疆电力有限公司信息通信公司,乌鲁木齐 830002
4.中国科学院信息工程研究所信息安全国家重点实验室,北京 100093
-
收稿日期:2022-12-28出版日期:2023-03-10发布日期:2023-03-14 -
通讯作者:王苏杭 E-mail:1058348091@qq.com -
作者简介:李晓华(1969—),女,辽宁,副教授,博士,主要研究方向为信息安全与隐私保护|王苏杭(1997—),男,湖北,硕士研究生,主要研究方向为网络与信息安全|李凯(1988—)男,辽宁,高级工程师,硕士,主要研究方向为信息安全、电网数字化|徐剑(1978—),男,辽宁,教授,博士,主要研究方向为网络与信息安全 -
基金资助:国家自然科学基金(61872069);国家自然科学基金(61991404);国家科技重大专项(J2019-IV-0002-0069)
A Privacy-Preserving Analysis Model of Human-to-Human Transmission of Infectious Diseases
LI Xiaohua1, WANG Suhang2( ), LI Kai3, XU Jian2,4
), LI Kai3, XU Jian2,4
- 1. School of Computer Science and Engineering, Northeastern University, Shenyang 110169, China
2. Software College, Northeastern University, Shenyang 110169, China
3. State Grid Xinjiang Information and Telecommunication Company, Urumqi 830002, China
4. State Key Laboratory of Information Security, Institute of Information Engineering, Chinese Academy of Sciences, Beijing 100093, China
-
Received:2022-12-28Online:2023-03-10Published:2023-03-14 -
Contact:WANG Suhang E-mail:1058348091@qq.com
摘要:
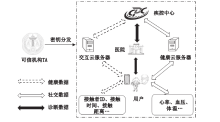
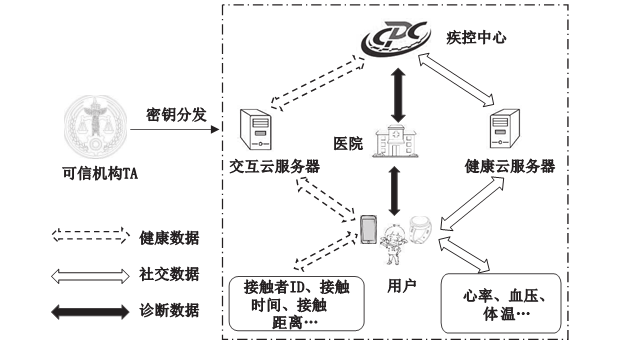
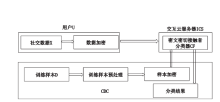
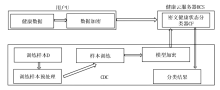
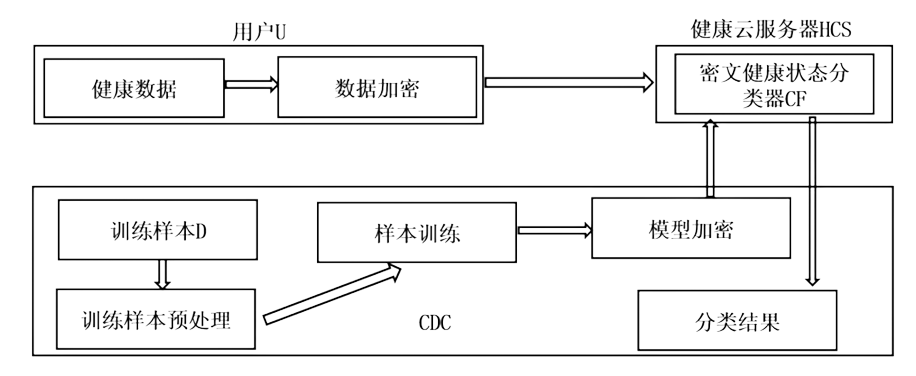
随着万物互联和大数据时代的到来,通过线下交互数据追踪传染病患者的密切接触者,利用健康数据对密切接触者的健康状态进行持续监测,为传染病人际传播分析带来了新的研究视角,为阻断传染病的传播提供了新的处理方式。然而,此类方法也存在较为严重的隐私泄露问题。为此,文章设计了基于线下交互和健康数据的传染病人际传播分析模型(Analysis Model of Human-to-Human Transmission of Infectious Diseases Based on Offline Interaction and Health Data,AMHHTID-OIHD)。该模型由可信机构、健康云服务器、交互云服务器、疾控中心、医院和用户6种实体组成,在支持隐私保护的同时实现CDC查找该患者的密切接触者并对其进行健康状态分类。文章以KNN分类和高斯朴素贝叶斯分类为基础,结合同态加密技术,设计了支持AMHHTID-OIHD的隐私保护密切接触者查找算法和隐私保护健康状态分类算法。最后,对该模型的安全性进行分析,结果表明该模型可以在保护隐私的情况下实现密切接触者查找和健康状态分类。
中图分类号:
引用本文
李晓华, 王苏杭, 李凯, 徐剑. 一种支持隐私保护的传染病人际传播分析模型[J]. 信息网络安全, 2023, 23(3): 35-44.
LI Xiaohua, WANG Suhang, LI Kai, XU Jian. A Privacy-Preserving Analysis Model of Human-to-Human Transmission of Infectious Diseases[J]. Netinfo Security, 2023, 23(3): 35-44.
| [1] |
ZHANG Nan, CHEN Wenzhao, CHAN P T, et al. Close Contact Behavior in Indoor Environment and Transmission of Respiratory Infection[J]. Indoor Air, 2020, 30(4): 645-661.
doi: 10.1111/ina.12673 pmid: 32259319 |
| [2] | LIANG Di, CUI Jing, LI Xiang. A Review of Offline Interaction in Dynamic Social Networks: Challenge and Prospect[J]. Chinese Journal of Computers, 2018, 41(7): 1598-1618. |
| 梁迪, 崔靖, 李翔. 线下交互的动态社交网络研究进展:挑战与展望[J]. 计算机学报, 2018, 41(7): 1598-1618. | |
| [3] | SMIESZEK T, BURRI E U, SCHERZINGER R, et al. Collecting Close-Contact Social Mixing Data with Contact Diaries: Reporting Errors and Biases[J]. Epidemiology & Infection, 2012, 140(4): 744-752. |
| [4] | TAN Weijun, LIU Jingfeng. Application of Face Recognition in Tracing COVID-19 Fever Patients and Close Contacts[C]// IEEE. 19th IEEE International Conference on Machine Learning and Applications (ICMLA). New York: IEEE, 2020: 1112-1116. |
| [5] | PDNN S, NOORDEEN F, KURUKULASURIYA H, et al. Effect of Climatic Factors and Population Density on the Distribution of Dengue in Sri Lanka: A GIS Based Evaluation for Prediction of Outbreaks[EB/OL]. (2017-07-09)[2022-12-12]. https://doi.org/10.1371/journal.pone.0166806. |
| [6] |
LI Qiaoxuan, CAO Wei, REN Hongyan, et al. Spatiotemporal Responses of Dengue Fever Transmission to the Road Network in an Urban Area[J]. Acta tropica, 2018, 183: 8-13.
doi: S0001-706X(17)31129-4 pmid: 29608873 |
| [7] | HO T S, WENG T C, WANG J D, et al. Comparing Machine Learning with Case-Control Models to Identify Confirmed Dengue Cases[EB/OL]. (2020-10-10)[2022-12-20]. https://doi.org/10.1371/journal.pntd.0008843. |
| [8] | WENG S F, REPS J, KAI J, et al. Can Machine-Learning Improve Cardiovascular Risk Prediction Using Routine Clinical Data?[EB/OL]. (2017-04-04)[2022-12-06]. https://doi.org/10.1371/journal.pone.0174944. |
| [9] |
AN C, LIM H, KIM D-W, et al. Machine Learning Prediction for Mortality of Patients Diagnosed with COVID-19: A Nationwide Korean Cohort Study[J]. Scientific Reports, 2020, 10(1): 1-11.
doi: 10.1038/s41598-019-56847-4 |
| [10] |
BANOEI M M, DINPARASTISALEH R, ZADEH A V, et al. Machine-Learning-Based COVID-19 Mortality Prediction Model and Identification of Patients at Low and High Risk of Dying[J]. Critical Care, 2021, 25(1): 1-14.
doi: 10.1186/s13054-020-03448-7 |
| [11] |
GAO Y, CAI G Y, FANG W, et al. Machine Learning Based Early Warning System Enables Accurate Mortality Risk Prediction for COVID-19[J]. Nature Communications, 2020, 11(1): 1-10.
doi: 10.1038/s41467-019-13993-7 |
| [12] | CHAE S, KWON S, LEE D. Predicting Infectious Disease Using Deep Learning and Big Data[EB/OL]. (2018-07-27) [2022-11-15] https://doi.org/10.3390/ijerph15081596. |
| [13] | YANG Xu, SHI Chenqi, LI Peihao, et al. Toward COVID-19 Contact Tracing Though Wi-Fi Probes[EB/OL]. (2022-03-14) [2022-11-30] https://doi.org/10.3390/s22062255. |
| [14] | WALRAVE M, WAETERLOOS C, PONNET K. Adoption of a Contact Tracing App for Containing COVID-19: A Health Belief Model Approach[J]. Jmir Public Health and Surveillance, 2020, 6(3): 488-497. |
| [15] | HINCH R, PROBERT W, NURTAY A, et al. Effective Configurations of a Digital Contact Tracing App: A Report to NHSX[EB/OL]. (2020-04-15) [2022-12-12] https://github.com/BDIpathogens/covid-19_instant_tracing/blob/master/Report. |
| [16] | DIAS D, CUNHA J P S. Wearable Health Devices-Vital Sign Monitoring, Systems and Technologies[EB/OL]. (2018-07-25) [2022-12-20] https://doi.org/10.3390/s18082414. |
| [17] |
KAISSIS G A, MAKOWSKI M R, RUCKERT D, et al. Secure, Privacy-Preserving and Federated Machine Learning in Medical Imaging[J]. Nature Machine Intelligence, 2020, 2(6): 305-311.
doi: 10.1038/s42256-020-0186-1 |
| [18] | MUNJAL K, BHATIA R. A Systematic Review of Homomorphic Encryption and its Contributions in Healthcare Industry[EB/OL]. (2022-05-03) [2022-11-16] https://10.1007/s40747-022-00756-z. |
| [19] |
JAGADEESH K A, WU D J, BIRGMEIER J A, et al. Deriving Genomic Diagnoses Without Revealing Patient Genomes[J]. Science, 2017, 357: 692-695.
doi: 10.1126/science.aam9710 pmid: 28818945 |
| [20] | ZHOU Yicong, PANETTA K, AGAIAN S. A Lossless Encryption Method for Medical Images Using Edge Maps[C]// IEEE. 31st Annual International Conference of the IEEE Engineering in Medicine and Biology Society. New York: IEEE, 2009: 3707-3710. |
| [21] |
VENGADAPURVAJA A, NISHA G, AARTHY R, et al. An Efficient Homomorphic Medical Image Encryption Algorithm for Cloud Storage Security[J]. Procedia Computer Science, 2017, 115: 643-650.
doi: 10.1016/j.procs.2017.09.150 URL |
| [22] |
CAUCHEMEZ S, BHATTARAI A, MARCHBANKS T L, et al. Role of Social Networks in Shaping Disease Transmission During a Community Outbreak of 2009 H1N1 Pandemic Influenza[J]. National Academy of Sciences, 2011, 108(7): 2825-2830.
doi: 10.1073/pnas.1008895108 URL |
| [23] | CHEN Yi, WANG Aihong, YI Bo, et al. Epidemiological Characteristics of Infection in COVID-19 Close Contacts in Ningbo City[J]. Chinese Journal of Epidemiology, 2020, 41(5): 667-671. |
| 陈奕, 王爱红, 易波, 等. 宁波市新型冠状病毒肺炎密切接触者感染流行病学特征分析[J]. 中华流行病学杂志, 2020, 41(5): 667-671. | |
| [24] |
THARAKAN S, NOMOTO K, MIYASHITA S, et al. Body Temperature Correlates with Mortality in COVID-19 Patients[J]. Critical Care, 2020, 24(1): 1-3.
doi: 10.1186/s13054-019-2683-3 |
| [25] |
XIE Yan, XU E, BOWE B, et al. Long-Term Cardiovascular Outcomes of COVID-19[J]. Nature Medicine, 2022, 28(3): 583-590.
doi: 10.1038/s41591-022-01689-3 |
| [1] | 郭瑞, 魏鑫, 陈丽. 工业物联网环境下可外包的策略隐藏属性基加密方案[J]. 信息网络安全, 2023, 23(3): 1-12. |
| [2] | 张学旺, 张豪, 姚亚宁, 付佳丽. 基于群签名和同态加密的联盟链隐私保护方案[J]. 信息网络安全, 2023, 23(3): 56-61. |
| [3] | 王晶宇, 马兆丰, 徐单恒, 段鹏飞. 支持国密算法的区块链交易数据隐私保护方案[J]. 信息网络安全, 2023, 23(3): 84-95. |
| [4] | 于晶, 袁曙光, 袁煜琳, 陈驰. 基于k匿名数据集的鲁棒性水印技术研究[J]. 信息网络安全, 2022, 22(9): 11-20. |
| [5] | 张学旺, 刘宇帆. 可追踪身份的物联网感知层节点匿名认证方案[J]. 信息网络安全, 2022, 22(9): 55-62. |
| [6] | 秦宝东, 余沛航, 郑东. 基于双陷门同态加密的决策树分类模型[J]. 信息网络安全, 2022, 22(7): 9-17. |
| [7] | 陈彬杰, 魏福山, 顾纯祥. 基于KNN的具有隐私保护功能的区块链异常交易检测[J]. 信息网络安全, 2022, 22(3): 78-84. |
| [8] | 王思蝶, 马兆丰, 罗守山, 徐单恒. 面向异构多链的区块链链上数据隐私保护方案[J]. 信息网络安全, 2022, 22(12): 67-75. |
| [9] | 晏燕, 张雄, 冯涛. 大数据统计划分发布的等比差分隐私预算分配方法[J]. 信息网络安全, 2022, 22(11): 24-35. |
| [10] | 梁广俊, 辛建芳, 倪雪莉, 马卓. 智能音箱安全与取证研究[J]. 信息网络安全, 2022, 22(10): 108-113. |
| [11] | 顾海艳, 蒋铜, 马卓, 朱季鹏. k-匿名改进算法及其在隐私保护中的应用研究[J]. 信息网络安全, 2022, 22(10): 52-58. |
| [12] | 徐硕, 张睿, 夏辉. 基于数据属性修改的联邦学习隐私保护策略[J]. 信息网络安全, 2022, 22(1): 55-63. |
| [13] | 路宏琳, 王利明, 杨婧. 一种新的参数掩盖联邦学习隐私保护方案[J]. 信息网络安全, 2021, 21(8): 26-34. |
| [14] | 靳姝婷, 何泾沙, 朱娜斐, 潘世佳. 基于本体推理的隐私保护访问控制机制研究[J]. 信息网络安全, 2021, 21(8): 52-61. |
| [15] | 刘子昂, 黄缘缘, 马佳利, 周睿. 基于区块链的医疗数据滥用监控平台设计与实现[J]. 信息网络安全, 2021, 21(5): 58-66. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||