信息网络安全 ›› 2022, Vol. 22 ›› Issue (12): 25-33.doi: 10.3969/j.issn.1671-1122.2022.12.004
一种基于切比雪夫混沌映射的可证明安全的溯源认证协议
- 1.北京工业大学信息学部,北京 100124
2.济宁学院数学与计算机应用技术学院,曲阜 272000
-
收稿日期:2022-08-10出版日期:2022-12-10发布日期:2022-12-30 -
通讯作者:孙光民 E-mail:gmsun@bjut.edu.cn -
作者简介:张昱(1978—),男,山东,博士研究生,主要研究方向为网络安全|孙光民(1960—),男,山西,教授,博士,主要研究方向为神经网络、网络安全|翟鹏(1978—),男,山东,博士研究生,主要研究方向为网络安全、区块链技术|李煜(1986—),男,北京,副教授,博士,主要研究方向为模式识别、深度学习及应用 -
基金资助:国家自然科学基金(41706201)
A Provably Secure Traceability Authentication Protocol Based on Chebyshev Chaotic Map
ZHANG Yu1,2, SUN Guangmin1( ), ZHAI Peng1,2, LI Yu1
), ZHAI Peng1,2, LI Yu1
- 1. Faculty of Information Technology, Beijing University of Technology, Beijing 100124, China
2. School of Mathematics and Computer Application Technology, Jining University, Qufu 272000, China
-
Received:2022-08-10Online:2022-12-10Published:2022-12-30 -
Contact:SUN Guangmin E-mail:gmsun@bjut.edu.cn
摘要:
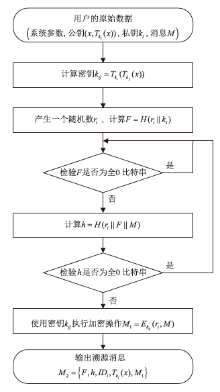
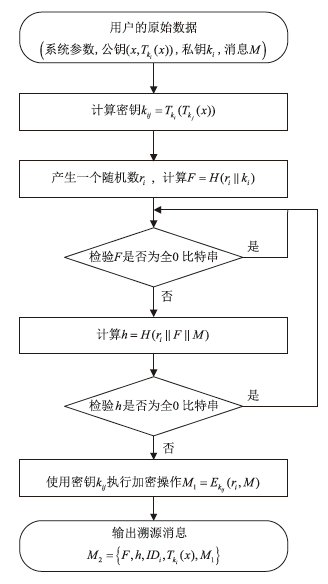
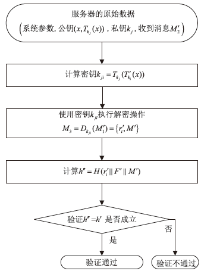
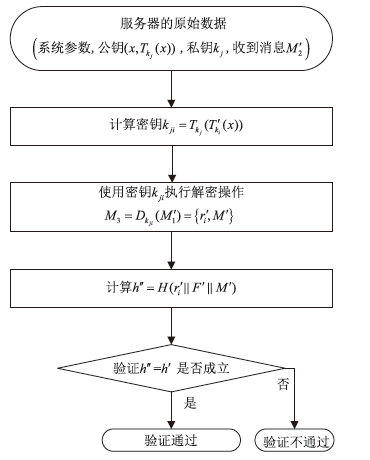
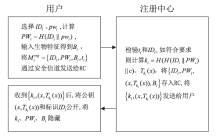
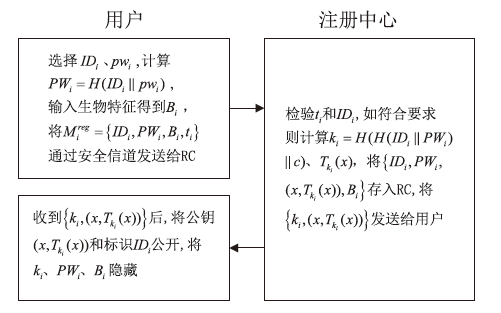
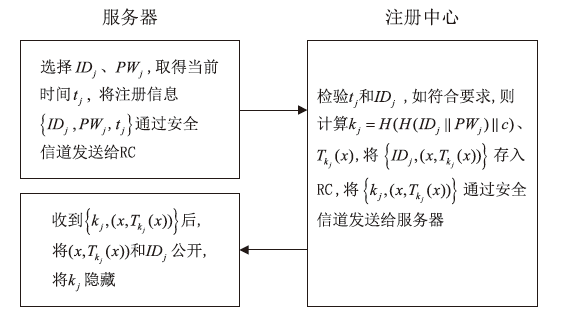
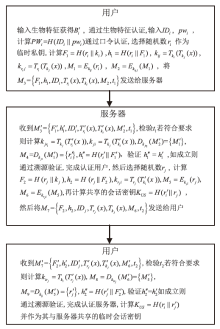
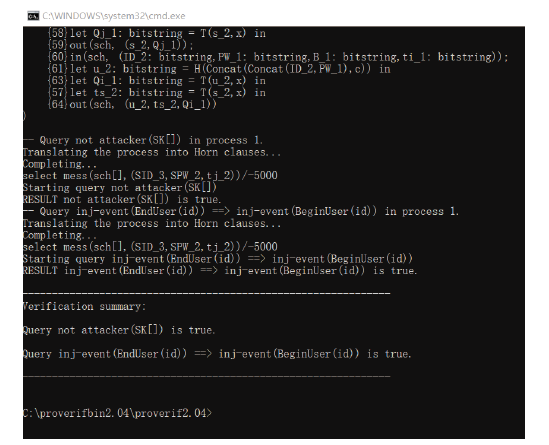
为降低计算开销,提高安全性,文章利用哈希函数的不可逆性和切比雪夫混沌映射的半群特性设计了一种溯源验证算法,并基于该算法设计了注册中心(Registry Centre,RC)离线模式的身份认证协议。文章提出的方案将传统的口令与生物特征、公钥密码相结合,实现了三因素认证和双向溯源认证,并且不需要注册中心参与认证过程。文章在认证方案中设计了双密钥双重加密机制,通过计算得到一次性密钥,传输的信息使用一次性密钥进行加密,能够有效降低计算开销,实现密文传输、隐私保护和前向安全。通过安全性分析、BAN逻辑证明、ProVerif工具仿真验证表明,文章提出的协议是安全的;与其他同类方案相比,文章所提方案更安全、更高效,适用于资源有限的移动互联网络环境。
中图分类号:
引用本文
张昱, 孙光民, 翟鹏, 李煜. 一种基于切比雪夫混沌映射的可证明安全的溯源认证协议[J]. 信息网络安全, 2022, 22(12): 25-33.
ZHANG Yu, SUN Guangmin, ZHAI Peng, LI Yu. A Provably Secure Traceability Authentication Protocol Based on Chebyshev Chaotic Map[J]. Netinfo Security, 2022, 22(12): 25-33.
表1
符号定义
| 符号 | 意义 | 符号 | 意义 |
|---|---|---|---|
| RC | 注册中心 | 服务器的公钥和 私钥 | |
| 注册中心的公钥和私钥 | Hash函数 | ||
| 一个大素数 | 密钥为 | ||
| 用户 | 密钥为 | ||
| 用户 | 随机数 | ||
| 用户的公钥和私钥 | 有效时间间隔 | ||
| 用户 | || | 比特串拼接 | |
| 服务器 标识 | 当前时间 | ||
| 服务器 口令 | 共享的临时会话 密钥 |
表3
BAN逻辑组件的语法和语义
| 符号 | 意义 |
|---|---|
| 主体 | |
| 主体 | |
| 主体 | |
| 主体 | |
| 用密钥 | |
| 消息 |
表4
BAN逻辑的推理规则
| 序号 | 规则 |
|---|---|
| R1 | |
| R2 | |
| R3 | |
| R4 | |
| R5 | |
| R6 | |
| R7 | |
| R8 | |
| R9 | |
| R10 | |
| R11 | |
| R12 | |
| R13 | |
| R14 | |
| R15 | |
| R16 | |
| R17 | |
| R18 | |
| R19 |
表5
执行时间对比(单位:ms)
| 方案 | 注册阶段 | 登录、认证、密钥协商阶段 | 口令更改阶段 |
|---|---|---|---|
| 文献[ | 3TH+TGen=404 | 12TH+6TC+8TE+ TGen=422.5 | 2TH+TGen=403.5 |
| 文献[ | 9TH+TGen=407 | 21TH+TRep+ 4TC=108 | 8TH+TRep+TGen=500 |
| 文献[ | 11TH+9TP+ 4TA=600.5 | 17TH+7TP+ 7TA=638.5 | 6TH+4TP+2TA=269 |
| 文献[ | TH+TECC=484.5 | 4TH+7TECC=3390 | 2TH+TECC+4TE=489 |
| 本文方案 | 4TH+2TC+TF=19 | 8TH+6TC+4TE+ 4TD+TB+TF=33 | 5TH+2TC+TB+TF=19.5 |
| [1] | ZHU Hongfeng, HAO Xin, ZHANG Yifeng, et al. A Biometrics-Based Multi-Server Key Agreement Scheme on Chaotic Maps Cryptosystem[J]. Journal of Information Hiding and Multimedia Signal Processing, 2015, 6(2): 211-224. |
| [2] |
JIANG Qi, WEI Fushan, FU Shuai, et al. Robust Extended Chaotic Maps-Based Three-Factor Authentication Scheme Preserving Biometric Template Privacy[J]. Nonlinear Dynamics, 2016, 83(4): 2085-2101.
doi: 10.1007/s11071-015-2467-5 URL |
| [3] |
ALI R, PAL A. A Secure and Robust Three-Factor Based Authentication Scheme Using RSA Cryptosystem[J]. International Journal of Business Data Communications and Networking, 2017, 13(1): 74-84.
doi: 10.4018/IJBDCN.2017010107 URL |
| [4] | ZHANG Min. Research and Design of Remote Identity Authentication Schemes Based on Three-Factor in Multi-Environments[D]. Chengdu: Southwest Jiaotong University, 2017. |
| 张敏. 多环境下基于三因素的远程身份认证协议研究与设计[D]. 成都: 西南交通大学, 2017. | |
| [5] | DONG Xiaolu, LI Meihong, DU Ye, et al. A Biometric Verification Based Authentication Scheme Using Chebyshev Chaotic Mapping[J]. Journal of Beijing University of Aeronautics and Astronautics, 2019, 45(5): 1052-1058. |
| 董晓露, 黎妹红, 杜晔, 等. 基于切比雪夫混沌映射和生物识别的身份认证方案[J]. 北京航空航天大学学报, 2019, 45(5): 1052-1058. | |
| [6] |
ZHOU Simin, GAN Qingqing, WANG Xiaoming. Authentication Scheme Based on Smart Card in Multi-Server Environment[J]. Wireless Networks, 2020, 26(2): 855-863.
doi: 10.1007/s11276-018-1828-7 URL |
| [7] |
LWAMO N, ZHU Lihuang, XU Chang, et al. Suaa: A Secure User Authentication Scheme with Anonymity for the Single & Multi-Server Environments[J]. Information Sciences, 2018, 477: 369-385.
doi: 10.1016/j.ins.2018.10.037 URL |
| [8] |
ROY S, DAS A, CHATTERJEE S, et al. Provably Secure Fine-Grained Data Access Control over Multiple Cloud Servers in Mobile Cloud Computing Based Healthcare Applications[J]. IEEE Transactions on Industrial Informatics, 2019, 15(1): 457-468.
doi: 10.1109/TII.2018.2824815 URL |
| [9] |
CHATTERJEE S, ROY S, DAS A, et al. Secure Biometric-Based Authentication Scheme Using Chebyshev Chaotic Map for Multi-Server Environment[J]. IEEE Transactions on Dependable and Secure Computing, 2018, 15(5): 824-839.
doi: 10.1109/TDSC.2016.2616876 URL |
| [10] | LUO Yuling, LIU Yunqi, LIU Junxiu, et al. ECM-IBS: A Chebyshev Map-Based Broadcast Authentication for Wireless Sensor Networks[J]. International Journal of Bifurcation and Chaos, 2019, 29(9): 1-16. |
| [11] |
RANGWANI D, SADHUKHAN D, RAY S, et al. A Robust Provable-Secure Privacy-Preserving Authentication Protocol for Industrial Internet of Things[J]. Peer-to-peer Networking and Applications, 2021, 14(12): 1548-1571.
doi: 10.1007/s12083-020-01063-5 URL |
| [12] | XU Zhiqiang, HE Debiao, HUANG Xinyi. Secure and Efficient Two-Factor Authentication Protocol Using RSA Signature for Multi-Server Environments[C]// Springer. International Conference on Information and Communications Security. Berlin:Springer, 2017: 595-605. |
| [13] |
BARMAN S, SHUM, H, CHATTOPADHYAY S, et al. A Secure Authentication Protocol for Multi-Server-Based E-Healthcare Using a Fuzzy Commitment Scheme[J]. IEEE Access, 2019, 7: 12557-12574.
doi: 10.1109/ACCESS.2019.2893185 URL |
| [14] | ZHANG Xiao, LIU Jiqiang. Multi-Factor Authentication Protocol Based on Hardware Fingerprint and Biometrics[J]. Netinfo Security, 2020, 20(8): 9-15. |
| 张骁, 刘吉强. 基于硬件指纹和生物特征的多因素身份认证协议[J]. 信息网络安全, 2020, 20(8): 9-15. | |
| [15] | NAMASUDR S, ROY P. A New Secure Authentication Scheme for Cloud Computing Environment[J]. Concurrency and Computation: Practice and Experience, 2017, 29(20): 1-20. |
| [16] | KOCAREV L, TASEV Z. Public-Key Encryption Based on Chebyshev Maps[C]// IEEE. International Symposium on Circuits and Systems. New York: IEEE, 2003: 25-28. |
| [17] |
ZHANG Linhua. Cryptanalysis of the Public Key Encryption Based on Multiple Chaotic Systems[J]. Chaos, Solitons and Fractals, 2008, 37(3): 669-674.
doi: 10.1016/j.chaos.2006.09.047 URL |
| [18] | LIU Tianhua, WANG Qian, ZHU Hongfeng. A Multi-Function Password Mutual Authentication Key Agreement Scheme with Privacy Preserving[J]. Journal of Information Hiding and Multimedia Signal Processing, 2014, 5(2): 165-178. |
| [19] | BURROWS M, ABADI M, NEEDHAM R. A Logic of Authentication[J]. Proceedings of the Royal Society, 1989, 426: 233-271. |
| [20] |
SHUAI Mengxia, XIONG Ling, WANG Changhui, et al. A Secure Authentication Scheme with Forward Secrecy for Industrial Internet of Things Using Rabin Cryptosystem[J]. Computer Communications, 2020, 160(7): 215-227.
doi: 10.1016/j.comcom.2020.06.012 URL |
| [21] |
LEE C. A Simple Key Agreement Scheme Based on Chaotic Maps for VSAT Satellite Communications[J]. International Journal of Satellite Communications and Networking, 2013, 31(4): 177-186.
doi: 10.1002/sat.1033 URL |
| [22] |
ODELU V, DAS A, GOSWAMI A. A Secure Biometrics-Based Multi-Server Authentication Protocol Using Smart Cards[J]. IEEE Transactions on Information Forensics and Security, 2015, 10(9): 1953-1966.
doi: 10.1109/TIFS.2015.2439964 URL |
| [23] |
ZHANG Min, ZHANG Jiashu, ZHANG Ying. Remote Three-Factor Authentication Scheme Based on Fuzzy Extractors[J]. Security and Communication Networks, 2015, 8(4): 682-693.
doi: 10.1002/sec.1016 URL |
| [24] | CHEN Sheng, LIU Yang, GAO Xiang, et al. MobileFaceNets: Efficient CNNs for Accurate Real-Time Face Verification on Mobile Devices[C]// Springer. Chinese Conference on Biometric Recognition. Berlin:Springer, 2018: 428-438. |
| [25] |
MO Jiaqing, HU Zhongwang, SHEN Wei. A Provably Secure Three-Factor Authentication Protocol Based on Chebyshev Chaotic Mapping for Wireless Sensor Network[J]. IEEE Access, 2022, 10: 12137-12152.
doi: 10.1109/ACCESS.2022.3146393 URL |
| [1] | 张敏, 许春香, 张建华. 无人机网络中基于多因子的认证密钥协商协议研究[J]. 信息网络安全, 2022, 22(9): 21-30. |
| [2] | 王姝爽, 马兆丰, 刘嘉微, 罗守山. 区块链跨链安全接入与身份认证方案研究与实现[J]. 信息网络安全, 2022, 22(6): 61-72. |
| [3] | 吴克河, 程瑞, 姜啸晨, 张继宇. 基于SDP的电力物联网安全防护方案[J]. 信息网络安全, 2022, 22(2): 32-38. |
| [4] | 吴克河, 程瑞, 郑碧煌, 崔文超. 电力物联网安全通信协议研究[J]. 信息网络安全, 2021, 21(9): 8-15. |
| [5] | 沈卓炜, 高鹏, 许心宇. 基于安全协商的DDS安全通信中间件设计[J]. 信息网络安全, 2021, 21(6): 19-25. |
| [6] | 张昱, 孙光民, 李煜. 基于SM9算法的移动互联网身份认证方案研究[J]. 信息网络安全, 2021, 21(4): 1-9. |
| [7] | 王健, 赵曼莉, 陈志浩, 石波. 基于假名的智能交通条件隐私保护认证协议[J]. 信息网络安全, 2021, 21(4): 49-61. |
| [8] | 李桐, 周小明, 任帅, 徐剑. 轻量化移动边缘计算双向认证协议[J]. 信息网络安全, 2021, 21(11): 58-64. |
| [9] | 肖帅, 张翰林, 咸鹤群, 陈飞. 一种面向物联网设备的口令认证密钥协商协议[J]. 信息网络安全, 2021, 21(10): 83-89. |
| [10] | 张骁, 刘吉强. 基于硬件指纹和生物特征的多因素身份认证协议[J]. 信息网络安全, 2020, 20(8): 9-15. |
| [11] | 刘晓芬, 陈晓峰, 连桂仁, 林崧. 基于d级单粒子的可认证多方量子秘密共享协议[J]. 信息网络安全, 2020, 20(3): 51-55. |
| [12] | 张正, 查达仁, 柳亚男, 方旭明. 基于物理不可克隆函数的Kerberos扩展协议及其形式化分析[J]. 信息网络安全, 2020, 20(12): 91-97. |
| [13] | 刘利娟, 李志慧, 支丹利. 可实现身份认证的多方量子密钥分发协议[J]. 信息网络安全, 2020, 20(11): 59-66. |
| [14] | 张富友, 王琼霄, 宋利. 基于生物特征识别的统一身份认证系统研究[J]. 信息网络安全, 2019, 19(9): 86-90. |
| [15] | 张顺, 陈张凯, 梁风雨, 石润华. 基于Bell态的量子双向身份认证协议[J]. 信息网络安全, 2019, 19(11): 43-48. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||