信息网络安全 ›› 2021, Vol. 21 ›› Issue (6): 1-10.doi: 10.3969/j.issn.1671-1122.2021.06.001
• 等级保护 • 下一篇
一种基于SGX的工业物联网身份认证协议
- 1. 兰州大学信息科学与工程学院,兰州 730000
2. 应急管理部通信信息中心,北京 100013
-
收稿日期:2021-03-08出版日期:2021-06-10发布日期:2021-07-01 -
通讯作者:刘忻 E-mail:xinl@lzu.edu.cn -
作者简介:刘忻(1988—),男,甘肃,讲师,博士,主要研究方向为认证协议、零信任体系架构、机密计算|郭振斌(1994—),男,山东,硕士研究生,主要研究方向为认证协议、机密计算|宋宇宸(1991—),男,北京,工程师,硕士,主要研究方向为区块链、机器学习、无线传感器网络 -
基金资助:中央高校基本科研业务费专项资金(lzujbky-2020-6);甘肃省科技计划项目(20YF3FA024);兰州市科技计划项目(2019-4-47)
An Authentication Scheme Based on SGX for Industrial Internet of Things
LIU Xin1( ), GUO Zhenbin1, SONG Yuchen2
), GUO Zhenbin1, SONG Yuchen2
- 1. School of Information Science & Engineering, Lanzhou University, Lanzhou 730000, China;
2. Ministry of Emergency Management Communication and Information Center, Beijing 100013, China
-
Received:2021-03-08Online:2021-06-10Published:2021-07-01 -
Contact:LIU Xin E-mail:xinl@lzu.edu.cn
摘要:
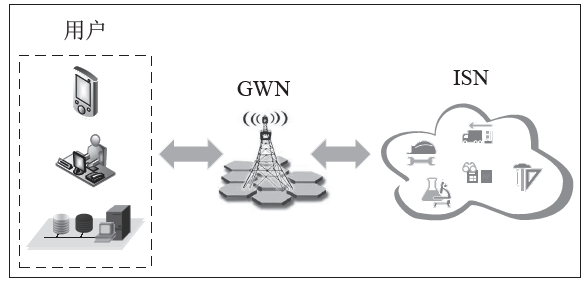
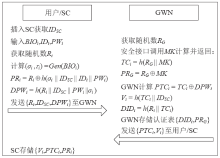
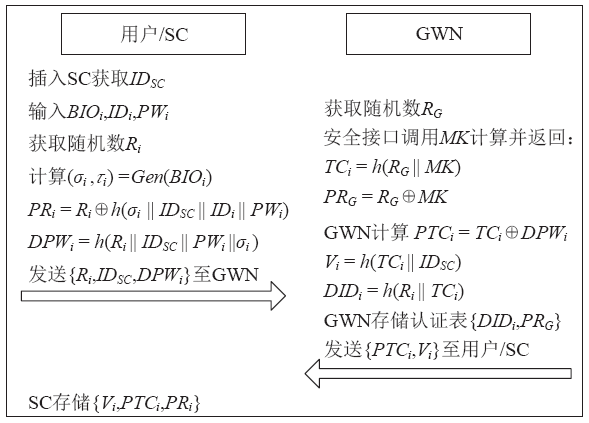
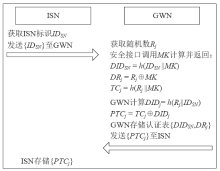
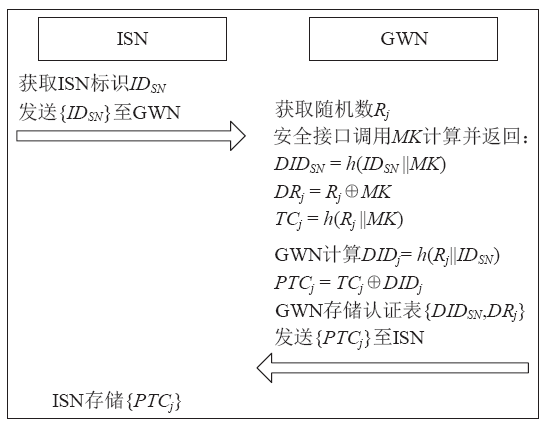
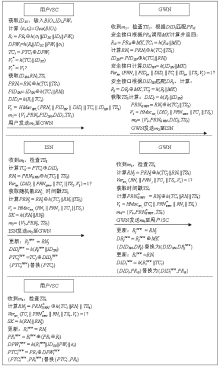
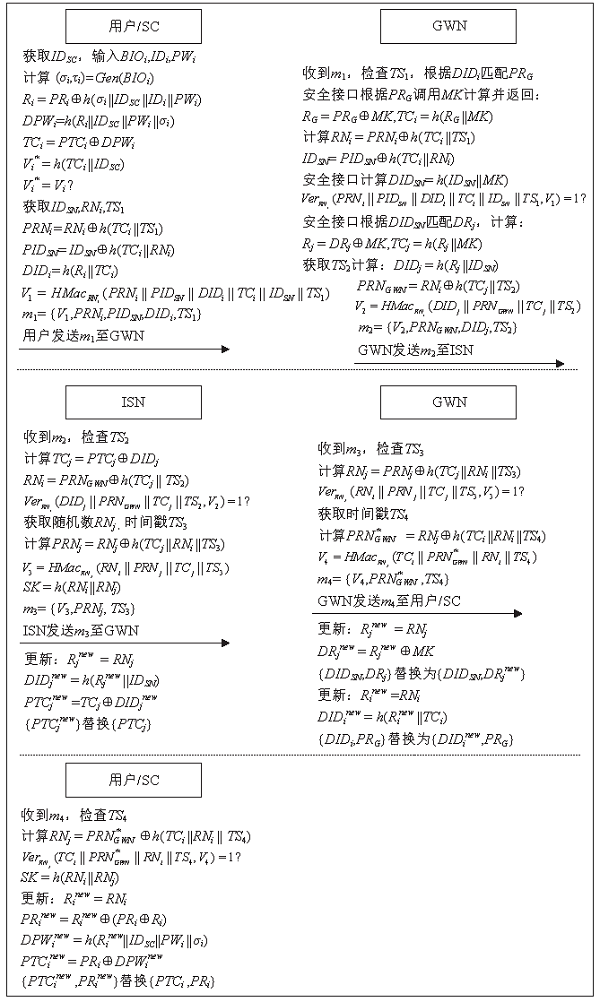
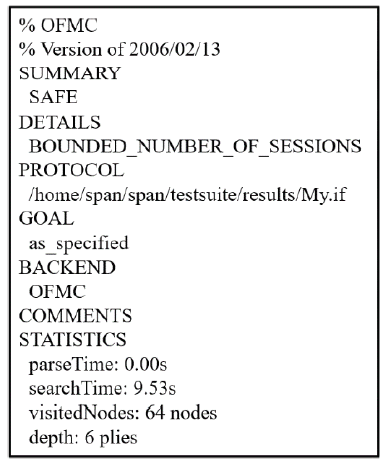
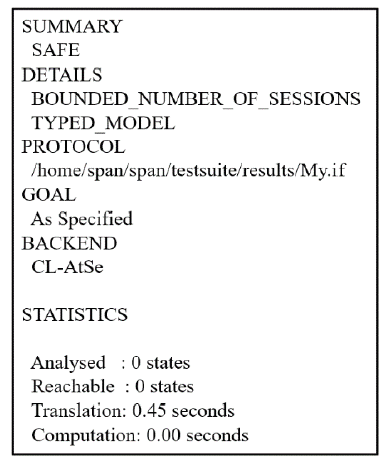
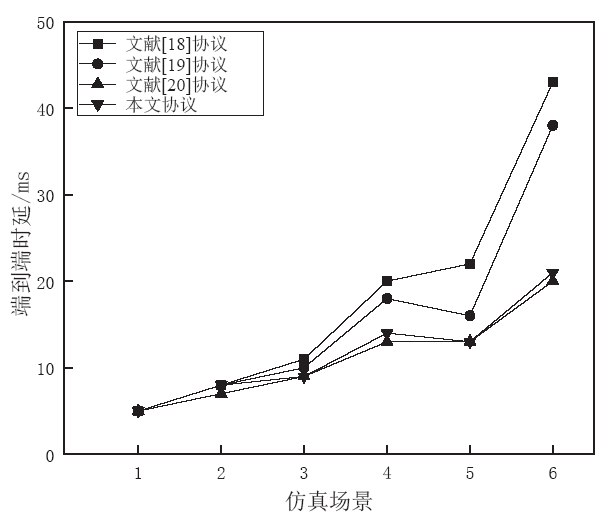
工业物联网广泛应用于制造、物流、石油和航空等领域,为现代工业的生产运营带来了革命性的机遇。但由于工业物联网通信信道的开放性和终端设备的资源有限性,数据和控制指令传输的安全性、实时性及高效性变得尤为重要。因此,专门设计一种适用于工业物联网的认证协议十分重要。目前,大部分认证协议不能很好地抵抗来自内部的特权用户攻击,且没有实现终端节点的不可追踪性,因此,文章设计了一种基于SGX技术的工业物联网认证协议。该协议采用SGX存储主密钥,同时借助SGX内存保密的特点实现机密计算。该协议可以有效抵抗特权用户攻击和终端节点的追踪攻击。最后,文章通过AVISPA仿真工具和非形式化安全分析证明了协议的安全性,并通过性能对比分析和NS3仿真证明了协议具有更好的实用性及先进性。
中图分类号:
引用本文
刘忻, 郭振斌, 宋宇宸. 一种基于SGX的工业物联网身份认证协议[J]. 信息网络安全, 2021, 21(6): 1-10.
LIU Xin, GUO Zhenbin, SONG Yuchen. An Authentication Scheme Based on SGX for Industrial Internet of Things[J]. Netinfo Security, 2021, 21(6): 1-10.
表1
MICAz平台操作能耗
| 操作 | 能耗 |
|---|---|
| 计算1 ms时间 | $3.0\text{V}\times 8.0\text{mA}\times 1\text{ms}=0.024\text{mJ}$ |
| 发送1 bit数据 | $3.0\text{V}\times 17.4\text{mA}\times \frac{1\text{bit}}{250\text{Kbps}}\approx 0.00021\text{mJ}$ |
| 接收1 bit数据 | $3.0\text{V}\times 19.7\text{mA}\times \frac{1\text{bit}}{250\text{Kbps}}\approx 0.00024\text{mJ}$ |
表4
计算开销对比
| 协议 | 用户开销 | GWN开销 | ISN开销 | 总开销/ms |
|---|---|---|---|---|
| 文献[ | $9{{T}_{H}}\text{+}{{T}_{R}}\text{+2}{{T}_{m}}$ | $10{{T}_{H}}\text{+2}{{T}_{m}}$ | $5{{T}_{H}}$ | 5080.69 |
| 文献[ | $13{{T}_{H}}\text{+}{{T}_{R}}\text{+4}{{T}_{m}}$ | $10{{T}_{H}}\text{+}{{T}_{S}}$ | $5{{T}_{H}}\text{+2}{{T}_{m}}\text{+}{{T}_{S}}$ | 5128.54 |
| 文献[ | $11{{T}_{H}}\text{+}{{T}_{R}}$ | $11{{T}_{H}}$ | $5{{T}_{H}}$ | 148.56 |
| 本文 | $11{{T}_{H}}\text{+}{{T}_{R}}$ | $14{{T}_{H}}$ | $6{{T}_{H}}$ | 180.56 |
| [1] | HUSSAIN S, ULLAH I, KHATTAK H, et al. A Lightweight and Provable Secure Identity-based Generalized Proxy Signcryption(IBGPS) Scheme for Industrial Internet of Things(IIoT)[EB/OL]., 2021-01-18. |
| [2] | ZHANG Meng. Risk Analysis and Countermeasure Research of Industrial Internet of Things Security[J]. China Compute Review, 2017(4):42-50. |
| 张猛. 工业物联网安全风险分析及对策研究[J].中国工业评论, 2017(4):42-50. | |
| [3] | TURKANOVIĆ M, BRUMEN B, HOELBL M. A Novel User Authentication And Key Agreement Scheme for Heterogeneous Ad Hoc Wireless Sensor Networks, Based on the Internet of Things notion[J]. Ad Hoc Neweorks, 2014,20(2):96-112. |
| [4] | TAI Weiliang, CHANG Yafen, LI Weihan. An IoT Notion-based Authentication and Key Agreement Scheme Ensuring User Anonymity for Heterogeneous[J]. Ad Hoc Wireless Sensor Networks, 2017,34(2):133-141. |
| [5] | ELDEFRAWY M H, FERRARI N, GIDLUND M. Dynamic User Authentication Protocol for Industrial IoT without Timestamping[EB/OL]. , 2019-07-11. |
| [6] |
LI Xiong, NIU Jianwei, BHUIYAN M, et al. A Robust ECC-Based Provable Secure Authentication Protocol with Privacy Preserving for Industrial Internet of Things[J]. IEEE Transactions on Industrial Informatics, 2018,14(8):3599-3609.
doi: 10.1109/TII.9424 URL |
| [7] | PALIWAL S. Hash-based Conditional Privacy Preserving Authentication and Key Exchange Protocol Suitable for Industrial Internet of Things[EB/OL]. , 2019-09-16. |
| [8] |
KARATI A, ISLAM S H, KARUPPIAH M. Provably Secure and Lightweight Certificateless Signature Scheme for IIoT Environments[J]. IEEE Transactions on Industrial Informatics, 2018,14(8):3701-3711.
doi: 10.1109/TII.9424 URL |
| [9] | ZHANG Bo, ZHU Tianqing, HU Cengyu, et al. Cryptanalysis of a Lightweight Certificateless Signature Scheme for IIOT Environments[EB/OL]. , 2018-11-27. |
| [10] | JANGIRALA S, KUMAR D A, MOHAMMAD W, et al. Anonymous Lightweight Chaotic Map-based Authenticated Key Agreement Protocol for Industrial Internet of Things[J]. IEEE Transactions on Dependable & Secure Computing, 2020,17(6):1133-1146. |
| [11] | AMIN R, BISWAS G P. A Secure Light Weight Scheme for User Authentication and Key Agreement in Multi-gateway Based Wireless Sensor Networks[EB/OL]. , 2021-01-10. |
| [12] |
HADLINGTON L, POPOVAC M, JANICKE H. Exploring the Role of Work Identity and Work Locus of Control in Information Security Awareness[J]. Computers & Security, 2019,81(1):41-48.
doi: 10.1016/j.cose.2018.10.006 URL |
| [13] | WANG Juan, FAN Chengyang, CHENG Yueqiang, et al. Analysis and Research on SGX Technology[J]. Journal of Software, 2018,29(9):2778-2798. |
| 王鹃, 樊成阳, 程越强, 等. SGX技术的分析和研究[J]. 软件学报, 2018,29(9):2778-2798. | |
| [14] |
YANG Zheng, HE Jun, TIAN Yangguang, et al. Faster Authenticated Key Agreement with Perfect Forward Secrecy for Industrial Internet-of-things[J]. IEEE Transactions on Industrial Informatics, 2020,16(10):6584-6596.
doi: 10.1109/TII.9424 URL |
| [15] | SHIM K A. A Practical Multi-user Broadcast Authentication Scheme in Wireless Sensor Networks[J]. IEEE Transactions on Information Forensics & Security, 2017,12(7):1545-1554. |
| [16] | CHEN Chienming, XIANG Bing, WU Tsuyang, et al. An Anonymous Mutual Authenticated Key Agreement Scheme for Wearable Sensors in Wireless Body Area Networks[EB/OL]. , 2018-07-02. |
| [17] | LIU Xin. Research on Authentication Scheme for Wireless Sensor Networks[D]. Lanzhou: Lanzhou University, 2019. |
| 刘忻. 基于无线传感器网络的身份认证协议的研究[D]. 兰州:兰州大学, 2019. | |
| [18] |
FAR H A N, BAYAT M, DAS A K, et al. LAPTAS: Lightweight Anonymous Privacy-preserving Three-factor Authentication Scheme for WSN-based IIoT[J]. Wireless Networks, 2021,27(4):1-24.
doi: 10.1007/s11276-020-02437-6 URL |
| [19] | MO Jiaqing, CHEN Hang. A Lightweight Secure User Authentication and Key Agreement Protocol for Wireless Sensor Networks[EB/OL]. , 2019-12-16. |
| [20] |
LUO Hanguang, WEN Guangjun, SU Jian. Lightweight Three Factor Scheme for Real-time Data Access in Wireless Sensor Networks[J]. Wireless Networks, 2020,26(2):955-970.
doi: 10.1007/s11276-018-1841-x URL |
| [1] | 王利, 李二霞, 纪宇晨, 李小勇. 基于PUF的抗物理克隆RFID安全认证协议[J]. 信息网络安全, 2020, 20(8): 89-97. |
| [2] | 孙子文, 张向阳. 大规模移动RFID系统Shamir’s密钥共享PUF安全认证协议[J]. 信息网络安全, 2020, 20(6): 26-35. |
| [3] | 韦永霜, 陈建华, 韦永美. 基于椭圆曲线密码的RFID/NFC安全认证协议[J]. 信息网络安全, 2019, 19(12): 64-71. |
| [4] | 郝文江, 宋斐, 万月亮. 可穿戴单警装备安全认证协议研究[J]. 信息网络安全, 2018, 18(9): 25-29. |
| [5] | 张小红, 郭焰辉. 基于椭圆曲线密码的RFID系统安全认证协议研究[J]. 信息网络安全, 2018, 18(10): 51-61. |
| [6] | 段然, 徐乃阳, 胡爱群. 基于形式化分析工具的认证协议安全性研究[J]. 信息网络安全, 2015, 15(7): 71-76. |
| [7] | 仇各各, 汪学明, 张言胜. 基于HECC的WSN身份认证协议研究[J]. 信息网络安全, 2015, 26(12): 54-58. |
| [8] | 夏戈明;史立哲;周文;沈恒丰. 轻量级RFID双向通信认证协议优化方案[J]. , 2014, 14(2): 0-0. |
| [9] | . 轻量级RFID双向通信认证协议优化方案[J]. , 2014, 14(2): 58-. |
| [10] | 蒋天发;王维虎;蒋巍. 基于TCP/IP应用层密码认证协议的研究[J]. , 2011, 11(5): 0-0. |
| [11] | 王琼;孙瑞冰;王良民;万可. 基于EPC物联网的公安数据通信安全认证协议研究[J]. , 2011, 11(12): 0-0. |
| [12] | 陈宇;王晋东. 无线传感网身份认证协议研究[J]. , 2011, 11(12): 0-0. |
| [13] | 李艳平. 抗中间人攻击的身份认证协议[J]. , 2009, 9(4): 0-0. |
| [14] | 郎为民;蔡理金;何伟. 3GPP LTE系统中用户安全研究[J]. , 2009, 9(10): 0-0. |
| [15] | 郎为民;焦巧;祈向宇;张颀. WiMAX认证方案研究[J]. , 2008, 8(9): 0-0. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||