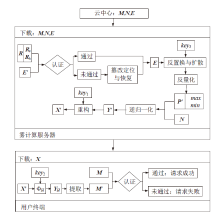
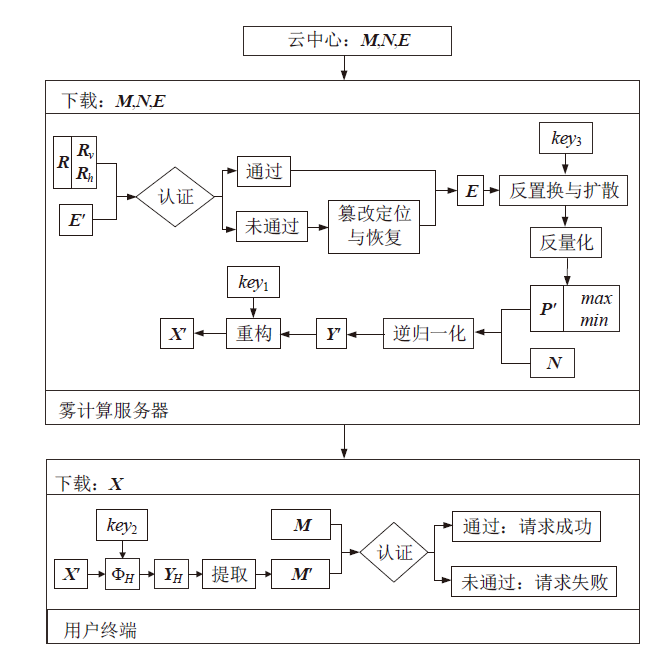
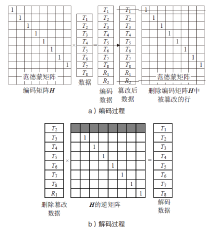
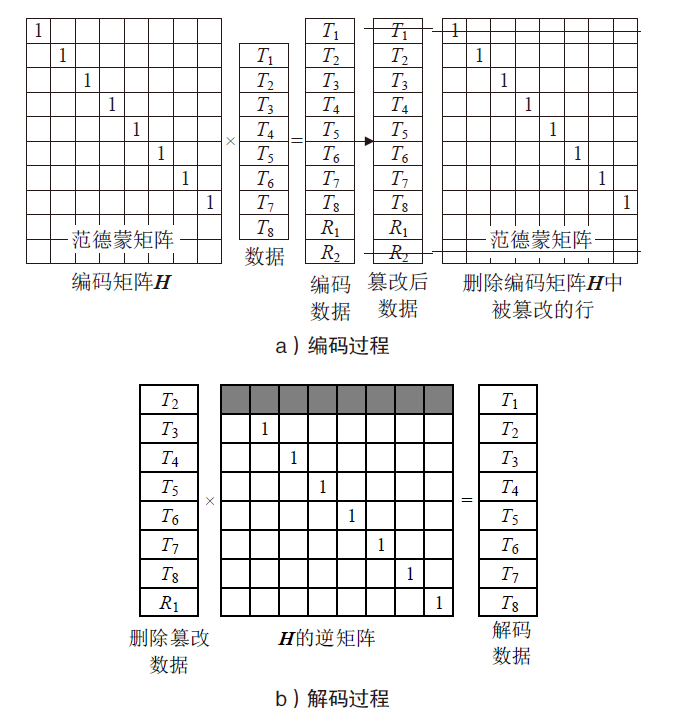
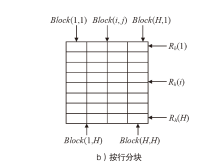
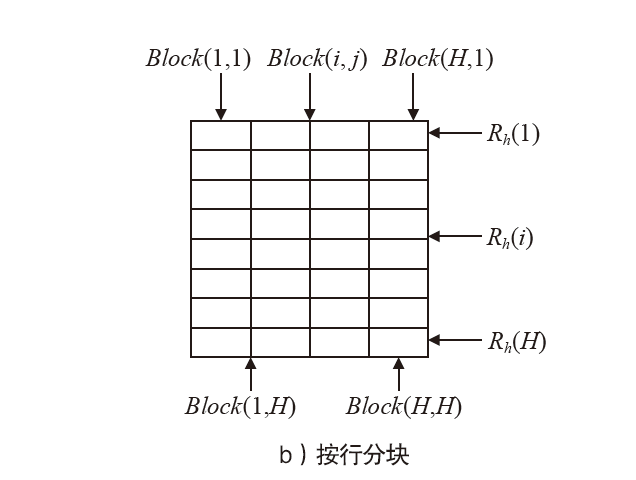
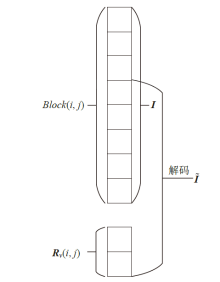
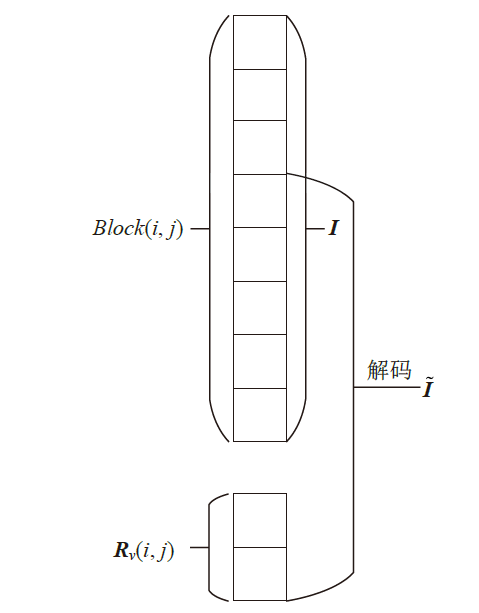
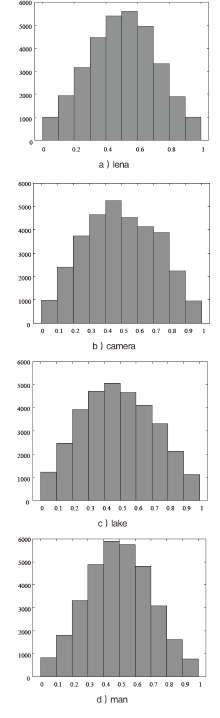
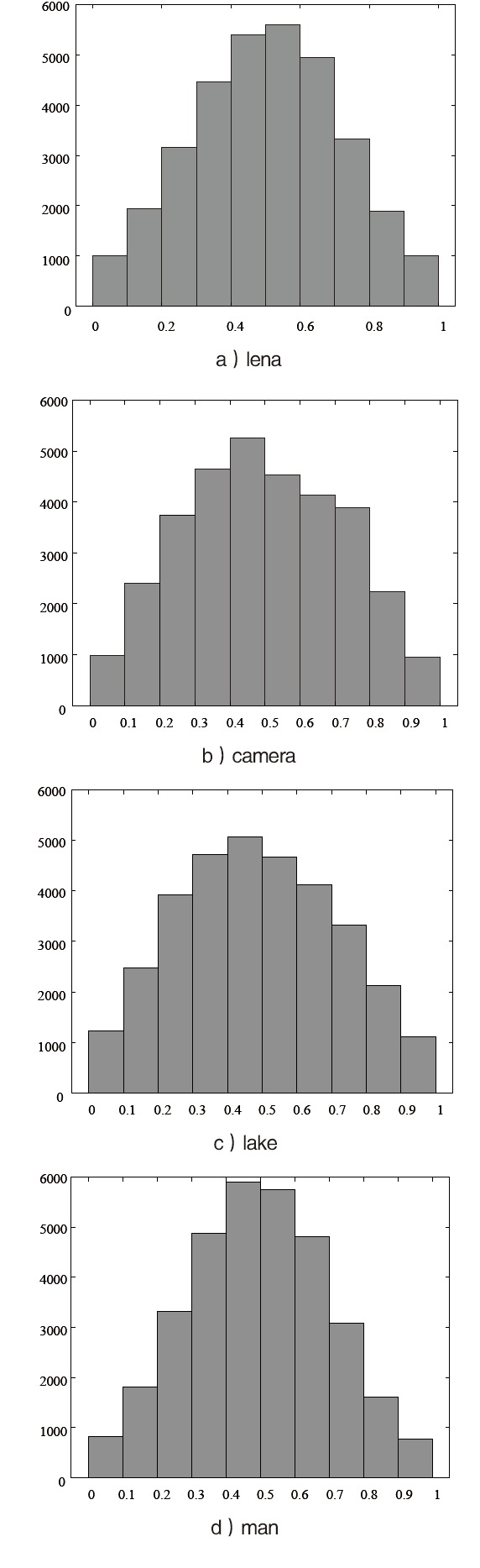
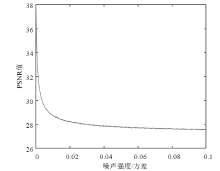
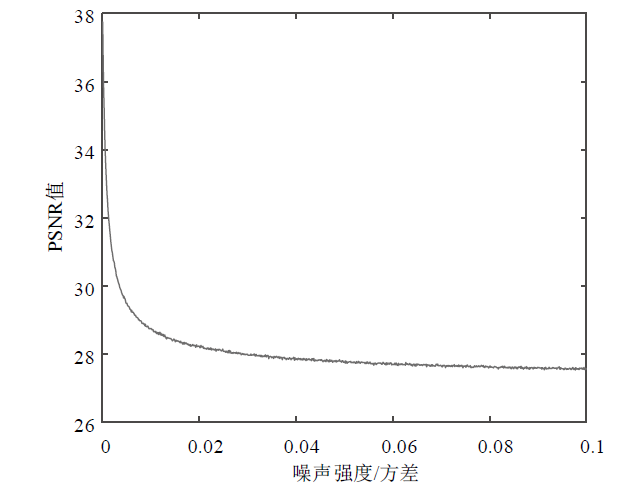
信息网络安全 ›› 2021, Vol. 21 ›› Issue (4): 10-20.doi: 10.3969/j.issn.1671-1122.2021.04.002
面向雾计算的压缩感知图像秘密传输和篡改恢复方案
- 重庆大学计算机学院,重庆 400044
-
收稿日期:2021-01-22出版日期:2021-04-10发布日期:2021-05-14 -
通讯作者:肖迪 E-mail:dixiao@cqu.edu.cn -
作者简介:郑洪英(1975—),女,重庆,副教授,博士,主要研究方向为多媒体安全|李琳(1996—),女,重庆,硕士研究生,主要研究方向为多媒体安全|肖迪(1975—),男,重庆,教授,博士,主要研究方向为多媒体安全、隐私保护 -
基金资助:国家自然科学基金(62072063)
Secret Image Transmission and Tamper Recovery Based on Compressed Sensing for Fog Computing
ZHENG Hongying, LI Lin, XIAO Di( )
)
- College of Computer Science, Chongqing University, Chongqing 400044, China
-
Received:2021-01-22Online:2021-04-10Published:2021-05-14 -
Contact:XIAO Di E-mail:dixiao@cqu.edu.cn
摘要:
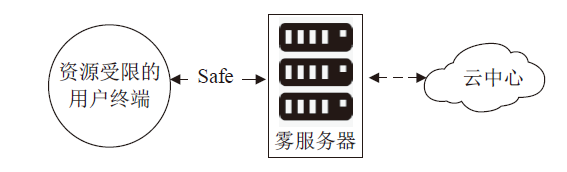
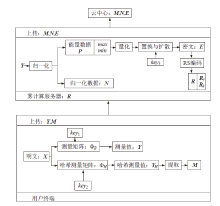
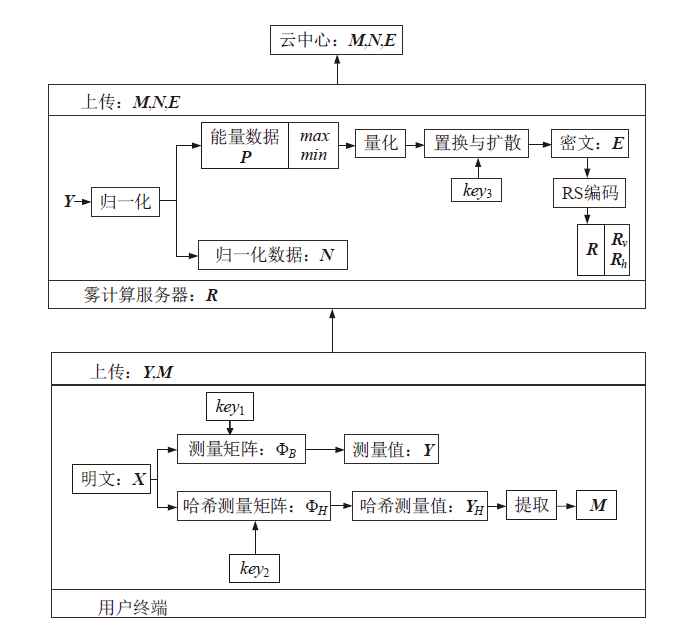
在雾计算三层数据传输框架下,用户的图像数据隐私泄露依然是最严重的问题之一,特别是大多数加密方法都不适用于物理终端资源受限的情况。因此,针对这类场景,需要设计合适的数据隐私保护方法。压缩感知具有轻量级和保密性,可以解决该问题。文章提出一种基于压缩感知的图像数据三层传输方案,不仅可以实现数据的安全传输,还可以结合里德-所罗门码(RS)应对篡改攻击,实现篡改定位和恢复。保密性方面,终端利用块压缩感知实现轻量级加密。由于测量值可能泄露明文能量,在雾服务器上将测量值进行局部归一化,对产生的能量值进行高强度加密,使传输过程达到完美保密。完整性方面,利用压缩感知的鲁棒性和RS编码的冗余性实现数据的篡改定位和双重篡改恢复。仿真结果和分析验证了该方案的性能。
中图分类号:
引用本文
郑洪英, 李琳, 肖迪. 面向雾计算的压缩感知图像秘密传输和篡改恢复方案[J]. 信息网络安全, 2021, 21(4): 10-20.
ZHENG Hongying, LI Lin, XIAO Di. Secret Image Transmission and Tamper Recovery Based on Compressed Sensing for Fog Computing[J]. Netinfo Security, 2021, 21(4): 10-20.
| [1] | MELL P M, GRANCE T. The NIST Definition of Cloud Computing[EB/OL]. https://nvlpubs.nist.gov/nistpubs/Legacy/SP/nistspecialpublication800-145.pdf, 2020-07-12. |
| [2] | TAYADE D. Mobile Cloud Computing: Issues, Security, Advantages, Trends[J]. International Journal of Computer Science and Information Technologies, 2014,5(5):6635-6639. |
| [3] | BONOMI F, MILITO R, ZHU Jiang, et al. Fog Computing and Its Role in the Internet of Things[C]// ACM. The First Edition of the MCC Workshop on Mobile Cloud Computing, August 17, 2012, Helsinki, Finland. New York: ACM, 2012: 13-16. |
| [4] |
WANG Tian, ZHOU Jiyuan, CHEN Xinlei, et al. A Three-layer Privacy Preserving Cloud Storage Scheme Based on Computational Intelligence in Fog Computing[J]. IEEE Transactions on Emerging Topics in Computational Intelligence, 2018,2(1):3-12.
doi: 10.1109/TETCI URL |
| [5] | WANG Tian, MEI Yaxin, JIA Weijia, et al. Edge-based Differential Privacy Computing for Sensor-cloud Systems[EB/OL]. https://www.sciencedirect.com/science/article/abs/pii/S074373151930293X, 2020-07-14. |
| [6] |
DONOHO D L. Compressed Sensing[J]. IEEE Transactions on Information Theory, 2006,52(4):1289-1306.
doi: 10.1109/TIT.2006.871582 URL |
| [7] | GAN Lu. Block Compressed Sensing of Natural Images[C]// IEEE. 15th International Conference on Digital Signal Processing, August 1-4, 2007, Cardiff, UK. New Jersey: IEEE, 2007: 403-406. |
| [8] |
BARANIUK R, DAVENPORT M, DEVORE R, et al. A Simple Proof of the Restricted Isometry Property for Random Matrices[J]. Constructive Approximation, 2008,28(3):253-263.
doi: 10.1007/s00365-007-9003-x URL |
| [9] |
CANDES E J, TAO T. Near-optimal Signal Recovery from Random Projections: Universal Encoding Strategies?[J]. IEEE Transactions on Information Theory, 2006,52(12):5406-5425.
doi: 10.1109/TIT.2006.885507 URL |
| [10] |
BIANCHI T, BIOGLIO V, MAGLI E, et al. Analysis of One-time Random Projections for Privacy Preserving Compressed Sensing[J]. IEEE Transactions on Information Forensics and Security, 2016,11(2):313-327.
doi: 10.1109/TIFS.2015.2493982 URL |
| [11] | CHEN Junxin, ZHANG Yu, LIN Qi, et al. Exploiting Chaos-based Compressed Sensing and Cryptographic Algorithm for Image Encryption and Compression[J]. Optics & Laser Technology, 2018,99(1):238-248. |
| [12] | ZHOU Kanglei, FAN Jingjing, FAN Haiju, et al. Secure Image Encryption Scheme Using Double Random-phase Encoding and Compressed Sensing[EB/OL]. https://www.sciencedirect.com/science/article/abs/pii/S0030399219309648, 2020-08-12. |
| [13] | CHAI Xiuli, FU Xianglong, GAN Zhihua, et al. An Efficient Chaos-based Image Compression and Encryption Scheme Using Block Compressive Sensing and Elementary Cellular Automata[EB/OL]. https://link.springer.com/article/10.1007/s00521-018-3913-3#article-info, 2018-12-29. |
| [14] | LIU Zhanqiang, WANG Licheng, WANG Xianmin, et al. Secure Remote Sensing Image Registration Based on Compressed Sensing in Cloud Setting[EB/OL]. https://ieeexplore.ieee.org/document/8663267, 2019-03-08. |
| [15] | XIE Dong, CHEN Fulong, LUO Yonglong, et al. One-to-many Image Encryption with Privacy-preserving Homomorphic Outsourced Decryption Based on Compressed Sensing[EB/OL]. https://www.sciencedirect.com/science/article/abs/pii/S1051200419301332, 2020-08-20. |
| [16] | ZHANG Yushu, XIANG Yong, ZHANG L Y, et al. Efficiently and Securely Outsourcing Compressed Sensing Reconstruction to a Cloud[EB/OL]. https://www.sciencedirect.com/science/article/abs/pii/S0020025519304293, 2020-08-20. |
| [17] |
ZHANG Yushu, WANG Ping, FANG Liming, et al. Secure Transmission of Compressed Sampling Data Using Edge Clouds[J]. IEEE Transactions on Industrial Informatics, 2020,16(10):6641-6651.
doi: 10.1109/TII.9424 URL |
| [18] | KANG Liwei, LU Chunshien, HSU C Y, et al. Compressive Sensing-based Image Hashing[C]// IEEE. 16th IEEE International Conference on Image Processing, November 7-10, 2009, Cairo, Egypt. New Jersey: IEEE, 2009: 1285-1288. |
| [19] | WU T, RULAND C. An Improved Authenticated Compressive Sensing Imaging[C]// IEEE. 12th International Conference on Semantic Computing, January 31-February 2, 2018, Laguna Hills, CA, USA. New Jersey: IEEE, 2018: 164-171. |
| [20] | BIANCHI T, BIOGLIO V, MAGLI E. On the Security of Random Linear Measurements[C]// IEEE. IEEE International Conference on Acoustics, Speech and Signal Processing, May 4-9, 2014, Florence, Italy. New Jersey: IEEE, 2014: 3992-3996. |
| [21] | PLANK J S. T1: Erasure Codes for Storage Applications[EB/OL]. http://ecee.colorado.edu/ecen5653/ecen5653/papers/Erasure-Code-Overview-FAST-2005.pdf, 2020-09-10. |
| [22] | PAK C, HUANG L. A New Color Image Encryption Using Combination of the 1D Chaotic Map[EB/OL]. https://dl.acm.org/doi/abs/10.5555/3085606.3085775, 2020-09-14. |
| [1] | 杜义峰, 郭渊博. 一种基于信任值的雾计算动态访问控制方法[J]. 信息网络安全, 2020, 20(4): 65-72. |
| [2] | 汪金苗, 王国威, 王梅, 朱瑞瑾. 面向雾计算的隐私保护与访问控制方法[J]. 信息网络安全, 2019, 19(9): 41-45. |
| [3] | 徐杰, 贺敏, 包秀国. 基于压缩感知的视频台标识别研究[J]. 信息网络安全, 2015, 15(5): 77-81. |
| [4] | . 一种分块压缩感知观测值的图像篡改认证算法[J]. , 2014, 14(4): 35-. |
| [5] | . 基于混沌和比特级置乱的并行图像加密算法[J]. , 2014, 14(4): 40-. |
| [6] | . 基于遍历矩阵和混合密钥的验证和图像空域加密技术[J]. , 2014, 14(11): 18-. |
| [7] | 周晓谊, 段玉聪, 冯文龙, 李益红. 基于遍历矩阵和混合密钥的验证和图像空域加密技术[J]. 信息网络安全, 2014, 15(11): 18-25. |
| [8] | 李进;徐红. 基于MD5算法和Logistic映射的图像加密方法研究[J]. , 2011, 11(8): 0-0. |
| [9] | 邵利平;蒙清照;李春枚;王旭. 图像置乱方法综述[J]. , 2009, 9(4): 0-0. |
| [10] | 徐献灵;崔楠. 数字图像置乱加密技术综述[J]. , 2009, 9(3): 0-0. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||