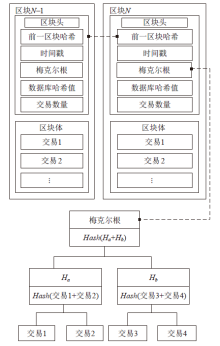
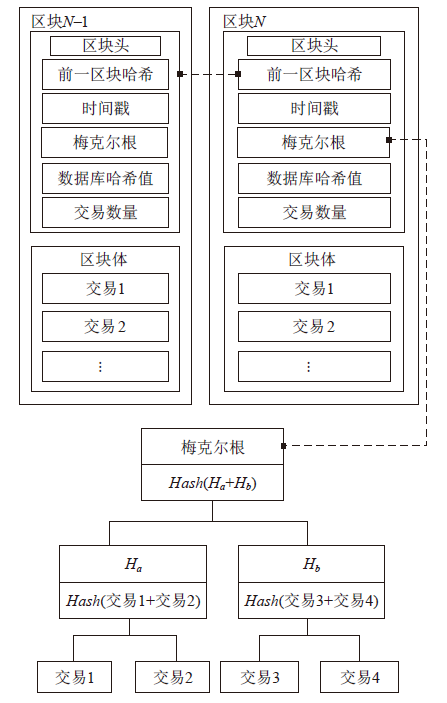
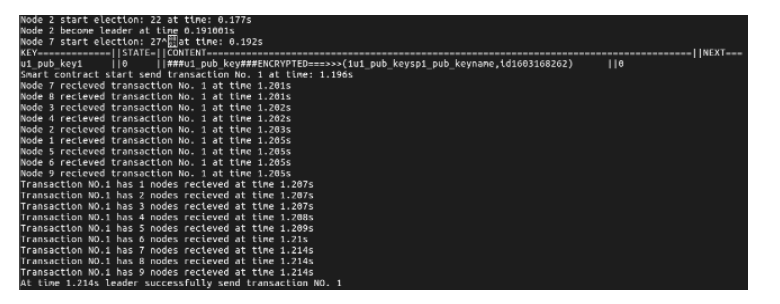
信息网络安全 ›› 2020, Vol. 20 ›› Issue (11): 22-31.doi: 10.3969/j.issn.1671-1122.2020.11.004
基于智能合约的个人隐私数据保护方法研究
- 1.北京工业大学信息学部,北京 100124
2.可信计算北京市重点实验室,北京 100124
3.信息安全等级保护关键技术国家工程实验室,北京 100124
4.智能交通数据安全与隐私保护技术北京市重点实验室,北京 100044
5.北京交通大学计算机与信息技术学院,北京 100044
-
收稿日期:2020-05-24出版日期:2020-11-10发布日期:2020-12-31 -
通讯作者:姜楠 E-mail:wangjian@bjtu.edu.cn -
作者简介:姜楠(1977—),女,山东,副教授,博士,主要研究方向为信息安全|王玮琦(1994—),女,河南,硕士研究生,主要研究方向为区块链|王健(1975—),男,山东,副教授,博士,主要研究方向为网络安全、密码应用、智能计算 -
基金资助:国家自然科学基金(61502016);教育部-中国移动科研基金(MCM20170402);教育部-中国移动科研基金(MCM20180503)
Research on Personal Information Protection Method Based on Smart Contract
JIANG Nan1,2,3( ), WANG Weiqi1, WANG Jian4,5
), WANG Weiqi1, WANG Jian4,5
- 1. Faculty of Information Technology, Beijing University of Technology, Beijing 100124, China
2. Beijing Key Laboratory of Trusted Computing, Beijing 100124, China
3. National Engineering Laboratory for Critical Technologies of Information Security Classified Protection, Beijing 100124, China
4. Beijing Key Laboratory of Security and Privacy in Intelligent Transportation, Beijing 100044, China
5. School of Computer and Information Technology, Beijing Jiaotong University, Beijing 100044, China
-
Received:2020-05-24Online:2020-11-10Published:2020-12-31 -
Contact:JIANG Nan E-mail:wangjian@bjtu.edu.cn
摘要:
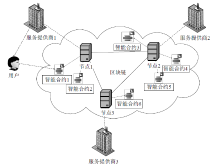
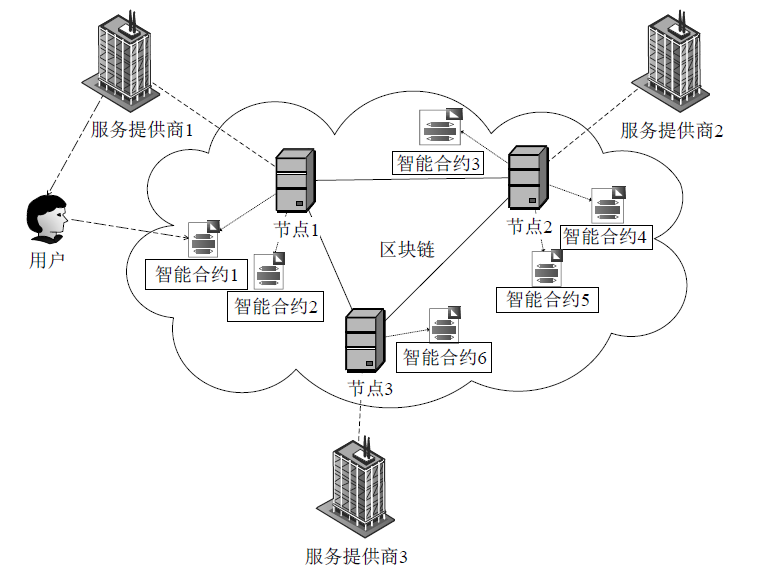
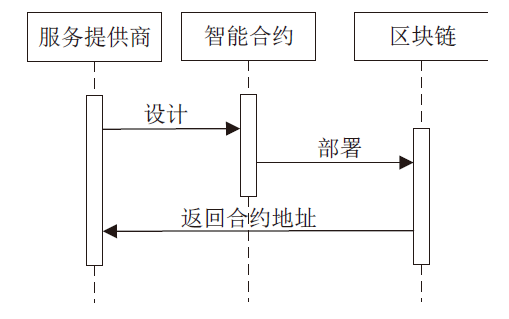
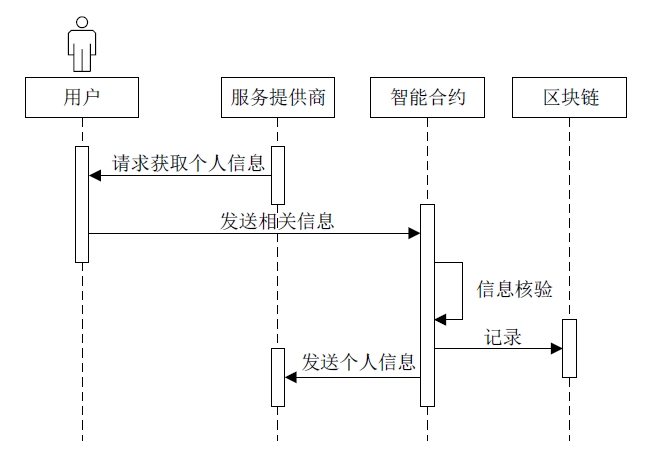
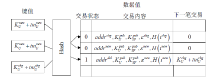
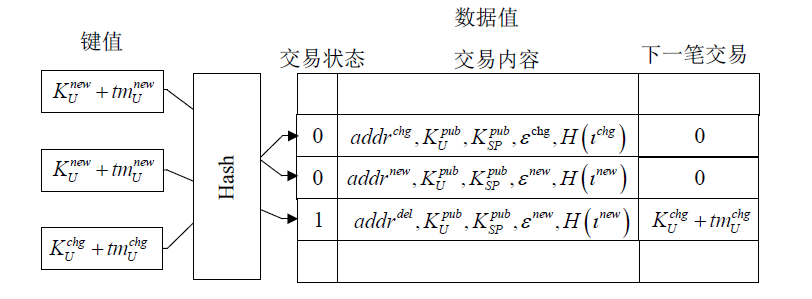
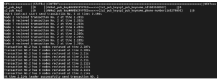
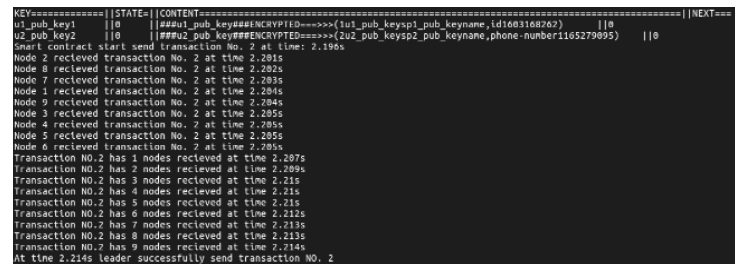
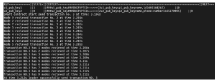
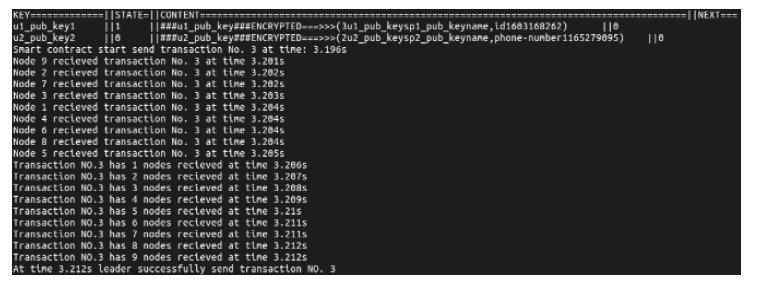
文章提出一种基于智能合约的个人隐私数据保护方法,利用区块链技术,在无须可信中心的前提下,将用户与服务提供商之间的个人交易记录存储在区块链上,作为交易存在性的可靠法律凭证,防止利用用户取证困难而实施个人信息盗窃的犯罪行为。个人信息的实际内容不会存储在区块链上,只有交易记录在区块链上加密存储,只有交易相关方可以进行解密查看,保障了用户隐私。同时,针对个人信息的交易创建、交易失效、交易修改设计了3种智能合约,对交易进行失效和修改并不会使之前的交易信息丢失,个人交易记录一经上链即可永久作为交易存在性的可靠证明。最后,通过NS-3网络模拟器进行仿真实验,结果表明该方法具有可行性。
中图分类号:
引用本文
姜楠, 王玮琦, 王健. 基于智能合约的个人隐私数据保护方法研究[J]. 信息网络安全, 2020, 20(11): 22-31.
JIANG Nan, WANG Weiqi, WANG Jian. Research on Personal Information Protection Method Based on Smart Contract[J]. Netinfo Security, 2020, 20(11): 22-31.
| [1] | SWINHOE D. The 15 Biggest Data Breaches of the 21st Century[EB/OL]. https://www.csoonline.com/article/2130877/the-biggest-data-breaches-of-the-21st-century.html, 2020-4-17. |
| [2] | WINDER D. Unsecured Facebook Databases Leak Data of 419 Million Users[EB/OL]. http://www.forbes.com/sites/daveywinder/2019/09/05/facebook-security-snafu-exposes-419-million-user-phone, 2019-9-5. |
| [3] | PATTERSON D, KATES G. We Found Our Personal Data on the Dark Web. Is Yours There, Too?[EB/OL]. https://www.cbsnews.com/news/we-found-our-personal-data-on-thedark-web-is-yours-there-too, 2019-3-25. |
| [4] | ARMSTRONG D. My Three Years in Identity Theft Hell[EB/OL]. https://www.bloomberg.com/news/articles/2017-09-13/my-three-years-in-identity-theft-hell, 2017-9-13. |
| [5] | CNNIC. The 44th China Statistical Report on Internet Development[R]. Beijing: China Internet Information Center, 1124938750, 2019-8-30. |
| 中国互联网信息中心. 第44次中国互联网络发展状况统计报告[R]. 北京:中国互联网络信息中心,1124938750, 2019-8-30. | |
| [6] | WANG Xueqi. Personal Privacy Information Leaked by Mobile Phone Apps, Just the Tip of the Iceberg, Exposed on March 15[EB/OL]. http://finance.sina.com.cn/consume/puguangtai/2019-03-17/doc-ihrfqzkc4361467.shtml, 2019-3-16. |
| 王雪琦. 3·15晚会曝光手机APP泄露个人隐私信息,这只是冰山一角[EB/OL]. http://finance.sina.com.cn/consume/puguangtai/2019-03-17/doc-ihrfqzkc4361467.shtml, 2019-3-16. | |
| [7] | NAKAMOTO S. Bitcoin: A Peer-to-peer Electronic Cash System[EB/OL]. https://bitco.in/pdf/bitcoin.pdf, 2008-11-1. |
| [8] | BAE S H, KIM J. Personal Information Protection Model Based on Mobile Agent[C]//IEEE. 7th International Conference on Information Technology: New Generations, April 12-14, 2010, Las Vegas, Nevada, USA. New York: IEEE, 2010: 719-724. |
| [9] | DE MONTJOYE Y A, SHMUELI E, WANG S S, et al. openPDS: Protecting the Privacy of Metadata through Safeanswers[EB/OL]. https://journals.plos.org/plosone/article/file?id=10.1371/journal.pone. 0098790& type=printable, 2020-2-11. |
| [10] | REAGLE J, CRANOR L F. The Platform for Privacy Preferences[J]. Communications of the ACM, 1999,42(2):48-55. |
| [11] | ASHLEY P, HADA S, KARJOTH G, et al. Enterprise Privacy Authorization Language(EPAL)[J]. IBM Research, 2003,1(1):30-31. |
| [12] | ANDERSON A, NADALIN A, PARDUCCI B, et al. Extensible Access Control Markup Language(xacml) Version 1.0[EB/OL]. https://www.oasis-open.org/committees/download.php/2406/oasis-xacml-1.0.pdf, 2003-2-18. |
| [13] | KO H G, KIM S H, JIN S H. Usability Enhanced Privacy Protection System Based on Users’ Responses[C]//IEEE. 2007 IEEE International Symposium on Consumer Electronics, June 20-23, 2007, Irving, Texas, USA. New York: IEEE, 2007: 1-6. |
| [14] | BEKARA K, LAURENT M. Enabling User Privacy in Identity Management Systems[C]//IEEE. 2010 IEEE International Conference on Information Theory and Information Security, December 17-19, 2010, Beijing, China. New York: IEEE, 2010: 514-520. |
| [15] | ARUNKUMAR S, RAGHAVENDRA A, WEERASINGHE D, et al. Policy Extension for Data Access Control[C]//IEEE. 6th IEEE Workshop on Secure Network Protocols, October. 5, 2010, Kyoto, Japan. New York: IEEE, 2010: 55-60. |
| [16] | ZYSKIND G, NATHAN O. Decentralizing Privacy: Using Blockchain to Protect Personal Data[C]//IEEE. 2015 IEEE Security and Privacy Workshops, May 21-22, 2015, San Jose, CA, USA. New York: IEEE, 2015: 180-184. |
| [17] | RAHMADIKA S, RHEE K H. Blockchain Technology for Providing an Architecture Model of Decentralized Personal Health Information[EB/OL]. https://www.onacademic.com/detail/journal_1000040485092010_cd21.html, 2020-2-11. |
| [18] | JI Y, BEA S, SHIN Y A. Personal Information Management Using Blockchain[C]//IEEE. 2019 International Conference on Information Networking(ICOIN), January 9-11, 2019, Kuala Lumpur, Malaysia, Malaysia. New York: IEEE, 2019: 489-493. |
| [19] | SZABO N. Smart Contracts: Building Blocks for Digital Markets[EB/OL]. https://kameir.com/smart-contracts. 2020-2-14. |
| [20] | RICHARD GENDAL BROWN. A Simple Model for Smart Contracts[EB/OL]. https://gendal.me/2015/02/10/a-simple-model-for-smart-contracts/, 2015-2-10. |
| [21] | MERKLE R C. Protocols for Public Key Cryptosystems[C]//IEEE. 1980 IEEE Symposium on Security and Privacy, April 14-16, 1980, Oakland, CA, USA. New York: IEEE, 1980: 122. |
| [22] | CASTRO M, LISKOV B. Practical Byzantine Fault Tolerance and Proactive Recovery[J]. ACM Transactions on Computer Systems(TOCS), 2002,20(4):398-461. |
| [23] | LAMPORT L. The Part-time Parliament[J]. ACM Transactions on Computer Systems, 1998,16(2):133-169. |
| [24] | LAMPORT L. Paxos Made Simple[J]. ACM Sigact News, 2001,32(4):18-25. |
| [25] | ONGARO D, OUSTERHOUT J. In Search of an Understandable Consensus Algorithm[C]// USENIX. 2014 USENIX Annual Technical Conference, June 19-20, 2014, Philadelphia, PA. California: USENIX, 2014: 305-319. |
| [1] | 韩磊, 陈武平, 曾志强, 曾颖明. 区块链层级网络结构与应用研究[J]. 信息网络安全, 2020, 20(9): 112-116. |
| [2] | 汪金苗, 谢永恒, 王国威, 李易庭. 基于属性基加密的区块链隐私保护与访问控制方法[J]. 信息网络安全, 2020, 20(9): 47-51. |
| [3] | 石润华, 石泽. 基于区块链技术的物联网密钥管理方案[J]. 信息网络安全, 2020, 20(8): 1-8. |
| [4] | 李莉, 曾庆贤, 文义红, 王士成. 基于区块链与代理重加密的数据共享方案[J]. 信息网络安全, 2020, 20(8): 16-24. |
| [5] | 边玲玉, 张琳琳, 赵楷, 石飞. 基于LightGBM的以太坊恶意账户检测方法[J]. 信息网络安全, 2020, 20(4): 73-80. |
| [6] | 毛志来, 刘亚楠, 孙惠平, 陈钟. 区块链性能扩展与安全研究[J]. 信息网络安全, 2020, 20(3): 56-64. |
| [7] | 郎为民, 张汉, 赵毅丰, 姚晋芳. 一种基于区块链的物联网行为监控和活动管理方案[J]. 信息网络安全, 2020, 20(2): 22-29. |
| [8] | 姚萌萌, 唐黎, 凌永兴, 肖卫东. 基于串空间的安全协议形式化分析研究[J]. 信息网络安全, 2020, 20(2): 30-36. |
| [9] | 刘开放, 付绍静, 苏金树, 张富成. 面向物联网多域协同的IOTA区块链优化方案[J]. 信息网络安全, 2020, 20(10): 41-48. |
| [10] | 彭如月, 马兆丰, 罗守山. 基于区块链的数字内容服务与安全监管技术研究与实现[J]. 信息网络安全, 2020, 20(10): 49-56. |
| [11] | 郭瑞, 陈宇霜, 郑东. 无线医疗传感网络中基于区块链的高效无证书聚合签名方案[J]. 信息网络安全, 2020, 20(10): 6-18. |
| [12] | 周艺华, 吕竹青, 杨宇光, 侍伟敏. 基于区块链技术的数据存证管理系统[J]. 信息网络安全, 2019, 19(8): 8-14. |
| [13] | 路爱同, 赵阔, 杨晶莹, 王峰. 区块链跨链技术研究[J]. 信息网络安全, 2019, 19(8): 83-90. |
| [14] | 郑敏, 王虹, 刘洪, 谭冲. 区块链共识算法研究综述[J]. 信息网络安全, 2019, 19(7): 8-24. |
| [15] | 周元健, 秦冬梅, 刘忆宁, 吕松展. 基于区块链的可信仓单系统设计[J]. 信息网络安全, 2019, 19(6): 84-90. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||