信息网络安全 ›› 2017, Vol. 17 ›› Issue (11): 7-12.doi: 10.3969/j.issn.1671-1122.2017.11.002
连续变量量子密钥分发实际安全性研究进展
- 上海交通大学区域光纤通信网与新型光通信系统国家重点实验室,上海 200240
-
收稿日期:2017-07-01出版日期:2017-11-20发布日期:2020-05-12 -
作者简介:作者简介:黄鹏 (1985—),男,江西,助理研究员,博士,主要研究方向为量子密码通信、量子信息论;曾贵华(1966—),男,湖南,教授,博士,主要研究方向为量子密码通信、量子精密测量、量子成像等。
-
基金资助:国家自然科学基金[61332019, 61671287,61631014];国家重点研发计划[2016YFA0302600]
The Development of Study on Practical Security of Continuous-variable Quantum Key Distribution
- State Key Laboratory of Advanced Optical Communication System and Networks, Shanghai Jiaotong University, Shanghai 200240, China
-
Received:2017-07-01Online:2017-11-20Published:2020-05-12
摘要:
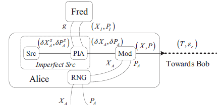
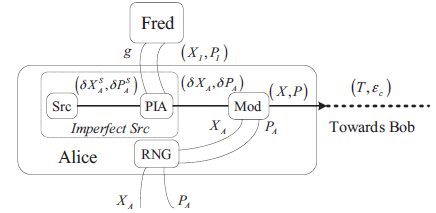
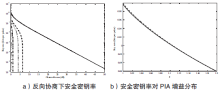
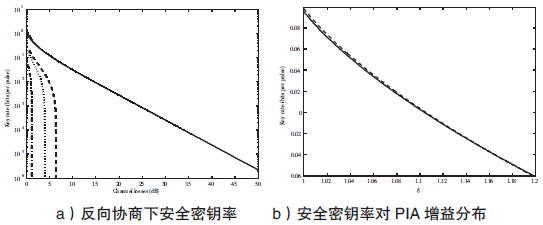
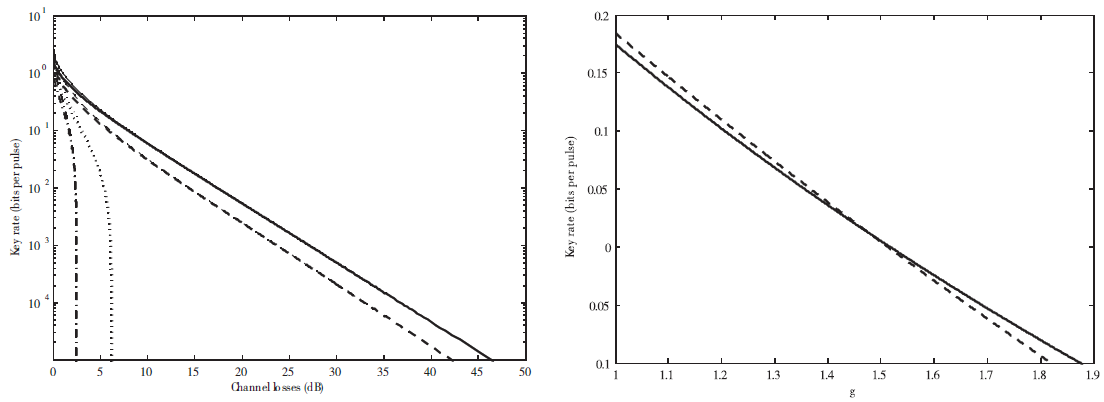
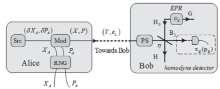
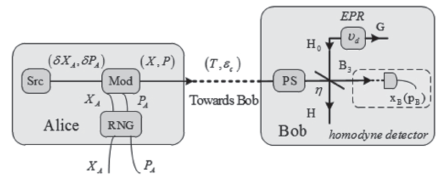
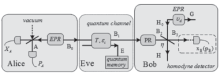
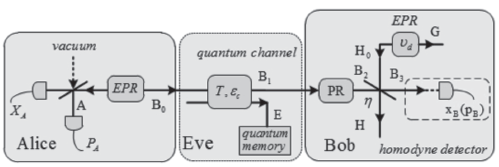
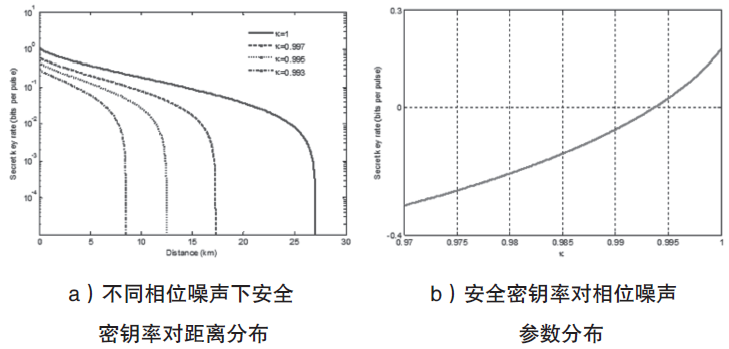
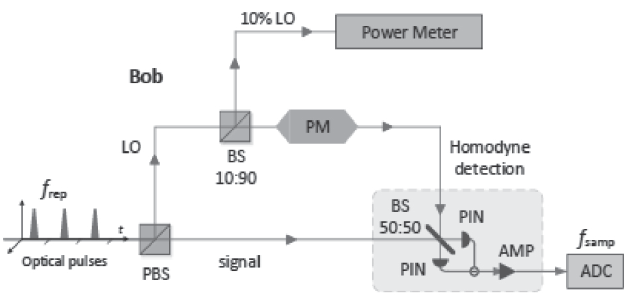
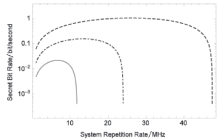
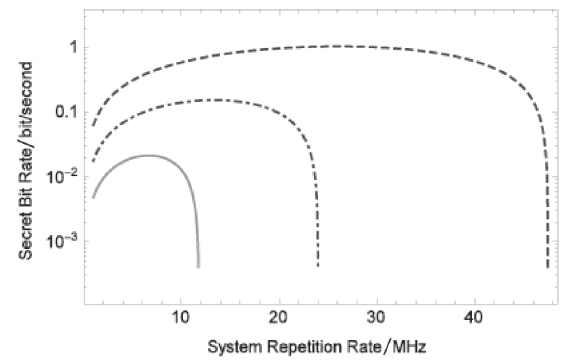
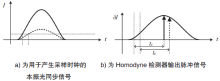
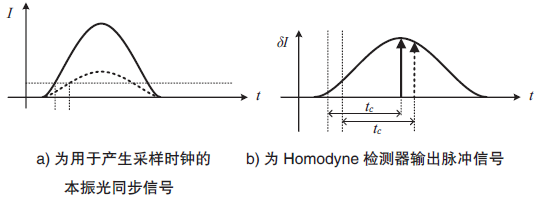
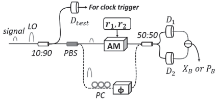
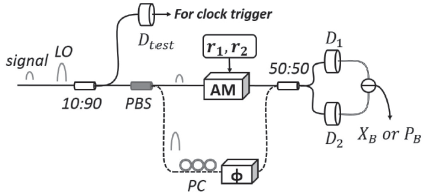
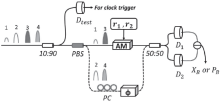
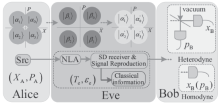
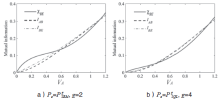
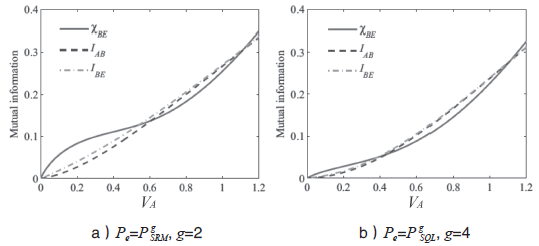
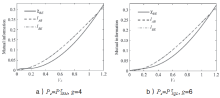
连续变量量子密钥分发(CVQKD)技术因其具有潜在高码率及与经典光通信良好融合性的特性,受到社会各界的广泛关注,近十几年来得到了迅速的发展。目前高斯调制CVQKD协议在理论上已经被证明具有无条件安全性。然而对于一个实际CVQKD系统,其各个硬件及软件子系统、模块不可能具有理论上的完善性,这些非理想特性一方面会导致系统实际运行安全密钥率的降低,另外还可能引入具体的黑客攻击,导致系统不再安全运行。文章分别从系统非理想特性对实际运行安全性的影响以及引入的具体攻击策略两个方面介绍了目前国内外针对CVQKD系统实际安全性的研究进展情况,并对该研究方向提出了展望。
中图分类号:
引用本文
黄鹏, 曾贵华. 连续变量量子密钥分发实际安全性研究进展[J]. 信息网络安全, 2017, 17(11): 7-12.
Peng HUANG, Guihua ZENG. The Development of Study on Practical Security of Continuous-variable Quantum Key Distribution[J]. Netinfo Security, 2017, 17(11): 7-12.
| [1] | RALPH T. C. Continuous Variable Quantum Cryptography [J]. Physical Review A, 1999(61):010303(R). |
| [2] | RALPH T C.Security of Continuous-variable Quantum Cryptography[J]. Physical Review A, 2000(62): 062306. |
| [3] | WEEDBROOK C, PIRANDOLA S, CERF N J, et al.Gaussian Quantum Information[J]. Review of Modern Physics, 2012, 84(6): 621. |
| [4] | LEVERRIER A,GRANGIER P.Unconditional Security Proof of Long-distance Continuous-variable Quantum Key Distribution with Discrete Modulation[J]. Physical Review Letters, 2009, 102(18):180504. |
| [5] | LEVERRIER A,GRANGIER P. Erratum: Unconditional Security Proof of Long Distance Continuous-variable Quantum Key Distribution with Discrete Modulation [phys. rev. lett. 102, 180504 (2009)][J]. Phys. Rev. Lett., 2011(106): 259902. |
| [6] | LEVERRIER A, GRANGIER P.Continuous-variable Quantum-key-distribution Protocols with a non-gaussian Modulation[J]. Physical Review A, 2011, 83(4): 042312. |
| [7] | GARCIA-PATRON R, CERF J N.Unconditional Optimality of Guassian Attacks against Continuous-variable Quantum Key Distribution[J].Physical Review Letters, 2006(97):190503. |
| [8] | NAVASCUÉS M, F.GROSSHANS, ACIN A. Optimality Of Gaussian Attacks In Continuous-Variable Quantum Cryptography[J]. Physical Review Letters, 2006(97):190502. |
| [9] | RENNER R, CIRAC J I.Definetti Representation Theorem For Infinite-Dimensional Quantum Systems And Applications To Quantum Cryptography[J]. Physical Review Letters, 2009(102): 110504. |
| [10] | LEVERRIER A, GARCÍA-PATRÓN R, RENNER R, et al. Security Of Continuous-Variable Quantum Key Distribution Against General Attacks[J]. Physical Review Letters, 2013(110): 030502. |
| [11] | LEVERRIER A.Composable Security Proof For Continuous-Variable Quantum Key Distribution With Coherent States[J]. Physical Review Letters, 2015(114): 070501. |
| [12] | HUANG Peng, HE Guangqiang, ZENG Guihua.Bound On Noise Of Coherent Source For Secure Continuous-Variable Quantum Key Distribution[J]. Int. J. Theor. Phys, 2013(52): 1572-1582. |
| [13] | HUANG Peng, LIN Dakai, HUANG Duan, et al.Security Of Continuous-Variable Quantum Key Distribution With Imperfect Phase Compensation[J]. Int. J. Theor. Phys., 2015, 52(5):1572-1582. |
| [14] | WANG Chao, HUANG Peng, HUANG Duan, et al.Practical Security Of Continuous-Variable Quantum Key Distribution With Finite Sampling Bandwidth Effects[J]. Physical Review A, 2016, 93(2): 022315. |
| [15] | MA XiangChun, SUN Shihai, JIANG Musheng, et al.Local Oscillator Fluctuation Opens A Loophole For Eve In Practical Continuous-Variable Quantum-Key-Distribution Systems[J]. Physical Review A, 2013(88):022339. |
| [16] | HUANG Jingzheng, WEEDBROOK C, YIN Zhenqiang, et al.Quantum Hacking Of A Continuous-Variable Quantum-Key-Distributionsystem Using A Wavelength Attack[J]. Physical Review A, 2013(87):062329. |
| [17] | HUANG Jingzheng.Quantum Hacking on Quantum Key Distribution using Homodyne Detection[J].Physical Review A, 2014(89):032304. |
| [18] | MA Xiangchun, SUN Shihai, JIANG Musheng, et al.Wavelength Attack on Practical Continuous-variable Quantum-key-distribution System with a Heterodyne Protocol[J].Physical Review A, 2013(87):052309. |
| [19] | PAUL J, SEBASTIEN K J, ELENI D.Preventing Calibration Attacks on the Local Oscillator in Continuous-variable Quantum Key Distribution[J]. Physical Review A, 2013(87):062313. |
| [20] | QIN H, KUMAR R, ALLEAUME R. Saturation Attack on Continuous-variable Quantum Key Distribution System [EB/OL]. , 2017-8-1. |
| [21] | HUANG Peng, FANG Jian, ZENG Guihua.State-Discrimination Attack On Discretely Modulated Continuous-Variable Quantum Key Distribution[J]. Physical Review A, 2014, 89(4): 042330. |
| [22] | QIN Hao, KUMAR Rupesh, ALLEAUME Romain.Quantum Hacking: Saturation Attack On Practical Continuous-Variable Quantum Key Distribution[J]. Physical Review A, 2016(94): 012325. |
| [23] | LI Zhengyu, ZHANG Yichen, XU Feihu.Continuous-variable Measurement-device-independent QuantumKey Distribution[J]. Physical Review A, 2014(89): 052301. |
| [24] | MA Xiangchun, SUN Shihai, JIANG Musheng.Gaussian-modulated Coherent-state Measurement-device-independent Quantum Key Distribution[J]. Physical Review A, 2014(89):042335. |
| [25] | ZHANG Yichen, LI Zhengyu, YU Song.Continuous-variable Measurement-device-independent Quantum Key Distribution[J]. Physical Review A, 2014(90): 052325. |
| [26] | PIRANDOLA S, OTTAVIANI C, SSPEDALIERI G, et al.High-rate Measurement-device-independent Quantum Cryptography[J]. Nature Photonics, 2015(9): 397-402. |
| [1] | 翟高寿, 刘晨, 向勇. 基于内核函数监控的Linux系统防护方法的研究与实现[J]. 信息网络安全, 2018, 18(3): 26-38. |
| [2] | 夏卓群, 赵磊, 王静, 李文欢. 一种基于虚拟环架构的电力用户隐私保护方法研究[J]. 信息网络安全, 2018, 18(2): 48-53. |
| [3] | 魏书宁, 陈幸如, 唐勇, 刘慧. AR-HELM算法在网络流量分类中的应用研究[J]. 信息网络安全, 2018, 18(1): 9-14. |
| [4] | 赵国锋, 叶飞, 姚永安, 赵岩. 一种面向云中心网络入侵检测的多模式匹配算法[J]. 信息网络安全, 2018, 18(1): 52-57. |
| [5] | 亢保元, 王佳强, 邵栋阳, 李春青. 一种适用于异构Ad Hoc无线传感器网络的身份认证与密钥共识协议[J]. 信息网络安全, 2018, 18(1): 23-30. |
| [6] | 石悦, 李相龙, 戴方芳. 一种基于属性基加密的增强型软件定义网络安全框架[J]. 信息网络安全, 2018, 18(1): 15-22. |
| [7] | 张建标, 赵子枭, 胡俊, 王晓. 云环境下可重构虚拟可信根的设计框架[J]. 信息网络安全, 2018, 18(1): 1-8. |
| [8] | 章红艳, 许力, 林丽美. 无线传感器网络中基于超立方体的对密钥建立方案研究[J]. 信息网络安全, 2017, 17(12): 1-5. |
| [9] | 宋利民, 宋晓锐. 一种基于混合加密的数据安全传输方案的设计与实现[J]. 信息网络安全, 2017, 17(12): 6-10. |
| [10] | 赵国锋, 赵岩, 王新恒, 叶飞. Web通信中可疑域名监控与反制系统的设计[J]. 信息网络安全, 2017, 17(12): 11-16. |
| [11] | 唐春明, 高隆. 区块链系统下的多方密钥协商协议[J]. 信息网络安全, 2017, 17(12): 17-21. |
| [12] | 徐洋, 陈燚, 何锐, 谢晓尧. SDN中DDoS检测及多层防御方法研究[J]. 信息网络安全, 2017, 17(12): 22-28. |
| [13] | GULKhanSafiQamas, 王鹏, 罗森林, 潘丽敏. 一种高并发网络Web应用技术研究[J]. 信息网络安全, 2017, 17(12): 29-35. |
| [14] | 吴同, 李思其, 杨卫军, 赵利. 基于KMP算法的云存储数据取证方法研究[J]. 信息网络安全, 2017, 17(12): 36-39. |
| [15] | 李红灵, 邹建鑫. 基于SVM和文本特征向量提取的SQL注入检测研究[J]. 信息网络安全, 2017, 17(12): 40-46. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||