信息网络安全 ›› 2016, Vol. 16 ›› Issue (9): 51-55.doi: 10.3969/j.issn.1671-1122.2016.09.010
路由器取证研究
- 河北省公安厅,河北石家庄 050000
Research on Routers Forensic
- Department of Public Security of Hebei Province, Shijiazhuang Hebei 050000, China
摘要:
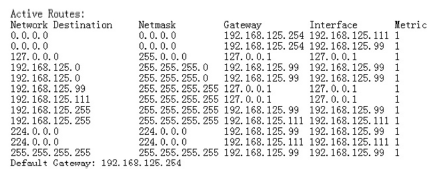
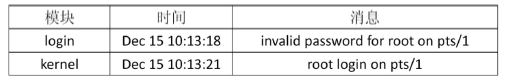
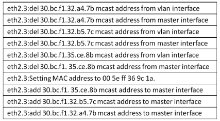
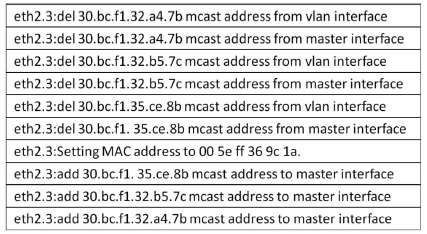
路由器作为一种普遍应用的网络设备,从其诞生就与网络犯罪纠缠在了一起,或者为网络犯罪提供网络传输,或者成为网络犯罪的对象,其存储器中通常保存有网络犯罪侦查的线索和证据。由于路由器具有自身特定的软硬件运行机制,需要通过特定的取证流程才能完整有效地提取、固定其中的电子证据。文章在介绍路由器基本功能的基础上,分析了路由器取证对网络犯罪侦查的重要作用。文章分别探讨了骨干级、企业级、接入级路由器的配置、日志等电子数据信息的查看、提取、固定的方法和流程,介绍了提取、分析路由表的要点。此外,文章还提出了智能路由器的取证方法。文章阐述了通过端口镜像技术提取、固定路由器正在转发的数据包的方法,实现了对路由器的全面取证。文章最后结合网络犯罪侦查和电子数据取证工作的基本要求和原则,针对路由器数据易丢失、不易提取固定的特性,给出了路由器取证的注意事项,以保障路由器取证的全面性、客观性和有效性。
中图分类号: