信息网络安全 ›› 2016, Vol. 16 ›› Issue (8): 32-38.doi: 10.3969/j.issn.1671-1122.2016.08.006
基于CPK的无线Mesh网络节点双向认证方案研究
- 1. 海军装备部,湖北武汉 430000
2. 海军工程大学,湖北武汉 430000
3. 92325部队,山西大同 037000
Research on Two-way Authentication Scheme for Wireless Mesh Network Based on CPK
Dongzhen LI1, Chenghua YAN2, Xun LUO3( )
)
- 1. Naval Armaments Department, Wuhan Hubei 430000, China
2. Naval University of Engineering, Wuhan Hubei 430000, China
3.Unit 92325, PLA, Datong Shanxi 037000, China
摘要:
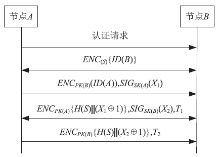
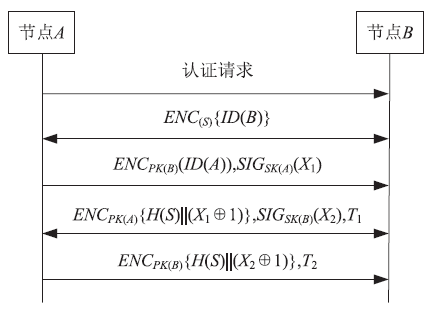
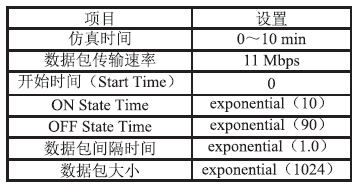
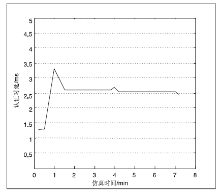
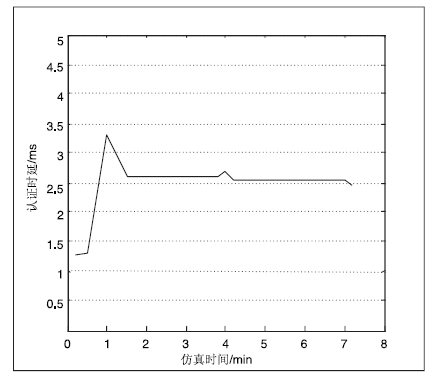
无线Mesh网络是一种新型的无线网络,它是WLAN和移动自组网的结合,同时兼有二者的优点,因而具有很大的发展潜力。然而安全问题一直是制约其发展的根本性问题,节点认证是保证无线Mesh网络安全的第一道屏障。文章通过对比分析IBC认证和CPK认证的优缺点,得出CPK组合公钥具有密钥空间巨大、密钥管理简单、安全性和保密性高等特点,特别适合大规模的网络节点接入。为解决无线Mesh网络节点安全、高效入网认证的问题,文章提出了基于CPK的无线Mesh网络节点双向认证方案,该方案针对Mesh网络特点,将CPK组合公钥技术引入到无线Mesh网络节点认证当中,在此基础上结合公钥密码体制和设置挑战随机数、时间戳等,实现了入网节点的双向身份认证,简化了认证的流程,减少了认证的时延,为大规模的节点接入提供了一种新的认证方案。最后通过安全分析和仿真验证,证明了该方案的安全性和有效性。
中图分类号: