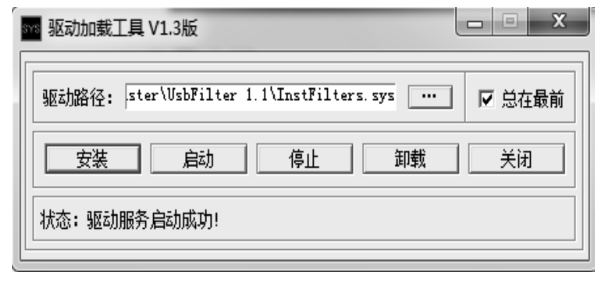
| [1] |
CHEN Ping, LIEVEN D, CHRISTOPHE H.A Study on Advance Persistent Threats[C]//IFIP. Communications and Multimedia Security, September 25-26, 2014.Aveiro, Portugal. Berlin Heidelberg: Springer , 2014: 63-72.
|
| [2] |
李凤海,李爽,张佰龙,等. 高等级安全网络抗APT攻击方案研究[J]. 信息网络安全,2014(9):109-114.
|
| [3] |
LANGNER R.Stuxnet: Dissecting a Cyberwarfare Weapon[C]// IEEE Computer Society. Security & Privacy, IEEE, May 23-24, 2011.Claremont Resort in Oakland, California. New York: IEEE, 2011, 9(3): 49-51.
|
| [4] |
王在富. 浅析APT 攻击检测与防护策略[J]. 无线互联科技,2014(3): 120-121.
|
| [5] |
NSFOCUS Information Technology Co Ltd. 2014 ICS Security Report[EB/OL]. , 2014-3-11.
|
| [6] |
李永强, 谭立清, 马同茂,等. USB移动存储设备密级保护系统的设计与实现[J]. 计算机光盘软件与应用, 2014, 17(13): 89-91.
|
| [7] |
陈晨,王奕钧,胡光俊,等. 针对手机的APT攻击方式的研究[J]. 信息网络安全,2015(3):33-37.
|
| [8] |
NIST. Managing Information Security Risk: Organization, Mission, and Information System View[EB/OL]. , 2011-3-1.
|
| [9] |
FireEye Labs. Fireeye Advanced Threat Report[EB/OL].,2014-2-15.
|
| [10] |
DIWAN S A, PERUMAL S, FATAH A J.Complete Security Package for USB Thumb Drive[J].Computer Engineering and Intelligent Systems, 2014, 5(8):30-37.
|
| [11] |
樊少.新的U盘自动运行—BadUSB原理与实现[EB/OL].,2014-12-9.
|
| [12] |
杨思燕. USB可移动存储设备监控软件研究与实现[J]. 计算机技术与发展, 2013, 23(12): 151-154.
|
| [13] |
LI Shaobo, JIA Xiaohui, LV Shulin, et al.Research and Application of USB Filter Driver Based on Windows Kernel[C]//IEEE Computer Society. Third International Symposium on Intelligent Information Technology and Security Informatics, April 2-4 2010. Jinggangshan, China. New York: IEEE, 2010: 438-441
|
| [14] |
ALZAROUNI M.The Reality of Risks from Consented Use of USB Devices[C]//Edith Cowan University. Proceedings of 4th Australian Information Security Management Conference, December 5, 2006. Edith Cowan University, Perth, Western Australia. Perth: School of Computer and Information Science, Edith Cowan University, 2006: 312-317.
|
| [15] |
卢志刚,刘建华,刘宝旭,等.基于HID 的 USB 监控技术的设计与实现[J]. 计算机工程, 2010,36(4): 1-3.
|
| [16] |
李锦山,舒辉,萱卫宇,等. 基于驱动层的USB存储设备安全监控技术[J]. 计算机工程,2008,34(8):255-257.
|
| [17] |
NOHL K, KRIBLER S, LEHL J. BadUSB-on Accessories That Turn Evil[EB/OL].https://srlabs.de/blog/wp-content/uploads/2014/07/SRLabs-BadUSB-BlackHat-v1.pdf (2014), 2014-8-6.
|
| [18] |
孙玉伟,童新海,张林惠,等. 云桌面中USB设备重定向技术研究[J]. 信息网络安全,2015(4):78-85.
|
 ), Jing MA2
), Jing MA2