信息网络安全 ›› 2014, Vol. 14 ›› Issue (11): 18-25.doi: 10.3969/j.issn.1671-1122.2014.11.003
基于遍历矩阵和混合密钥的验证和图像空域加密技术
- 海南大学信息科学技术学院,海南海口 570228
-
收稿日期:2014-09-23出版日期:2014-11-01发布日期:2020-05-18 -
作者简介:作者简介:周晓谊(1979-),女,海南,副教授,博士,主要研究方向:密码、信息隐藏等;段玉聪(1977-),男,河南,教授,博士,主要研究方向:软件工程;冯文龙(1968-),男,贵州,副教授,硕士,主要研究方向:信息网络理论与技术;李益红(1979-),男,江西,副教授,博士研究生,主要研究方向:图像处理。
-
基金资助:海南省自然科学基金[613152,614226].海南省教育厅课题[Hjkj2013-14]
Authentication and Image Spatial Encryption Based on Ergodic Matrix and Hybrid Key System
ZHOU Xiao-yi, DUAN Yu-cong, FENG Wen-long, LI Yi-hong( )
)
- College of Information Science & Technology, Hainan University, Haikou Hainan 570228, China
-
Received:2014-09-23Online:2014-11-01Published:2020-05-18
摘要:
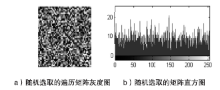
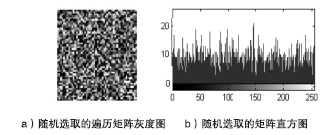
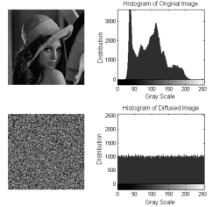
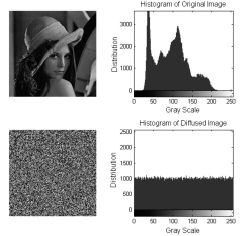
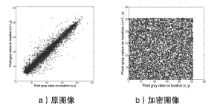
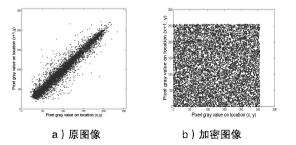
由于图像与人感知外部世界的基本手段相吻合,因此相关的信息量有可能涉及到个人隐私、商业利益、军事机密等,所以多媒体信息的安全问题变得越来越重要。传统的加密系统,如RSA、DES、IDEA、SAFER和FEAL等,其加密速度慢而且不能有效去除相邻像素的相关性,不适合用于图像加密。经过二十多年研究的混沌加密系统具有良好的特性适合图像加密,但大部分是基于对称加密。对称加密比非对称加密速度更快,但是对于密钥的管理制约了其广泛的使用,为了弥补这一缺陷,文章提出混合密钥机制,不仅可用于图像加密,而且可用于验证。遍历矩阵在加/解密系统中不仅作为公开密钥存在,而且是图像置乱和扩散的关键参数。实验结果表明,与现有的混沌加密系统相比,文章提出的图像加密技术彻底置乱和扩散原始图像,并且拥有至少3.08×105898个密钥的巨大空间,因此足够抵制蛮力攻击。相比于现有的混沌密码系统,文章的实验测试结果更加乐观,在C语言下,置乱和扩散阶段的执行时间相当稳定(分别是1.9~2.0毫秒和2.0~2.1毫秒)。与Yang和Ismail所提出的算法相比,根据文章中的性能评估、敏感度分析和统计分析,文章所提出的算法具有更高的安全性,并且适用于网络传输。
中图分类号:
引用本文
周晓谊, 段玉聪, 冯文龙, 李益红. 基于遍历矩阵和混合密钥的验证和图像空域加密技术[J]. 信息网络安全, 2014, 14(11): 18-25.
ZHOU Xiao-yi, DUAN Yu-cong, FENG Wen-long, LI Yi-hong. Authentication and Image Spatial Encryption Based on Ergodic Matrix and Hybrid Key System[J]. Netinfo Security, 2014, 14(11): 18-25.
| [1] | Furht B, Kirovski D.Multimedia Security Handbook[M].Florida: CRC Press, 2005. |
| [2] | Acharya B, Panigrahy S.K., et al. Image Encryption Using Advanced Hill Cipher Algorithm[J]. International Journal of Recent Trends in Engineering, 2009,1(1): 663-667. |
| [3] | Öztürk I, Sogukpınar I.Analysis and Comparison of Image Encryption Algorithms[J]. World Academy of Science, Engineering and Technology,2005,(3): 26-30. |
| [4] | Diffie W, Hellman M E.New Directions in Cryptography[J]. IEEE Transactions on Information Theory,1976,22(6): 644-654. |
| [5] | Zhang L, Liao X, Wang X.An image encrypton approach based on chaotic maps[J]. Chaos, Solitions and Fractals,2005,(24): 759-765. |
| [6] | Fridrich J.Symmetric ciphers based on two-dimensional chaotic maps[J]. International Journal of Bifurcation and Chaos,1998, 8(6): 1259-1284. |
| [7] | Giesl J, Behal L, et al.Improving Chaos Image Encryption Speed[J]. International Journal of Future Communication and Networking ,2009,2(3): 23-36. |
| [8] | Miao Y, Chen G, et al.A novel fast image encryption scheme based on 3D chaotic baker maps[J]. International Journal of Bifurcation and Chaos,2004,14(10): 3613-3624. |
| [9] | Chen G, Mao Y, et al.A symmetric image encryption scheme based on 3D chaotic cat maps[J]. Chaos, Solitions and Fractals, 2004, (21): 749-761. |
| [10] | Guan Z, Huang F, et al.Chaos-based image encryption algorithm[J]. Physics Letters A, 2005, 346(1-3): 153-157. |
| [11] | Yang H, Wong K, et al.A fast image encryption and authentication scheme based on chaotic maps[J]. Communications in Nonlinear Science and Numerical Simulation, 2010, 15(11): 3507-3517. |
| [12] | Zhao Y, Wang L, et al.Information-Exchange Using the Ergodic Matrices in GF(2)[C]//Proceedings of the 2nd ACM symposium on Information, Computer and Communications Security ACNS 2004: 347-349. |
| [13] | Anonymous. Introduction to public-key cryptography[EB/OL]. . |
| [14] | Menezes A. J.,P. C. v. Oorschot, et al. (1996). Handbook of Applied Cryptography. United States, CRC Press: 816. |
| [15] | Lin Shen-yi, Chen Chih-shen, Li Liu, et al.Tensor product formulation for Hilbert space-filling curves[C]//Proceedings of Parallel Processing, Kaohsiung, 2003:99-106. |
| [16] | Josef S.Secure digital watermark generation based on chaotic Kolmogorov flows[C]//Security and Watermarking of Multimedia Content II, Proceedings of SPIE, 2000,(3971): 306-313. |
| [17] | Jormakka J. Symmetric and asymmetric cryptography overview[EB/OL]. . |
| [18] | 赵永哲,黄声烈,邢磊. 与计算能力无关之密码体制研究[J]. 现代情报,2003,(06):86-87. |
| [19] | 赵永哲,黄声烈,赵焱,等. 程序功能的局限性与密码系统[J]. 吉林大学学报(工学版), 2004,(03):173-177. |
| [20] | 赵永哲,黄声烈,姜占华. GF(2~k)上的遍历矩阵及其特性分析[J]. 小型微型计算机系统,2005,(12):73-77. |
| [21] | 孙永雄,赵永哲,杨永健,等.基于遍历矩阵的单向(陷门)函数的构造方案[J]. 吉林大学学报(信息科学版),2006,(05):102-103. |
| [22] | 周晓谊,赵永哲. 遍历矩阵及其单向限门函数在密码学中的应用[J]. 信息安全与通信保密,2006,(05):112-113,116. |
| [23] | Zhou X, Ma J, et al.BMQE system: an MQ euqations system based on ergodic matrix[C]// Proceedings of the International Conference on Security and Cryptography,2010: 431-435. |
| [24] | Zhou Xiao-yi, Ma Ji-xin, Du Wen-cai, et al.Cryptanalysis of the bisectional MQ equations system[C]// In Proceedings of the 2010 10th IEEE International Conference on Computer and Information Technology, CIT ’10, Washington, DC, USA, 2010:1038-1043. |
| [25] | 宋严,赵永哲. I-HFEM公钥密码方案在数字签名应用上的特性研究[J]. 长春师范学院学报,2013,(08):23-26. |
| [26] | Ismail I A, Amin M, et al.A digital image encryption algorithm based a composition of two chaotic logisitc maps[J]. International Journal of Network Security,2010,11(1): 1-10. |
| [27] | Runger G C, Eaton M L.Most powerful invariant permutation tests[J]. Journal of Multivariate Analysis,1992,42(2): 202-209. |
| [28] | Miyamoto M, Tanaka K, et al.Truncated baker transformation and its extension to image encryption[C]// Proceedings of SPIE on Advanced Materials and Optical System for Chemical, 1999,(3858): 13-25. |
| [29] | Parberry I.Scalability of a neural network for the Knight's tour problem[]J. Neurocomputing 1996,12(1,15): 19-33. |
| [30] | Parberry I.An efficient algorithm for the Knight's tour problem[J]. Discrete Applied Mathematics,1997,73(3,21): 251-260. |
| [31] | Shannon C.Communication theory of secrecy systems[J]. Bell System Technical Journal,1949,28(4): 656-715. |
| [32] | Zhao Y.,S. Pei, et al. Using the Ergodic Matrices over Finite Field to Construct the Dynamic Encryptor[J]. Journal of Chinese Computer Systems, 2007,(11): 2010-2014. |
| [33] | Ye Guo-dong.Image scrambling encryption algorithm of pixel bit based on chaos map[J]. Pattern Recognition Letters,2010,(31) :347-354. |
| [34] | Lian S, Sun J, et al.A block cipher based on a suitable use of the chaotic standard map[J]. Chaos, Solitions and Fractals,2005,(26):177-129. |
| [1] | 董云云, 朱玉玲, 姚绍文. 基于改进U-Net和混合注意力机制的高质量全尺寸图像隐写方法[J]. 信息网络安全, 2024, 24(7): 1050-1061. |
| [2] | 何业锋, 权家辉, 刘妍. 基于混合区块链的位置隐私保护方案[J]. 信息网络安全, 2024, 24(2): 229-238. |
| [3] | 李莉, 朱江文, 杨春艳. 基于属性加密的可撤销机制研究综述[J]. 信息网络安全, 2023, 23(4): 39-50. |
| [4] | 刘兴斌, 刘聪. 基于级联混沌系统和量子Baker映射的图像加密算法[J]. 信息网络安全, 2023, 23(12): 49-58. |
| [5] | 佟晓筠, 毛宁, 张淼, 王翥. 基于Henon映射与改进的提升小波变换图像加密算法[J]. 信息网络安全, 2022, 22(9): 31-39. |
| [6] | 汪勍, 徐国天. 基于改进Logistic映射和双图混合的加密算法[J]. 信息网络安全, 2022, 22(12): 76-86. |
| [7] | 李丹, 燕婷, 郭瑞. 基于交替量子漫步的量子彩色图像加密算法[J]. 信息网络安全, 2021, 21(6): 45-51. |
| [8] | 郑洪英, 李琳, 肖迪. 面向雾计算的压缩感知图像秘密传输和篡改恢复方案[J]. 信息网络安全, 2021, 21(4): 10-20. |
| [9] | 郭烜臻, 潘祖烈, 沈毅, 陈远超. 一种基于被动DNS数据分析的DNS重绑定攻击检测技术[J]. 信息网络安全, 2021, 21(3): 87-95. |
| [10] | 罗文华, 程家兴. 基于Hadoop架构的混合型DDoS攻击分布式检测系统[J]. 信息网络安全, 2021, 21(2): 61-69. |
| [11] | 张玉磊, 骆广萍, 王欢, 刘祥震. 5G网络下可证安全的TPKC-CLPKC异构混合签密方案[J]. 信息网络安全, 2019, 19(5): 30-37. |
| [12] | 梅东晖, 李红灵. 基于多目标混合粒子群算法的虚拟机负载均衡研究[J]. 信息网络安全, 2018, 18(2): 78-83. |
| [13] | 陈小明, 游伟青, 李文喜, 蒋浩. 一类可逆矩阵在保密通信中的应用[J]. 信息网络安全, 2017, 17(5): 7-7. |
| [14] | 楼叶. 基于信息传播模型研究的舆情导控方法探寻[J]. 信息网络安全, 2016, 16(9): 257-266. |
| [15] | 陈飞, 司一帆, 韩益亮. 适用于PHR系统的混合属性加密签名方案[J]. 信息网络安全, 2016, 16(12): 46-50. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||