信息网络安全 ›› 2025, Vol. 25 ›› Issue (5): 794-805.doi: 10.3969/j.issn.1671-1122.2025.05.011
基于包长序列的恶意通信行为隐蔽变换方法研究
- 1.四川大学网络空间安全学院,成都 610065
2.数据安全防护与智能治理教育部重点实验室,成都 610065
3.四川大学网络空间安全研究院,成都 610065
-
收稿日期:2025-02-15出版日期:2025-05-10发布日期:2025-06-10 -
通讯作者:陈兴蜀chenxsh@scu.edu.cn -
作者简介:杨榉栋(2000—),男,四川,硕士研究生,主要研究方向为网络安全|陈兴蜀(1968—),女,贵州,教授,博士,主要研究方向为云计算安全、数据安全、威胁检测、开源情报和人工智能安全|朱毅(1991—),男,四川,博士研究生,主要研究方向为网络行为与威胁识别 -
基金资助:四川省自然科学基金(2024NSFSC1450);中央高校基础研究基金(SCU2024D01);中央高校基础研究基金(2023SCU12126);四川大学理工科发展计划(2020SCUNG129)
Research on Covert Transformation Method for Malicious Communication Behavior Based on Packet Length Sequence
YANG Judong1,2,3, CHEN Xingshu1,2,3( ), ZHU Yi1,2,3
), ZHU Yi1,2,3
- 1. School of Cyber Science and Engineering, Sichuan University, Chengdu 610065, China
2. Key Laboratory of Data Protection and Intelligent Management, Ministry of Education, Chengdu 610065, China
3. Cyber Science Research Institute, Sichuan University, Chengdu 610065, China
-
Received:2025-02-15Online:2025-05-10Published:2025-06-10
摘要:
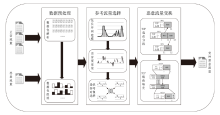
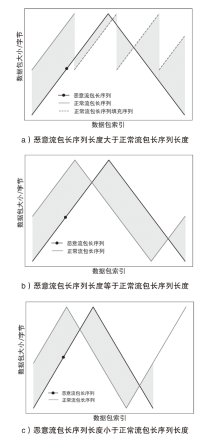
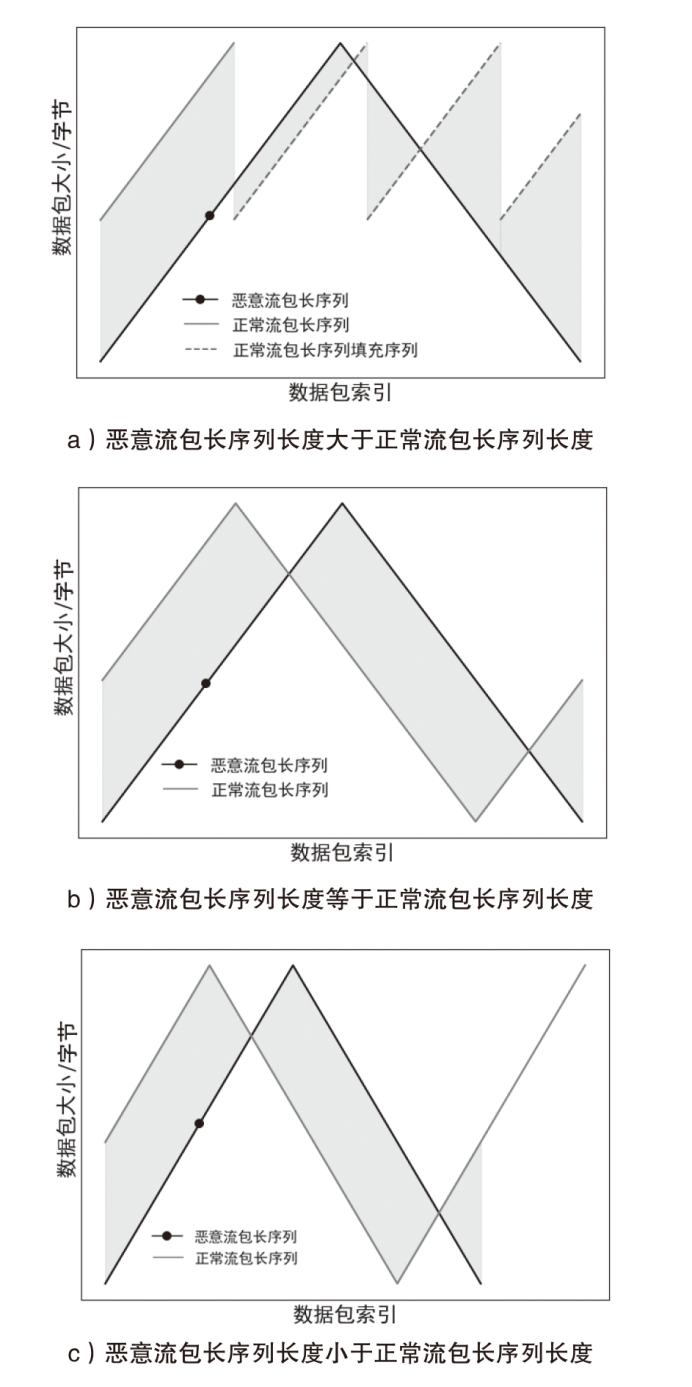
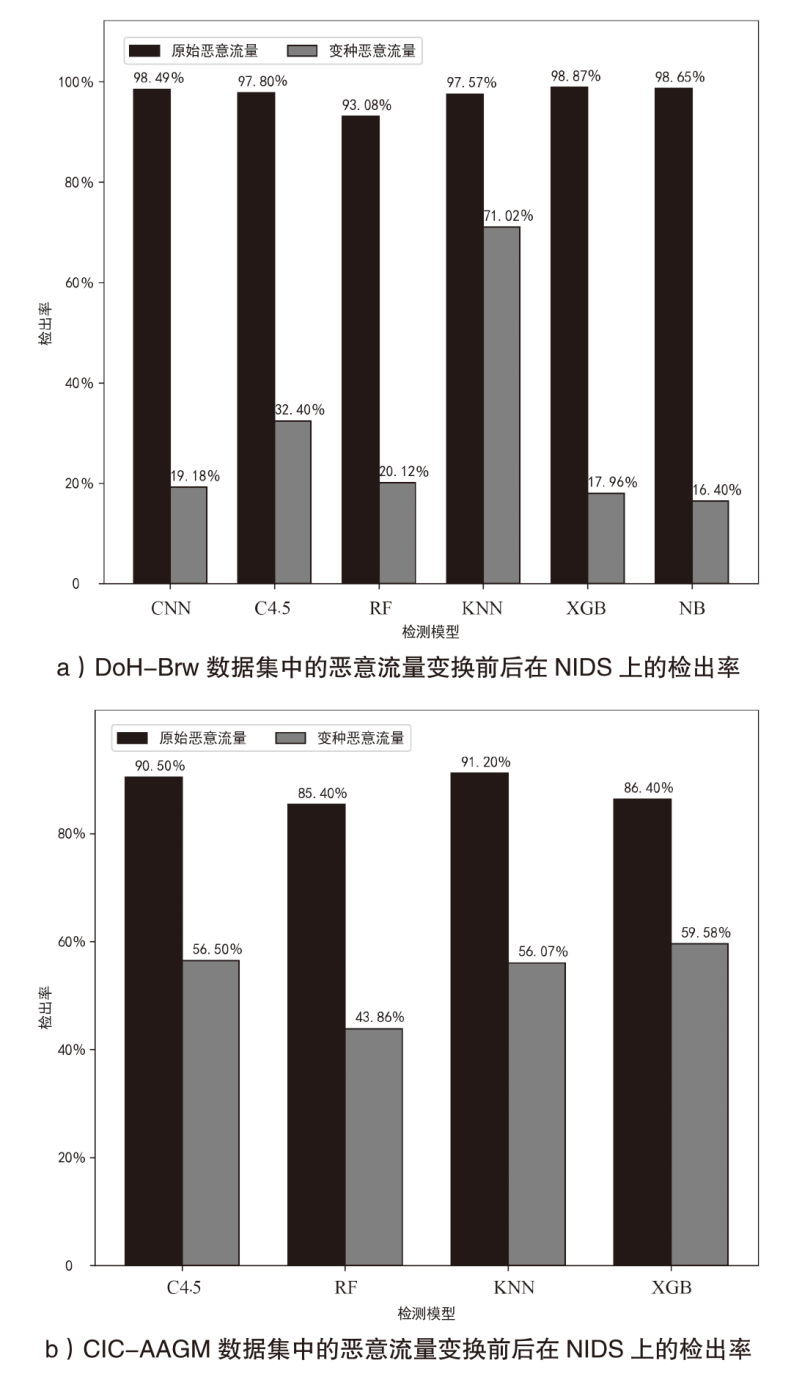
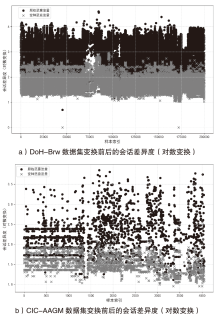
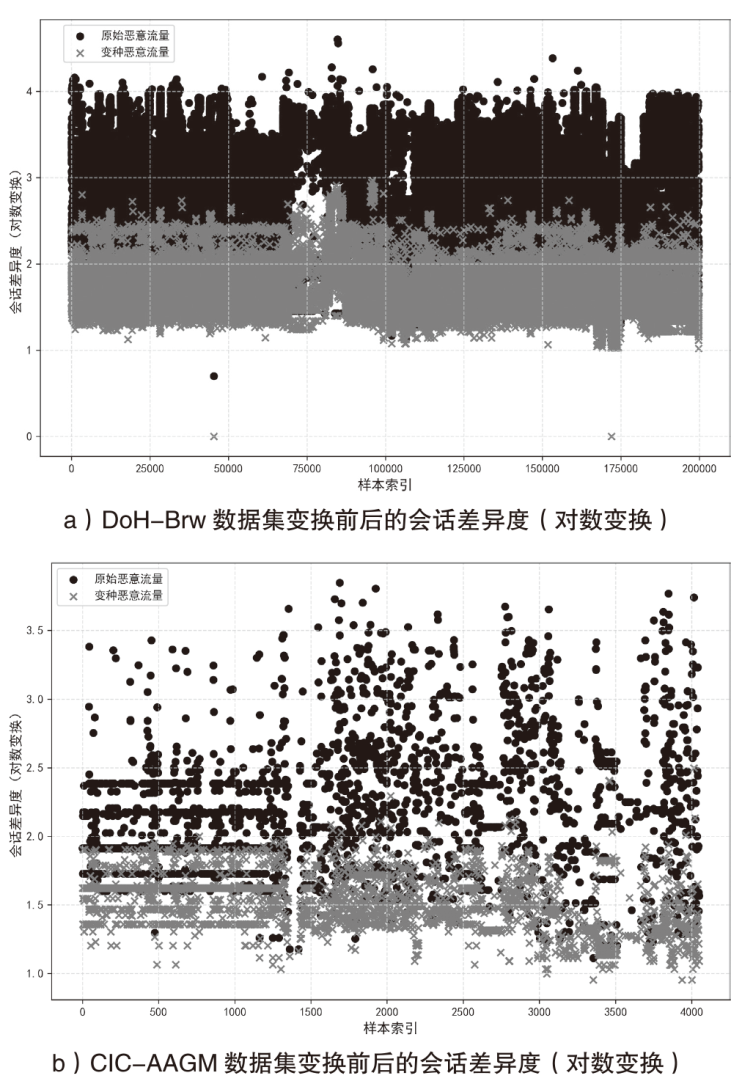
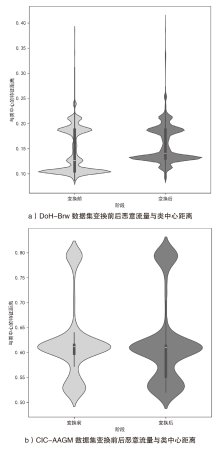
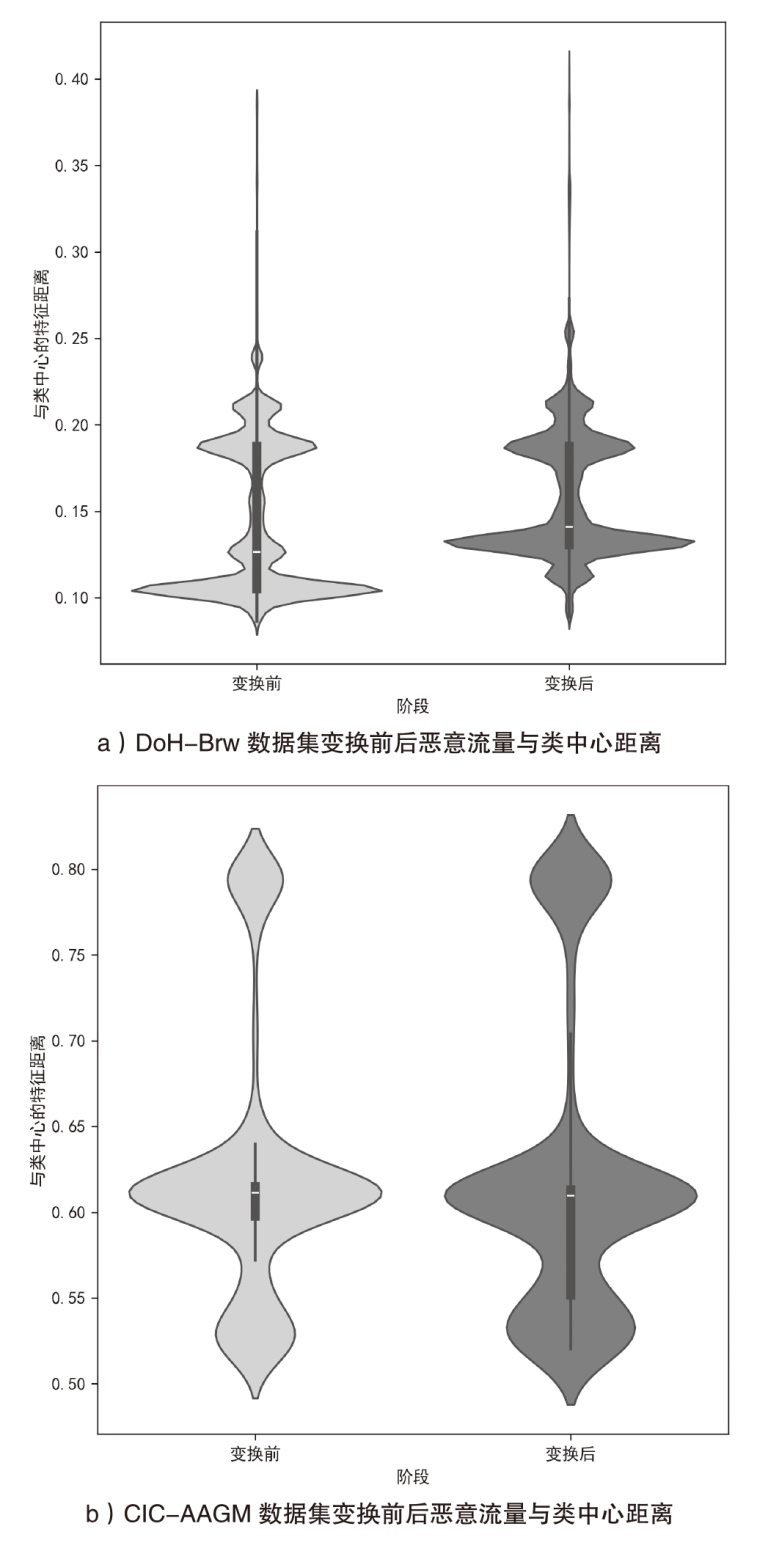
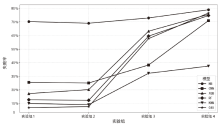
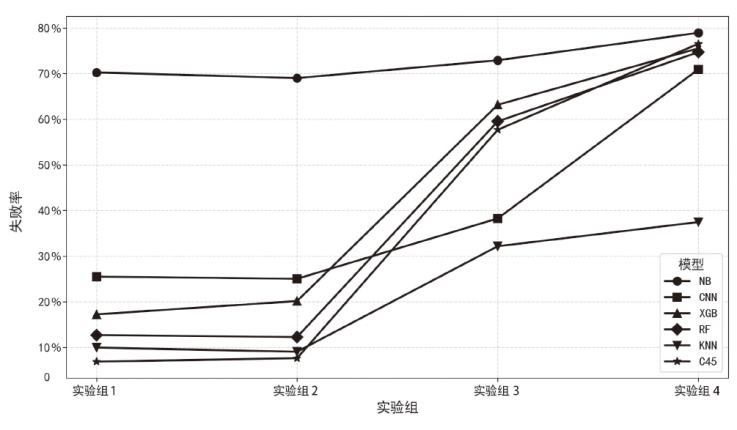
为了向网络入侵检测系统(NIDS)提供变种恶意流量以评估检测模型的能力,文章针对恶意通信行为隐蔽变换方法开展研究。首先,文章通过包长序列刻画流量通信行为,包长序列的改变能够指导恶意流量在数据层面的变换以得到真实可用的变种恶意流量,进而影响数据包长度的相关统计特征以干扰NIDS检测结果;然后,基于包长序列设计了一种恶意通信行为隐蔽变换方法,该方法选择与待变换恶意流量在包长序列属性上最相似的正常流量作为参考流量,并通过TCP载荷填充和分段两种策略调整恶意流量中数据包的大小,使变种恶意流量的包长序列与正常流量相似,从而实现变种恶意流量对正常流量通信行为的模拟;最后,基于DoH-Brw数据集和CIC-AAGM数据集构建测试数据集,实验结果表明,基于DoH-Brw数据集生成的变种恶意流量在6种NIDS上的检出率平均下降超过 60%,基于CIC-AAGM数据集在4种NIDS上的检出率平均下降超过30%,有效证明了该方法的有效性。
中图分类号:
引用本文
杨榉栋, 陈兴蜀, 朱毅. 基于包长序列的恶意通信行为隐蔽变换方法研究[J]. 信息网络安全, 2025, 25(5): 794-805.
YANG Judong, CHEN Xingshu, ZHU Yi. Research on Covert Transformation Method for Malicious Communication Behavior Based on Packet Length Sequence[J]. Netinfo Security, 2025, 25(5): 794-805.
表1
NIDS检测特征
| 数据集 | 特征名称 |
|---|---|
| DoH-Brw | 数据包长度均值、数据包长度中位数、数据包长度众数、数据包长度方差、数据包长度标准差、数据包长度变异系数、数据包长度相对于中位数的偏斜度、数据包长度相对于众数的偏斜度、请求方发送字节数、响应方发送字节数、数据包时间间隔均值、数据包时间间隔中位数、数据包时间间隔众数、数据包时间间隔方差、数据包时间间隔标准差、数据包时间间隔变异系数、数据包时间间隔相对于中位数的偏斜度、数据包时间间隔相对于众数的偏斜度、响应时间均值、请求/响应时间差的中位数、响应时间众数、响应时间方差、响应时间标准差、响应时间变异系数、响应时间相对于中位数的偏斜度、响应时间相对于众数的偏斜度、请求方发送速率、响应方发送速率 |
| CIC-AAGM | 最大流数据包长度、最小流数据包长度、反向数据字节的方差、流中的 FIN 标志计数、流中正向的字节数、流中反向的字节数、最大空闲时间、正向初始窗口大小、正向最小段大小 |
| [1] | DEEPEN D. ThreatLabz Report:87.2% of Threats Delivered over Encrypted Channels[EB/OL]. (2024-12-05)[2025-01-25]. https://www.zscaler.com/blogs/security-research/threatlabz-report-threats-delivered-over-encrypted-channels. |
| [2] | SIMONOVICH E M V. Highlights from Q3 2024 Cato CTRL SASE Threat Report[EB/OL]. (2024-11-19)[2025-01-25]. https://www.catonetworks.com/blog/highlights-from-q3-2024-cato-ctrl-sase-threat-report/. |
| [3] | ABDULGANIYU O H, TCHAKOUCHT T A, SAHEED Y K. Towards an Efficient Model for Network Intrusion Detection System(IDS): Systematic Literature Review[J]. Wireless Networks, 2024, 30(1): 453-482. |
| [4] | HOU Jian, LU Hui, LIU Fang'ai, et al. Detection and Countermeasure of Encrypted Malicious Traffic: A Survey[J]. Journal of Software, 2024, 35(1): 333-355. |
| 侯剑, 鲁辉, 刘方爱, 等. 加密恶意流量检测及对抗综述[J]. 软件学报, 2024, 35(1): 333-355. | |
| [5] | NIAKANLAHIJI A, ORLOWSKI S, VAHID A, et al. Toward Practical Defense against Traffic Analysis Attacks on Encrypted DNS Traffic[J]. Computers & Security, 2023, 124: 103001-103014. |
| [6] | QIAN Yuwei, HUANG Guodong, MA Chuan, et al. Enhancing Resilience in Website Fingerprinting: Novel Adversary Strategies for Noisy Traffic Environments[J]. IEEE Transactions on Information Forensics and Security, 2024, 19: 7216-7231. |
| [7] | XIONG Sijie, SARWATE A D, MANDAYAM N B. Network Traffic Shaping for Enhancing Privacy in IoT Systems[J]. IEEE/ACM Transactions on Networking, 2022, 30(3): 1162-1177. |
| [8] | VERGUTZ A, SANTOS B V D, KANTARCI B, et al. Data Instrumentation from IoT Network Traffic as Support for Security Management[J]. IEEE Transactions on Network and Service Management, 2023, 20(2): 1392-1404. |
| [9] | WANG Shunyao, KO R K L, BAI Guangdong, et al. Evasion Attack and Defense on Machine Learning Models in Cyber-Physical Systems: A Survey[J]. IEEE Communications Surveys & Tutorials, 2024, 26(2): 930-966 |
| [10] | ZHU Yiran, CUI Lei, DING Zhenquan, et al. Black Box Attack and Network Intrusion Detection Using Machine Learning for Malicious Traffic[J]. Computers & Security, 2022, 123: 102922-102936. |
| [11] | WANG Minxiao, YANG Ning, FORCADE-PERKINS N J, et al. ProGen: Projection-Based Adversarial Attack Generation against Network Intrusion Detection[J]. IEEE Transactions on Information Forensics and Security, 2024, 19: 5476-5491. |
| [12] | ZHANG Rongqian, LUO Senlin, PAN Limin, et al. Generating Adversarial Examples via Enhancing Latent Spatial Features of Benign Traffic and Preserving Malicious Functions[J]. Neurocomputing, 2022, 490(14): 413-430. |
| [13] | ZHANG Chaoyun, COSTA-PÉREZ X, PATRAS P, et al. Adversarial Attacks against Deep Learning-Based Network Intrusion Detection Systems and Defense Mechanisms[J]. IEEE/ACM Transactions on Networking, 2022, 30(3): 1294-1311. |
| [14] | HE Daojing, DAI Jiayu, LIU Xiaoxia, et al. Adversarial Attacks for Intrusion Detection Based on Bus Traffic[J]. IEEE Network, 2022, 36(4): 203-209. |
| [15] | LIU Jian, XIAO Qingsai, JIANG Zhengwei, et al. Effectiveness Evaluation of Evasion Attack on Encrypted Malicious Traffic Detection[C]// IEEE. 2022 IEEE Wireless Communications and Networking Conference (WCNC). New York: IEEE, 2022: 1158-1163. |
| [16] | YAN Haonan, LI Xiaoguang, ZHANG Wenjing, et al. Automatic Evasion of Machine Learning-Based Network Intrusion Detection Systems[J]. IEEE Transactions on Dependable and Secure Computing, 2024, 21(1): 153-167. |
| [17] | DEBICHA I, COCHEZ B, KENAZA T, et al. Adv-Bot: Realistic Adversarial Botnet Attacks against Network Intrusion Detection Systems[J]. Computers & Security, 2023, 129: 103176-103190. |
| [18] | SUN Hanwu, PENG Chengwei, SANG Yafei, et al. Evading Encrypted Traffic Classifiers by Transferable Adversarial Traffic[C]//IEEE. Collaborative Computing:Networking, Applications and Worksharing(CollaborateCom 2022). Heidelberg: Springer, 2022: 153-173. |
| [19] | XU Zhenning, KHAN H, MURESAN R. TMorph: A Traffic Morphing Framework to Test Network Defenses against Adversarial Attacks[C]// IEEE. 2022 International Conference on Information Networking (ICOIN). New York: IEEE, 2022: 18-23. |
| [20] | MONTAZERISHATOORI M, DAVIDSON L, KAUR G, et al. Detection of DoH Tunnels Using Time-Series Classification of Encrypted Traffic[C]// IEEE. 2020 IEEE International Symposium on Dependable, Autonomic and Secure Computing (DASC). New York: IEEE, 2020: 63-70. |
| [21] | LASHKARI A H A. KADIR A F, GONZALEZ H, et al. Towards a Network-Based Framework for Android Malware Detection and Characterization[C]// IEEE. 2017 15th Annual Conference on Privacy, Security and Trust (PST). New York: IEEE, 2020: 23300-23309. |
| [1] | 李俊娥, 马子玉, 陆秋余, 俞凯龙. 融合时序特征的IEC 61850网络攻击智能检测方法[J]. 信息网络安全, 2025, 25(5): 689-699. |
| [2] | 张双全, 殷中豪, 张环, 高鹏. 基于残差卷积神经网络的网络攻击检测技术研究[J]. 信息网络安全, 2025, 25(2): 240-248. |
| [3] | 顾国民, 陈文浩, 黄伟达. 一种基于多模型融合的隐蔽隧道和加密恶意流量检测方法[J]. 信息网络安全, 2024, 24(5): 694-708. |
| [4] | 屠晓涵, 张传浩, 刘孟然. 恶意流量检测模型设计与实现[J]. 信息网络安全, 2024, 24(4): 520-533. |
| [5] | 张国敏, 屠智鑫, 邢长友, 王梓澎, 张俊峰. 基于对抗样本的流量时序特征混淆方法[J]. 信息网络安全, 2024, 24(12): 1882-1895. |
| [6] | 王强, 刘奕智, 李涛, 贺小川. 网络流量密态匿迹与体系对抗综述[J]. 信息网络安全, 2024, 24(10): 1484-1492. |
| [7] | 张俊, 王永杰, 张敬业, 杨林. 基于最优有效路径的域间路由系统级联失效模型[J]. 信息网络安全, 2021, 21(5): 90-99. |
| [8] | 王腾飞, 蔡满春, 芦天亮, 岳婷. 基于iTrace_v6的IPv6网络攻击溯源研究[J]. 信息网络安全, 2020, 20(3): 83-89. |
| [9] | 董威, 李永刚. 基于复杂网络的智能电网网络攻击影响分析研究[J]. 信息网络安全, 2020, 20(1): 52-60. |
| [10] | 陈良臣, 刘宝旭, 高曙. 网络攻击检测中流量数据抽样技术研究[J]. 信息网络安全, 2019, 19(8): 22-28. |
| [11] | 陈冠衡, 苏金树. 基于深度神经网络的异常流量检测算法[J]. 信息网络安全, 2019, 19(6): 68-75. |
| [12] | 傅建明, 黎琳, 郑锐, 苏日古嘎. 基于GAN的网络攻击检测研究综述[J]. 信息网络安全, 2019, 19(2): 1-9. |
| [13] | 鲁刚, 郭荣华, 周颖, 王军. 恶意流量特征提取综述[J]. 信息网络安全, 2018, 18(9): 1-9. |
| [14] | 夏玉明, 胡绍勇, 朱少民, 刘丽丽. 基于卷积神经网络的网络攻击检测方法研究[J]. 信息网络安全, 2017, 17(11): 32-36. |
| [15] | 宋国江, 肖荣华, 晏培. 工业控制系统中PLC面临的网络空间安全威胁[J]. 信息网络安全, 2016, 16(9): 228-233. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||