信息网络安全 ›› 2023, Vol. 23 ›› Issue (11): 27-37.doi: 10.3969/j.issn.1671-1122.2023.11.004
基于安全多方计算的图像分类方法
孙永奇1,2( ), 宋泽文1,2, 朱卫国1,2, 赵思聪3
), 宋泽文1,2, 朱卫国1,2, 赵思聪3
- 1.交通大数据与人工智能教育部重点实验室,北京 100044
2.北京交通大学计算机与信息技术学院,北京 100044
3.北京航天晨信科技有限责任公司,北京 102308
-
收稿日期:2023-08-30出版日期:2023-11-10发布日期:2023-11-10 -
通讯作者:孙永奇yqsun@bjtu.edu.cn -
作者简介:孙永奇(1969—),男,河南,教授,博士,CCF会员,主要研究方向为深度学习和人工智能安全|宋泽文(1999—),男,湖北,硕士研究生,CCF会员,主要研究方向为深度学习和数据隐私保护|朱卫国(1995—),男,天津,博士研究生,CCF会员,主要研究方向为深度学习和数据隐私保护|赵思聪(1987—),男,辽宁,高级工程师,博士,主要研究方向为深度学习和人工智能安全 -
基金资助:科技创新2030—重大项目(2021ZD0113002)
Image Classification Method Based on Secure Multiparty Computation
SUN Yongqi1,2( ), SONG Zewen1,2, ZHU Weiguo1,2, ZHAO Sicong3
), SONG Zewen1,2, ZHU Weiguo1,2, ZHAO Sicong3
- 1. Key Laboratory of Big Data & Artificial Intelligence in Transportation, Ministry of Education, Beijing 100044, China
2. School of Computer and Information Technology, Beijing Jiaotong University, Beijing 100044, China
3. Beijing Aerocim Technology Co., Ltd., Beijing 102308, China
-
Received:2023-08-30Online:2023-11-10Published:2023-11-10
摘要:
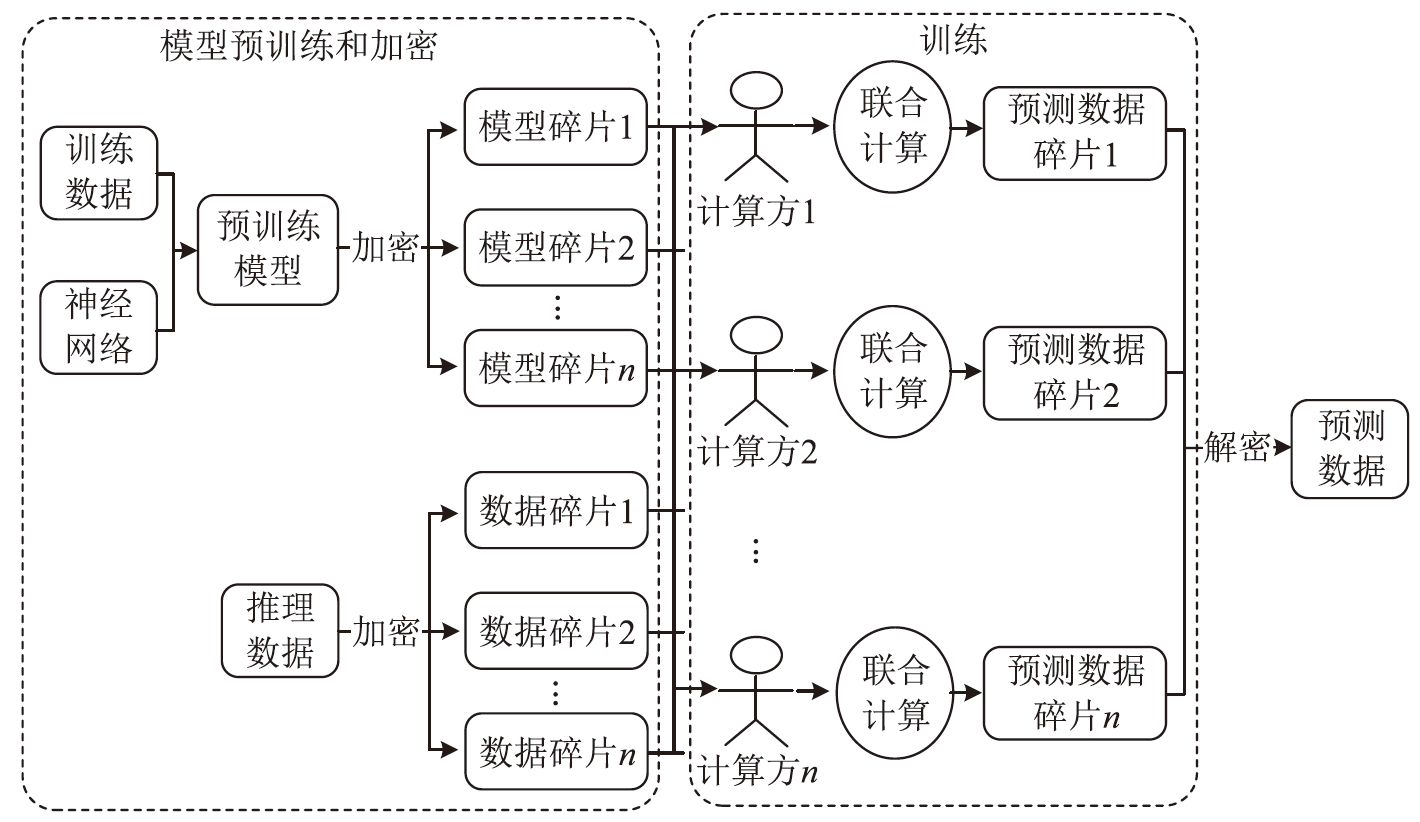
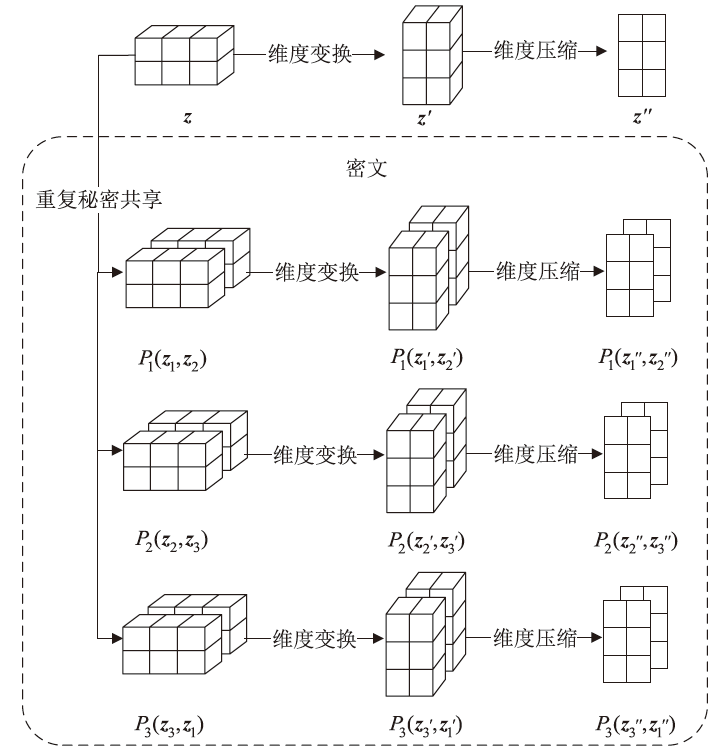
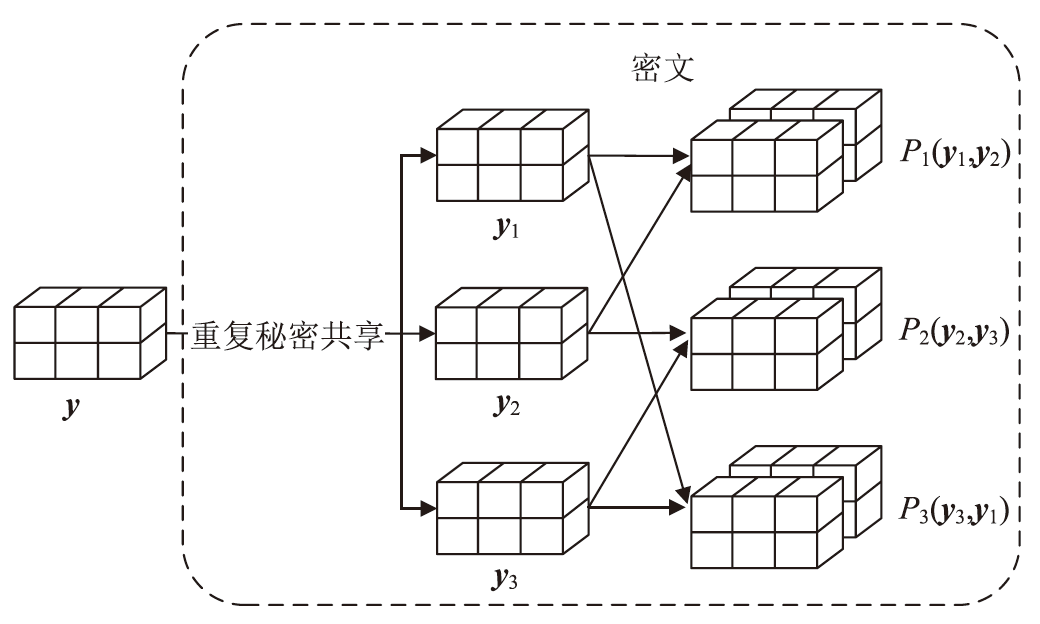
文章针对基于安全多方计算(Secure Multi-Party Computation,MPC)的图像分类方法进行研究,针对基于ABY3协议的PaddleFL方法无法支持复杂模型中的一些网络加密操作问题,提出一种面向ABY3协议重复秘密共享的维度变换和维度压缩操作的加密方法;针对基于Beaver协议的CrypTen方法在密文训练时出现的模型崩溃问题,提出一种基于标志位的检测方法,通过舍弃异常值避免模型训练的环绕错误;针对近似计算错误问题,提出一种基于阈值限制的Softmax函数密文计算方法,满足更大数值范围的密文计算。在公开数据集上进行实验,结果表明,该方法能够在保证模型准确性的前提下有效保护用户数据的隐私。
中图分类号:
引用本文
孙永奇, 宋泽文, 朱卫国, 赵思聪. 基于安全多方计算的图像分类方法[J]. 信息网络安全, 2023, 23(11): 27-37.
SUN Yongqi, SONG Zewen, ZHU Weiguo, ZHAO Sicong. Image Classification Method Based on Secure Multiparty Computation[J]. Netinfo Security, 2023, 23(11): 27-37.
使用本文
表1
图像文本识别模型网络结构及其参数
| 网络层 | 尺寸 | 参数(步长,填充) |
|---|---|---|
| Convolution+ReLU | 16×3×3 | (1, 1) |
| MaxPooling | 16×2×2 | (2, 0) |
| Convolution+ReLU | 32×3×3 | (1, 1) |
| MaxPooling | 32×2×2 | (2, 0) |
| Convolution+ReLU | 64×3×3 | (1, 1) |
| Convolution+ReLU | 64×2×2 | (1, 1) |
| FullyConnected | 50 | — |
| MaxPooling | 64×2×2 | (2, 0) |
| Convolution+ReLU+BtchNorm | 128×3×3 | (1, 1) |
| Convolution+ReLU+BtchNorm | 128×3×3 | (1, 1) |
| FullyConnected | 54 | — |
| MaxPooling | 128×2×2 | (2, 0) |
| Convolution | 128×2×2 | (1, 0) |
| Transpose | — | perm=(1, 2, 0) |
| Squeeze | — | axes=0 |
| FullyConnected +Softmax | 38 | — |
表5
场景一下模型的测试结果
| 框架 | 数据集 | 准确率 | 推理时间/s |
|---|---|---|---|
| PaddlePaddle | MNIST | 98.47% | 2.05×10-5 |
| Fashion-MNIST | 87.90% | 2.03×10-5 | |
| CIFAR-10 | 59.23% | 2.37×10-5 | |
| PaddleFL | MNIST | 98.47% | 0.000955 |
| Fashion-MNIST | 87.90% | 0.000845 | |
| CIFAR-10 | 59.23% | 0.001182 | |
| PyTorch | MNIST | 98.48% | 4.03×10-6 |
| Fashion-MNIST | 87.47% | 3.94×10-6 | |
| CIFAR-10 | 58.24% | 4.21×10-6 | |
| CrypTen | MNIST | 98.48% | 0.0159 |
| Fashion-MNIST | 87.47% | 0.0159 | |
| CIFAR-10 | 58.24% | 0.0211 |
表6
场景二下模型的训练和测试结果
| 框架 | 数据集 | 准确率(密文/明文) | 训练时间/s | 推理时间/s |
|---|---|---|---|---|
| PaddleFL | MNIST | 98.22%/98.47% | 0.00159 | 0.000946 |
| Fashion-MNIST | 86.92%/87.90% | 0.00158 | 0.000835 | |
| CIFAR-10 | 56.43%/59.23% | 0.00247 | 0.001211 | |
| CrypTen | MNIST | 98.60%/98.48% | 0.0299 | 0.0161 |
| Fashion-MNIST | 87.43%/87.47% | 0.0306 | 0.0158 | |
| CIFAR-10 | 57.51%/58.24% | 0.0395 | 0.0217 |
| [1] | WANG Fei. Application Analysis of Privacy Computing in the Field of Public Security[J]. Netinfo Security, 2021, 21(S1): 70-73. |
| 王飞. 隐私计算在公安领域的应用分析[J]. 信息网络安全, 2021, 21(S1):70-73. | |
| [2] | YAO C C. Protocols for Secure Computations[C]// IEEE. 23rd Annual Symposium on Foundations of Computer Science. New York: IEEE, 1982: 160-164. |
| [3] | YAO C C. How to Generate and Exchange Secrets[C]// IEEE. 27th Annual Symposium on Foundations of Computer Science. New York: IEEE, 1986: 162-167. |
| [4] | CHAUM D, CRÉPEAU C, DAMGARD I. Multiparty Unconditionally Secure Protocols[C]// ACM. 20th Annual ACM Symposium on Theory of Computing. New York: ACM, 1988: 11-19. |
| [5] |
SHAMIR A. How to Share a Secret[J]. Communications of the ACM, 1979, 22(11): 612-613.
doi: 10.1145/359168.359176 URL |
| [6] | BLAKLEY G R. Safeguarding Cryptographic Keys[C]// IEEE. Managing Requirements Knowledge, International Workshop on IEEE Computer Society. New York: IEEE, 1979: 313-318. |
| [7] | GOLDREICH O. How to Play Any Mental Game[C]// ACM. 19th Annual ACM Symposium on Theory of Computing. New York: ACM, 1987: 218-229. |
| [8] | BEAVER D. Efficient Multiparty Protocols Using Circuit Randomization[C]// Springer. 11th Annual International Cryptology Conference on Advances in Cryptology. Heidelberg: Springer, 1991: 420-432. |
| [9] | PEI Bei, ZHANG Shuihai, LYU Chunli. A Proactive Multi-Secret Sharing Scheme for Cloud Storage[J]. Netinfo Security, 2023, 23(5): 95-104. |
| 裴蓓, 张水海, 吕春利. 用于云存储的主动秘密共享方案[J]. 信息网络安全, 2023, 23(5):95-104. | |
| [10] | ARAKI T, FURUKAWA J, LINDELL Y, et al. High-Throughput Semi-Honest Secure Three-Party Computation with an Honest Majority[C]// ACM. 2016 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2016: 805-817. |
| [11] | MOHASSEL P, RINDAL P. ABY3: A Mixed Protocol Framework for Machine Learning[C]// ACM. 2018 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2018: 35-52. |
| [12] | WAGH S, TOPLE S, BENHAMOUDA F, et al. Falcon: Honest-Majority Maliciously Secure Framework for Private Deep Learning[J]. Privacy Enhancing Technologies, 2021(1): 188-208. |
| [13] | WAGH S, GUPTA D, CHANDRAN N. SecureNN: 3-Party Secure Computation for Neural Network Training[J]. Privacy Enhancing Technologies, 2019(3): 26-49. |
| [14] |
LECUN Y, BOTTOU L. Gradient-Based Learning Applied to Document Recognition[J]. Proceedings of the IEEE, 1998, 86(11): 2278-2324.
doi: 10.1109/5.726791 URL |
| [15] |
KRIZHEVSKY A, SUTSKEVER I, HINTON G. ImageNet Classification with Deep Convolutional Neural Networks[J]. Communications of The ACM, 2017, 60(6): 84-90.
doi: 10.1145/3065386 URL |
| [16] | SIMONYAN K, ZISSERMAN A. Very Deep Convolutional Networks for Large-Scale Image Recognition[EB/OL]. (2014-09-04)[2023-07-27]. https://doi.org/10.48550/arXiv.1409.1556. |
| [17] | SZEGEDY C, LIU Wei, JIA Yangqing, et al. Going Deeper with Convolutions[C]// IEEE. Computer Vision and Pattern Recognition. New York: IEEE, 2015: 1-9. |
| [18] | HE Kaiming, ZHANG Xiangyu, REN Shaoqing, et al. Deep Residual Learning for Image Recognition[C]// IEEE. Computer Vision and Pattern Recognition. New York: IEEE, 2016: 770-778. |
| [19] | HARALAMPIEVA V, RUECKERT D, PASSERAT-PALMBACH J. A Systematic Comparison of Encrypted Machine Learning Solutions for Image Classification[C]// ACM. 2020 Workshop on Privacy-Preserving Machine Learning in Practice. New York: ACM, 2020: 55-59. |
| [20] | BAIDU. Instructions for PaddleFL-MPC Model Encryption Demo[EB/OL]. (2021-06-07)[2023-07-27]. https://github.com/PaddlePaddle/PaddleFL/tree/master/python/paddle_fl/mpc/examples/model_encryption. |
| [21] | DOSOVITSKIY A, BEYER L, KOLESNIKOV A, et al. An Image is Worth 16×16 Words: Transformers for Image Recognition at Scale[EB/OL]. (2020-10-22)[2023-07-27]. https://arxiv.org/abs/2010.11929v2. |
| [22] | MOHASSEL P, ZHANG Yupeng. SecureML: A System for Scalable Privacy-Preserving Machine Learning[C]// IEEE. Security and Privacy(SP). New York: IEEE, 2017: 19-38. |
| [23] | RIAZI M S, WEINERT C, TKACHENKO O, et al. Chameleon: A Hybrid Secure Computation Framework for Machine Learning Applications[C]// ACM. 2018 Asia Conference on Computer and Communications Security. New York: ACM, 2018: 707-721. |
| [24] | KNOTT B, VENKATARAMAN S, HANNUN A, et al. CrypTen: Secure Multi-Party Computation Meets Machine Learning[EB/OL]. (2021-09-02)[2023-07-27]. https://arxiv.org/abs/2109.00984. |
| [25] | LEÓN MD, MORENO-BÁEZ A, MAGALLANES-QUINTANAR R, et al. Assessment in Subsets of MNIST Handwritten Digits and Their Effect in the Recognition Rate[J]. Journal of Pattern Recognition Research, 2011, 2(2): 244-252. |
| [26] | XIAO Han, RASUL K, VOLLGRAF R. Fashion-MNIST: A Novel Image Dataset for Benchmarking Machine Learning Algorithms[EB/OL]. (2017-09-15)[2023-07-27]. https://arxiv.org/abs/1708.07747. |
| [27] |
LI Hongmin, LIU Hanchao, JI Xiangyang, et al. CIFAR10-DVS: An Event-Stream Dataset for Object Classification[J]. Frontiers in Neuroscience, 2017, 11: 309-319.
doi: 10.3389/fnins.2017.00309 pmid: 28611582 |
| [1] | 李晨蔚, 张恒巍, 高伟, 杨博. 基于AdaN自适应梯度优化的图像对抗迁移攻击方法[J]. 信息网络安全, 2023, 23(7): 64-73. |
| [2] | 李增鹏, 王梅, 陈梦佳. 新形态伪随机函数研究[J]. 信息网络安全, 2023, 23(5): 11-21. |
| [3] | 郑耀昊, 王利明, 杨婧. 基于网络结构自动搜索的对抗样本防御方法研究[J]. 信息网络安全, 2022, 22(3): 70-77. |
| [4] | 唐春明, 林旭慧. 隐私保护集合交集计算协议[J]. 信息网络安全, 2020, 20(1): 9-15. |
| [5] | 陈付龙, 张紫阳, 王涛春, 谢冬. 一种基于联络信号的物联网安全身份认证方法[J]. 信息网络安全, 2018, 18(11): 40-48. |
| [6] | 陈莉;林柏钢. 基于分布式线性方程组求解的安全多方计算协议[J]. , 2013, 13(9): 0-0. |
| [7] | 刘镪;唐春明;胡杏;张永强. 多租赁用户模型下有效安全外包计算[J]. , 2013, 13(9): 0-0. |
| [8] | 南文倩;郭斌;於志文;皇甫深龙. 基于群智感知的校园活动信息采集与分享系统[J]. , 2013, 13(12): 0-0. |
| [9] | 封化民;孙轶茹;孙莹. 基于身份认证加密的匿名私钥共享方案[J]. , 2013, 13(11): 0-0. |
| 阅读次数 | ||||||||||||||||||||||||||||||||||||||||||||||||||
|
全文 165
|
|
|||||||||||||||||||||||||||||||||||||||||||||||||
|
摘要 198
|
|
|||||||||||||||||||||||||||||||||||||||||||||||||