信息网络安全 ›› 2023, Vol. 23 ›› Issue (11): 17-26.doi: 10.3969/j.issn.1671-1122.2023.11.003
基于自主舍弃与校准的鲁棒物联网设备无线密钥生成方法
- 北京理工大学网络空间安全学院,北京 100081
-
收稿日期:2023-08-17出版日期:2023-11-10发布日期:2023-11-10 -
通讯作者:郇鑫焘xintao.huan@bit.edu.cn -
作者简介:郇鑫焘(1990—),男,山东,副研究员,博士,主要研究方向为无线传感网、物联网安全、智能无线感知|缪凯焘(1999—),男,福建,硕士研究生,主要研究方向为物联网安全|陈稳(2000—),男,贵州,硕士研究生,主要研究方向为物联网时间同步及安全|吴畅帆(2002—),男,江西,硕士研究生,主要研究方向为无线传感网和物联网 -
基金资助:国家自然科学基金(62201040);国家重点研发计划(2021YFC3300200);北京理工大学青年教师学术启动计划
A Robust Wireless Key Generation Method for IoT Devices Based on Autonomous Discarding and Calibration
HUAN Xintao( ), MIAO Kaitao, CHEN Wen, WU Changfan
), MIAO Kaitao, CHEN Wen, WU Changfan
- School of Cyberspace Science and Technology, Beijing Institute of Technology, Beijing 100081, China
-
Received:2023-08-17Online:2023-11-10Published:2023-11-10
摘要:
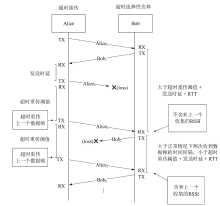
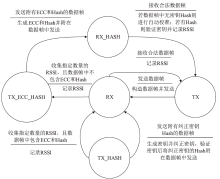
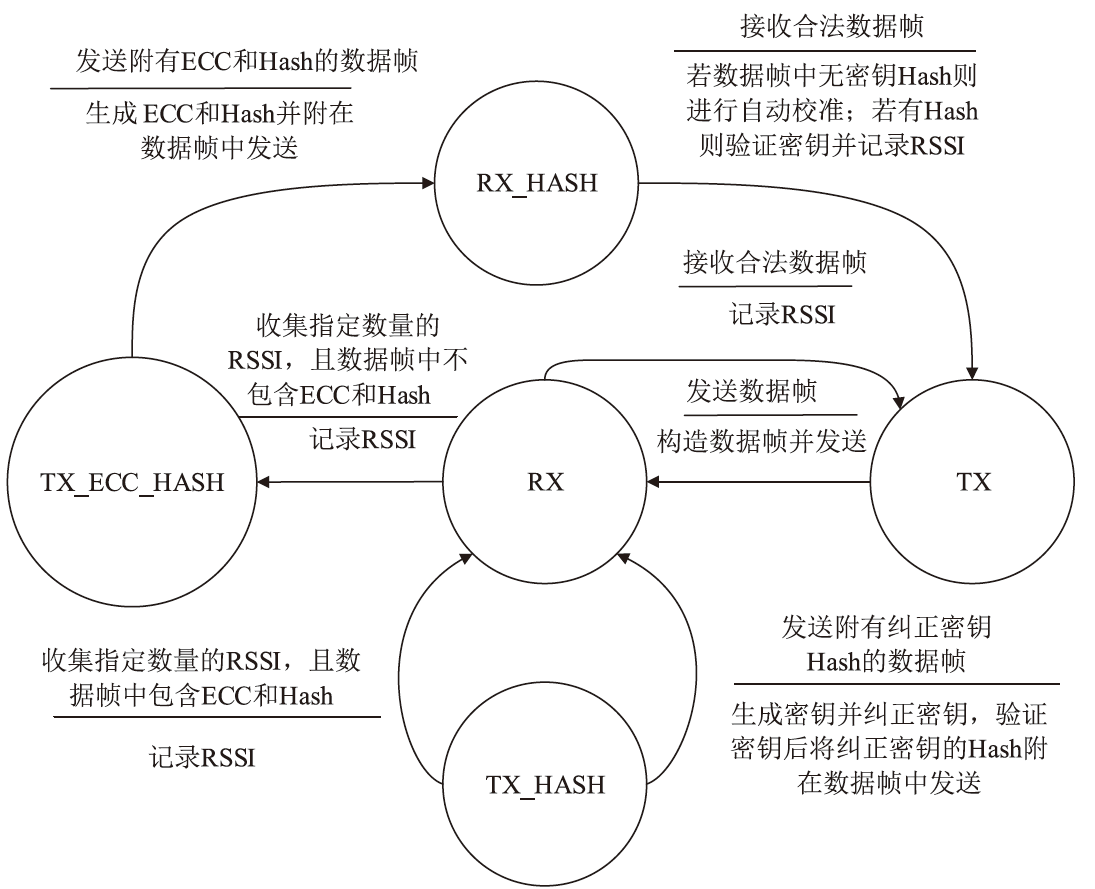
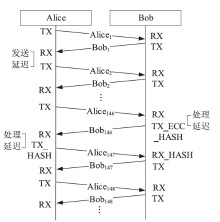
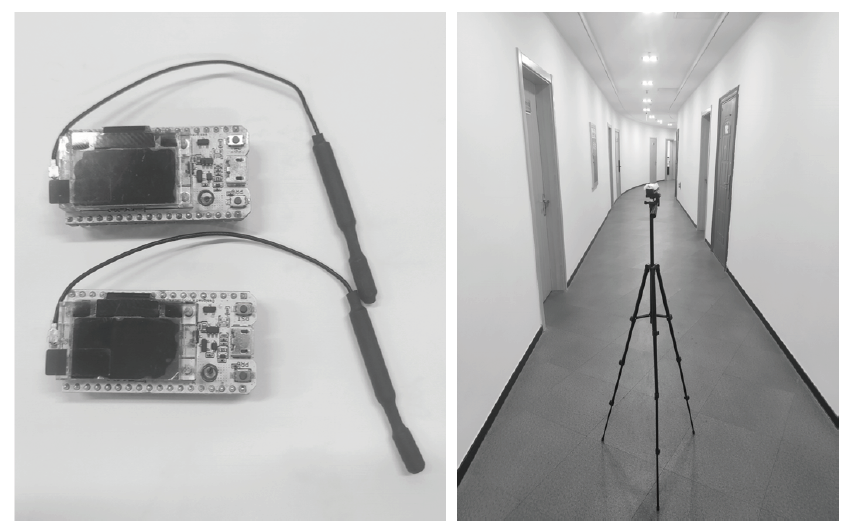
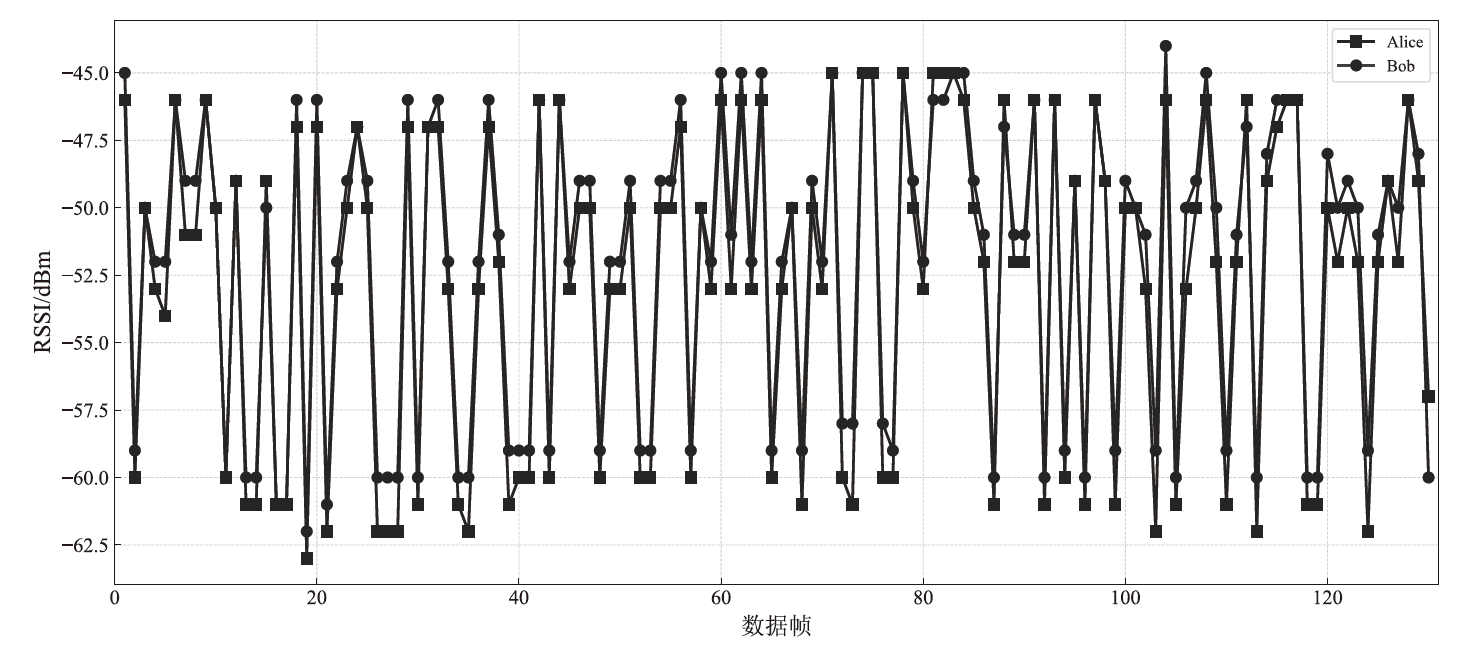
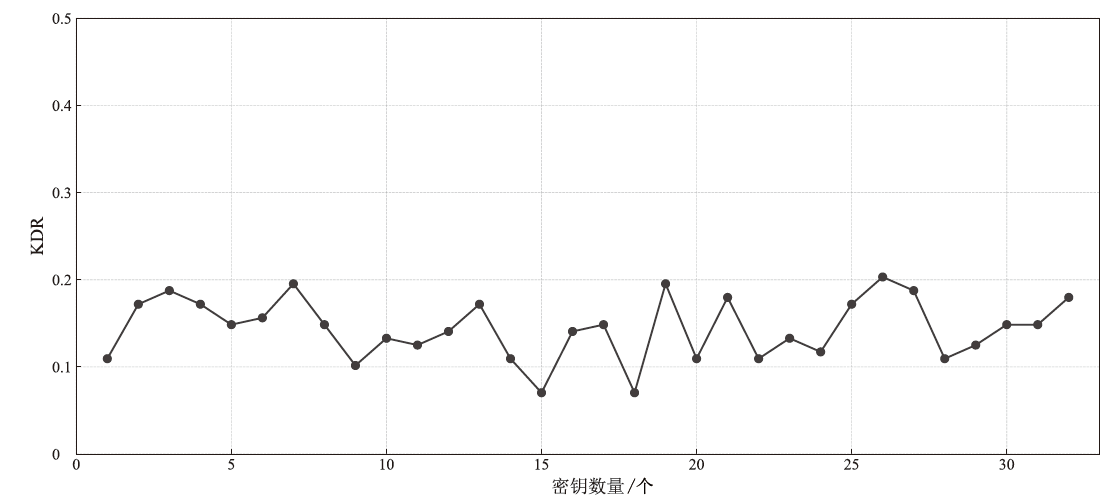
物联网设备资源匮乏、部署规模巨大,传统的密钥预共享方法及先进的密钥分发方法更新困难、计算复杂度较高,不适用于物联网设备。基于无线信道特征的无线密钥生成方法具有复杂度低和资源需求少的优势,非常适合物联网设备密钥共享。文章提出一种基于自主舍弃与校准的物联网设备无线密钥生成方法,在仅增加少量开销的情况下实现鲁棒的无线密钥生成。文章提出一种自主校准重置机制,在通信双方节点意外重启时,实现同步收集信道特征数据;同时提出一种超时选择性舍弃机制,解决丢包后通信双方信道特征数据不配对问题。该方法能够显著提升无线密钥生成系统的鲁棒性。最后在真实的物联网设备上进行实验,证明了该方法的有效性与稳定性。
中图分类号:
引用本文
郇鑫焘, 缪凯焘, 陈稳, 吴畅帆. 基于自主舍弃与校准的鲁棒物联网设备无线密钥生成方法[J]. 信息网络安全, 2023, 23(11): 17-26.
HUAN Xintao, MIAO Kaitao, CHEN Wen, WU Changfan. A Robust Wireless Key Generation Method for IoT Devices Based on Autonomous Discarding and Calibration[J]. Netinfo Security, 2023, 23(11): 17-26.
| [1] |
HERSHEY J E, HASSAN A A. Unconventional Cryptographic Keying Variable Management[J]. IEEE Transactions on Communications, 1995, 43(1): 3-6.
doi: 10.1109/26.385951 URL |
| [2] | XU Weitao, ZHANG Junqing, HUANG Shunqi, et al. Key Generation for Internet of Things: A Contemporary Survey[J]. ACM Computing Surveys, 2021, 54(1): 1-37. |
| [3] | OU Minsheng, LIAO Wei, YUAN Zhiming, et al. Research on Key Generation in Marine Environment Based on VHF Channel Characteristics[J]. Netinfo Security, 2015, 15(10): 80-85. |
| 欧敏晟, 廖巍, 袁志民, 等. 海上基于超短波信道特征的密钥生成技术研究[J]. 信息网络安全, 2015, 15(10):80-85. | |
| [4] | MATHUR S, TRAPPE W, MANDAYAM N, et al. Radio-Telepathy: Extracting a Secret Key from an Unauthenticated Wireless Channel[C]// ACM. 14th Annual International Conference on Mobile Computing and Networking. New York: ACM, 2008: 128-139. |
| [5] | ZENG Kai, WU D, CHAN An, et al. Exploiting Multiple-Antenna Diversity for Shared Secret Key Generation in Wireless Networks[C]// IEEE. IEEE INFOCOM. New York: IEEE, 2010: 1-9. |
| [6] | JANA S, PREMNATH S N, CLARK M, et al. On the Effectiveness of Secret Key Extraction from Wireless Signal Strength in Real Environments[C]// ACM. 15th Annual International Conference on Mobile Computing and Networking. New York: ACM, 2009: 321-332. |
| [7] | LIU Hongbo, WANG Yang, YANG Jie, et al. Fast and Practical Secret Key Extraction by Exploiting Channel Response[C]// IEEE. IEEE INFOCOM. New York: IEEE, 2013: 3048-3056. |
| [8] |
XU Weitao, JHA S, HU Wen. LoRa-Key: Secure Key Generation System for LoRa-Based Network[J]. IEEE Internet of Things Journal, 2019, 6(4): 6404-6416.
doi: 10.1109/JIOT.2018.2888553 |
| [9] |
PATWARI N, CROFT J, JANA S, et al. High-Rate Uncorrelated Bit Extraction for Shared Secret Key Generation from Channel Measurements[J]. IEEE Transactions on Mobile Computing, 2010, 9(1): 17-30.
doi: 10.1109/TMC.2009.88 URL |
| [10] | YASUKAWA S, IWAI H, SASAOKA H. Adaptive Key Generation in Secret Key Agreement Scheme Based on the Channel Characteristics in OFDM[C]// IEEE. 2008 International Symposium on Information Theory and Its Applications. New York: IEEE, 2008: 1-6. |
| [11] | MARGELIS G, FAFOUTIS X, OIKONOMOU G, et al. Physical Layer Secret-Key Generation with Discreet Cosine Transform for the Internet of Things[C]// IEEE. 2017 IEEE International Conference on Communications(ICC). New York: IEEE, 2017: 1-6. |
| [12] | WU Yang, SUN Yongmei, ZHAN Lei, et al. Low Mismatch Key Agreement Based on Wavelet-Transform Trend and Fuzzy Vault in Body Area Network[EB/OL]. (2013-06-06)[2023-04-11]. https://journals.sagepub.com/doi/10.1155/2013/912873. |
| [13] |
ZHANG Junqing, LI Guyue, MARSHALL A, et al. A New Frontier for IoT Security Emerging From Three Decades of Key Generation Relying on Wireless Channels[J]. IEEE Access, 2020, 8: 138406-138446.
doi: 10.1109/Access.6287639 URL |
| [14] |
ZHANG Junqing, RAJENDRAN S, SUN Zhi, et al. Physical Layer Security for the Internet of Things: Authentication and Key Generation[J]. IEEE Wireless Communications, 2019, 26(5): 92-98.
doi: 10.1109/MWC.2019.1800455 |
| [15] |
JUNEJO A K, BENKHELIFA F, WONG B, et al. LoRa-LiSK: A Lightweight Shared Secret Key Generation Scheme for LoRa Networks[J]. IEEE Internet of Things Journal, 2022, 9(6): 4110-4124.
doi: 10.1109/JIOT.2021.3103009 URL |
| [16] |
RUOTSALAINEN H, ZHANG Junqing, GREBENIUK S. Experimental Investigation on Wireless Key Generation for Low Power Wide Area Networks[J]. IEEE Internet of Things Journal, 2019, 7(3): 1745-1755.
doi: 10.1109/JIoT.6488907 URL |
| [17] | LI Guyue, HU Aiqun, SHI Le. Secret Key Extraction in Wireless Channel[J]. Journal of Cryptologic Research, 2014, 1(3): 211-224. |
| [18] |
SUI Lei, GUO Yuanbo, JIANG Wenbo, et al. Research on Key Generation and Extraction Based on Wireless Channel Characteristics[J]. Computer Science, 2015, 42(2): 137-141.
doi: 10.11896/j.issn.1002-137X.2015.02.030 |
|
隋雷, 郭渊博, 姜文博, 等. 基于无线信道特征的密钥生成与提取研究[J]. 计算机科学, 2015, 42(2):137-141.
doi: 10.11896/j.issn.1002-137X.2015.02.030 |
| [1] | 张伟, 李子轩, 徐晓瑀, 黄海平. SDP-CoAP:基于软件定义边界的安全增强CoAP通信框架设计[J]. 信息网络安全, 2023, 23(8): 17-31. |
| [2] | 李志华, 王志豪. 基于LCNN和LSTM混合结构的物联网设备识别方法[J]. 信息网络安全, 2023, 23(6): 43-54. |
| [3] | 郭瑞, 魏鑫, 陈丽. 工业物联网环境下可外包的策略隐藏属性基加密方案[J]. 信息网络安全, 2023, 23(3): 1-12. |
| [4] | 宋丽华, 张津威, 张少勇. 基于博弈论对手建模的物联网SSH自适应蜜罐策略[J]. 信息网络安全, 2023, 23(11): 38-47. |
| [5] | 廖丽云, 张伯雷, 吴礼发. 基于代价敏感学习的物联网异常检测模型[J]. 信息网络安全, 2023, 23(11): 94-103. |
| [6] | 刘翔宇, 芦天亮, 杜彦辉, 王靖翔. 基于特征选择的物联网轻量级入侵检测方法[J]. 信息网络安全, 2023, 23(1): 66-72. |
| [7] | 张学旺, 刘宇帆. 可追踪身份的物联网感知层节点匿名认证方案[J]. 信息网络安全, 2022, 22(9): 55-62. |
| [8] | 赵洪, 李姗, 左珮良, 魏占祯. 基于强化学习的物联网安全资源分配方法[J]. 信息网络安全, 2022, 22(6): 44-52. |
| [9] | 吴克河, 程瑞, 姜啸晨, 张继宇. 基于SDP的电力物联网安全防护方案[J]. 信息网络安全, 2022, 22(2): 32-38. |
| [10] | 韩俐, 宋吉祥, 孙士民. SD-IoT中基于设备地址的移动目标防御机制研究[J]. 信息网络安全, 2022, 22(11): 36-46. |
| [11] | 李桐, 任帅, 王刚, 孟庆宇. 基于变色龙认证树的云边端协同流式数据完整性验证模型[J]. 信息网络安全, 2022, 22(1): 37-45. |
| [12] | 陈庆港, 杜彦辉, 韩奕, 刘翔宇. 基于深度可分离卷积的物联网设备识别模型[J]. 信息网络安全, 2021, 21(9): 67-73. |
| [13] | 吴克河, 程瑞, 郑碧煌, 崔文超. 电力物联网安全通信协议研究[J]. 信息网络安全, 2021, 21(9): 8-15. |
| [14] | 李群, 董佳涵, 关志涛, 王超. 一种基于聚类分类的物联网恶意攻击检测方法[J]. 信息网络安全, 2021, 21(8): 82-90. |
| [15] | 刘忻, 杨浩睿, 郭振斌, 王家寅. 一种实现在线注册与权限分离的工业物联网身份认证协议[J]. 信息网络安全, 2021, 21(7): 1-9. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||