信息网络安全 ›› 2022, Vol. 22 ›› Issue (9): 1-10.doi: 10.3969/j.issn.1671-1122.2022.09.001
基于状态机子图同构匹配的私有工控协议溯源
宋宇波1,2,3( ), 陈烨1,2,3, 蔡义涵1,2,3, 张波4
), 陈烨1,2,3, 蔡义涵1,2,3, 张波4
- 1.东南大学网络空间安全学院,南京 211189
2.江苏省计算机网络技术重点实验室,南京 211189
3.网络通信与安全紫金山实验室,南京 211189
4.国网智能电网研究院有限公司,南京 210003
-
收稿日期:2022-06-13出版日期:2022-09-10发布日期:2022-11-14 -
通讯作者:宋宇波 E-mail:songyubo@seu.edu.cn -
作者简介:宋宇波(1977—),男,江苏,副教授,博士,主要研究方向为无线网络和移动通信安全、移动终端安全、隐私数据安全、区块链安全|陈烨(2000—),男,江西,硕士研究生,主要研究方向为移动通信安全、隐私数据安全、区块链安全|蔡义涵(2000—),男,江苏,硕士研究生,主要研究方向为区块链安全|张波(1985—),男,江苏,高级工程师,博士,主要研究方向为电力网络安全、电网数字化、信息物理融合安全 -
基金资助:国家自然科学基金(61601113)
Traceability of Private Industrial Control Protocol Based on Subgraph Isomorphic Matching of Protocol State Machine
SONG Yubo1,2,3( ), CHEN Ye1,2,3, CAI Yihan1,2,3, ZHANG Bo4
), CHEN Ye1,2,3, CAI Yihan1,2,3, ZHANG Bo4
- 1. School of Cyber Science and Engineering, Southeast University, Nanjing 211189, China
2. Jiangsu Key Laboratory of Computer Networking Technology, Nanjing 211189, China
3. Network Communication and Security Purple Mountain Laboratory, Nanjing 211189, China
4. Global Energy Interconnection Research Institute Co.,Ltd., Nanjing 210003, China
-
Received:2022-06-13Online:2022-09-10Published:2022-11-14 -
Contact:SONG Yubo E-mail:songyubo@seu.edu.cn
摘要:
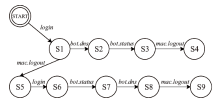
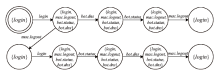
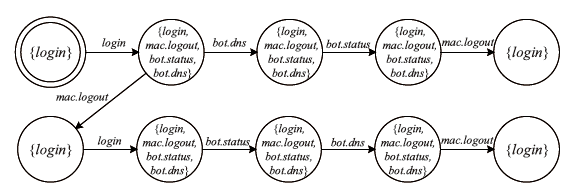
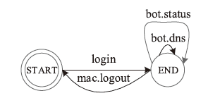
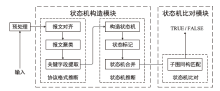
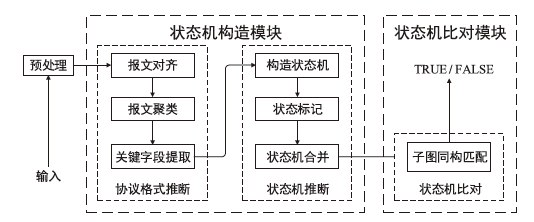
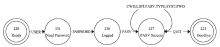
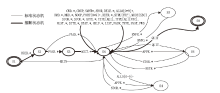
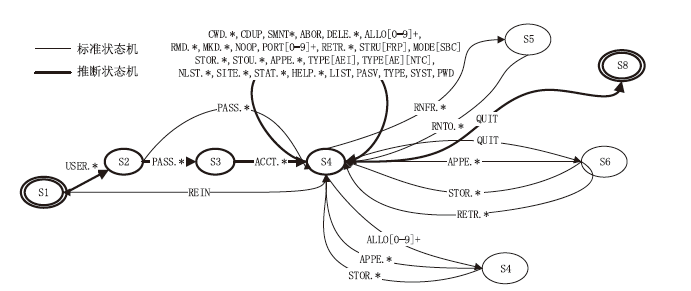
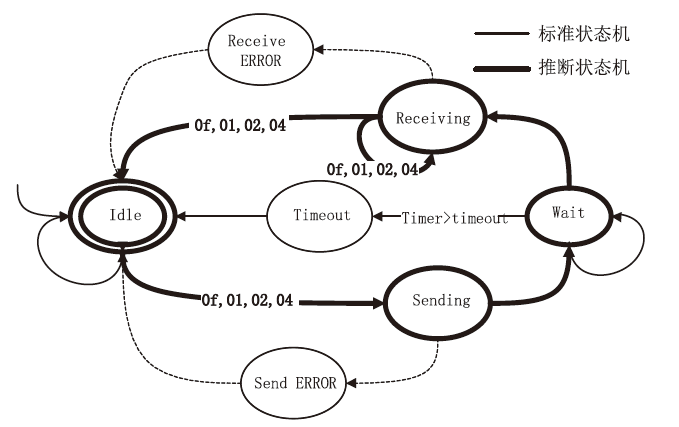
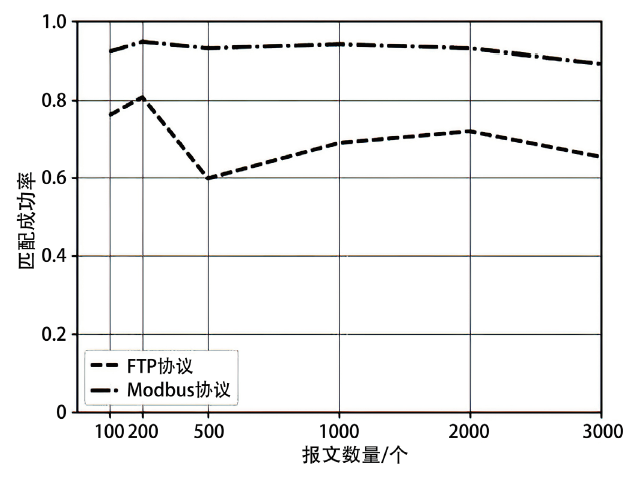
在对工业互联网设备私有工控协议进行安全分析时,溯源其采用的工控网络协议标准十分困难。文章提出一种基于状态机子图同构匹配的私有工控协议溯源方法,可快速匹配私有工控协议所采用的工控网络协议标准。该方法首先对私有工控协议流量数据进行逆向解析,通过聚类算法提取消息格式和关键字段,根据关键字段构造增广前缀树(Augmented Prefix Tree Acceptor,APTA),推断出协议状态机图;然后采用子图同构匹配算法将该状态机图与工控协议标准状态机图进行子图匹配,解决流量数据有限导致生成状态机图不完整的问题。实验结果表明,该方法溯源准确率在95%以上,可快速定位私有协议采用的工控网络协议标准,从而为进一步的安全分析提供帮助。
中图分类号:
引用本文
宋宇波, 陈烨, 蔡义涵, 张波. 基于状态机子图同构匹配的私有工控协议溯源[J]. 信息网络安全, 2022, 22(9): 1-10.
SONG Yubo, CHEN Ye, CAI Yihan, ZHANG Bo. Traceability of Private Industrial Control Protocol Based on Subgraph Isomorphic Matching of Protocol State Machine[J]. Netinfo Security, 2022, 22(9): 1-10.
| [1] | LIU Kaizheng, YANG Ming, LING Zhen, et al. On Manually Reverse Engineering Communication Protocols of Linux-Based IoT Systems[J]. IEEE, 2020, 8(8): 6815-6827. |
| [2] | FANG Weiqing, LI Peng, ZHANG Yujie, et al. Research on Optimization of Fuzzing Test of Unknown Protocol Based on Message Type[C]// Springer.International Conference on Big Data and Security.Heidelberg:Springer, 2021: 284-298. |
| [3] | BEDDOE M A. Network Protocol Analysis Using Bioinformatics Algorithms[J]. Toorcon, 2004, 26(6): 1095-1098 |
| [4] | LEITA C, MERMOUD K, DACIER M. Scriptgen: An Automated Script Generation Tool for Honeyd[C]// IEEE. Computer Security Applications Conference, 21st Annual. New York: IEEE, 2005: 203-214. |
| [5] | CUI Weidong, KANNAN J, WANG H J. Discoverer: Automatic Protocol Reverse Engineering From Network Traces[EB/OL]. (2007-8-6)[2022-06-05]. https://www.cs.purdue.edu/homes/xyzhang/fall07/Papers/discoverer.pdf |
| [6] | BOSSERT G, GUIHERY F, HIET G. Towards Automated Protocol Reverse Engineering Using Semantic information[C]// ACM. Proceedings of the 9th ACM Symposium on Information, Computer and Communications Security. New York: ACM, 2014: 51-62. |
| [7] | WANG Yiping, LI Xingjian, MENG Jiao, et al. Biprominer: Automatic Mining of Binary Protocol Features[C]// IEEE. 2011 12th International Conference on Parallel and Distributed Computing, Applications and Technologies. New York: IEEE, 2011: 179-184. |
| [8] | LUO Jianzheng, YU Shunzheng. Position-Based Automatic Reverse Engineering of Network Protocols[J]. Journal of Network and Computer Applications, 2003(3): 1070-1077. |
| [9] | CAI Jun, LUO Jianzhen, LEI Fangyuan. Analyzing Network Protocols of Application Layer Using Hidden Semi-Markov Model[J]. Mathematical Problems in Engineering, 2016(11): 1-14. |
| [10] | LIN Y D, LAI Y K, BUI Q T, et al. ReFSM: Reverse Engineering From Protocol Packet Traces to Test Generation by Extended Finite State Machines[J]. Journal of Network and Computer Applications, 2020, 171: 102819-102830. |
| [11] | KLEBER S, KOPP H, KARGL F. {NEMESYS}: Network Message Syntax Reverse Engineering by Analysis of the Intrinsic Structure of Individual Messages[EB/OL]. (2018-08-13)[2022-06-05]. https://dl.acm.org/doi/abs/10.5555/3307423.3307431. |
| [12] | YE Yapeng, ZHANG Zhuo, WANG Fei, et al. NetPlier: Probabilistic Network Protocol Reverse Engineering From Message Traces[EB/OL]. (2021-01-10)[2022-06-05]. https://www.researchgate.net/publication/350051374_NetPlier_Probabilistic_Network_Protocol_Reverse_Engineering_from_Message_Traces. |
| [13] | ULLMANN J R. An Algorithm for Subgraph Isomorphism[J]. ACM, 1976, 23(1): 31-42. |
| [14] | CORDELLA L P, FOGGIA P, SANSONE C, et al. A (Sub) Graph Isomorphism Algorithm for Matching Large Graphs[J]. IEEE Transactions on Pattern Analysis and Machine Intelligence, 2004, 26(10): 1367-1372. |
| [15] | NEEDLEMAN S B, Wunsch C D. A General Method Applicable to the Search for Similarities in the Amino Acid Sequence of Two Proteins[J]. Journal of Molecular Biology, 1970, 48(3): 443-453. |
| [16] | KAUFMAN L, ROUSSEEUW P J. Finding Groups in Data: An Introduction to Cluster Analysis[M]. New Jersey: John Wiley & Sons, 2009. |
| [17] | ANTUNES J, NEVES N. Automatically Complementing Protocol Specifications From Network Traces[EB/OL]. (2011-5-11)[2022-06-07]. https://doi.org/10.1145/1978582.1978601. |
| [1] | 张征辉, 陈兴蜀, 罗永刚, 吴天雄. 一种Spark平台下的作业性能评估方法[J]. 信息网络安全, 2022, 22(9): 86-95. |
| [2] | 梁言, 李冬, 赵贻竹, 于俊清. 基于链路冲突图嵌入的信道干扰测量与优化方法[J]. 信息网络安全, 2022, 22(9): 76-85. |
| [3] | 胡禹佳, 代政一, 孙兵. SIMON算法的差分—线性密码分析[J]. 信息网络安全, 2022, 22(9): 63-75. |
| [4] | 张学旺, 刘宇帆. 可追踪身份的物联网感知层节点匿名认证方案[J]. 信息网络安全, 2022, 22(9): 55-62. |
| [5] | 张光华, 刘永升, 王鹤, 于乃文. 基于BiLSTM和注意力机制的智能合约漏洞检测方案[J]. 信息网络安全, 2022, 22(9): 46-54. |
| [6] | 文伟平, 刘成杰, 时林. 基于数据流追溯的空指针引用挖掘系统[J]. 信息网络安全, 2022, 22(9): 40-45. |
| [7] | 佟晓筠, 毛宁, 张淼, 王翥. 基于Henon映射与改进的提升小波变换图像加密算法[J]. 信息网络安全, 2022, 22(9): 31-39. |
| [8] | 张敏, 许春香, 张建华. 无人机网络中基于多因子的认证密钥协商协议研究[J]. 信息网络安全, 2022, 22(9): 21-30. |
| [9] | 于晶, 袁曙光, 袁煜琳, 陈驰. 基于k匿名数据集的鲁棒性水印技术研究[J]. 信息网络安全, 2022, 22(9): 11-20. |
| [10] | 刘翎翔, 潘祖烈, 李阳, 李宗超. 基于前后端关联性分析的固件漏洞静态定位方法[J]. 信息网络安全, 2022, 22(8): 44-54. |
| [11] | 高博, 陈琳, 严迎建. 基于CNN-MGU的侧信道攻击研究[J]. 信息网络安全, 2022, 22(8): 55-63. |
| [12] | 魏松杰, 李成豪, 沈浩桐, 张文哲. 基于深度森林的网络匿名流量检测方法研究与应用[J]. 信息网络安全, 2022, 22(8): 64-71. |
| [13] | 黄保华, 赵伟宏, 彭丽, 谢统义. 基于MPT索引的高效链上PKI模型[J]. 信息网络安全, 2022, 22(8): 72-80. |
| [14] | 佟晓筠, 苏煜粤, 张淼, 王翥. 基于混沌和改进广义Feistel结构的轻量级密码算法[J]. 信息网络安全, 2022, 22(8): 8-18. |
| [15] | 顾兆军, 刘婷婷, 高冰, 隋翯. 基于GAN-Cross的工控系统类不平衡数据异常检测[J]. 信息网络安全, 2022, 22(8): 81-89. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||