信息网络安全 ›› 2016, Vol. 16 ›› Issue (2): 66-73.doi: 10.3969/j.issn.1671-1122.2016.02.011
新型SQL注入及其防御技术研究与分析
- 1. 华侨大学工学院,福建泉州 362021
2. 东北林业大学信息与计算机工程学院,黑龙江哈尔滨 150000
-
收稿日期:2015-12-15出版日期:2016-02-10发布日期:2020-05-13 -
作者简介:作者简介: 李鑫(1990—),男,山东,硕士研究生,主要研究方向为网络信息安全;张维纬(1982—),男,福建,硕士生导师,博士,主要研究方向为信息安全;隋子畅(1995—),男,山东,本科,主要研究方向信息安全;郑力新(1967—),男,福建,教授,博士,主要研究方向为智能仪器和系统控制。
-
基金资助:福建省自然科学基金[2015J05125];福建省科技厅专项资助项目[2013H2002];华侨大学研究生科研创新能力培育计划资助项目 [1400422005];华侨大学科研基金资助项目[13BS415];泉州市科技计划项目[2014Z112]
Research and Analysis on the Novel SQL Injection and Defense Technique
Xin LI1( ), Weiwei ZHANG1, Zichang SUI2, Lixin ZHENG1
), Weiwei ZHANG1, Zichang SUI2, Lixin ZHENG1
- 1. College of Engineering, Huaqiao University, Quanzhou Fujian 362021, China
2. Information and Computer Engineering College, Northeast Forestry University, Harbin Heilongjiang 150000,China
-
Received:2015-12-15Online:2016-02-10Published:2020-05-13
摘要:
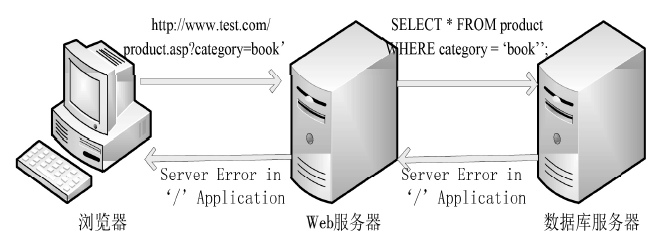
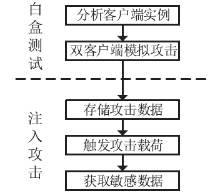
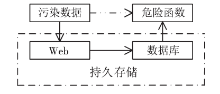
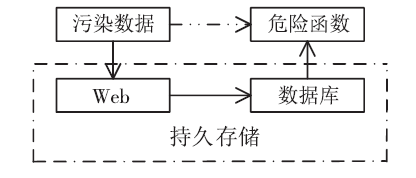
SQL注入严重威胁Web安全,并在近些年发展出新的技术。当前研究主要集中于对传统SQL注入技术的检测与防御,而忽视了新型SQL注入技术。文章在介绍传统SQL注入和现有防御技术的基础上,详细介绍了3种新型SQL注入技术——客户端SQL注入、防注检测绕过和二阶SQL注入,并从注入的效果、防御方法等方面对传统与新型SQL注入技术进行了分析比较。对注入效果的分析结果表明,新型SQL注入技术具有危害大、影响范围广、依赖手工实施等特点;对防御方法的分析结果表明,新型SQL注入技术虽然能够突破一些传统的防御方案,但是依赖现有防御技术能够对其进行有效防御。文章并在分析的最后针对每一种技术提出了适合的Web防御方案。
中图分类号:
引用本文
李鑫, 张维纬, 隋子畅, 郑力新. 新型SQL注入及其防御技术研究与分析[J]. 信息网络安全, 2016, 16(2): 66-73.
Xin LI, Weiwei ZHANG, Zichang SUI, Lixin ZHENG. Research and Analysis on the Novel SQL Injection and Defense Technique[J]. Netinfo Security, 2016, 16(2): 66-73.
| [1] | BISHT P, VENKATAKRISHNAN V N. XSS-GUARD.Detection of Intrusions and Malware, and Vulnerability Assessment[M]. Berlin Heidelberg:Springer, 2008. |
| [2] | ZELLER W, FELTEN E W.Cross-site Request Forgeries: Exploitation and Prevention[J]. The New York Times, 2008: 1-13. |
| [3] | 陈林博,江建慧,张丹青. 基于双栈的缓冲区溢出攻击的防御[J]. 同济大学学报:自然科学版,2012,40(3):452-458. |
| [4] | OWASP Foundation. OWASP Top Ten Project[EB/OL]. , 2015-5-15. |
| [5] | ANLEY C. Advanced SQL Injection in SQL Server Applications[EB/OL]. ,2015-5-15. |
| [6] | 陈小兵,张汉煜,骆力明,等. SQL 注入攻击及其防范检测技术研究[J]. 计算机工程与应用,2007,43(11): 150-152. |
| [7] | HALFOND W G, VIEGAS J, ORSO A.A Classification of SQL-injection Attacks and Countermeasures[C]//IEEE. IEEE International Symposium on Secure Software Engineering, March 13-15, 2006, McLean, Virginia. Piscataway, NJ: IEEE, 2006, (1): 13-15. |
| [8] | 韩涛. 基于解析树的SQL注入检测方法研究[D]. 哈尔滨:哈尔滨工业大学, 2013. |
| [9] | FU X, LU X, PELTSVERGER B, et al.A Static Analysis Framework for Detecting SQL Injection Vulnerabilities[C]// IEEE. 31st Annual International of Computer Software and Applications Conference, 2007(COMPSAC 2007 ). July 24-27 2007, Beijing, China. Piscataway, NJ: IEEE, 2007, (1) : 87-96. |
| [10] | 田伟,许静,杨巨峰,等. 模型驱动的Web应用SQL注入渗透测试[J]. 高技术通讯,2012,22(11):1161-1168. |
| [11] | 马小婷,胡国平,李舟军. SQL 注入漏洞检测与防御技术研究[J]. 计算机安全,2010(11):18-24. |
| [12] | BANDHAKAVI S, BISHT P, MADHUSUDAN P, et al.CANDID: Preventing SQL Injection Attacks Using Dynamic Candidate Evaluations[C]//ACM. 14th ACM conference on Computer and communications security. Oct. 29-Nov. 2, 2007, Alexandria, VA, USA. New York, NY: ACM, 2007: 12-24. |
| [13] | 刘华星,杨庚. HTML5——下一代Web开发标准研究[J]. 计算机技术与发展,2011,21(8):54-58. |
| [14] | 孙茜. Web2.0的含义、特征与应用研究[J]. 现代情报,2006,26(2):69-70. |
| [15] | 冯谷,高鹏. 新型SQL注入技术研究与分析[J]. 计算机科学, 2012,(S3):415-417. |
| [16] | CLARKE J.SQL Injection Attacks and Defense[M]. Amsterdam: Elsevier, 2009. |
| [17] | 赵瑞颖. 基于时间的SQL 注入分析与防范[J],信息网络安全,2010(1):56-57. |
| [18] | 张卓. SQL注入攻击技术及防范措施研究[D]. 上海:上海交通大学,2007. |
| [19] | WEI K, MUTHUPRASANNA M, KOTHARI S.Preventing SQL Injection Attacks in Stored Procedures[C]// IEEE. Piscataway, Software Engineering Conference, May 20-28, 2006, Shanghai, China. Piscataway, NJ: IEEE, 2006: 191-198. |
| [20] | GUPTA N, SAIKIA A.Web Application Firewall[R]. Tech. Report: CS499, Department of Computer Science and Engineering Indian Institute of Technology, Kanpur, 2007. |
| [21] | RISRIC I.ModSecurity Handbook[M]. London: Feisty Duck, 2010. |
| [22] | Comodo Security Solutions Inc. Comodo Web Application Firewall -Quick Start Guide[EB/OL]. ,2015-5-15. |
| [23] | MCCLURE R, KRÜGER I H. SQL DOM: Compile Time Checking Of Dynamic SQL Statements[C]// IEEE.2005.27th International Conference on ICSE. May 15-21, 2005, St. Louis, Missouri, USA. Piscataway, NJ: IEEE, 2005: 88-96. |
| [24] | COOK W R, RAI S.Safe Query Objects: Statically Typed Objects as Remotely Executable Queries[C]//IEEE. 27th International Conference on ICSE. May 15-21, 2005, St. Louis, Missouri, USA. Piscataway, NJ :IEEE, 2005: 97-106. |
| [25] | BOYD S W, KEROMYTIS A D. SQLrand: Preventing SQL Injection Attacks[J]. Lecture Notes in Computer Science, 2004, (3089): 292--302. |
| [26] | STUTTARD D, PINTO M.The Web Application Hacker's Handbook: Finding and Exploiting Security Flaws[M]. New York: John Wiley & Sons, 2011. |
| [27] | 闫璐. Web 应用二阶 SQL 注入漏洞检测方法研究[D]. 天津:天津大学,2014. |
| [28] | DAHSE J, HOLZ T.Static Detection of Second-Order Vulnerabilities in Web Applications[C]//USENIX. The Advanced Computing Systems Association,USENIX Security Symposium, August 20-22, 2014, San Diego, CA, USA. Berkeley,CA: USENIX, 2014: 989-1003. |
| [1] | 胡建伟, 赵伟, 闫峥, 章芮. 基于机器学习的SQL注入漏洞挖掘技术的分析与实现[J]. 信息网络安全, 2019, 19(11): 36-42. |
| [2] | 杨连群, 孟魁, 王斌, 韩勇. 基于隐马尔可夫模型的新型SQL注入攻击检测方法[J]. 信息网络安全, 2017, 17(9): 115-118. |
| [3] | 李红灵, 邹建鑫. 基于SVM和文本特征向量提取的SQL注入检测研究[J]. 信息网络安全, 2017, 17(12): 40-46. |
| [4] | 黄娜娜, 万良, 邓烜堃, 易辉凡. 一种基于序列最小优化算法的跨站脚本漏洞检测技术[J]. 信息网络安全, 2017, 17(10): 55-62. |
| [5] | 季玉香, 朱延, 唐晓强. 基于Web的软件安全分析与监测[J]. 信息网络安全, 2016, 16(9): 208-212. |
| [6] | 刘文生, 乐德广, 刘伟. SQL注入攻击与防御技术研究[J]. 信息网络安全, 2015, 15(9): 129-134. |
| [7] | 姜国锋, 高能, 江伟玉. 基于Shadow DOM和改进PBE的安全口令管理器[J]. 信息网络安全, 2015, 15(9): 270-273. |
| [8] | 田玉杰, 赵泽茂, 王丽君, 连科. 基于分类的SQL注入攻击双层防御模型研究[J]. 信息网络安全, 2015, 15(6): 1-6. |
| [9] | 邸洪波, 于绍辉, 苏吉成. 网站安全扫描产品的分析与比较[J]. 信息网络安全, 2014, 14(9): 180-183. |
| [10] | . 常见源代码安全漏洞分析与研究[J]. , 2014, 14(2): 48-. |
| [11] | 朱圣才;徐御;王火剑. 常见源代码安全漏洞分析与研究[J]. , 2014, 14(2): 0-0. |
| [12] | . 二阶 SQL 注入攻击防御模型[J]. , 2014, 14(11): 70-. |
| [13] | 杜雷, 辛阳. 基于规则库和网络爬虫的漏洞检测技术研究与实现[J]. 信息网络安全, 2014, 14(10): 38-43. |
| [14] | 杨玉龙;彭长根;周洲. 基于同态加密的防止SQL注入攻击解决方案[J]. , 2014, 14(1): 0-0. |
| [15] | 张兴杰;池阳;朱潜;徐剑. 基于内核监控及过滤规则的网站防护系统[J]. , 2013, 13(9): 0-0. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||