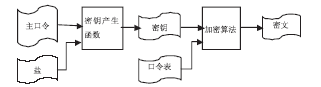
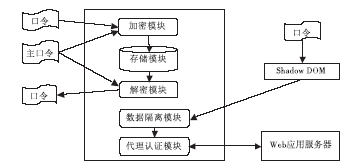
| [1] |
杨晨,游林. 可计算密文加密体制研究[J]. 信息网络安全,2014,(5):78-81.
|
| [2] |
Kontaxis G, Athanasopoulos E, Portokalidis G, et al.Sauth: Protecting user accounts from password database leaks[C]//Proceedings of the 2013 ACM SIGSAC conference on Computer & communications security. ACM, 2013: 187-198.
|
| [3] |
Bonneau J, Herley C, Van Oorschot P C, et al. The quest to replace passwords: A framework for comparative evaluation of web authentication schemes[C]// Security and Privacy (SP), 2012 IEEE Symposium on. IEEE, 2012: 553-567.Herley C, Van Oorschot P. A research agenda acknowledging the persistence of passwords. Security & Privacy, IEEE, 2012, 10(1): 28-36.
|
| [4] |
Herley C, Van Oorschot P.A research agenda acknowledging the persistence of passwords[J]. Security & Privacy, IEEE, 2012, 10(1): 28-36.
|
| [5] |
Herley C, van Oorschot P C, Patrick A S. Passwords: If we’re so smart, why are we still using them?[M]. Financial Cryptography and Data Security. Springer Berlin Heidelberg, 2009: 230-237.
|
| [6] |
He W, Akhawe D, Jain S, et al.ShadowCrypt: Encrypted Web Applications for Everyone[C]//Proceedings of the 2014 ACM SIGSAC Conference on Computer and Communications Security. ACM, 2014: 1028-1039.
|
| [7] |
Zhao R, Yue C.Toward a secure and usable cloud-based password manager for web browsers[J]. Computers & Security, 2014, 46: 32-47.
|
| [8] |
Dimitri Glazkov, Hayato Ito..
|
| [9] |
Paul December. New 25 GPU Monster Devours Passwords In Seconds[EB/OL]. https://securityledger.com/2012/12/new-25-gpu-monster-devours-passwords-in-seconds/, 2015-06-24.
|
| [10] |
Weir M, Aggarwal S, De Medeiros B, et al.Password cracking using probabilistic context-free grammars[C]//Security and Privacy, 2009 30th IEEE Symposium on. IEEE, 2009: 391-405.
|
| [11] |
吴茜,刘嘉勇,卿粼波. 基于VIPS算法和模糊字典匹配的网页提取技术研究[J]. 信息网络安全,2014,(10):49-53.
|
| [12] |
Bojinov H, Bursztein E, Boyen X, et al.Kamouflage: Loss-resistant password management[M]. Computer Security-ESORICS 2010. Springer Berlin Heidelberg, 2010: 286-302.
|
| [13] |
袁艳祥,游林. 基于身份加密的可认证密钥协商协议[J]. 信息网络安全,2014,(3):1-6.
|
| [14] |
He W, Akhawe D, Jain S, et al.ShadowCrypt: Encrypted Web Applications for Everyone[C]//Proceedings of the 2014 ACM SIGSAC Conference on Computer and Communications Security. ACM, 2014: 1028-1039.
|
 ), Neng GAO1, Wei-yu JIANG1
), Neng GAO1, Wei-yu JIANG1