信息网络安全 ›› 2015, Vol. 15 ›› Issue (9): 231-235.doi: 10.3969/j.issn.1671-1122.2015.09.051
基于IDS报警和rootkit的威胁溯源方法研究
- 云南省公安厅网络安全保卫总队,云南昆明 650021
-
收稿日期:2015-07-15出版日期:2015-09-01发布日期:2015-11-13 -
作者简介:作者简介: 夏坤鹏(1988-),男,河南,硕士,主要研究方向:信息安全、等级保护、网络安全信息通报处置;谢正勇(1973-),男,湖南,硕士,主要研究方向:网络安全管控;崔伟(1961-),男,河北,本科,主要研究方向:信息安全、等级保护、网络安全信息通报处置、网络侦查谋略。
-
基金资助:国家自然科学基金[61172072,61271308];北京市自然科学基金[4112045]
Research on Threat Traceback Method Based on IDS Alarms and Rootkit
Kun-peng XIA( ), Zheng-yong XIE, Wei CUI
), Zheng-yong XIE, Wei CUI
- Yunnan Province Public Security Bureau Cyber Police Corps, Kunming Yunnan 650021, China
-
Received:2015-07-15Online:2015-09-01Published:2015-11-13
摘要:
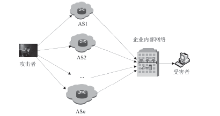
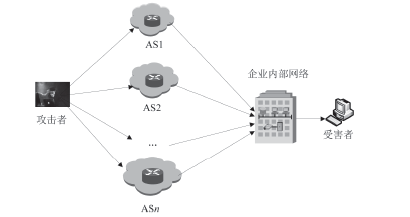
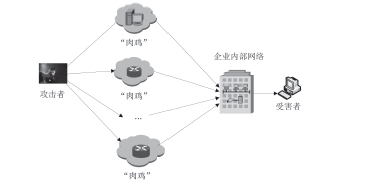
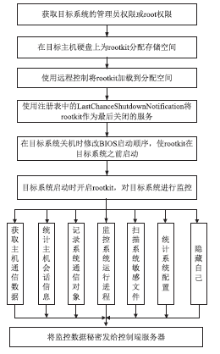
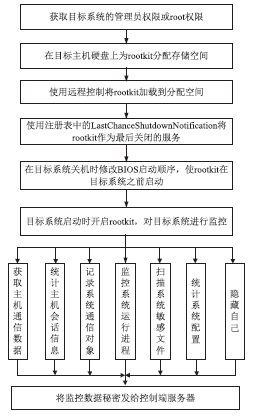
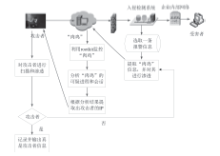
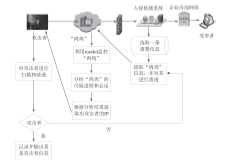
随着互联网应用的普及和不断深入,网络威胁也给人们的工作和生活带来了重大挑战。为了应对这些挑战,给广大网民营造一个安全、可信的互联网环境,文章研究了威胁信息溯源问题,分析了现有威胁溯源方法存在的不足,从实践角度出发提出了一种基于入侵检测系统报警信息和rootkit的威胁溯源方案。文章设定了本方案的假设条件,分析了该方案的可行性,指出了方案面临的挑战。
中图分类号:
引用本文
夏坤鹏, 谢正勇, 崔伟. 基于IDS报警和rootkit的威胁溯源方法研究[J]. 信息网络安全, 2015, 15(9): 231-235.
Kun-peng XIA, Zheng-yong XIE, Wei CUI. Research on Threat Traceback Method Based on IDS Alarms and Rootkit[J]. Netinfo Security, 2015, 15(9): 231-235.
| [1] | LU G, ZHONG H L, ZHANG Y, et al.Automatically Mining Application Signatures for Lightweight Deep Packet Inspection[J]. Network Technology and Application, 2013, 10(6): 86-99. |
| [2] | LENKA R K, RANJAN P.A Comparative Study on DFA-Based Pattern Matching for Deep Packet Inspection[C]//2012 Third International Conference on Computer and Communication Technology, 2012: 255-260. |
| [3] | VASHIST A, POYLISHER A, GHOSH A, et al.Managing high volume data for network attack detection using real-time flow filtering[J]. Wireless Communication Over Zigbee for Automotive Inclination Measurement China Communications, 2013, 10(3): 56-66. |
| [4] | ISO/IEC. Information technology -- Open Systems Interconnection -- Basic Reference Model: The Basic Model[EB/OL]. . |
| [5] | SILVA S S C, SILVA R M P, PINTO R C G, et al. Botnets: A survey[J]. Computer Networks, 2013, 57(2): 378-403. |
| [6] | ZHAO D, TRAORE I, SAYED B, et al.Botnet detection based on traffic behavior analysis and flow intervals[J]. Computers & Security, 2013,39(4): 2-16. |
| [7] | WEBER T. Criminals may overwhelm the web[N]. BBC News, 2007-02-25. |
| [8] | RFC 2827 Network Ingress Filtering: Defeating Denial of Service Attacks which employ IP Source Address Spoofing[S]. Network Working Group, 2000. |
| [9] | SAVAGE S, WETHERALL D, KARLIN A, et al.Network Support for IP Traceback[J]. IEEE/ACM Transactions on Networking, 2001, 9(3): 226-237. |
| [10] | STONE R.CenterTrack: An IP overlay network for tracking DoS floods[C]//in Proc. 2000 USENIX Security Syrup, 2000: 199-212. |
| [11] | LODI G, ANIELLO L, LUNA G A D, et al. An event-based platform for collaborative threats detection and monitoring[J]. Information Systems, 2014, 39(1): 175-195. |
| [12] | ZHANG L, YU S, W D, et al. A Survey on Latest Botnet Attack and Defense[C]//IEEE International Conference on Trust, Security & Privacy in Computing & Communications, 2011: 5-60 |
| [13] | YU W, ZHANG N, FU X W, et al.Localization Attacks to Internet Threat Monitors: Modeling and Countermeasures[J]. IEEE Transactions on Computers, 2010,59(12): 1655-1668. |
| [14] | 李娜,杜彦辉,高峰. 移动僵尸网络综述[J]. 信息网络安全,2015,(4):19-27. |
| [15] | 肖云,王选宏. 支持向量机理论及其在网络安全中的应用[M]. 西安:西安电子科技大学出版社,2011. |
| [16] | 何鹏程,方勇. 一种基于Web日志和网站参数的入侵检测和风险评估模型的研究[J]. 信息网络安全,2015,(1):61-65. |
| [17] | Denning D E.An Intrusion-Detection Model[J]. IEEE Transactions on Software Engineering, 1987, 13(2): 222-232. |
| [18] | 蒋建春,马恒太,任党恩,等. 网络安全入侵检测研究综述[J]. 软件学报,2000,11(11):1460-1466. |
| [19] | 戚名钰,刘铭,傅彦铭. 基于PCA的SVM网络入侵检测研究[J]. 信息网络安全,2015,(2):15-18. |
| [20] | MANGANARIS S, CHRISTENSEN M, ZERKLE D, et al.A data mining analysis of RTID alarms[J]. Computer Networks, 2000,34(4): 571-577. |
| [21] | ABOUABDALLA O, EL-TAJ H, MANASRAH A, et al.False positive reduction in intrusion detection system: a survey[C]//Proceedings of the 2009 2nd IEEE International Conference on Broadband Network & Multimedia Technology (IC-BNMT), 2009: 463-466. |
| [22] | BARAPATRE P, TARAPORE N Z, PUKALE S G, et al.Training MLP neural network to reduce false alerts in IDS[C]//Proceedings of the 2008 International Conference on Computing, Communication and Networking, 2008: 1-7. |
| [23] | 段新东,林玉香,张鑫. 基于智能化自学习方式的入侵检测防护系统设计与实现[J]. 信息网络安全,2014,(2):20-26. |
| [1] | 王蓉, 马春光, 武朋. 基于联邦学习和卷积神经网络的入侵检测方法[J]. 信息网络安全, 2020, 20(4): 47-54. |
| [2] | 罗文华, 许彩滇. 基于改进MajorClust聚类的网络入侵行为检测[J]. 信息网络安全, 2020, 20(2): 14-21. |
| [3] | 康健, 王杰, 李正旭, 张光妲. 物联网中一种基于多种特征提取策略的入侵检测模型[J]. 信息网络安全, 2019, 19(9): 21-25. |
| [4] | 冯文英, 郭晓博, 何原野, 薛聪. 基于前馈神经网络的入侵检测模型[J]. 信息网络安全, 2019, 19(9): 101-105. |
| [5] | 饶绪黎, 徐彭娜, 陈志德, 许力. 基于不完全信息的深度学习网络入侵检测[J]. 信息网络安全, 2019, 19(6): 53-60. |
| [6] | 刘敬浩, 毛思平, 付晓梅. 基于ICA算法与深度神经网络的入侵检测模型[J]. 信息网络安全, 2019, 19(3): 1-10. |
| [7] | 陈虹, 肖越, 肖成龙, 陈建虎. 融合最大相异系数密度的SMOTE算法的入侵检测方法[J]. 信息网络安全, 2019, 19(3): 61-71. |
| [8] | 田峥, 李树, 孙毅臻, 黎曦. 一种面向S7协议的工控系统入侵检测模型[J]. 信息网络安全, 2019, 19(11): 8-13. |
| [9] | 张阳, 姚原岗. 基于Xgboost算法的网络入侵检测研究[J]. 信息网络安全, 2018, 18(9): 102-105. |
| [10] | 张戈琳, 李勇. 非负矩阵分解算法优化及其在入侵检测中的应用[J]. 信息网络安全, 2018, 18(8): 73-78. |
| [11] | 魏书宁, 陈幸如, 焦永, 王进. AR-OSELM算法在网络入侵检测中的应用研究[J]. 信息网络安全, 2018, 18(6): 1-6. |
| [12] | 和湘, 刘晟, 姜吉国. 基于机器学习的入侵检测方法对比研究[J]. 信息网络安全, 2018, 18(5): 1-11. |
| [13] | 刘超玲, 张棪, 杨慧然, 吴宏晶. 基于DPDK的虚拟化网络入侵防御系统设计与实现[J]. 信息网络安全, 2018, 18(5): 41-51. |
| [14] | 陈红松, 王钢, 宋建林. 基于云计算入侵检测数据集的内网用户异常行为分类算法研究[J]. 信息网络安全, 2018, 18(3): 1-7. |
| [15] | 翟继强, 肖亚军, 杨海陆, 王健. 改进的人工蜂群结合优化的随机森林的U2R攻击检测研究[J]. 信息网络安全, 2018, 18(12): 38-45. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||