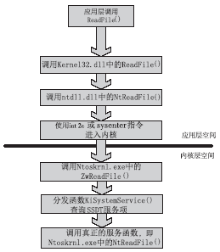
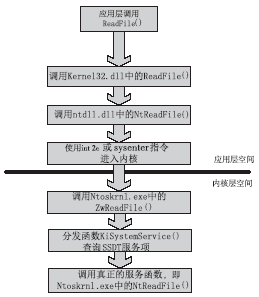
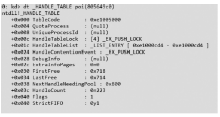
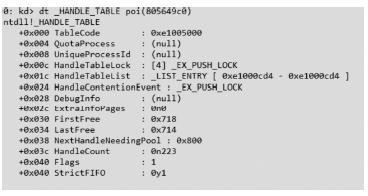
信息网络安全 ›› 2014, Vol. 14 ›› Issue (11): 52-58.doi: 10.3969/j.issn.1671-1122.2014.11.009
基于Windows API调用机制的Rootkit检测系统的设计与研究
- 华南师范大学计算机学院,广东广州 510631
-
收稿日期:2014-08-28出版日期:2014-11-01发布日期:2020-05-18 -
作者简介:作者简介:袁宇恒(1990-),男,广东,硕士研究生,主要研究方向:密码学与网络安全;黄耿星(1990-),男,广东,本科,主要研究方向:客户端安全;龚征(1981-),男,江西,副教授,博士,主要研究方向:密码学与网络安全。
-
基金资助:国家自然科学基金[61100201,61300204];广东省自然科学基金[S2012040006711];广东省高等学校优秀青年教师培养计划资助项目[Yq2013051];广州市珠江科技新星专项[2014J2200006]
The Design and Research of Rootkit Detection System Based on Windows API
YUAN Yu-heng, HUANG Geng-xing, GONG Zheng( )
)
- School of Computer Science, South China Normal University, Guangzhou Guangdong 510631,China
-
Received:2014-08-28Online:2014-11-01Published:2020-05-18
摘要:
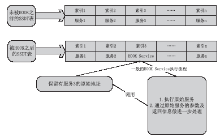
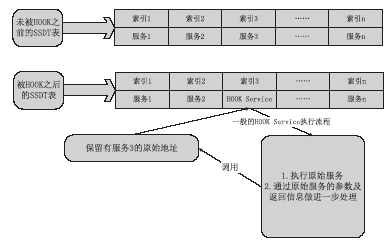
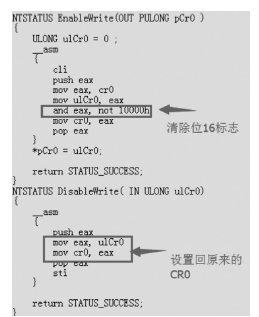
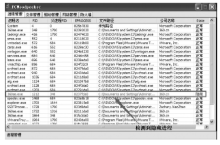
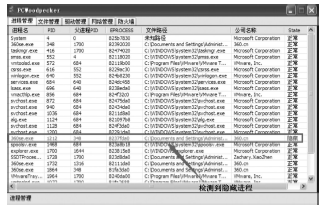
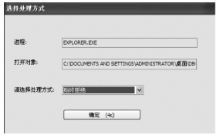
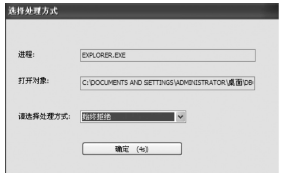
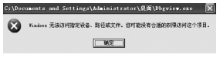
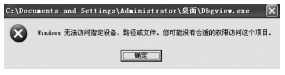
从功能上来看,Rootkit是指隐藏进程、网络端口、文件痕迹等的恶意软件,现已被广泛应用在黑客入侵和攻击他人的计算机系统上。许多计算机病毒、间谍软件也都常常使用Rootkit潜伏在操作系统上伺机而动。如何有效地对Rootkit进行检测和防范成为应对木马入侵和僵尸网络的首要解决的关键问题。文章在以往的研究基础上,通过深入探讨Windows底层原理,开发了一个基于Windows API调用机制的Rootkit检测系统。在该系统的帮助下,用户不但可以深入查看操作系统的各类底层信息,还可以很方便地找出隐藏在计算机之中的病毒、木马并进行清理,从而更好地保护操作系统。该系统丰富了现今针对Rootkit检测的研究成果,对后续的研究具有一定的参考价值。
中图分类号:
引用本文
袁宇恒, 黄耿星, 龚征. 基于Windows API调用机制的Rootkit检测系统的设计与研究[J]. 信息网络安全, 2014, 14(11): 52-58.
YUAN Yu-heng, HUANG Geng-xing, GONG Zheng. The Design and Research of Rootkit Detection System Based on Windows API[J]. Netinfo Security, 2014, 14(11): 52-58.
| [1] | 康治平,向宏,胡海波. Windows系统Rootkit隐藏技术研究与实践[J]. 计算机工程与设计,2007,28(14):3337-3343. |
| [2] | 杨彦,黄皓. Windows Rootkit隐藏技术研究[J].计算机工程,2008,34(12):152-156. |
| [3] | 白光冬, 郭耀, 陈向群. 一种基于交叉视图的Windows Rootkit检测方法[J]. 计算机科学,2009,36(8):133-137. |
| [4] | 左黎明,蒋兆峰,汤鹏志. Windows Rootkit隐藏技术与综合检测方法[J]. 计算机工程,2009,35(10):118-120. |
| [5] | 刘喆,张家旺. Rootkit木马隐藏技术分析与检测技术综述[J]. 信息安全与通信保密,2010,(11):61-65. |
| [6] | 王雷,凌翔. Windows Rootkit进程隐藏与检测技术[J]. 计算机工程,2010,36(5):140-142. |
| [7] | 潘剑锋,奚宏生,谭小彬.一种利用程序行为分析的rootkit异常检测方法[J]. 中国科学技术大学学报,2010,40(8):863-869. |
| [8] | Wang J.A rule-based approach for rootkit detection[C]//Information Management and Engineering (ICIME), 2010 The 2nd IEEE International Conference on. IEEE, 2010: 405-408. |
| [9] | Fu D, Zhou S, Cao C.A Windows rootkit detection method based on cross-view[J]. E-Product E-Service and E-Entertainment (ICEEE), 2010, 2(110): 1-3. |
| [10] | Tsaur W, Chen Y C.Exploring Rootkit Detectors' Vulnerabilities Using a New Windows Hidden Driver Based Rootkit[C]//Social Computing (SocialCom), 2010 IEEE Second International Conference on. IEEE, 2010: 842-848. |
| [11] | Mahapatra C, Selvakumar S.An online cross view difference and behavior based kernel rootkit detector[J]. ACM SIGSOFT Software Engineering Notes, 2011, 36(4): 1-9. |
| [12] | Arnold T, Yang T A.Rootkit attacks and protection: a case study of teaching network security[J]. Journal of Computing Sciences in Colleges, 2011, 26(5): 122-129. |
| [13] | Alexander J S, Dean T, Knight S, et al.Spy: counter-intelligence methods for backtracking malicious intrusions[C]//Proceedings of the 2011 Conference of the Center for Advanced Studies on Collaborative Research. IBM Corp., 2011: 1-14. |
| [14] | Jeffrey Richter.Windows核心编程[M].黄陇,李虎,译.4版.北京:机械工业出版社,2008. |
| [15] | 段钢. 加密与解密第三版[M].北京:电子工业出版社,2008. |
| [16] | Kris Kaspersky.黑客反汇编揭秘[M].谭明金译.2版.北京:电子工业出版社,2010. |
| [17] | 张银奎. 软件调试[M].北京:电子工业出版社,2008. |
| [18] | Russinovich M E, Solomon D A.Microsoft Windows internals (4th ed.)[M]. Redmond:Microsoft Press, 2005. |
| [19] | Hoglund G, Butler J.Rootkits: subverting the Windows kernel[M]. Stoughton: Addison-Wesley Professional, 2005. |
| [20] | 潘爱民. Windows内核原理与实现[M].北京:电子工业出版社,2009. |
| [21] | 谭文,邵坚磊.从汇编语言到Windows内核编程[M].北京:电子工业出版社,2008. |
| [22] | 张佩,马勇,董鉴远.深入浅出windows驱动开发[M].北京:电子工业出版社,2011. |
| [23] | Nagar R.Windows NT file system internals: a developer's guide[M]. Amherst: O'Reilly & Associates, Inc., 1997. |
| [1] | 赵俊, 任怡, 李宝, 谭郁松. 混源操作系统供应链安全风险评估方法研究[J]. 信息网络安全, 2023, 23(5): 50-61. |
| [2] | 翟高寿, 刘晨, 向勇. 基于内核函数监控的Linux系统防护方法的研究与实现[J]. 信息网络安全, 2018, 18(3): 26-38. |
| [3] | 张健, 高铖, 宫良一, 顾兆军. 虚拟机自省技术研究[J]. 信息网络安全, 2017, 17(9): 63-68. |
| [4] | 谭茁, 翟高寿. 设备驱动非内核化通信架构的研究与实现[J]. 信息网络安全, 2016, 16(11): 57-65. |
| [5] | 张磊, 陈兴蜀, 任益, 李辉. 一种基于VMM的内核级Rootkit检测技术[J]. 信息网络安全, 2015, 15(4): 56-61. |
| [6] | 卿斯汉. 关键基础设施安全防护[J]. 信息网络安全, 2015, 15(2): 1-6. |
| [7] | . 操作系统指纹特征伪装技术研究[J]. , 2014, 14(5): 1-. |
| [8] | . 电力移动智能终端安全技术研究[J]. , 2014, 14(4): 70-. |
| [9] | . Linux 操作系统 root 账号密码获取防范技术研究[J]. , 2014, 14(3): 24-. |
| [10] | 陈小兵. Linux 操作系统 root 账号密码获取防范技术研究[J]. , 2014, 14(3): 0-0. |
| [11] | 何弦庭;叶小平;黄耿星. PE病毒感染行为重定向器设计与实现[J]. , 2013, 13(4): 0-0. |
| [12] | 李宇飞;关钦;李豪;蔡志豪. NDIS数据过滤的实现及应用[J]. , 2013, 13(4): 0-0. |
| [13] | 周运伟. 手机安全问题的难点剖析及其对策[J]. , 2013, 13(10): 0-0. |
| [14] | 李科. 服务器操作系统的测评方法[J]. , 2012, 12(Z): 0-0. |
| [15] | 杨卫军;秦海权;王鹏. Android移动应用软件检测平台[J]. , 2012, 12(8): 0-0. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||