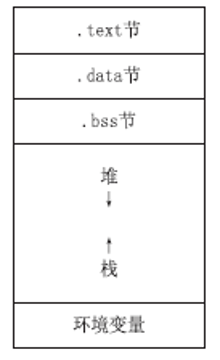
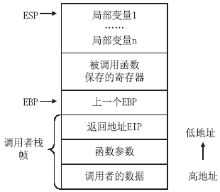
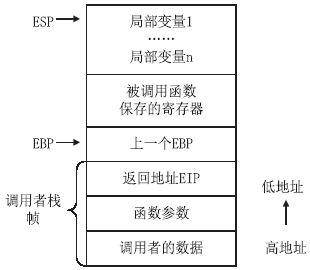
信息网络安全 ›› 2014, Vol. 14 ›› Issue (11): 59-65.doi: 10.3969/j.issn.1671-1122.2014.11.010
基于Windows的软件安全典型漏洞利用策略探索与实践
- 北京大学软件与微电子学院,北京 102600
Exploration and Practice of Using Typical Software Vulnerabilities Based on Windows
GUAN Tong( ), REN Fu-li, WEN Wei-ping, ZHANG Hao
), REN Fu-li, WEN Wei-ping, ZHANG Hao
- School of Software & Microelectronics, Peking University, Beijing 102600, China
摘要:
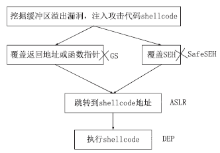
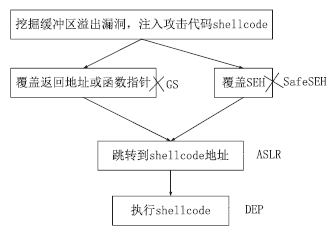
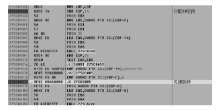
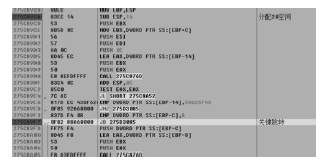
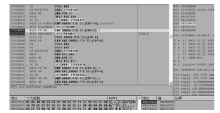
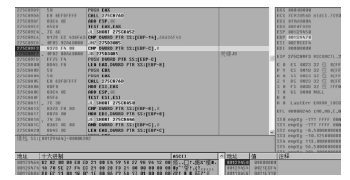
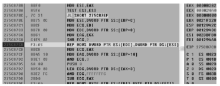
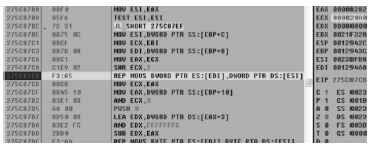
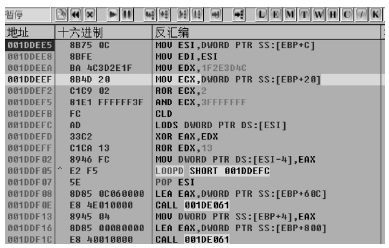
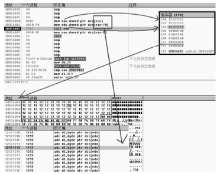
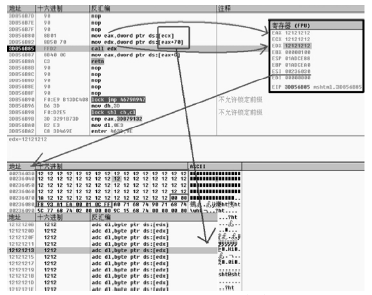
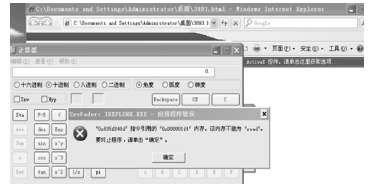
随着全球信息化的迅猛发展,计算机软件已成为世界经济、科技、军事和社会发展的重要引擎。信息安全的核心在于其所依附的操作系统的安全机制以及软件本身存在的漏洞。软件漏洞本身无法构成攻击,软件漏洞利用使得把漏洞转化为攻击变为可能。文章立足于Windows操作系统,主要分析了一些常用软件的典型漏洞原理以及常见的利用方法,比较了不同利用方法在不同环境下的性能优劣,并简单分析了Windows的安全机制对软件的防护作用以及对软件漏洞利用的阻碍作用。文章着重对几种典型漏洞进行了软件漏洞利用的探索和实践,并使用当前流行的对安全机制的绕过方法分析了Windows几种安全机制的脆弱性。
中图分类号: