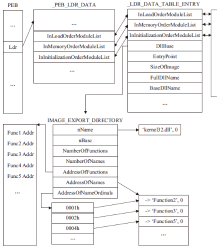
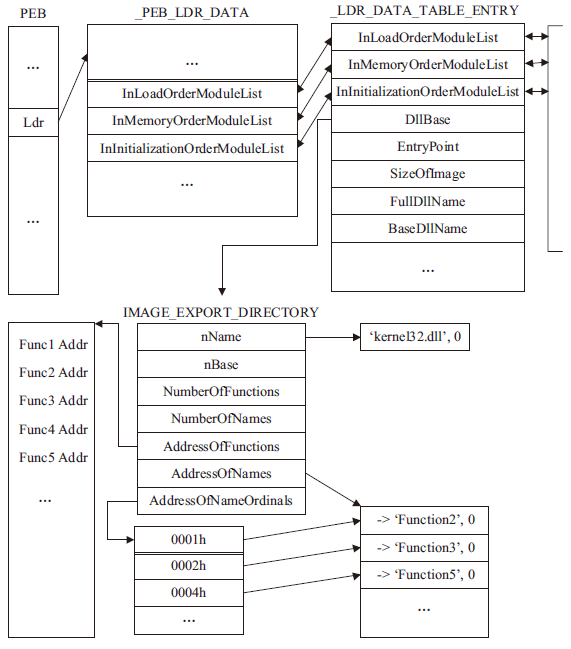
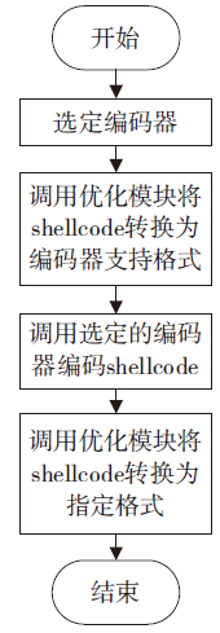
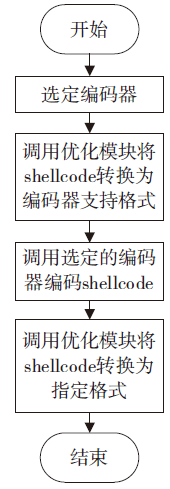
| [1] |
诸葛建伟,陈力波,田繁,等. Metasploit渗透测试魔鬼训练营[M]. 北京:机械工业出版社,2013.
|
| [2] |
BIODI P. ShellForge G2 Shellcodes for Everybody and every Platform[EB/OL]. , 2017-1-22.
|
| [3] |
BIODI P. ShellForge G3[EB/OL]. , 2017-1-22.
|
| [4] |
YUANGE. WINDOWS的SHELLCODE编写高级技巧[EB/OL]. , 2017-2-11.
|
| [5] |
HUME. 关于Windows下ShellCode编写的一点思考[EB/OL]. , 2017-2-11.
|
| [6] |
NICKHARBOUR. Writing Shellcode with a C Compiler[EB/OL]. , 2010-7-1.
|
| [7] |
KMSRUSSIAN. Windows平台下高级Shellcode编程技术[EB/OL]. , 2017-2-12.
|
| [8] |
高君丰,张岳峰,罗森林,等. 网络编码协议污点回溯逆向分析方法研究[J].信息网络安全,2017(1):68-76.
|
| [9] |
TIAN Donghai, CHEN Mo, HU Changzhen, et al. Efficient Shellcode Detection on Commodity Hardware[J]. IEICE Transactions on Information and Systems.2013, E96, D(10): 2272-2276.
|
| [10] |
郭亮,罗森林,潘丽敏. 编码函数交叉定位网络协议测试数据生成方法研究[J].信息网络安全,2016(3):8-14.
|
| [11] |
SONG Yingbo, LOCASTO M E, STAVROU A, et al.On the Infeasibility of Modeling Polymorphic Shellcode[J]. Machine Learning, 2010, 81(2): 179-205.
|
| [12] |
BASU A, MATHURIA A, CHOWDARY N.Automatic Generation of Compact Alphanumeric Shellcodes for x86[C]//Springer. Smart System Platform Development for City and Society, GoeSmart 2014, September 24-25, 2014, Grand Royal Panghegar, Bandung, Indonesia. Heidelberg: Springer, 2014: 399-410.
|
| [13] |
MASON J, SMALL S, MONROSE F, et al.English Shellcode[C]//ACM. 16th ACM Conference on Computer and Communications Security, November 9-13, 2009, Chicago, Illinois, USA. New York: ACM, 2009: 524-533.
|
| [14] |
SkyLined. ALPHA3-Alphanumeric Shellcode Encoder[EB/OL]. , 2017-2-12.
|
| [15] |
tombkeeper. Shellcode_Template_in_C[EB/OL]., 2017-2-12.
|
| [16] |
丁庸,曹伟,罗森林. 基于LKM系统调用劫持的恶意软件行为监控技术研究[J].信息网络安全,2016(4):1-8.
|
| [17] |
ARCE I.The Shellcode Generation[J]. IEEE Security & Privacy, 2004, 2(5):72-76.
|
| [18] |
ROSCHKE S, CHENG Feng, MEINEL C.BALG: Bypassing Application Layer Gateways using Multi-staged Encrypted Shellcodes[C]//IEEE. 2011 IFIP/IEEE International Symposium on Integrated Network Management (IM), May 23-27, 2011, Dublin, Ireland. New Jersey: IEEE, 2011: 399-406.
|
 ), Dongxiang KE
), Dongxiang KE