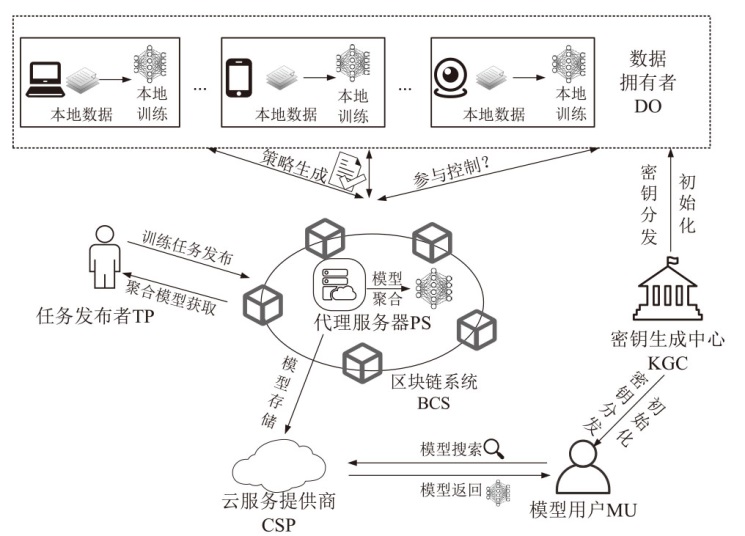
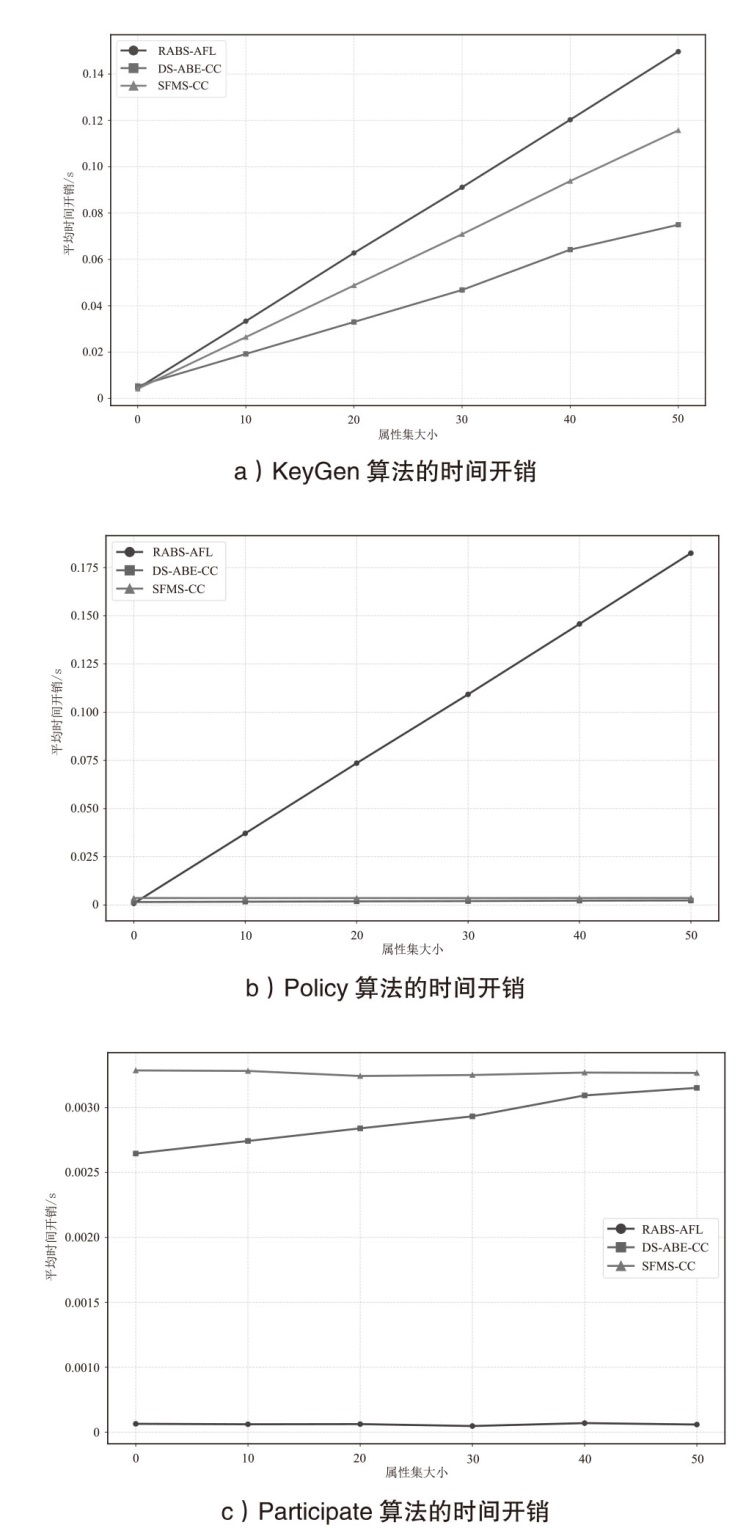
Netinfo Security ›› 2026, Vol. 26 ›› Issue (1): 102-114.doi: 10.3969/j.issn.1671-1122.2026.01.009
Previous Articles Next Articles
A Lightweight Dynamic Node Participation Scheme for Federated Learning Nodes Supporting Attribute Update
ZHENG Kaifa1, LUO Zhenpeng2, LIU Jiayi2, LIU Zhiquan2, WANG Ze3, WU Yunkun4( )
)
- 1. College of Computer Science and Technology, Zhejiang University, Hangzhou 310027, China
2. School of Cyber Security, Jinan University, Guangzhou 511443, China
3. School of Software, Tiangong University, Tianjin 300387, China
4. Qi An Xin Technology Group Inc., Beijing 100084, China
-
Received:2025-08-20Online:2026-01-10Published:2026-02-13
CLC Number:
Cite this article
ZHENG Kaifa, LUO Zhenpeng, LIU Jiayi, LIU Zhiquan, WANG Ze, WU Yunkun. A Lightweight Dynamic Node Participation Scheme for Federated Learning Nodes Supporting Attribute Update[J]. Netinfo Security, 2026, 26(1): 102-114.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2026.01.009
| 方案 | DO加密开销 | DO解密开销 | PS解密开销 |
|---|---|---|---|
| 本文方案 | |||
| 文献[ | |||
| 文献[ | |||
| 文献[ | |||
| 文献[ | — | ||
| 文献[ | |||
| 文献[ | |||
| 文献[ |
| 方案 | DO密钥 | DO密文 | CSP密文 |
|---|---|---|---|
| 本文方案 | |||
| 文献[ | — | ||
| 文献[ | |||
| 文献[ | |||
| 文献[ | — | ||
| 文献[ | — | ||
| 文献[ | — | ||
| 文献[ | — |
| [1] | ZHENG Wenbo, YAN Lang, GOU Chao, et al. Federated Meta-Learning for Fraudulent Credit Card Detection[C]// IEEE. The Twenty-Ninth International Joint Conference on Artificial Intelligence. New York: IEEE, 2021: 4654-4660. |
| [2] |
BRISIMI T S, CHEN Ruidi, MELA T, et al. Federated Learning of Predictive Models from Federated Electronic Health Records[J]. International Journal of Medical Informatics, 2018, 112: 59-67.
doi: S1386-5056(18)30008-X pmid: 29500022 |
| [3] |
POKHREL S R, CHOI J. Federated Learning with Blockchain for Autonomous Vehicles: Analysis and Design Challenges[J]. IEEE Transactions on Communications, 2020, 68(8): 4734-4746.
doi: 10.1109/TCOMM.26 URL |
| [4] | NIKNAM S, DHILLON H S, REED J H. Federated Learning for Wireless Communications: Motivation, Opportunities, and Challenges[J]. IEEE Communications Magazine, 2020, 58(6): 46-51. |
| [5] | LIU Yang, HUANG Anbu, LUO Yun, et al. FedVision: An Online Visual Object Detection Platform Powered by Federated Learning[C]// AAAI. The AAAI Conference on Artificial Intelligence. New York: AAAI Press, 2020: 13172-13179. |
| [6] | LI Li, FAN Yuxi, TSE M, et al. A Review of Applications in Federated Learning[EB/OL]. (2020-11-01)[2025-02-20]. https://doi.org/10.1016/j.cie.2020.106854. |
| [7] | MCMAHAN B, MOORE E, RAMAGE D, et al. Communication-Efficient Learning of Deep Networks from Decentralized Data[C]// AISTATS. The 20th International Conference on Artificial Intelligence and Statistics. New York: PMLR, 2017: 1273-1282. |
| [8] | XIE Cong, KOYEJO S, GUPTA I. Asynchronous Federated Optimization[EB/OL]. (2020-01-01)[2025-02-20]. https://arxiv.org/abs/1903.03934. |
| [9] | SAHAI A, WATERS B. Fuzzy Identity-Based Encryption[C]// EUROCRYPT. Advances in Cryptology- EUROCRYPT 2005. Heidelberg: Springer, 2005: 457-473. |
| [10] |
KIM H, PARK J, BENNIS M, et al. Blockchained on-Device Federated Learning[J]. IEEE Communications Letters, 2019, 24(6): 1279-1283.
doi: 10.1109/COML.4234 URL |
| [11] | WANG Rong, TSAI W T. Asynchronous Federated Learning System Based on Permissioned Blockchains[EB/OL]. (2022-02-21)[2025-02-20]. https://doi.org/10.3390/s22041672. |
| [12] | KHAN L U, SAAD W, HAN Zhu, et al. Federated Learning for Internet of Things: Recent Advances, Taxonomy, and Open Challenges[J]. IEEE Communications Surveys & Tutorials, 2021, 23(3): 1759-1799. |
| [13] | GUO Shaoyong, XIANG Baoyu, XIA Xuwei, et al. Blockchain and Federated Learning Based Data Security Sharing Mechanism over Smart City[EB/OL]. (2020-11-12)[2025-02-20]. https://doi.org/10.21203/rs.3.rs-104012/v1. |
| [14] |
LU Yunlong, HUANG Xiaohong, DAI Yueyue, et al. Blockchain and Federated Learning for Privacy-Preserved Data Sharing in Industrial IoT[J]. IEEE Transactions on Industrial Informatics, 2019, 16(6): 4177-4186.
doi: 10.1109/TII.9424 URL |
| [15] | ALBOGAMI N N. Intelligent Deep Federated Learning Model for Enhancing Security in Internet of Things Enabled Edge Computing Environment[EB/OL]. (2025-02-03)[2025-02-20]. https://doi.org/10.1038/s41598-025-88163-5. |
| [16] |
WANG Pengpian, FENG Dengguo, ZHANG Liwu. CP-ABE Scheme Supporting Fully Fine-Grained Attribute Revocation[J]. Journal of Software, 2012, 23(10): 2805-2816.
doi: 10.3724/SP.J.1001.2012.04184 URL |
| 王鹏翩, 冯登国, 张立武. 一种支持完全细粒度属性撤销的CP-ABE方案[J]. 软件学报, 2012, 23(10): 2805-2816. | |
| [17] | WU Xia, XU Lei, ZHU Liehuang. Local Differential Privacy-Based Federated Learning under Personalized Settings[EB/OL]. (2023-03-24)[2025-02-20]. https://doi.org/10.3390/app13074168. |
| [18] | PANG Bo, LIANG Huihui, ZHANG Linghao, et al. An Improved Federated Learning-Assisted Data Aggregation Scheme for Smart Grids[EB/OL]. (2023-08-22)[2025-02-20]. https://doi.org/10.3390/app13179813. |
| [19] | WANG Pengfei, WEI Zongzheng, ZHOU Dongsheng, et al. Survey on Federated Forgetting Learning[J]. Chinese Journal of Computers, 2024, 47(2): 396-422. |
| 王鹏飞, 魏宗正, 周东生, 等. 联邦忘却学习研究综述[J]. 计算机学报, 2024, 47(2): 396-422. | |
| [20] |
BAUCAS M J, SPACHOS P, PLATANIOTIS K N. Federated Learning and Blockchain-Enabled Fog-IoT Platform for Wearables in Predictive Healthcare[J]. IEEE Transactions on Computational Social Systems, 2023, 10(4): 1732-1741.
doi: 10.1109/TCSS.2023.3235950 URL |
| [21] |
SAVAZZI S, NICOLI M, RAMPA V. Federated Learning with Cooperating Devices: A Consensus Approach for Massive IoT Networks[J]. IEEE Internet of Things Journal, 2020, 7(5): 4641-4654.
doi: 10.1109/JIoT.6488907 URL |
| [22] |
LIU Jingwei, LI Yating, SUN Rong, et al. EMK-ABSE: Efficient Multikeyword Attribute-Based Searchable Encryption Scheme through Cloud-Edge Coordination[J]. IEEE Internet of Things Journal, 2022, 9(19): 18650-18662.
doi: 10.1109/JIOT.2022.3163340 URL |
| [23] | ZHENG Kaifa, DING Caiyang, WANG Jinchen. A Secure Data-Sharing Scheme for Privacy-Preserving Supporting Node-Edge-Cloud Collaborative Computation[EB/OL]. (2023-06-15)[2025-02-20]. https://doi.org/10.3390/electronics12122737. |
| [24] |
ZHENG Kaifa, ZHOU Ziyu, LIU Jianwei, et al. Secure Fine-Grained Multi-Keyword Ciphertext Search Supporting Cloud-Edge-End Collaboration in IoT[J]. Chinese Journal of Electronics, 2025, 34(1): 266-281.
doi: 10.23919/cje.2023.00.244 URL |
| [25] | WATERS B. Ciphertext-Policy Attribute-Based Encryption:An Expressive, Efficient, and Provably Secure Realization[C]// Springer. International Workshop on Public Key Cryptography. Heidelberg: Springer, 2011: 53-70. |
| [26] | LI Yanfeng, ZHANG Guipeng, LIN Lubin, et al. Accountable and Verifiable Outsourced Decryption for Ciphertext-Policy Attribute-Based Encryption[J]. Journal of Guangdong University of Technology, 2024, 41(4): 106-113. |
| 李彦锋, 张桂鹏, 林禄滨, 等. 一种支持追责和可验证外包解密的属性基加密方案[J]. 广东工业大学学报, 2024, 41(4): 106-113. | |
| [27] |
QIN Baodong, DENG R H, LIU Shengli, et al. Attribute-Based Encryption with Efficient Verifiable Outsourced Decryption[J]. IEEE Transactions on Information Forensics and Security, 2015, 10(7): 1384-1393.
doi: 10.1109/TIFS.2015.2410137 URL |
| [28] | LI Qi, ZHU Hongbo, YING Zuobin, et al. Traceable Ciphertext-Policy Attribute-Based Encryption with Verifiable Outsourced Decryption in eHealth Cloud[EB/OL]. (2018-06-06)[2025-02-20]. https://doi.org/10.1155/2018/1701675. |
| [1] | ZHANG Xuewang, CHEN Siyu, LUO Xinyue, LEI Zhitao, XIE Haofei. Efficient Searchable Attribute-Based Encryption Scheme for Cloud-Assisted Industrial IoT [J]. Netinfo Security, 2024, 24(9): 1352-1363. |
| [2] | XIE Xiaofeng, ZHANG Xintao, WANG Xin, LU Xiuqing. Multi-Keyword Searchable Encryption Scheme Based on Cloud Storage [J]. Netinfo Security, 2024, 24(9): 1444-1457. |
| [3] | GUO Rui, YANG Xin, WANG Junming. Verifiable and Revocable Attribute Encryption Scheme Based on Blockchain [J]. Netinfo Security, 2024, 24(6): 863-878. |
| [4] | WU Lizhao, WANG Xiaoding, XU Tian, QUE Youxiong, LIN Hui. Defense Strategies against Poisoning Attacks in Semi-Asynchronous Federated Learning [J]. Netinfo Security, 2024, 24(10): 1578-1585. |
| [5] | ZHOU Quan, CHEN Minhui, WEI Kaijun, ZHENG Yulong. Blockchain Access Control Scheme with SM9-Based Attribute Encryption [J]. Netinfo Security, 2023, 23(9): 37-46. |
| [6] | SHI Runhua, XIE Chenlu. Verifiable Outsourcing EMR Scheme with Attribute-Based Encryption in Cloud-Edge Environments [J]. Netinfo Security, 2023, 23(7): 9-21. |
| [7] | LI Li, ZHU Jiangwen, YANG Chunyan. Overview of Research on the Revocable Mechanism of Attribute-Based Encryption [J]. Netinfo Security, 2023, 23(4): 39-50. |
| [8] | LI Jiahui, QIN Sujuan, GAO Fei, SUN Dongxu. Controllable and Supervised Privacy Protection Scheme for Blockchain Organization Transaction Based on Attribute Encryption [J]. Netinfo Security, 2023, 23(12): 103-112. |
| [9] | CUI Haoyu, MA Limin, WANG Jiahui, ZHANG Wei. Research on the Security Model of Multi-Authority for Attribute Encryption Based on Blockchain [J]. Netinfo Security, 2022, 22(5): 84-93. |
| [10] | ZHANG Xuewang, YAO Yaning, LI Zhihong, ZHANG Hao. Data Sharing Scheme Based on Consortium Blockchain and Asmuth-Bloom Secret Sharing Algorithm [J]. Netinfo Security, 2022, 22(11): 17-23. |
| [11] | LU Xiaofeng, FU Songbing. A Trusted Data Access Control Scheme Combining Attribute-based Encryption and Blockchain [J]. Netinfo Security, 2021, 21(3): 7-8. |
| [12] | WANG Jinmiao, XIE Yongheng, WANG Guowei, LI Yiting. A Method of Privacy Preserving and Access Control in Blockchain Based on Attribute-based Encryption [J]. Netinfo Security, 2020, 20(9): 47-51. |
| [13] | SHI Guofeng, ZHANG Xinglan. An Attribute-based Encryption Scheme for Cloud Storage Supporting Range Ciphertext Search [J]. Netinfo Security, 2020, 20(6): 75-81. |
| [14] | LIU Peng, HE Qian, LIU Wangyang, CHENG Xu. CP-ABE Scheme Supporting Attribute Revocation and Outsourcing Decryption [J]. Netinfo Security, 2020, 20(3): 90-97. |
| [15] | XU Shengwei, WANG Feijie. Attribute-based Encryption Scheme Traced Under Multi-authority [J]. Netinfo Security, 2020, 20(1): 33-39. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||