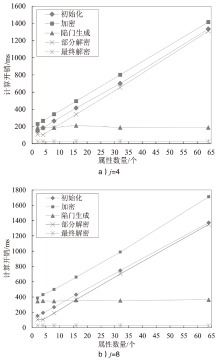
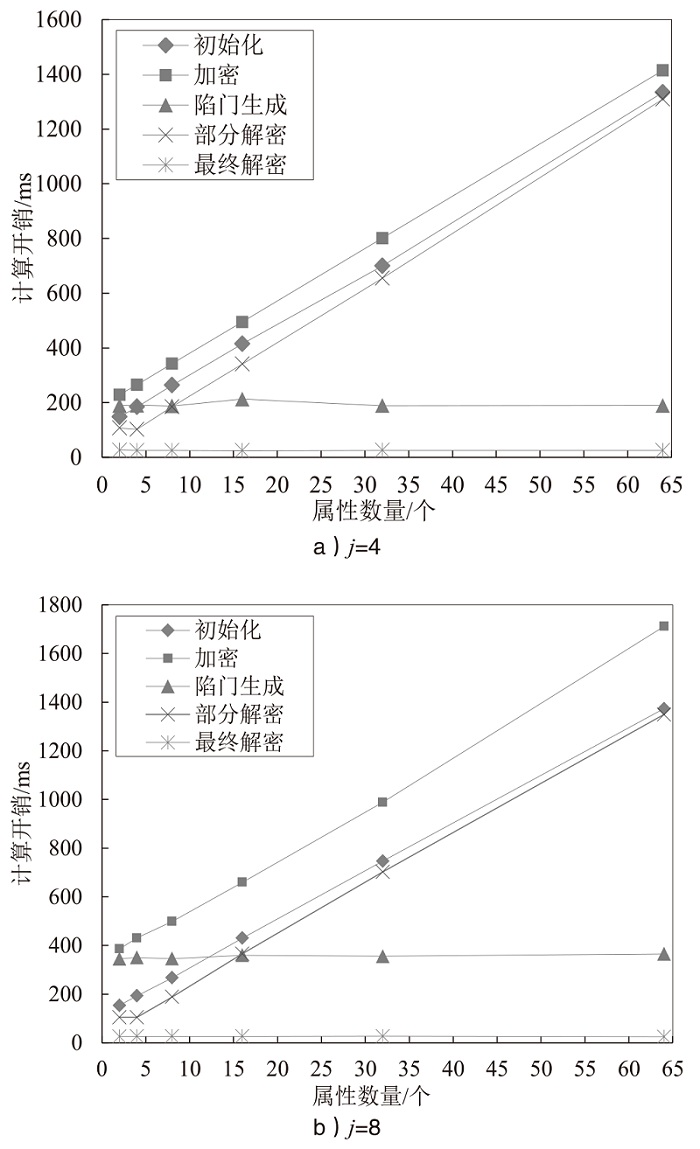
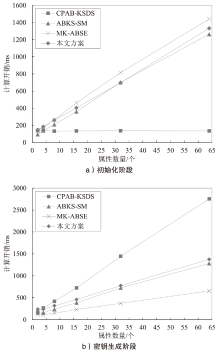
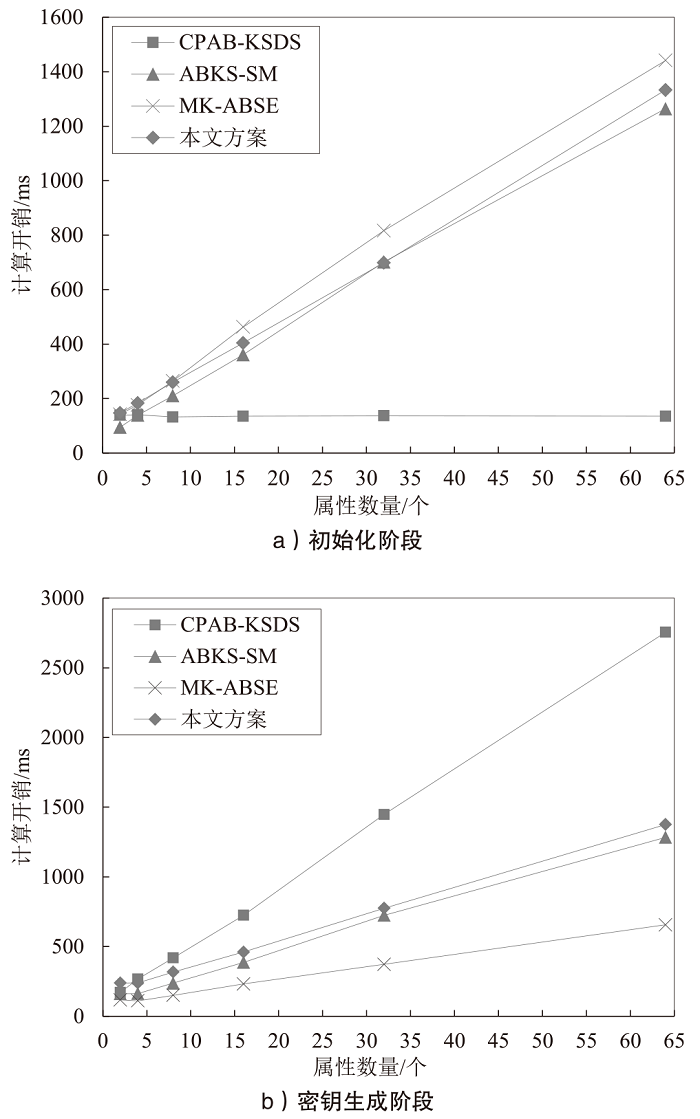
Netinfo Security ›› 2024, Vol. 24 ›› Issue (9): 1444-1457.doi: 10.3969/j.issn.1671-1122.2024.09.012
Previous Articles Next Articles
Multi-Keyword Searchable Encryption Scheme Based on Cloud Storage
XIE Xiaofeng, ZHANG Xintao, WANG Xin, LU Xiuqing( )
)
- College of Computer Science and Technology, Qingdao University, Qingdao 266071, China
-
Received:2023-11-16Online:2024-09-10Published:2024-09-27
CLC Number:
Cite this article
XIE Xiaofeng, ZHANG Xintao, WANG Xin, LU Xiuqing. Multi-Keyword Searchable Encryption Scheme Based on Cloud Storage[J]. Netinfo Security, 2024, 24(9): 1444-1457.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2024.09.012
| [1] | YANG Pan, XIONG Naixue, REN Jingli. Data Security and Privacy Protection for Cloud Storage: A Survey[J]. IEEE Access, 2020, 8: 131723-131740. |
| [2] | HUANG Qinlong, CHEN Lixuan, WANG Chao. A Parallel Secure Flow Control Framework for Private Data Sharing in Mobile Edge Cloud[J]. IEEE Transactions on Parallel and Distributed Systems, 2022, 33(12): 4638-4653. |
| [3] | LIU Liyuan, HAN Meng, WANG Yan, et al. Understanding Data Breach: A Visualization Aspect[C]// WASA. Wireless Algorithms, Systems, and Applications:13th International Conference. Heidelberg: Springer, 2018(13): 883-892. |
| [4] | KOLEVSKI D, MICHAEL K, ABBAS R et al. Cloud Data Breach Disclosures: The Consumer and Their Personally Identifiable Information(PII)?[C]// IEEE. Norbert Wiener in the 21st Century(21CW). New York: IEEE, 2021: 1-9. |
| [5] |
WANG Yunling, WANG Jianfeng, CHEN Xiaofeng. Secure Searchable Encryption: A Survey[J]. Journal of Communications and Information Networks, 2016, 1: 52-65.
doi: 10.11959/j.issn.2096-1081.2016.043 |
| [6] | LI Chaoyang, DONG Mianxiong, LI Jian, et al. Efficient Medical Big Data Management with Keyword-Searchable Encryption in Healthchain[J]. IEEE Systems Journal, 2022, 16(4): 5521-5532. |
| [7] | ZHANG Yinghui, ZHU Tian, ZHENG Dong. Multi-Keyword Fine-Grained Searchable Encryption Scheme Based on Blockchain[J]. Netinfo Security, 2021, 21(2): 34-44. |
| 张应辉, 朱甜, 郑东. 基于区块链的多关键字细粒度可搜索加密方案[J]. 信息网络安全, 2021, 21(2):34-44. | |
| [8] |
ZHANG Jianhong, WU Menglong, WANG Jing, et al. Secure and Verifiable Multi-Keyword Searchable Encryption Scheme in Cloud[J]. Journal on Communications, 2021, 42(4): 139-149.
doi: 10.11959/j.issn.1000-436x.2021054 |
|
张键红, 武梦龙, 王晶, 等. 云环境下安全的可验证多关键词搜索加密方案[J]. 通信学报, 2021, 42(4):139-149.
doi: 10.11959/j.issn.1000-436x.2021054 |
|
| [9] | SONG D X, WAGNER D, PERRIG A. Practical Techniques for Searches on Encrypted Data[C]// IEEE. Symposium on Security and Privacy. New York: IEEE, 2000: 44-55. |
| [10] | LIU Xueqiao, YANG Guomin, SUSILO W, et al. Privacy-Preserving Multi-Keyword Searchable Encryption for Distributed Systems[J]. IEEE Transactions on Parallel and Distributed Systems, 2020, 32(3): 561-574. |
| [11] |
WANG Shangping, JIA Shasha, ZHANG Yaling. Verifiable and Multi-Keyword Searchable Attribute-Based Encryption Scheme for Cloud Storage[J]. IEEE Access, 2019, 7: 50136-50147.
doi: 10.1109/ACCESS.2019.2910828 |
| [12] | LU Xiaofeng, FU Songbing. A Trusted Data Access Control Scheme Combining Attribute-Based Encryption and Blockchain[J]. Netinfo Security, 2021, 21(3): 7-14. |
| 芦效峰, 付淞兵. 属性基加密和区块链结合的可信数据访问控制方案[J]. 信息网络安全, 2021, 21(3):7-14. | |
| [13] | LIANG Yanrong, LI Yanping, ZHANG Kai, et al. VMSE: Verifiable Multi-Keyword Searchable Encryption in Multi-User Setting Supporting Keywords Updating[EB/OL]. (2023-08-10)[2023-10-11]. https://doi.org/10.1016/j.jisa.2023.103518. |
| [14] | MOATZA T, SHIKFA A. Boolean Symmetric Searchable Encryption[C]// ACM. 8th ACM SIGSAC Symposium on Information, Computer and Communications Security. New York: ACM, 2013: 265-276. |
| [15] | ZHANG Rui, IMAI H. Generic Combination of Public Key Encryption with Keyword Search and Public Key Encryption[C]// Springer. 6th International Conference on Cryptology and Network Security. Heidelberg: Springer, 2007: 159-174. |
| [16] | SHI Zhenkui, FU Xuemei, LI Xianxian, et al. ESVSSE: Enabling Efficient, Secure, Verifiable Searchable Symmetric Encryption[J]. IEEE Transactions on Knowledge and Data Engineering, 2020, 34(7): 3241-3254. |
| [17] | WANG Xiaofen, MU Yi, CHEN Rongmao, et al. Secure Channel Free ID-Based Searchable Encryption for Peer-to-Peer Group[J]. Journal of Computer Science and Technology, 2016, 31: 1012-1027. |
| [18] | GOLLE P, STADDON J, WATERS B. Secure Conjunctive Keyword Search over Encrypted Data[C]//Springer. Applied Cryptography and Network Security:Second International Conference, ACNS 2004. Heidelberg: Springer, 2004: 31-45. |
| [19] | XU Peiming, TANG Shaohua, XU Peng, et al. Practical Multi-Keyword and Boolean Search over Encrypted E-Mail in Cloud Server[J]. IEEE Transactions on Services Computing, 2019, 14(6): 1877-1889. |
| [20] | GAO Sheng, CHEN Yuqi, ZHU Jianming, et al. BPMS: Blockchain-Based Privacy-Preserving Multi-Keyword Search in Multi-Owner Setting[J]. IEEE Transactions on Cloud Computing, 2022, 11(3): 2260-2272. |
| [21] | ZOU Yipeng, PENG Tao, WANG Guojun, et al. Blockchain-Assisted Multi-Keyword Fuzzy Search Encryption for Secure Data Sharing[EB/OL]. (2023-09-09)[2023-10-29]. https://doi.org/10.1016/j.sysarc.2023.102984. |
| [22] | SAHAI A, WATERS B. Fuzzy Identity-Based Encryption[C]// IACR. 24th Annual Iernational Cnference on the Teory and Appcations of Cyptographic Tchniques. Heidelberg: Springer, 2005: 457-473. |
| [23] | GOYAL V, PANDEY O, SAHAI A, et al. Attribute-Based Encryption for Fine-Grained Access Control of Encrypted Data[C]// ACM. 13th ACM Conference on Computer and Communications Security. New York: ACM, 2006: 89-98. |
| [24] | GE Chunpeng, SUSILO W, LIU Zhe, et al. Secure Keyword Search and Data Sharing Mechanism for Cloud Computing[J]. IEEE Transactions on Dependable and Secure Computing, 2021, 18(6): 2787-2800. |
| [25] | MIAO Yinbin, LIU Ximeng, CHOO K K R, et al. Privacy-Preserving Attribute-Based Keyword Search in Shared Multi-Owner Setting[J]. IEEE Transactions on Dependable and Secure Computing, 2019, 18(3): 1080-1094. |
| [26] | WU Yalian, LI Xinyu, LIU Zheng. Attribute-Based Keyword Searchable Encryption Scheme for Multi-Authority in Cloud Storage[C]// IEEE. 22nd International Conference on Communication Technology(ICCT). New York: IEEE, 2022: 933-939. |
| [27] | MIAO Yinbin, DENG R H, LIU Ximing, et al. Multi-Authority Attribute-Based Keyword Search over Encrypted Cloud Data[J]. IEEE Transactions on Dependable and Secure Computing, 2019, 18(4): 1667-1680. |
| [28] | LIU Xueyan, HUAN Lijuan, SUN Ruirui, et al. Lightweight Fine-Grained Multiowner Search over Encrypted Data in Cloud-Edge Computing[EB/OL]. (2023-01-06)[2023-10-29]. https://doi.org/10.1155/2023/1701874. |
| [29] | VIVEK S S, RAMASAMY R, GEORGE P, et al. Dynamic Verifiable Encrypted Keyword Search: Using Bitmap Index[J]. Journal of Signal Processing Systems, 2018, 90(8-9): 1151-1165. |
| [30] | QIN Baodong, CHEN Congzheng, HE Junjie, et al. Multi-Keyword Searchable Encryption Scheme Based on Verifiable Secret Sharing[J]. Netinfo Security, 2023, 23(5): 32-40. |
| 秦宝东, 陈从正, 何俊杰, 等. 基于可验证秘密共享的多关键词可搜索加密方案[J]. 信息网络安全, 2023, 23(5):32-40. | |
| [31] | SUN Jin, REN Lili, WANG Shangping, et al. Multi-Keyword Searchable and Data Verifiable Attribute-Based Encryption Scheme for Cloud Storage[J]. IEEE Access, 2019(7): 66655-66667. |
| [32] | LI Feng, MA Jianfeng, MIAO Yinbin, et al. Verifiable and Dynamic Multi-Keyword Search over Encrypted Cloud Data Using Bitmap[J]. IEEE Transactions on Cloud Computing, 2021, 11(1): 336-348. |
| [33] | FENG Tao, MIAO Sirui, LIU Chunyan, et al. Verifiable Keyword Search Encryption Scheme That Supports Revocation of Attributes[J]. Symmetry, 2023, 15(4): 914-926. |
| [34] | CHEN Biwen, XIANG Tao, HE Debiao, et al. BPVSE: Publicly Verifiable Searchable Encryption for Cloud-Assisted Electronic Health Records[J]. IEEE Transactions on Information Forensics and Security, 2023, 18: 3171-3184. |
| [1] | ZHANG Xuewang, CHEN Siyu, LUO Xinyue, LEI Zhitao, XIE Haofei. Efficient Searchable Attribute-Based Encryption Scheme for Cloud-Assisted Industrial IoT [J]. Netinfo Security, 2024, 24(9): 1352-1363. |
| [2] | GUO Rui, YANG Xin, WANG Junming. Verifiable and Revocable Attribute Encryption Scheme Based on Blockchain [J]. Netinfo Security, 2024, 24(6): 863-878. |
| [3] | ZHOU Quan, CHEN Minhui, WEI Kaijun, ZHENG Yulong. Blockchain Access Control Scheme with SM9-Based Attribute Encryption [J]. Netinfo Security, 2023, 23(9): 37-46. |
| [4] | SHI Runhua, XIE Chenlu. Verifiable Outsourcing EMR Scheme with Attribute-Based Encryption in Cloud-Edge Environments [J]. Netinfo Security, 2023, 23(7): 9-21. |
| [5] | LI Li, ZHU Jiangwen, YANG Chunyan. Overview of Research on the Revocable Mechanism of Attribute-Based Encryption [J]. Netinfo Security, 2023, 23(4): 39-50. |
| [6] | LI Jiahui, QIN Sujuan, GAO Fei, SUN Dongxu. Controllable and Supervised Privacy Protection Scheme for Blockchain Organization Transaction Based on Attribute Encryption [J]. Netinfo Security, 2023, 23(12): 103-112. |
| [7] | CUI Haoyu, MA Limin, WANG Jiahui, ZHANG Wei. Research on the Security Model of Multi-Authority for Attribute Encryption Based on Blockchain [J]. Netinfo Security, 2022, 22(5): 84-93. |
| [8] | ZHANG Xuewang, YAO Yaning, LI Zhihong, ZHANG Hao. Data Sharing Scheme Based on Consortium Blockchain and Asmuth-Bloom Secret Sharing Algorithm [J]. Netinfo Security, 2022, 22(11): 17-23. |
| [9] | LU Xiaofeng, FU Songbing. A Trusted Data Access Control Scheme Combining Attribute-based Encryption and Blockchain [J]. Netinfo Security, 2021, 21(3): 7-8. |
| [10] | WANG Jinmiao, XIE Yongheng, WANG Guowei, LI Yiting. A Method of Privacy Preserving and Access Control in Blockchain Based on Attribute-based Encryption [J]. Netinfo Security, 2020, 20(9): 47-51. |
| [11] | LANG Weimin, MA Weiguo, ZHANG Yin, YAO Jinfang. A Data Deduplication Scheme Supporting Dynamic Management of Data Ownership [J]. Netinfo Security, 2020, 20(6): 1-9. |
| [12] | SHI Guofeng, ZHANG Xinglan. An Attribute-based Encryption Scheme for Cloud Storage Supporting Range Ciphertext Search [J]. Netinfo Security, 2020, 20(6): 75-81. |
| [13] | ZHANG Yi, LIU Hongyan, XIAN Hequn, TIAN Chengliang. A Cloud Storage Encrypted Data Deduplication Method Based on Authorization Records [J]. Netinfo Security, 2020, 20(3): 75-82. |
| [14] | LIU Peng, HE Qian, LIU Wangyang, CHENG Xu. CP-ABE Scheme Supporting Attribute Revocation and Outsourcing Decryption [J]. Netinfo Security, 2020, 20(3): 90-97. |
| [15] | LANG Weimin, WANG Xueli, ZHANG Han, PEI Yunxiang. A Secure Data Deduplication Scheme Based on Secret Sharing Algorithm [J]. Netinfo Security, 2020, 20(11): 43-50. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||